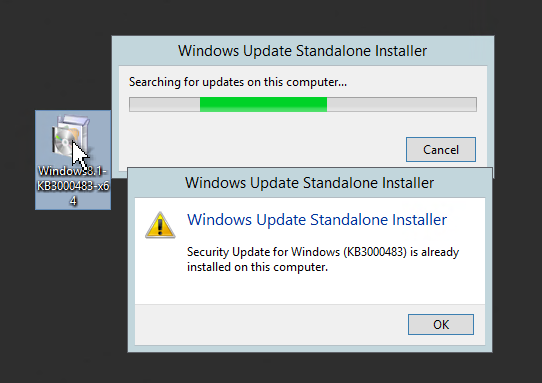
 |
| Applied Patch |
Microsoft Group Policy Remote Code Execution Vulnerability (MS15-011) - Microsoft Internet Explorer Cumulative Security Update (MS15-124)
The point is , there are extra additional steps you will have to do to remedy those two vulnerabilities.
Microsoft Group Policy Remote Code Execution Vulnerability (MS15-011) Remediation
For Microsoft Group Policy Remote Code Execution Vulnerability (MS15-011), based on KB MS15-011: Vulnerability in Group Policy could allow remote code execution: February 10, 2015, Microsoft recommend that all NETLOGON and SYSVOL shares be configured to require both mutual authentication and integrity in order to help secure Group Policy against spoofing and tampering attacks that can be leveraged to achieve remote code execution.
Hardened UNC paths
| Value name | Value |
|---|---|
| \\*\NETLOGON | RequireMutualAuthentication=1, RequireIntegrity=1 |
| \\*\SYSVOL | RequireMutualAuthentication=1, RequireIntegrity=1 |
Microsoft Group Policy Remote Code Execution Vulnerability (MS15-011) Remediation
Since Qualys result clear show there are some registry key missing, the easiest way is to add this key in manually after you applied the patch.
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ALLOW_USER32_EXCEPTION_HANDLER_HARDENING iexplore.exe is missing.
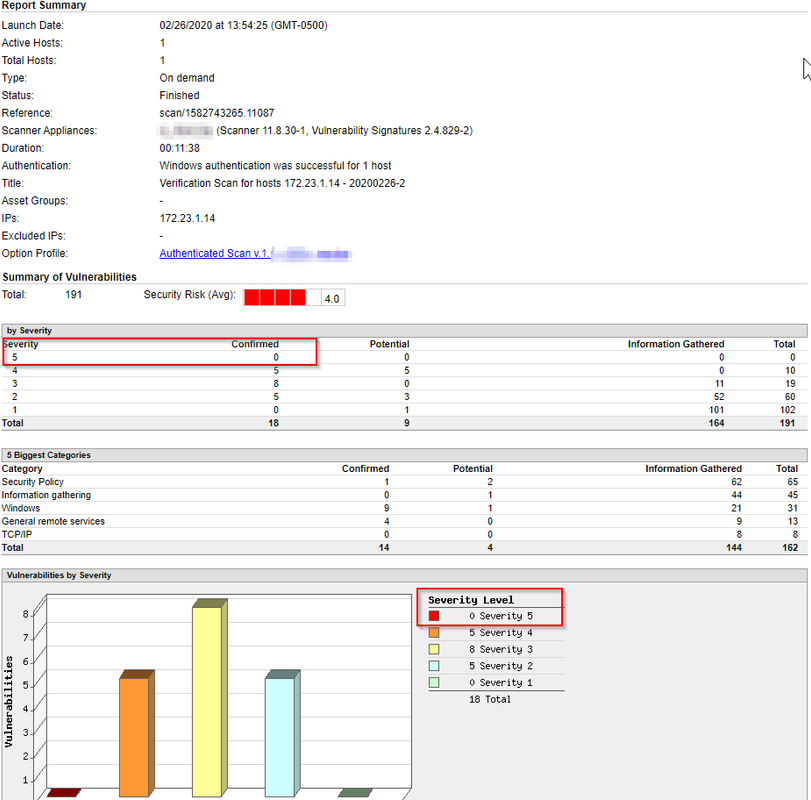
After two manual additional changes done to the system, the scan results shows clean on Severity 5 findings.
Appendixes
 5 5 | Microsoft Group Policy Remote Code Execution Vulnerability (MS15-011) |
- QID:
- 91017
- Category:
- Windows
- CVE ID:
- CVE-2015-0008
- Vendor Reference
- MS15-011
- Bugtraq ID:
- 72477
- Service Modified:
- 02/05/2020
- User Modified:
- -
- Edited:
- No
- PCI Vuln:
- Yes
- THREAT:
- The security update addresses the vulnerability by improving how domain-configured systems connect to domain controllers prior to Group Policy accepting configuration data.
This security update is rated Critical for all supported editions of Windows Server 2003, Windows Vista, Windows Server 2008, Windows 7, Windows Server 2008 R2, Windows 8, Windows Server 2012, Windows RT, Windows 8.1, Windows Server 2012 R2, and Windows RT 8.1Note: There is no update released for Windows 2003. This vulnerability requires that a user connect their computer to an untrusted network such as a Wi-Fi hotspot in a coffee shop; therefore, workstations that are connected to an untrusted network are most at risk from this vulnerability.QID Detection Logic (Authenticated):
Operating Systems: Windows Vista, Windows Server 2008, Windows Server 2008 R2, Windows 7, Windows 8, Windows RT, Windows RT 8.1, Windows Server 2012
This QID checks for the file version of %windir%\system32\gpsvc.dll
The following KBs are checked:
The patch version of 6.0.6002.19279 (KB3000483)
The patch version of 6.0.6002.23588 (KB3000483)
The patch version of 6.1.7601.18711 (KB3000483)
The patch version of 6.1.7601.22917 (KB3000483)
The patch version of 6.2.9200.17225 (KB3000483)
The patch version of 6.2.9200.21339 (KB3000483)
The patch version of 6.3.9600.17630 (KB3000483)
In addition, Registry Key - HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy\History - checks if system is connected to the domain. If yes, then following Minimum recommended settings mentioned in KB3000483 are checked:-
1. Registry key - HKLM\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths with value "Netlogon" contains data - RequireMutualAuthentication=1, RequireIntegrity=1
2. Registry key - HKLM\SOFTWARE\Policies\Microsoft\Windows\NetworkProvider\HardenedPaths with value "Sysvol" contains data - RequireMutualAuthentication=1, RequireIntegrity=1Value Name Value \\*\NETLOGON RequireMutualAuthentication=1, RequireIntegrity=1 \\*\SYSVOL RequireMutualAuthentication=1, RequireIntegrity=1
- IMPACT:
- The vulnerability could allow remote code execution if an attacker convinces a user with a domain-configured system to connect to an attacker-controlled network.
- SOLUTION:
- Refer to MS15-011to obtain further patch information.
In some environments, to be completely protected from the vulnerability, additional configuration by a system administrator is required in addition to deploying this security update. Refer to Microsoft Knowledge Base Article KB3000483 to obtain further information.Patch:
Following are links for downloading patches to fix the vulnerabilities: - COMPLIANCE:
- Not Applicable
- EXPLOITABILITY:
-
- Reference:
- CVE-2015-0008
- Description:
- Microsoft Windows Group Policy Remote Code Execution Vulnerability Exploit (MS15-011) - Core Security Category : Exploits/Remote
- Reference:
- CVE-2015-0008
- Description:
- Microsoft Windows Server 2012 - 'Group Policy' Remote Code Execution - The Exploit-DB Ref : 47558
- Link:
- http://www.exploit-db.com/exploits/47558
- Reference:
- CVE-2015-0008
- Description:
- Microsoft Windows Group Policy Remote Code Execution Vulnerability Exploit (MS15-011) - MWR InfoSecurity
- Link:
- https://labs.mwrinfosecurity.com/blog/practically-exploiting-ms15-014-and-ms15-011/
- ASSOCIATED MALWARE:
- There is no malware information for this vulnerability.
- RESULTS:
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Group Policy\History DCName exists.
Minimum recommended settings for MS15-011 mentioned in KB3000483 is not applied on the target.
 5 5 | Microsoft Internet Explorer Cumulative Security Update (MS15-124) |
- QID:
- 100269
- Category:
- Internet Explorer
- CVE ID:
- CVE-2015-6083 CVE-2015-6134 CVE-2015-6135 CVE-2015-6136 CVE-2015-6138 CVE-2015-6139 CVE-2015-6140 CVE-2015-6141 CVE-2015-6142 CVE-2015-6143 CVE-2015-6144 CVE-2015-6145 CVE-2015-6146 CVE-2015-6147 CVE-2015-6148 CVE-2015-6149 CVE-2015-6150 CVE-2015-6151 CVE-2015-6152 CVE-2015-6153 CVE-2015-6154 CVE-2015-6155 CVE-2015-6156 CVE-2015-6157 CVE-2015-6158 CVE-2015-6159 CVE-2015-6160 CVE-2015-6161 CVE-2015-6162 CVE-2015-6164
- Vendor Reference
- MS15-124
- Bugtraq ID:
- -
- Service Modified:
- 11/29/2019
- User Modified:
- -
- Edited:
- No
- PCI Vuln:
- Yes
- THREAT:
- Microsoft Internet Explorer is a graphical web browser developed by Microsoft and included as part of the Microsoft Windows operating systems.
This security update resolves multiple vulnerabilities in Internet Explorer. The most severe of the vulnerabilities could allow remote code execution if a user views a specially crafted webpage using Internet Explorer.Update (8/15/2017): The QID has been updated to additionally check for MS15-135 (For OS prior to Windows 10) and check for "FEATURE_ALLOW_USER32_EXCEPTION_HANDLER_HARDENING" as described in the fix for CVE-2015-6161 in MS15-124QID Detection Logic:
Operating Systems: Windows Vista, Windows Server 2008 SP2, Windows 7 SP1, Windows Server 2008 R2 SP1, Windows 8, Windows 8.1, Windows RT, Windows RT 8.1, Windows Server 2012, Windows Server 2012 R2, Windows 10 (build 1507 and 1511).
The QID checks if the host is running a vulnerable version of Internet Explorer with the help of the file %windir%\System32\mshtml.dll
The following KBs are checked:
The patch version of 7.0.6002.19537(KB3104002)
The patch version of 7.0.6002.23847(KB3104002)
The patch version of 8.0.6001.19705(KB3104002)
The patch version of 8.0.6001.23765(KB3104002)
The patch version of 8.0.6001.23952(KB3104002)
The patch version of 8.0.7601.19058(KB3104002)
The patch version of 8.0.7601.23262(KB3104002)
The patch version of 9.0.8112.16723(KB3104002)
The patch version of 9.0.8112.20838(KB3104002)
The patch version of 10.0.9200.17566(KB3104002)
The patch version of 10.0.9200.21684(KB3104002)
The patch version of 11.0.9600.18125(KB3104002)
The patch version of 11.0.10240.16603(KB3116869)
The patch version of 11.0.10586.20(KB3116900)The QID additionally checks if the patch for CVE-2015-6161 is enabled or not by check for:1) MS15-135 on Operating Systems before Windows 10:
Operating Systems: Windows Vista, Windows Server 2008 SP2, Windows 7 SP1, Windows Server 2008 R2 SP1, Windows 8, Windows 8.1, Windows RT, Windows RT 8.1, Windows Server 2012, Windows Server 2012 R2
the file version of %windir%\System32\win32k.sys
The patch version of 6.0.6002.19535(KB3109094)
The patch version of 6.0.6002.23845(KB3109094)
The patch version of 6.1.7601.19061(KB3109094)
The patch version of 6.1.7601.23265(KB3109094)
The patch version of 6.2.9200.17568(KB3109094)
The patch version of 6.2.9200.21687(KB3109094)
The patch version of 6.3.9600.18123(KB3109094)2) The following Registry keys are configured on all affected OS:
a)HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ALLOW_USER32_EXCEPTION_HANDLER_HARDENING with value 1
b)HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ALLOW_USER32_EXCEPTION_HANDLER_HARDENING with value 1 (64 bit only)Note: The QID has been updated to check for the additional steps required to enable fix for CVE-2015-6161 even when later updates than MS15-124 are applied. This is because the fix for CVE-2015-6161 is disabled by default and needs to be enabled manually even after applying latest updates on affected Operating Systems.Note (02/26/2018) : The QID has been updated to check for the additional steps required to enable fix for CVE-2015-6161 even when later updates than MS15-124 are applied. This is because the fix for CVE-2015-6161 is disabled by default and needs to be enabled manually even after applying latest updates on affected Operating Systems. - IMPACT:
- A remote, unauthenticated attacker could exploit these vulnerabilities to conduct cross-site scripting attacks, elevate their privileges, execute arbitrary code or cause a denial of service condition on the targeted system.
- SOLUTION:
- Customers are advised to refer to Microsoft Advisory MS15-124 for more details.
Patch:
Following are links for downloading patches to fix the vulnerabilities: - COMPLIANCE:
- Not Applicable
- EXPLOITABILITY:
-
- Reference:
- CVE-2015-6152
- Description:
- Microsoft Internet Explorer 11 - MSHTML!CObjectElement Use-After-Free (MS15-124) - The Exploit-DB Ref : 38972
- Link:
- http://www.exploit-db.com/exploits/38972
- ASSOCIATED MALWARE:
- There is no malware information for this vulnerability.
- RESULTS:
- HKLM\Software\Microsoft\Internet Explorer Version = 9.11.9600.19626
HKLM\SOFTWARE\Microsoft\Internet Explorer Version = 9.11.9600.19626
HKLM\SOFTWARE\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ALLOW_USER32_EXCEPTION_HANDLER_HARDENING iexplore.exe is missing.
HKLM\SOFTWARE\WOW6432Node\Microsoft\Internet Explorer\Main\FeatureControl\FEATURE_ALLOW_USER32_EXCEPTION_HANDLER_HARDENING iexplore.exe is missing.











No comments:
Post a Comment