 This topic has been haunted in my mind for quite a while. As an information security guy, we got tons of reports about end point activities. One of them is the website ip or urls they were accessing. A typical network abnormal behavior for an infected or compromised end point is huge amount of accessing malicious ip or bad reputation websites.
This topic has been haunted in my mind for quite a while. As an information security guy, we got tons of reports about end point activities. One of them is the website ip or urls they were accessing. A typical network abnormal behavior for an infected or compromised end point is huge amount of accessing malicious ip or bad reputation websites.For many investigations, I can generate an ip list but how to quickly find out the ip reputation is a challenge for me.
That is why I am writing this post today. I am still checking those websites or scripts, hopefully I can get a good understanding then comes out my own script to do this job.
Online Service - Bulkblacklist.com
Here are some good online resources:
https://www.bulkblacklist.com/ - Simple IP and Domain Reputation Tracking System - Mostly focus on email reputation. It will use following online services to do a search;
- SpamCop
- SPAMHAUS
- Barracuda
- SenderSscore
- SenderBase
- https://www.ipvoid.com/ip-blacklist-check/
- https://www.virustotal.com/gui/home/url
Run Scripts
Here are three interesting projects we can use to check bulk ip addresses' reputation:- http://www.tekdefense.com/automater/
- https://github.com/clairmont32/VirusTotal-Tools
- https://github.com/Gajasurve/Blacklister-IP/blob/master/Bulk_check.py
[root@linux-centos-client1 ~]# yum install git
[root@linux-centos-client1 ~]# rm -r -d -f TekDefense-Automater/
[root@linux-centos-client1 ~]# git clone https://github.com/1aN0rmus/TekDefense-Automater.git
Cloning into 'TekDefense-Automater'...
remote: Enumerating objects: 260, done.
remote: Total 260 (delta 0), reused 0 (delta 0), pack-reused 260
Receiving objects: 100% (260/260), 136.82 KiB | 0 bytes/s, done.
Resolving deltas: 100% (143/143), done.
[root@linux-centos-client1 ~]# ls
TekDefense-Automater
[root@linux-centos-client1 ~]# cd TekDefense-Automater/
[root@linux-centos-client1 TekDefense-Automater]# ls
Automater.py inputs.py outputs.py siteinfo.py tekdefense.xml
docs LICENSE README.md sites.xml utilities.py
[root@linux-centos-client1 TekDefense-Automater]# python Automater.py -h
Automater.py test.txt -o test.out -c test.csv -w test.html -d 10
[root@linux-centos-client1 TekDefense-Automater]# python Automater.py test.txt -o test.out -c test.csv -w test.html -d 10
If you are using Alpine linux OS, the command might be different. Please see some examples commands below:
$ sudo apk update
fetch https://dl-cdn.alpinelinux.org/alpine/v3.16/main/x86_64/APKINDEX.tar.gz
fetch https://dl-cdn.alpinelinux.org/alpine/v3.16/community/x86_64/APKINDEX.tar.gz
v3.16.2-203-g16a4499ea3 [https://dl-cdn.alpinelinux.org/alpine/v3.16/main]
v3.16.2-202-ge26245aea1 [https://dl-cdn.alpinelinux.org/alpine/v3.16/community]
OK: 17053 distinct packages available
[node1] (local) [email protected] ~
$ sudo apk add git
OK: 395 MiB in 156 packages
[node1] (local) [email protected] ~
$ git --version
git version 2.36.2
[node1] (local) [email protected] ~
$
Note: If you are using PWD (Play with docker), the copy shortcut key is ctrl+insert, paste is ctrl+shift+v or shift+insert.Use Python2 Docker to Run Automater Script
$ docker run -it -d frolvlad/alpine-python2
43e5aec794b00c10f262e446fd210532f72a73bea93fafb689b7dfbd9f95fb10
[node1] (local) [email protected] ~/TekDefense-Automater
$ docker ps
CONTAINER ID IMAGE COMMAND CREATED STATUS PORTS NAMES
43e5aec794b0 frolvlad/alpine-python2 "/bin/sh" 3 seconds ago Up 2 seconds thirsty_burnell
[node1] (local) [email protected] ~/TekDefense-Automater
$ docker exec -it thirsty_burnell /bin/bash
OCI runtime exec failed: exec failed: unable to start container process: exec: "/bin/bash": stat /bin/bash: no such file or directory: unknown
[node1] (local) [email protected] ~/TekDefense-Automater
$ docker exec -it thirsty_burnell pwd
/
[node1] (local) [email protected] ~/TekDefense-Automater
$ docker exec -it thirsty_burnell sh
/ # python2
Python 2.7.18 (default, Oct 16 2021, 08:19:50)
[GCC 10.3.1 20210921] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> / # apk update fetch https://dl-cdn.alpinelinux.org/alpine/v3.15/main/x86_64/APKINDEX.tar.gz fetch https://dl-cdn.alpinelinux.org/alpine/v3.15/community/x86_64/APKINDEX.tar.gz v3.15.6-79-g18b652f36d [https://dl-cdn.alpinelinux.org/alpine/v3.15/main] v3.15.6-75-g2ba602a0c7 [https://dl-cdn.alpinelinux.org/alpine/v3.15/community] OK: 15866 distinct packages available / # apk add git (1/6) Installing ca-certificates (20220614-r0) (2/6) Installing brotli-libs (1.0.9-r5) (3/6) Installing nghttp2-libs (1.46.0-r0) (4/6) Installing libcurl (7.80.0-r3) (5/6) Installing pcre2 (10.40-r0) (6/6) Installing git (2.34.4-r0) Executing busybox-1.34.1-r5.trigger Executing ca-certificates-20220614-r0.trigger OK: 60 MiB in 29 packages / # git clone https://github.com/1aN0rmus/TekDefense-Automater.git Cloning into 'TekDefense-Automater'... remote: Enumerating objects: 260, done. remote: Total 260 (delta 0), reused 0 (delta 0), pack-reused 260 Receiving objects: 100% (260/260), 136.83 KiB | 5.95 MiB/s, done. Resolving deltas: 100% (143/143), done. / # cd TekDefense-Automater/ /TekDefense-Automater # vi test.txt /TekDefense-Automater # python Automater.py test.txt -o test.out -c test.csv -w test.html -d 10 Traceback (most recent call last): File "Automater.py", line 40, in <module> from siteinfo import SiteFacade, Site File "/TekDefense-Automater/siteinfo.py", line 28, in <module> import requests ImportError: No module named requests /TekDefense-Automater # pip install requests DEPRECATION: Python 2.7 reached the end of its life on January 1st, 2020. Please upgrade your Python as Python 2.7 is no longer maintained. pip 21.0 will drop support for Python 2.7 in January 2021. More details about Python 2 support in pip can be found at https://pip.pypa.io/en/latest/development/release-process/#python-2-support pip 21.0 will remove support for this functionality. Collecting requests Downloading requests-2.27.1-py2.py3-none-any.whl (63 kB) |████████████████████████████████| 63 kB 2.2 MB/s Collecting urllib3<1.27,>=1.21.1 Downloading urllib3-1.26.12-py2.py3-none-any.whl (140 kB) |████████████████████████████████| 140 kB 22.4 MB/s Collecting certifi>=2017.4.17 Downloading certifi-2021.10.8-py2.py3-none-any.whl (149 kB) |████████████████████████████████| 149 kB 21.8 MB/s Collecting idna<3,>=2.5; python_version < "3" Downloading idna-2.10-py2.py3-none-any.whl (58 kB) |████████████████████████████████| 58 kB 4.8 MB/s Collecting chardet<5,>=3.0.2; python_version < "3" Downloading chardet-4.0.0-py2.py3-none-any.whl (178 kB) |████████████████████████████████| 178 kB 18.7 MB/s Installing collected packages: urllib3, certifi, idna, chardet, requests Successfully installed certifi-2021.10.8 chardet-4.0.0 idna-2.10 requests-2.27.1 urllib3-1.26.12 /TekDefense-Automater # python Automater.py test.txt -o test.out -c test.csv -w test.html -d 10
/TekDefense-Automater # python Automater.py test.txt
____________________ Results found for: 117.40.196.21 ____________________
No results found in the RTex DNS
No results found in the FNet URL
[+] VT ASN: No results found
[+] VT Country: No results found
[+] VT AS Owner: No results found
[+] VT pDNS: No results found
[+] VT Malware: No results found
[+] VT Mal URLs: No results found
[+] Blacklist from IPVoid: No results found
[+] ISP from IPvoid: No results found
[+] Country from IPVoid: No results found
[+] Malc0de Date: No results found
[+] Malc0de IP: No results found
[+] Malc0de Country: No results found
[+] Malc0de ASN: No results found
[+] Malc0de ASN Name: No results found
[+] Malc0de MD5: No results found
No results found in the RA Score
[+] FreeGeoIP Country Name: No results found
[+] FreeGeoIP Region Name: No results found
[+] FreeGeoIP City: No results found
[+] FreeGeoIP Zipcode: No results found
[+] FreeGeoIP Latitude: No results found
[+] FreeGeoIP Longitude: No results found
[+] SANS total target IPs seen: No results found
[+] SANS total packets blocked: No results found
[+] SANS last seen on: No results found
[+] SANS first seen on: No results found
No results found in the THIP
No results found in the TekHP
[+] ProjectHoneypot activity type: No results found
[+] ProjectHoneypot first mail received: No results found
[+] ProjectHoneypot last mail received: No results found
[+] ProjectHoneypot total mails received: No results found
[+] ProjectHoneypot spider first seen: No results found
[+] ProjectHoneypot spider last seen: No results found
[+] ProjectHoneypot spider sightings: No results found
[+] ProjectHoneypot user-agent sightings: No results found
[+] ProjectHoneypot first post on: No results found
[+] ProjectHoneypot last post on: No results found
[+] ProjectHoneypot form posts: No results found
[+] ProjectHoneypot first rule break on: No results found
[+] ProjectHoneypot last rule break on: No results found
[+] ProjectHoneypot rule break sightings: No results found
[+] ProjectHoneypot first dictionary attack on: No results found
[+] ProjectHoneypot last dictionary attack on: No results found
[+] ProjectHoneypot dictionary attack sightings: No results found
[+] ProjectHoneypot harvester first seen: No results found
[+] ProjectHoneypot harvester last seen: No results found
[+] ProjectHoneypot harvester sightings: No results found
[+] ProjectHoneypot harvester results: No results found
____________________ Results found for: 37.192.170.224 ____________________
No results found in the RTex DNS
No results found in the FNet URL
[+] VT ASN: No results found
[+] VT Country: No results found
[+] VT AS Owner: No results found
[+] VT pDNS: No results found
[+] VT Malware: No results found
[+] VT Mal URLs: No results found
[+] Blacklist from IPVoid: No results found
[+] ISP from IPvoid: No results found
[+] Country from IPVoid: No results found
[+] Malc0de Date: No results found
[+] Malc0de IP: No results found
[+] Malc0de Country: No results found
[+] Malc0de ASN: No results found
[+] Malc0de ASN Name: No results found
[+] Malc0de MD5: No results found
No results found in the RA Score
[+] FreeGeoIP Country Name: No results found
[+] FreeGeoIP Region Name: No results found
[+] FreeGeoIP City: No results found
[+] FreeGeoIP Zipcode: No results found
[+] FreeGeoIP Latitude: No results found
[+] FreeGeoIP Longitude: No results found
[+] SANS total target IPs seen: No results found
[+] SANS total packets blocked: No results found
[+] SANS last seen on: No results found
[+] SANS first seen on: No results found
No results found in the THIP
No results found in the TekHP
[+] ProjectHoneypot activity type: No results found
[+] ProjectHoneypot first mail received: No results found
[+] ProjectHoneypot last mail received: No results found
[+] ProjectHoneypot total mails received: No results found
[+] ProjectHoneypot spider first seen: approximately 2 years, 10 months, 4 weeks ago
[+] ProjectHoneypot spider last seen: within 2 years, 10 months, 4 weeks
[+] ProjectHoneypot spider sightings: 6 visit
[+] ProjectHoneypot user-agent sightings: seen with 1 user-agent(s)
[+] ProjectHoneypot first post on: No results found
[+] ProjectHoneypot last post on: No results found
[+] ProjectHoneypot form posts: No results found
[+] ProjectHoneypot first rule break on: No results found
[+] ProjectHoneypot last rule break on: No results found
[+] ProjectHoneypot rule break sightings: No results found
[+] ProjectHoneypot first dictionary attack on: No results found
[+] ProjectHoneypot last dictionary attack on: No results found
[+] ProjectHoneypot dictionary attack sightings: No results found
[+] ProjectHoneypot harvester first seen: No results found
[+] ProjectHoneypot harvester last seen: No results found
[+] ProjectHoneypot harvester sightings: No results found
[+] ProjectHoneypot harvester results: No results found
____________________ Results found for: 66.240.236.119 ____________________
No results found in the RTex DNS
No results found in the FNet URL
[+] VT ASN: No results found
[+] VT Country: No results found
[+] VT AS Owner: No results found
[+] VT pDNS: No results found
[+] VT Malware: No results found
[+] VT Mal URLs: No results found
[+] Blacklist from IPVoid: No results found
[+] ISP from IPvoid: No results found
[+] Country from IPVoid: No results found
[+] Malc0de Date: No results found
[+] Malc0de IP: No results found
[+] Malc0de Country: No results found
[+] Malc0de ASN: No results found
[+] Malc0de ASN Name: No results found
[+] Malc0de MD5: No results found
No results found in the RA Score
[+] FreeGeoIP Country Name: No results found
[+] FreeGeoIP Region Name: No results found
[+] FreeGeoIP City: No results found
[+] FreeGeoIP Zipcode: No results found
[+] FreeGeoIP Latitude: No results found
[+] FreeGeoIP Longitude: No results found
[+] SANS total target IPs seen: 1496
[+] SANS total packets blocked: 9910
[+] SANS last seen on: 2022-09-26
[+] SANS first seen on: 2021-09-11
No results found in the THIP
No results found in the TekHP
[+] ProjectHoneypot activity type: No results found
[+] ProjectHoneypot first mail received: No results found
[+] ProjectHoneypot last mail received: No results found
[+] ProjectHoneypot total mails received: No results found
[+] ProjectHoneypot spider first seen: approximately 5 years, 8 months, 3 weeks ago
[+] ProjectHoneypot spider last seen: within 2 weeks
[+] ProjectHoneypot spider sightings: 604 visit
[+] ProjectHoneypot user-agent sightings: seen with 5 user-agent(s)
[+] ProjectHoneypot first post on: No results found
[+] ProjectHoneypot last post on: No results found
[+] ProjectHoneypot form posts: No results found
[+] ProjectHoneypot first rule break on: No results found
[+] ProjectHoneypot last rule break on: No results found
[+] ProjectHoneypot rule break sightings: No results found
[+] ProjectHoneypot first dictionary attack on: No results found
[+] ProjectHoneypot last dictionary attack on: No results found
[+] ProjectHoneypot dictionary attack sightings: No results found
[+] ProjectHoneypot harvester first seen: No results found
[+] ProjectHoneypot harvester last seen: No results found
[+] ProjectHoneypot harvester sightings: No results found
[+] ProjectHoneypot harvester results: No results found
____________________ Results found for: 70.119.165.198 ____________________
No results found in the RTex DNS
No results found in the FNet URL
[+] VT ASN: No results found
[+] VT Country: No results found
[+] VT AS Owner: No results found
[+] VT pDNS: No results found
[+] VT Malware: No results found
[+] VT Mal URLs: No results found
[+] Blacklist from IPVoid: No results found
[+] ISP from IPvoid: No results found
[+] Country from IPVoid: No results found
[+] Malc0de Date: No results found
[+] Malc0de IP: No results found
[+] Malc0de Country: No results found
[+] Malc0de ASN: No results found
[+] Malc0de ASN Name: No results found
[+] Malc0de MD5: No results found
No results found in the RA Score
[+] FreeGeoIP Country Name: No results found
[+] FreeGeoIP Region Name: No results found
[+] FreeGeoIP City: No results found
[+] FreeGeoIP Zipcode: No results found
[+] FreeGeoIP Latitude: No results found
[+] FreeGeoIP Longitude: No results found
[+] SANS total target IPs seen: No results found
[+] SANS total packets blocked: No results found
[+] SANS last seen on: No results found
[+] SANS first seen on: No results found
No results found in the THIP
No results found in the TekHP
[+] ProjectHoneypot activity type: No results found
[+] ProjectHoneypot first mail received: No results found
[+] ProjectHoneypot last mail received: No results found
[+] ProjectHoneypot total mails received: No results found
[+] ProjectHoneypot spider first seen: No results found
[+] ProjectHoneypot spider last seen: No results found
[+] ProjectHoneypot spider sightings: No results found
[+] ProjectHoneypot user-agent sightings: No results found
[+] ProjectHoneypot first post on: No results found
[+] ProjectHoneypot last post on: No results found
[+] ProjectHoneypot form posts: No results found
[+] ProjectHoneypot first rule break on: No results found
[+] ProjectHoneypot last rule break on: No results found
[+] ProjectHoneypot rule break sightings: No results found
[+] ProjectHoneypot first dictionary attack on: No results found
[+] ProjectHoneypot last dictionary attack on: No results found
[+] ProjectHoneypot dictionary attack sightings: No results found
[+] ProjectHoneypot harvester first seen: No results found
[+] ProjectHoneypot harvester last seen: No results found
[+] ProjectHoneypot harvester sightings: No results found
[+] ProjectHoneypot harvester results: No results found
____________________ Results found for: 99.203.86.107 ____________________
No results found in the RTex DNS
No results found in the FNet URL
[+] VT ASN: No results found
[+] VT Country: No results found
[+] VT AS Owner: No results found
[+] VT pDNS: No results found
[+] VT Malware: No results found
[+] VT Mal URLs: No results found
[+] Blacklist from IPVoid: No results found
[+] ISP from IPvoid: No results found
[+] Country from IPVoid: No results found
[+] Malc0de Date: No results found
[+] Malc0de IP: No results found
[+] Malc0de Country: No results found
[+] Malc0de ASN: No results found
[+] Malc0de ASN Name: No results found
[+] Malc0de MD5: No results found
No results found in the RA Score
[+] FreeGeoIP Country Name: No results found
[+] FreeGeoIP Region Name: No results found
[+] FreeGeoIP City: No results found
[+] FreeGeoIP Zipcode: No results found
[+] FreeGeoIP Latitude: No results found
[+] FreeGeoIP Longitude: No results found
[+] SANS total target IPs seen: No results found
[+] SANS total packets blocked: No results found
[+] SANS last seen on: No results found
[+] SANS first seen on: No results found
No results found in the THIP
No results found in the TekHP
[+] ProjectHoneypot activity type: No results found
[+] ProjectHoneypot first mail received: No results found
[+] ProjectHoneypot last mail received: No results found
[+] ProjectHoneypot total mails received: No results found
[+] ProjectHoneypot spider first seen: No results found
[+] ProjectHoneypot spider last seen: No results found
[+] ProjectHoneypot spider sightings: No results found
[+] ProjectHoneypot user-agent sightings: No results found
[+] ProjectHoneypot first post on: No results found
[+] ProjectHoneypot last post on: No results found
[+] ProjectHoneypot form posts: No results found
[+] ProjectHoneypot first rule break on: No results found
[+] ProjectHoneypot last rule break on: No results found
[+] ProjectHoneypot rule break sightings: No results found
[+] ProjectHoneypot first dictionary attack on: No results found
[+] ProjectHoneypot last dictionary attack on: No results found
[+] ProjectHoneypot dictionary attack sightings: No results found
[+] ProjectHoneypot harvester first seen: No results found
[+] ProjectHoneypot harvester last seen: No results found
[+] ProjectHoneypot harvester sightings: No results found
[+] ProjectHoneypot harvester results: No results found
____________________ Results found for: 99.203.87.35 ____________________
No results found in the RTex DNS
No results found in the FNet URL
[+] VT ASN: No results found
[+] VT Country: No results found
[+] VT AS Owner: No results found
[+] VT pDNS: No results found
[+] VT Malware: No results found
[+] VT Mal URLs: No results found
[+] Blacklist from IPVoid: No results found
[+] ISP from IPvoid: No results found
[+] Country from IPVoid: No results found
[+] Malc0de Date: No results found
[+] Malc0de IP: No results found
[+] Malc0de Country: No results found
[+] Malc0de ASN: No results found
[+] Malc0de ASN Name: No results found
[+] Malc0de MD5: No results found
No results found in the RA Score
[+] FreeGeoIP Country Name: No results found
[+] FreeGeoIP Region Name: No results found
[+] FreeGeoIP City: No results found
[+] FreeGeoIP Zipcode: No results found
[+] FreeGeoIP Latitude: No results found
[+] FreeGeoIP Longitude: No results found
[+] SANS total target IPs seen: No results found
[+] SANS total packets blocked: No results found
[+] SANS last seen on: No results found
[+] SANS first seen on: No results found
No results found in the THIP
No results found in the TekHP
[+] ProjectHoneypot activity type: No results found
[+] ProjectHoneypot first mail received: No results found
[+] ProjectHoneypot last mail received: No results found
[+] ProjectHoneypot total mails received: No results found
[+] ProjectHoneypot spider first seen: No results found
[+] ProjectHoneypot spider last seen: No results found
[+] ProjectHoneypot spider sightings: No results found
[+] ProjectHoneypot user-agent sightings: No results found
[+] ProjectHoneypot first post on: No results found
[+] ProjectHoneypot last post on: No results found
[+] ProjectHoneypot form posts: No results found
[+] ProjectHoneypot first rule break on: No results found
[+] ProjectHoneypot last rule break on: No results found
[+] ProjectHoneypot rule break sightings: No results found
[+] ProjectHoneypot first dictionary attack on: No results found
[+] ProjectHoneypot last dictionary attack on: No results found
[+] ProjectHoneypot dictionary attack sightings: No results found
[+] ProjectHoneypot harvester first seen: No results found
[+] ProjectHoneypot harvester last seen: No results found
[+] ProjectHoneypot harvester sightings: No results found
[+] ProjectHoneypot harvester results: No results found
/TekDefense-Automater #
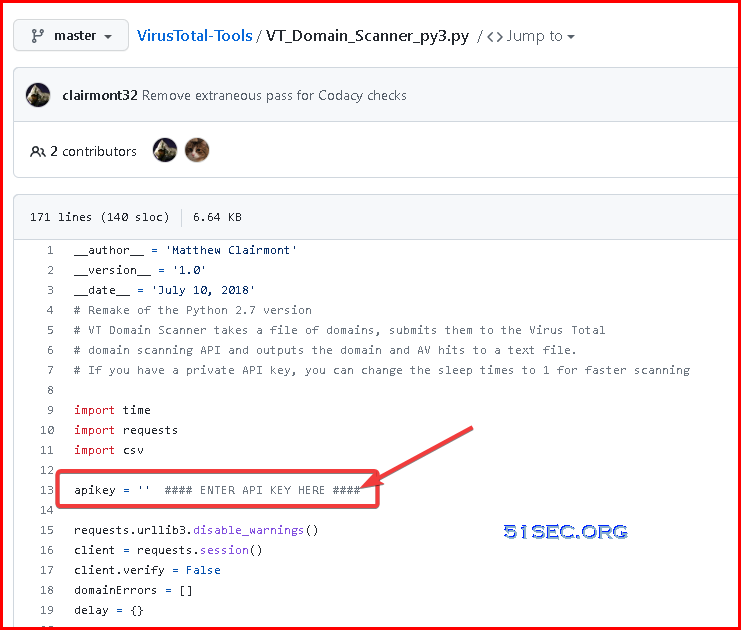
Run VirusTotal-Tools/VT_Domain_Scanner_py3.py
$ git clone https://github.com/clairmont32/VirusTotal-Tools
Cloning into 'VirusTotal-Tools'...
remote: Enumerating objects: 240, done.
remote: Counting objects: 100% (27/27), done.
remote: Compressing objects: 100% (23/23), done.
remote: Total 240 (delta 6), reused 0 (delta 0), pack-reused 213
Receiving objects: 100% (240/240), 7.32 MiB | 34.52 MiB/s, done.
Resolving deltas: 100% (97/97), done.
[node1] (local) [email protected] ~
$ cd VirusTotal-Tools/
[node1] (local) [email protected] ~/VirusTotal-Tools
$ python3 VT_Domain_Scanner_py3.py
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:46: SyntaxWarning: "is not" with a literal. Did you mean "!="?
if jsonResponse['response_code'] is not 1:
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:100: SyntaxWarning: "is" with a literal. Did you mean "=="?
if jsonResponse['response_code'] is 0:
Traceback (most recent call last):
File "/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py", line 10, in <module>
import requests
ModuleNotFoundError: No module named 'requests'
[node1] (local) [email protected] ~/VirusTotal-Tools
$ pip install requests
Collecting requests
Downloading requests-2.28.1-py3-none-any.whl (62 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 62.8/62.8 kB 10.0 MB/s eta 0:00:00
Collecting charset-normalizer<3,>=2
Downloading charset_normalizer-2.1.1-py3-none-any.whl (39 kB)
Collecting idna<4,>=2.5
Downloading idna-3.4-py3-none-any.whl (61 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 61.5/61.5 kB 12.8 MB/s eta 0:00:00
Collecting urllib3<1.27,>=1.21.1
Downloading urllib3-1.26.12-py2.py3-none-any.whl (140 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 140.4/140.4 kB 21.8 MB/s eta 0:00:00
Collecting certifi>=2017.4.17
Downloading certifi-2022.9.24-py3-none-any.whl (161 kB)
━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━━ 161.1/161.1 kB 29.9 MB/s eta 0:00:00
Installing collected packages: urllib3, idna, charset-normalizer, certifi, requests
Successfully installed certifi-2022.9.24 charset-normalizer-2.1.1 idna-3.4 requests-2.28.1 urllib3-1.26.12
WARNING: Running pip as the 'root' user can result in broken permissions and conflicting behaviour with the system package manager. It is recommended to use a virtual environment instead: https://pip.pypa.io/warnings/venv
[node1] (local) [email protected] ~/VirusTotal-Tools
$ python3 VT_Domain_Scanner_py3.py
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:46: SyntaxWarning: "is not" with a literal. Did you mean "!="?
if jsonResponse['response_code'] is not 1:
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:100: SyntaxWarning: "is" with a literal. Did you mean "=="?
if jsonResponse['response_code'] is 0:
Please ensure the file is closed.
[Errno 2] No such file or directory: 'domains.txt'
[node1] (local) [email protected] ~/VirusTotal-Tools
/TekDefense-Automater # cat test.txt
54.179.131.230
185.220.101.54
117.149.0.14
112.11.242.201
45.185.6.35
185.183.158.57
2600:1f18:d7f:1900:4909:f65c:c131:aa6b
/TekDefense-Automater # exit
[node1] (local) [email protected] ~/VirusTotal-Tools
$ vi domains.txt
[node1] (local) [email protected] ~/VirusTotal-Tools
$ python3 VT_Domain_Scanner_py3.py
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:46: SyntaxWarning: "is not" with a literal. Did you mean "!="?
if jsonResponse['response_code'] is not 1:
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:100: SyntaxWarning: "is" with a literal. Did you mean "=="?
if jsonResponse['response_code'] is 0:
54[.]179[.]131[.]230
<Response [403]>
185[.]220[.]101[.]54
<Response [403]>
117[.]149[.]0[.]14
<Response [403]>
112[.]11[.]242[.]201
<Response [403]>
45[.]185[.]6[.]35
<Response [403]>
185[.]183[.]158[.]57
<Response [403]>
2600:1f18:d7f:1900:4909:f65c:c131:aa6b
<Response [403]>
[node1] (local) [email protected] ~/VirusTotal-Tools
$ ls
LICENSE VT_Domain_Scanner_py3.exe VT_Domain_Scanner_py3_CLI_version.py domains.txt
README.md VT_Domain_Scanner_py3.py VT_Hash_Search.py results.csv
[node1] (local) [email protected] ~/VirusTotal-Tools
$ vi VT_Domain_Scanner_py3.py
[node1] (local) [email protected] ~/VirusTotal-Tools
$ python3 VT_Domain_Scanner_py3.py
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:46: SyntaxWarning: "is not" with a literal. Did you mean "!="?
if jsonResponse['response_code'] is not 1:
/root/VirusTotal-Tools/VT_Domain_Scanner_py3.py:100: SyntaxWarning: "is" with a literal. Did you mean "=="?
if jsonResponse['response_code'] is 0:
54[.]179[.]131[.]230
<Response [200]>
54[.]179[.]131[.]230 was scanned successfully.
Report is ready for 54[.]179[.]131[.]230
185[.]220[.]101[.]54
<Response [200]>
185[.]220[.]101[.]54 was scanned successfully.
Report is ready for 185[.]220[.]101[.]54
117[.]149[.]0[.]14
<Response [200]>
117[.]149[.]0[.]14 was scanned successfully.
Report is ready for 117[.]149[.]0[.]14
112[.]11[.]242[.]201
<Response [200]>
112[.]11[.]242[.]201 was scanned successfully.
Report is ready for 112[.]11[.]242[.]201
45[.]185[.]6[.]35
<Response [200]>
45[.]185[.]6[.]35 was scanned successfully.
Report is ready for 45[.]185[.]6[.]35
185[.]183[.]158[.]57
<Response [200]>
185[.]183[.]158[.]57 was scanned successfully.
Report is ready for 185[.]183[.]158[.]57
2600:1f18:d7f:1900:4909:f65c:c131:aa6b
<Response [200]>
There was an error submitting the domain for scanning.
Invalid URL, the scan request was not queued
There was an error submitting the domain for scanning.
There was an error when scanning 2600:1f18:d7f:1900:4909:f65c:c131:aa6b. Adding domain to error list....
There were 1 errors scanning domains
['2600:1f18:d7f:1900:4909:f65c:c131:aa6b']
[node1] (local) [email protected] ~/VirusTotal-Tools
$ more results.csv
Scan Date,Domain,# of Positive Scans,# of Total Scans,Permalink
2020-06-13 18:40:30,54[.]179[.]131[.]230,0,79,https://www.virustotal.com/gui/url/a6be98ea89ea1fbe029e74d1b7d6e5b245f0769bd91e79c3d9d9d867f065b26f/detection/u-a6be98
ea89ea1fbe029e74d1b7d6e5b245f0769bd91e79c3d9d9d867f065b26f-1592073630
2022-09-25 17:56:57,185[.]220[.]101[.]54,10,88,https://www.virustotal.com/gui/url/ec895a3b96ac0b00ea1ca399d126e6fcf9066f720fc364b5550bf8d38e52b116/detection/u-ec895
a3b96ac0b00ea1ca399d126e6fcf9066f720fc364b5550bf8d38e52b116-1664128617
2022-09-18 13:01:53,117[.]149[.]0[.]14,1,88,https://www.virustotal.com/gui/url/44807e29e82f7a33bdb08ee2bba57985c6b4b78380e308abc61404122db994f4/detection/u-44807e29
e82f7a33bdb08ee2bba57985c6b4b78380e308abc61404122db994f4-1663506113
2022-09-26 13:01:45,112[.]11[.]242[.]201,2,88,https://www.virustotal.com/gui/url/fec3bab04a07fa515a6cc9d072d029e6c047a2eb02f4aa7e429203418120f6fd/detection/u-fec3ba
b04a07fa515a6cc9d072d029e6c047a2eb02f4aa7e429203418120f6fd-1664197305
2022-09-26 17:14:23,45[.]185[.]6[.]35,4,88,https://www.virustotal.com/gui/url/ee2c58572262408b77a73309bffbce0b08648a89395455ac864eb26593236cde/detection/u-ee2c58572
262408b77a73309bffbce0b08648a89395455ac864eb26593236cde-1664212463
2022-09-26 17:14:53,185[.]183[.]158[.]57,2,88,https://www.virustotal.com/gui/url/f30cbb07e73d3fe3bb68e140e124bff245f8e2ca6fc4b6aeb182f141e8b399e6/detection/u-f30cbb
07e73d3fe3bb68e140e124bff245f8e2ca6fc4b6aeb182f141e8b399e6-1664212493
YouTube Video
References
- https://github.com/Gajasurve/Blacklister-IP/blob/master/Bulk_check.py
- http://www.tekdefense.com/automater/
- https://github.com/clairmont32/VirusTotal-Tools
- https://scamalytics.com/ - scamalytics - stop scammers automatically using API







Please help to fix this error, do let me know what parameter to be change.
ReplyDeleteroot@MUM-G9SG453:~/TekDefense-Automater# python Automater.py 111.231.227.249
Traceback (most recent call last):
File "Automater.py", line 40, in
from siteinfo import SiteFacade, Site
File "/root/TekDefense-Automater/siteinfo.py", line 28, in
import requests
ImportError: No module named requests
module "Requests" is not installed by default by python. Follow this https://stackoverflow.com/a/17309309 to install it.
ReplyDelete