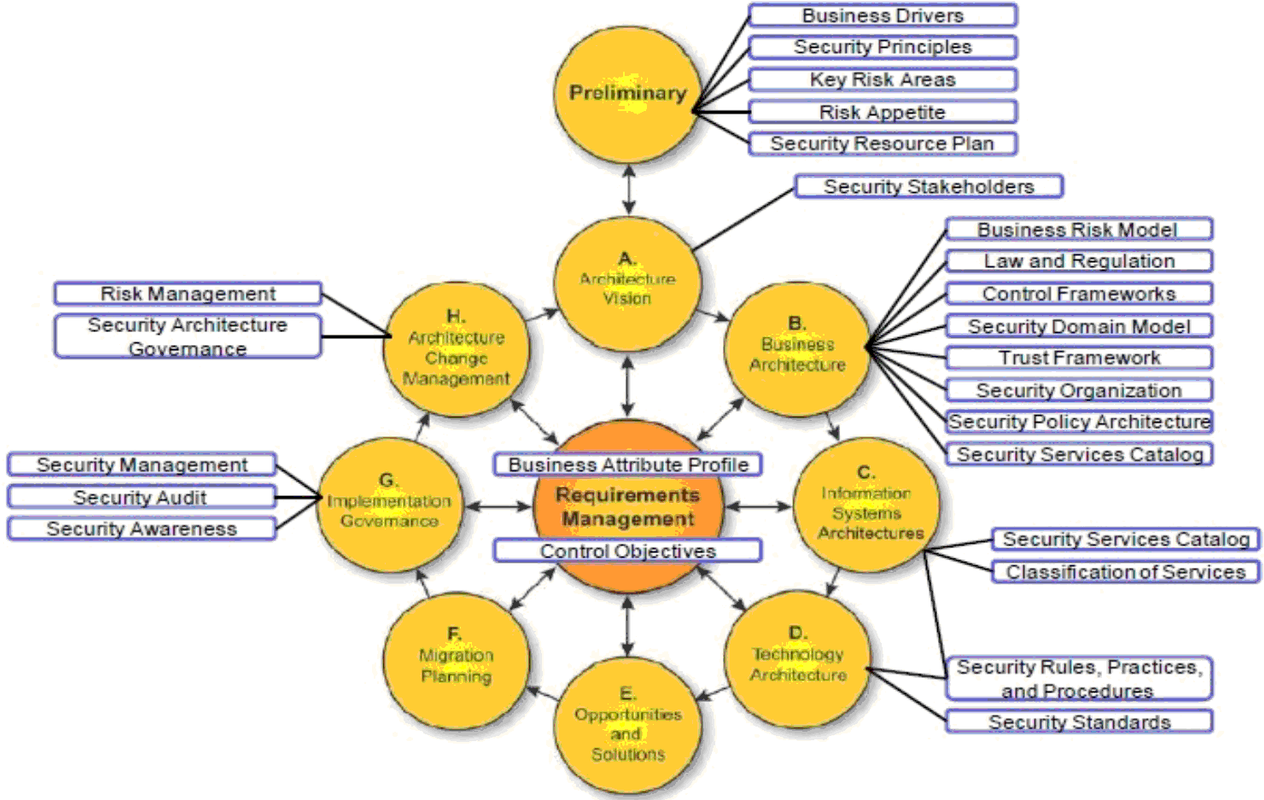
A Cyber Security Framework is a risk-based compilation of guidelines designed to help organizations assess current capabilities and draft a prioritized road map toward improved cyber security practices. (From Arnab Chattopadhaya 's Enterprise Security Architecture)
Related Posts:
- Canadian Cybersecurity and Privacy Framework
- [Cybersecurity Architecture] Policy / Standards / Procedures Framework with an Example
- Layered Security Architecture -Cyber Security Technology with NIST Cyber Security Framework
- Cyber Security Frameworks and Integrated with TOGAF
- EA (Enterprise Architecture) Framework Resources
Well Known Cyber Security Frameworks
• Sherwood Applied Business Security Architecture (SABSA)
• ISO/IEC 31000
• NIST SP 800-53: Security and Privacy Controls for Federal Information Systems and Organizations
• NIST SP 800-39: Risk Management Framework
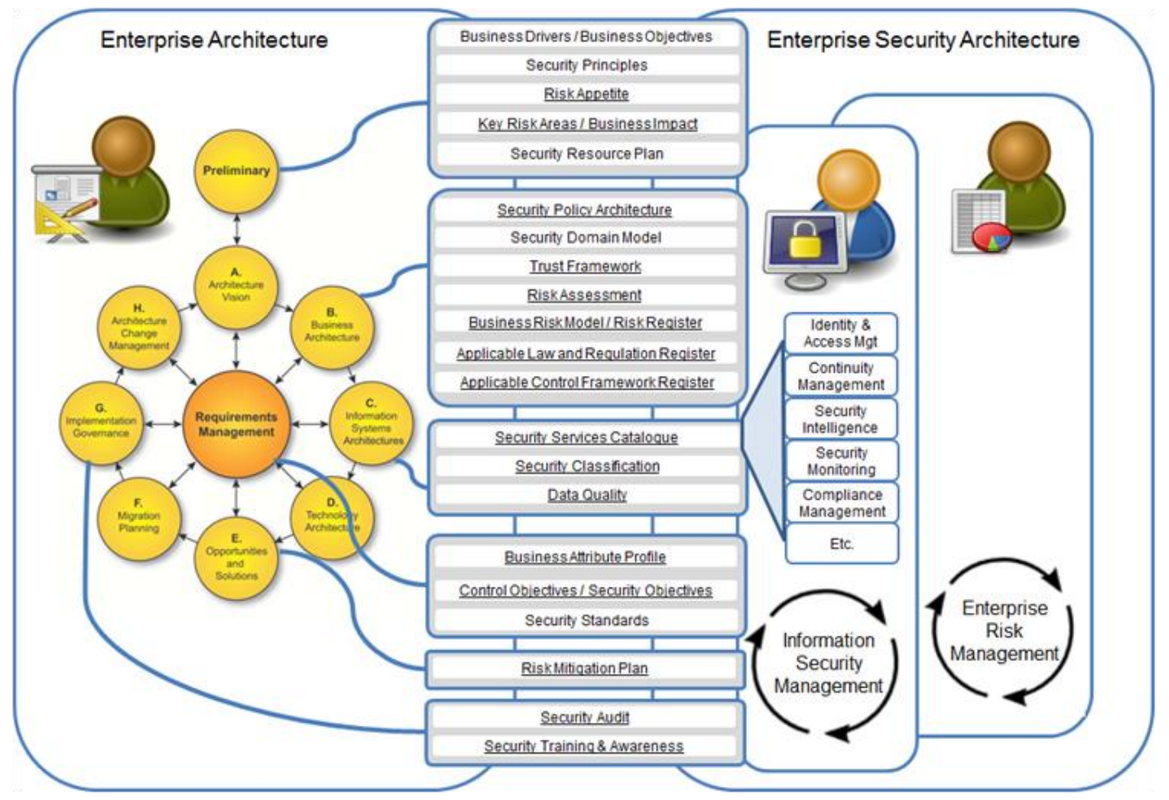 |
| Essential security and risk concepts and their position in the TOGAF ADM (Source: TOGAF Security Guide) |
Other standards / frameworks related to Cyber Security Frameworks
• COBIT• ITIL
• COSO
• Other Major IT Cyber Security Frameworks
-O-ESA
-O-ISM3
-Open Fair
SABSA Model
SABSA is a proven methodology for developing business-driven, risk and opportunity focused Security Architectures at both enterprise and solutions level that traceably support business objectives. It is also widely used for Information Assurance Architectures, Risk Management Frameworks, and to align and seamlessly integrate security and risk management into IT Architecture methods and frameworks.SABSA is a ‘Through-Life’ method and framework: it applies throughout the entire lifecycle from Business Requirements Engineering to management of the solutions delivered.
SABSA certification is widely requested by employers globally and is a mandatory requirement for Security Architects and Enterprise Architects alike in numerous large-scale and national financial sector bodies. SABSA is also widely referenced in other security and IT certification programmes and throughout the tertiary academic world.
• Comprises of six layers
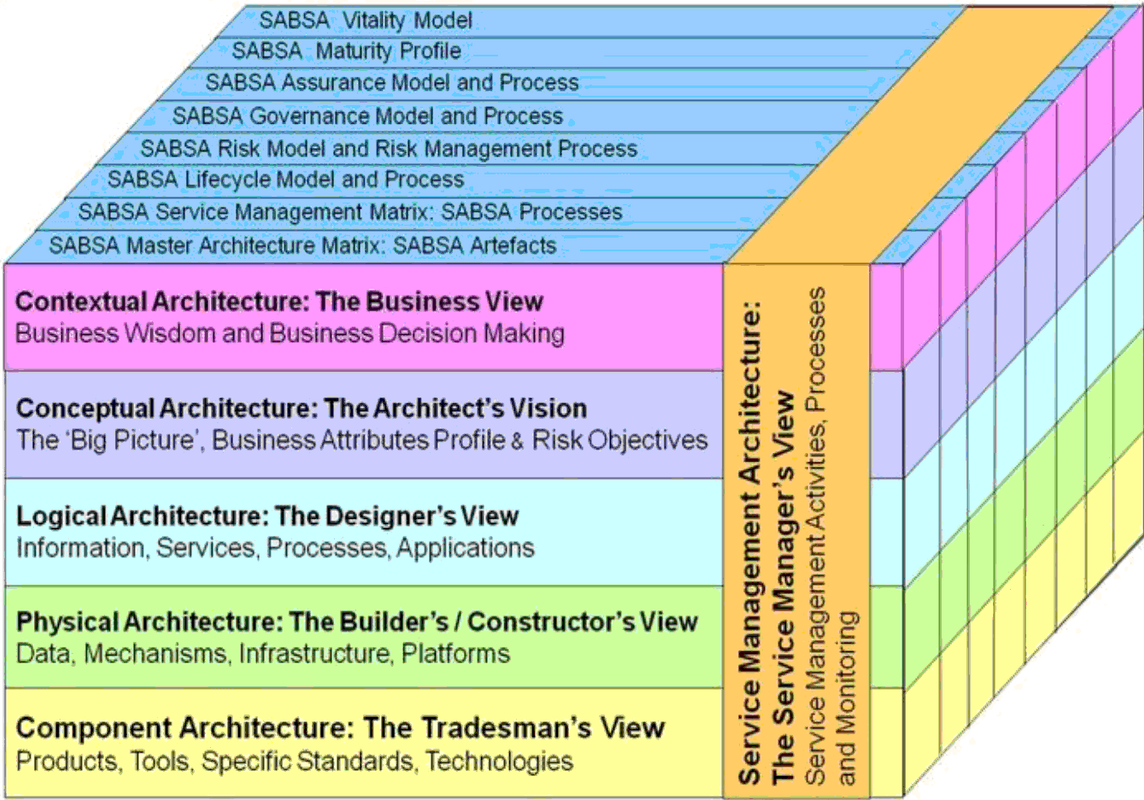 • Based on Zachman framework/taxonomy
• Based on Zachman framework/taxonomy• The Security Service Management Architecture has been placed vertically across the other five layers
– Security management issues arises in every horizontal layer
• Each horizontal layers are made of a series of vertical communication interrogatives
– What (Assets)
– Why (Motivation)
– How (Process and Technology)
– Who (People)
– Where (Location)
– When (Time)
SABSA Lifecycle
• Strategy and Planning
• Design
• Implement
• Manage and Measure
Reference: SABSA vs. TOGAF
How SABSA can be integrated with TOGAF
ISO27001 / ISO31000
How ISO 27001 Integrated with TOGAF
“ISO/IEC 27001:2013 is a standard that specifies the requirements for establishing, implementing, maintaining, and continually improving an information security management system within the context of the organization. This International Standard also includes requirements for the assessment and treatment of information security risks tailored to the needs of the organization.”In January 2016, the TOGAF Security Guide was published. It addresses security and risk management at a conceptual level, which matches with the way that TOGAF defines architecture. This enables the integration of both processes in the architecture. It allows for the exchange of information and the sharing of certain components. Thus, enterprise architecture and security architecture can co-exist and collaborate.
The TOGAF Security Guide is based on an enterprise security architecture that includes two successful standards, namely ISO 27001 (security management) and ISO 31000 (risk management). In line with ISO 31000, the definition of risk is broad and is close to that of 'uncertainty'. This means that risk can be positive or negative. The broad definition makes it possible to use it for (positive) business opportunities as well as (negative) security threats. The latter is, of course, the most common within IT-security.
ISO 31000:2009 sets out principles, a framework, and a process for the management of risk that are applicable to any type of organization in the public or private sector. It does not mandate a “one size fits all” approach, but rather emphasizes the fact that the management of risk must be tailored to the specific needs and structure of the particular organization. It has a related standard IEC 31010:2009 that describes examples of qualitative risk assessment methods.
PDCA - Plan , Do, Check Act
Content Coverage Differences from NIST CSF
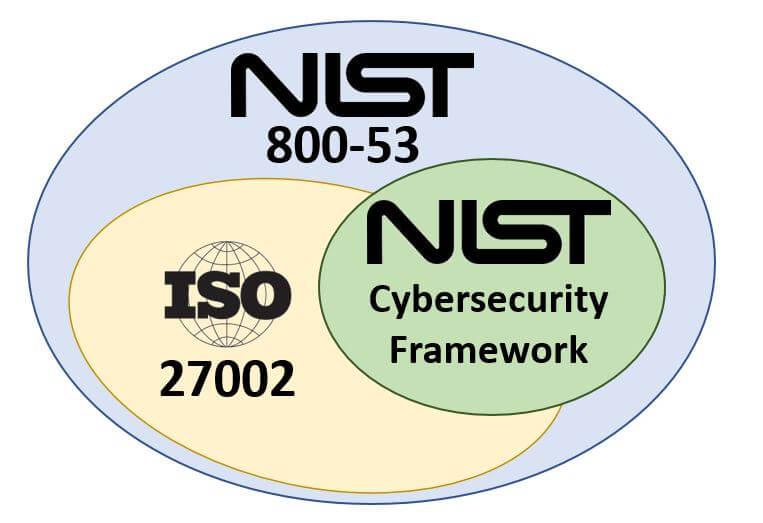 From A Content Perspective, NIST CSF < ISO 27002 < NIST 800-53 < Secure Controls Framework (from Compliance Forge page - NIST 800-53 vs ISO 27002 vs NIST Cybersecurity Framework):
From A Content Perspective, NIST CSF < ISO 27002 < NIST 800-53 < Secure Controls Framework (from Compliance Forge page - NIST 800-53 vs ISO 27002 vs NIST Cybersecurity Framework):- NIST Cybersecurity Framework (NIST CSF) covers a lot, but it is not inclusive of all ISO 27002 controls.
- ISO 27002 addresses most of what you need to comply with NIST CSF and a few other requirements.
- NIST 800-53 includes what ISO 27002 addresses, as well as a whole host of other requirements.
NIST CSF
This framework aims to help organizations in critical infrastructure sectors to reduce risk, and protect their critical infrastructure. The NIST Cybersecurity Framework groups security functions into these five areas: Identify, Protect, Detect, Respond, and Recover.Differences from NIST 800 and Other NIST Frameworks
While the Framework was written primarily by NIST, the same organization behind 800-53, there are several differences between them.- The Framework is more high-level in its scope compared to existing frameworks like NIST 800-53.It focuses on how to access and prioritize security functions, and references existing documents like NIST 800-53, COBIT 5, and ISO 27000 for more detail on how to implement specific controls and processes.This allows the Framework to be a much more concise document at 40 pages as opposed to NIST 800-53’s 460 pages.
- NIST 800-53 is a regulatory document, encompassing the processes and controls needed for a government-affiliated entity to comply with the FIPS 200 certification. In contrast, the Framework is voluntary for organizations and therefore allows more flexibility in its implementation.
800 : Computer Security Resource Center
800-39 : Managing Information Security Risk: Organization, Mission, and Information System View
800-53 : Security and Privacy Controls for Federal Information Systems and Organizations
800-61 : Computer Security Incident handling Guide- PDCP life cycle (Preparation, Detection & Analysis, Containment Eradication & Recovery, Post-incident Activity)
800-171: Protecting Unclassified Information in Nonfederal Information Systems and Organizations
COBIT
“COBIT 5 provides a comprehensive framework that assists enterprises in achieving their objectives for the governance and management of enterprise IT. Simply stated, it helps enterprises create optimal value from Information Technology (IT) by maintaining a balance between realizing benefits and optimizing risk levels and resource use. COBIT 5 for Information Security builds on the COBIT 5 framework in that it focuses on information security and provides more detailed and more practical guidance for information security professionals and other interested parties at all levels of the enterprise.”ITIL
The Information Technology Infrastructure Library is a customisable framework of best practices that promote quality computing services in the information technology (IT) sector. ITIL was originally created by a UK government agency Central Computer and Telecommunications Agency (CCTA) and is now adopted and used worldwide as a standard for best practice in provisioning IT Services.A component of ITIL—ITIL Security Management, based on ISO 17799—is of particular relevance to the application of the information security principles. The ITIL Security Management component is procedure based and includes ITIL standard processes such as service level, incident and change management processes. A key concept is that security should be perceived as a service and be incorporated into Service Level Agreements (SLAs).
COSO
The US Committee of Sponsoring Organizations (COSO) of the Treadway Commission published an internal control framework in 1994 which subsequently served as a basis for standards such as COBIT. Key concepts developed in this framework are prevalent in a number of contemporary risk management and corporate governance approaches. COSO requires that a formal risk assessment be performed to evaluate the internal and external factors that impact an organisation's performance. The results of the risk assessment will determine the controls that need to be implemented. COSO focuses on financial controls but also has implications for functions like information security.O-ESA
The Open Enterprise Security Architecture (O-ESA) standard, published by The Open Group in 2011, is a reference Security Architecture and guide to building a security program. While it contains useful information on information security governance, security principles, and technology components and services needed in Security Architectures, this reference architecture can be also applied to support the implementation of security and risk in Enterprise Architectures using the TOGAF standard.O-ISM3
The Open Information Security Management Maturity Model (O-ISM3) standard, published by The Open Group in 2011, describes a process-based approach towards building and operating an Information Security Management System (ISMS). Successful operation of the ISMS is generally a prerequisite for Enterprise Architectures to meet the security objectives established by an organization. A chapter of the Security Architecture Practitioners Guide will be devoted to the relationship between Enterprise Architecture, the TOGAF standard, and ISMSs. The O-ISM3 standard defines security services as strategic, tactical, or operational processes, and provides a metrics-based approach to continuous improvement of the processes. Many of the services or processes described in the O-ISM3 standard are expected to be referenced in the Security Services Catalog Project as well.Open FAIR
The Open FAIR Body of Knowledge comprises the Risk Taxonomy (O-RT) Standard and the Risk Analysis (O-RA) Standard. These standards help organizations to better measure their information security and operational risks. The Open FAIR quantitative risk analysis approach is highly useful during threat assessments and helps to understand the impact of threat mitigation options during the ADM cycle. Open FAIR can be thought of as a tool or technique in analyzing risk throughout the TOGAF ADM.(AI) Popular Cybersecurity Frameworks
1. Introduction to Cybersecurity Frameworks
In today's digital age, cybersecurity has become a top priority for individuals and organizations alike. With the increasing number of cyber threats and attacks, it is essential to have a comprehensive cybersecurity framework in place to protect sensitive information and data. Cybersecurity frameworks provide a structured approach to managing and mitigating cyber risks by outlining best practices, guidelines, and standards. In this article, we will explore three of the most widely used cybersecurity frameworks: NIST Cybersecurity Framework, ISO 27001 Information Security Management System, and CIS Controls for Effective Cyber Defense. By understanding these frameworks, you can better protect yourself and your organization from cyber threats and ensure that your cybersecurity measures are up to par with industry standards.
2. NIST Cybersecurity Framework
The NIST Cybersecurity Framework is a set of guidelines and best practices designed to help organizations manage and reduce cybersecurity risks. It was developed by the National Institute of Standards and Technology (NIST) in response to Executive Order 13636, which called for the creation of a framework that would help critical infrastructure organizations improve their cybersecurity posture.
The framework consists of five core functions: Identify, Protect, Detect, Respond, and Recover. Each function is further broken down into categories and subcategories that provide more specific guidance on how to implement the framework.
The Identify function focuses on understanding an organization's cybersecurity risks and vulnerabilities. This includes identifying all assets, systems, and data that need to be protected, as well as assessing the potential impact of a cyber attack.
The Protect function involves implementing safeguards to protect against cyber threats. This includes measures such as access controls, encryption, and security awareness training for employees.
The Detect function involves monitoring systems and networks for signs of a cyber attack. This includes implementing intrusion detection and prevention systems, as well as conducting regular vulnerability scans and penetration testing.
The Respond function involves developing and implementing a plan to respond to a cyber attack. This includes establishing an incident response team, defining roles and responsibilities, and developing procedures for containing and mitigating the effects of an attack.
Finally, the Recover function involves restoring normal operations after a cyber attack. This includes developing a business continuity plan, conducting backups of critical data, and ensuring that systems can be quickly restored in the event of an outage.
Overall, the NIST Cybersecurity Framework provides a comprehensive approach to managing cybersecurity risks. By following its guidelines and best practices, organizations can better protect themselves against cyber threats and ensure the confidentiality, integrity, and availability of their sensitive data.
3. ISO 27001 Information Security Management System
The ISO 27001 Information Security Management System is a globally recognized framework that provides a systematic approach to managing sensitive information. It outlines a set of best practices for establishing, implementing, maintaining, and continually improving an organization's information security management system.
The framework is designed to help organizations identify and manage risks to their information assets, including confidential data, intellectual property, and customer information. It also helps ensure compliance with legal, regulatory, and contractual requirements related to information security.
ISO 27001 consists of several key components, including risk assessment and treatment, security controls, and continuous improvement. The framework emphasizes the importance of a risk-based approach to information security, which involves identifying potential threats and vulnerabilities, assessing the likelihood and impact of those risks, and implementing appropriate controls to mitigate them.
One of the strengths of ISO 27001 is its flexibility. The framework can be adapted to suit the specific needs of different organizations, regardless of their size, industry, or location. It can also be integrated with other management systems, such as quality management or environmental management, to create a more comprehensive approach to organizational governance.
Overall, the ISO 27001 Information Security Management System is a valuable tool for organizations looking to establish a robust and effective information security program. By following the framework's guidelines, organizations can better protect their sensitive information, reduce the risk of cyber attacks, and demonstrate their commitment to security to stakeholders and customers alike.
4. CIS Controls for Effective Cyber Defense
The Center for Internet Security (CIS) Controls is a set of best practices designed to help organizations protect their systems and data from cyber threats. The controls are organized into three categories: Basic, Foundational, and Organizational.
The Basic Controls include measures such as inventory and control of hardware assets, inventory and control of software assets, continuous vulnerability management, and controlled use of administrative privileges. These controls are considered essential for any organization that wants to establish a strong cybersecurity posture.
The Foundational Controls build upon the Basic Controls and include measures such as email and web browser protections, malware defenses, data recovery capabilities, and secure configurations for network devices. These controls are designed to provide additional layers of protection against common cyber threats.
Finally, the Organizational Controls focus on the policies, procedures, and training necessary to maintain an effective cybersecurity program. These controls include measures such as security awareness training, incident response planning, and penetration testing.
By implementing the CIS Controls, organizations can establish a comprehensive cybersecurity program that addresses both technical and organizational aspects of security. The controls are regularly updated based on new threats and vulnerabilities, ensuring that organizations stay up-to-date with the latest best practices in cybersecurity.
Videos
References:
- Integrating Risk and Security within a TOGAF® Enterprise Architecture
- Secure Your Information: Information Security Principles for Enterprise Architecture








No comments:
Post a Comment