I had a chance to install it in my lab environment for a testing. This post is kind of recording all steps including all mistakes I had made, especially in the YouTube video. The version I am using is 11.2.1. The process is also test with version 11.3.x
1. Pre-Installation System Requirements:
1.1 OS Requirements
- Microsoft Windows Server 2016 Datacenter, with updates
- Microsoft Windows Server 2016 Standard, with updates
- Microsoft Windows Server 2012 R2 Datacenter, with updates
- Microsoft Windows Server 2012 R2 Standard, with updates
- Microsoft Windows Server 2008 R2 Enterprise SP1 (Deprecated in SEE 11.2.1 MP1)
- Microsoft Windows Server 2008 R2 Standard SP1 (Deprecated in SEE 11.2.1 MP1)
1.2 .NET Requirements
| Operating system | Required version of .NET Framework |
| Microsoft Windows Server 2008 R2 | 4.5.2 (Deprecated in SEE 11.2.1 MP1) |
| Microsoft Windows Server 2012 R2 | 4.5.2 |
| Microsoft Windows Server 2016 |
4.6.2 (For Symantec Endpoint Encryption 11.1.3 and later)
|
| SQL Server Version | On the Symantec Endpoint Encryption Management Server |
| SQL Server 2016 Enterprise (64-bit) | Yes |
| SQL Server 2016 Standard (64-bit) | Yes |
| SQL Server 2014 Enterprise (64-bit) | Yes |
| SQL Server 2014 Standard (64-bit) | Yes |
| SQL Server 2014 Express with Advanced Services (64-bit) (deprecated in SEE 11.2.1 MP1) | Yes |
| SQL Server 2012 Enterprise, SP1 (64-bit) (deprecated in SEE 11.2.1 MP1) | Yes |
| SQL Server 2012 Standard, SP1 (64-bit) (deprecated in SEE 11.2.1 MP1) | Yes |
| SQL Server 2012 Express with Advanced Services, SP1 (64-bit) (deprecated in SEE 11.2.1 MP1) | Yes |
1.4 Add prerequisites to the server
including Internet Information Services (IIS), the .NET framework, and other tools.See article HOWTO101921 for enabling the prerequisite server roles and features.
1.5 Download SEE Installation Software
2. Installing Symantec Endpoint Encryption Server
2.1 Install Server
Double-click the file "SEE Server Suite x64.msi" to run it.
You can find the Symantec Endpoint Encryption Installation Guide at https://support.symantec.com/en_US/article.DOC9134.html. Download 11.2.1 installation guide file - symcEE_11.2.1_InstallGuide_en.pdf.
Follow the guide, you should be able to get installation done if all prerequisites meet. My video at the end of this post will give you an idea how this installation looks like.
2.2 Install AutoLogon
Install the Autologon server MSI on a machine with the Symantec Endpoint Encryption Management Console
- The MSI files are included with the initial server installers downloaded from Symantec
- The Symantec Endpoint Encryption Management Agent component must be installed first
- Credentials to connect to the database will be needed
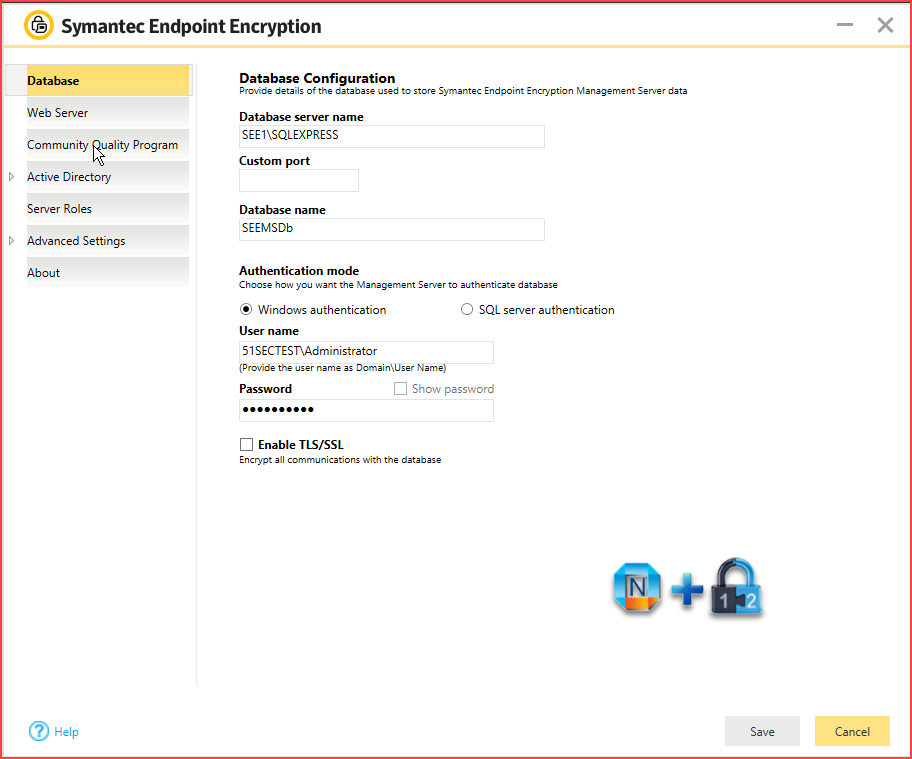
3. Configuring the Symantec Endpoint Encryption Management Server
After you run the Symantec Endpoint Encryption Management Server wizard, the configuration
wizard automatically launches. You use the wizard to set up your directory service synchronization and to configure the Web service. You can also manually start the wizard by running the configuration manager program on the Symantec Endpoint Encryption Management Server. You must complete the wizard before you can synchronize your directory services and create your client installation packages.
4. Using the Symantec Endpoint Encryption Manager to Generate Windows Clients
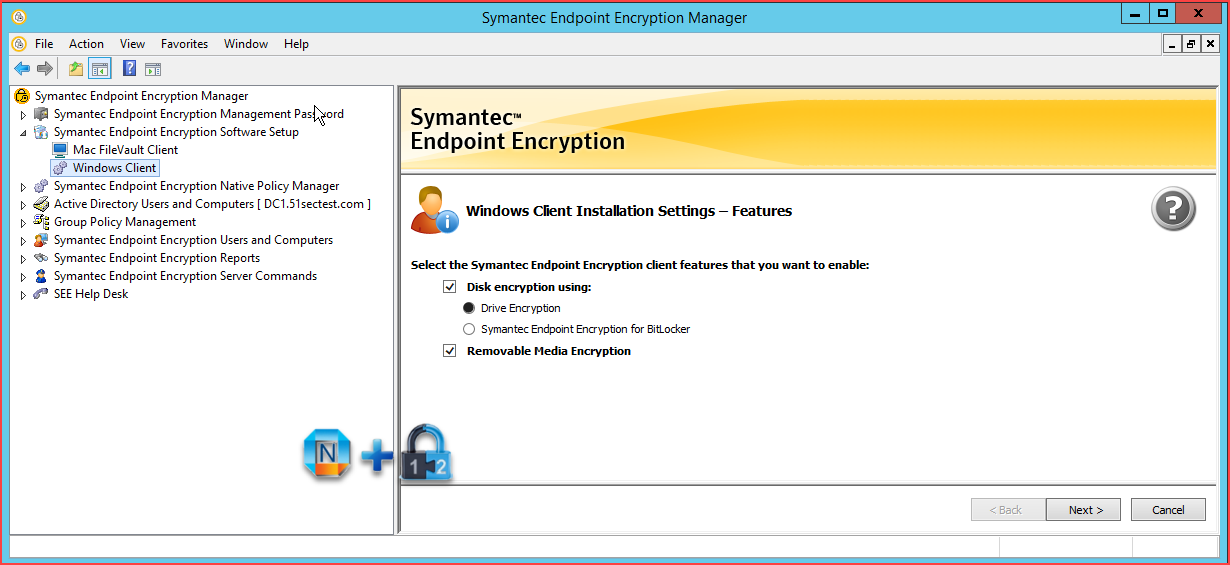
4.1 Generate SEE Client
For the Disk encryption option, you can select either the Drive Encryption feature, or Symantec Endpoint Encryption for BitLocker. If you select Drive Encryption, ensure that the Microsoft BitLocker feature is disabled on the Microsoft Windows computers on which you want to install Symantec Endpoint Encryption Client. If you select Symantec Endpoint Encryption for BitLocker, ensure that you install Symantec Endpoint Encryption Client on Windows computers that support the BitLocker feature.
Click SEE RME to encrypt files to removable media using the Symantec Endpoint Encryption Removable Media Encryption 11.x format. This option is selected by default.
Click SEE RS to encrypt files to removable media using the Symantec Endpoint Encryption Removable Storage 8.2.1 format.
4.2 Generate AutoLogon Client
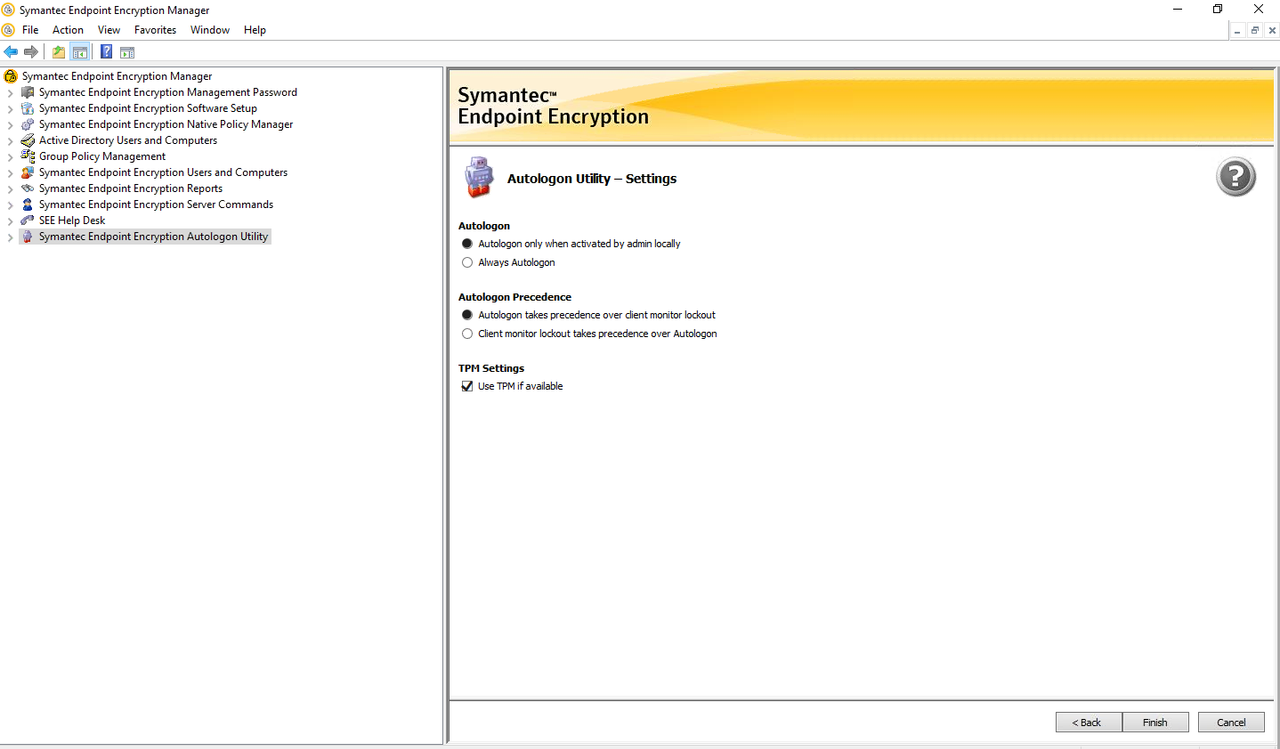
Note:
- Enable Always Autologon
- Uncheck 'Use TPM if Available'
5. Deploying Clients
5.1 Deploy SEE Client
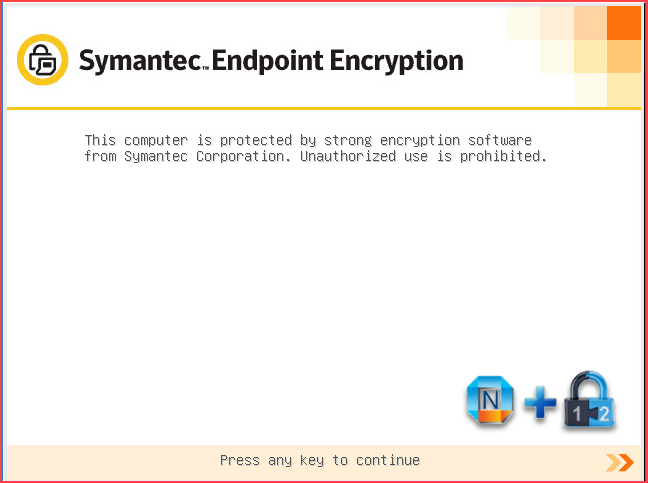
Double click new generated SEE client software , either "SEE Client.exe" or "SEE Client_x64.exe", to start installation. You will need admin privilege account to install this client.
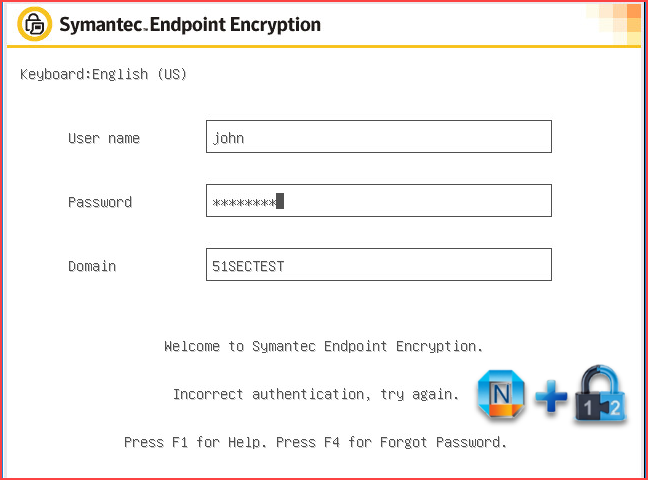
After complete installation, based on your package settings, you might see following screen after you rebooted your machine.
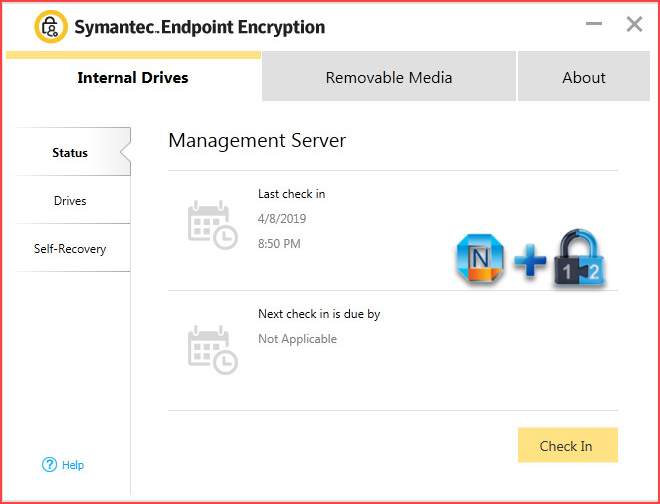
Once you successfully SSO logged in client machine, you can check SEE Management Agent software to see check in status.
5.2 Deploy AutoLogon Client
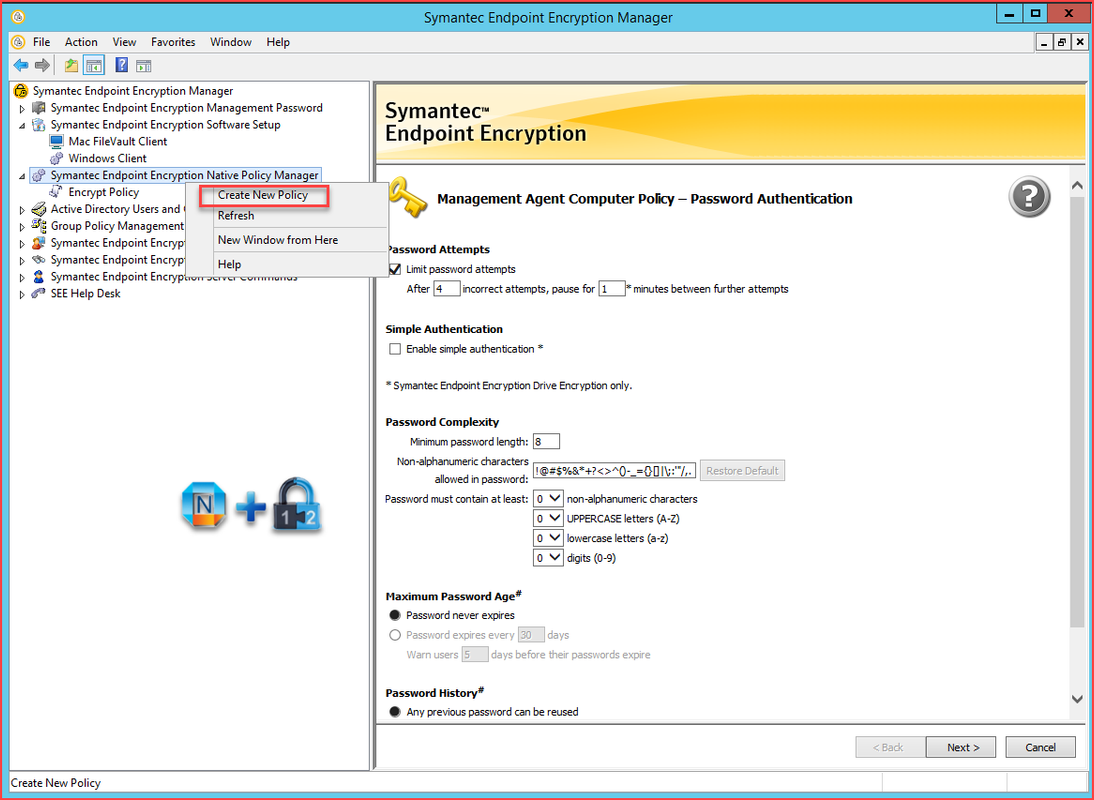
6. Create SEE Policy
6.1 SEE Native Policy Manager
- If Directory Synchronization is not enabled, or the machine is not a member of the configured domain, Native Policies will be used to manage settings for the Autologon Utility
- Settings can be updated in the Symantec Endpoint Encryption Management Console from the "Symantec Endpoint Encryption Native Policy Manager" snap-in.
6.2 Using Group policy to manage SEE settings and autologon utility
7. Create Groups at SEE Users and Computers - > SEE Managed Computers
You can create your own group based on your policy.
8. Assign SEE policy created at step 6 to the Group created at step 7
Troubleshooting:
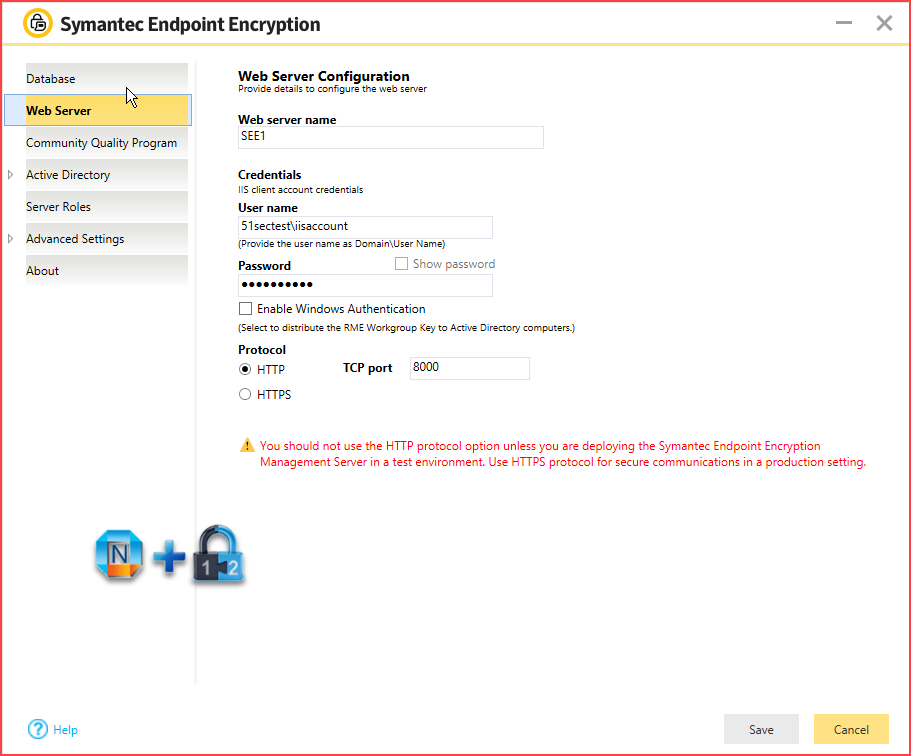
Issue 1 - Save failed for web server configuration due to invalid data
The web site actually creates during the initial Management Server installation. If you are at the section where the yellow/white boxes are asking for configuration data, the site should be saved already. If it is not, uninstall, verify IIS components are all installed as required in HOWTO101921, and try again.
Troubleshooting Tools: Drive Encryption Administrator Command Line Interface
Symantec Endpoint Encryption Autologon Settings may be managed from the client machine itself using the built in Client Administrator Command Line Interface. The command line utility can be used to check the current status of Autologon, as well as enable or disable the utility.
Only Drive Encryption Client Administrators can use the command line utility.
Sample Commands:
To be run from the C:\Program File\Symantec\Endpoint Encryption Clients\Drive Encryption
directory inside Command Prompt. In the below examples, replace <Client Admin Username>, <Client Admin Password>, and <Number of bypasses> with the appropriate values
Check Status of Autologon:
eedadmincli --check-autologon --au <Client Admin Username> --ap <Client Admin Password>
Enable Autologon (The count option is optional with a default of 1 if not specified):
eedadmincli --enable-autologon --count <Number of bypasses> --au <Client Admin Username> --ap <Client Admin Password>
Disable Autologon:
eedadmincli --disable-autologon --au <Client Admin Username> --ap <Client Admin Password>
Decrypt SEE encrypted disk or USB files
* Burn the WinPE to a bootable USB/DVD
* Change the BIOS boot sequence to boot from USB/DVD
* Try to change the boot options to legacy and try to disable the secure boot
or fast boot if you are unable to boot from USB/DVD
* Use the command ( eedadmincli --status ) To check if the drive is
instrumented by bootguard
* Use the command ( eedAdminCli --decrypt --disk <number> --au
<AdminUserName> --ap <AdminPassword> ) to decrypt the drive
Note: Please do not restart the machine while it is decrypting. Use the
command ( eedadmincli --status ) to check the watermark values
often as the low watermark will increase as the data decrypts. Only when the
Low watermark is equal to the total sectors it indicates that the drive is completely
decrypted.
Here are some articles from Broadcom:
1. To Upload the CA certificate:
https://knowledge.broadcom.com/external/article/178609/how-to-create-an-ssl-certificate-to-be-u.html
2. To decrypt the Removable Media files.
https://knowledge.broadcom.com/external/article/154529/how-to-decrypt-removable-storage-files-u.html
YouTube - Deploy SEE Video:
References:
- System Requirements for Symantec Endpoint Encryption Management Server 11.2.x
- How to: Install Symantec Endpoint Encryption 11
- Symantec Endpoint Encryption Policy Administrator Guide
- Symantec Encryption Endpoint 11.2.1 Installation Guide
- How to use the Autologon Utility for Symantec Endpoint Encryption version 11.x
- How to create an SSL certificate to be used to secure Client Communication with the Symantec Endpoint Encryption Management Server
- Creating a Symantec Endpoint Encryption Client installation package
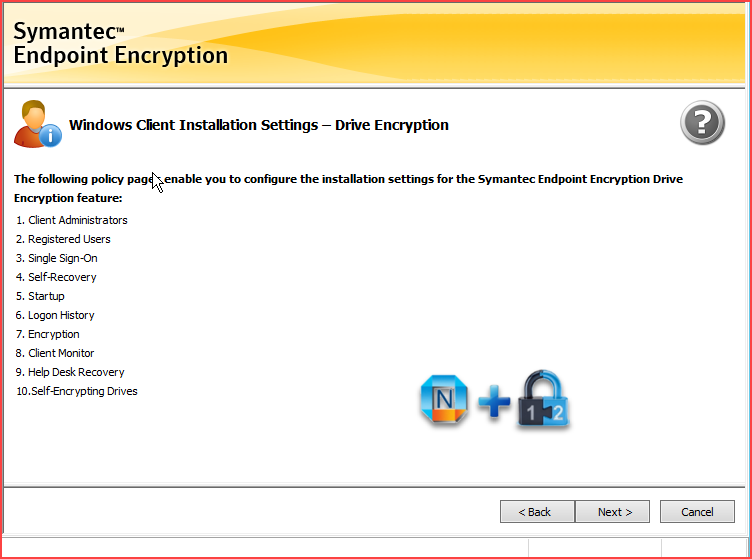
- Configuring the Drive Encryption installation settings
Configuring the Drive Encryption - Client Administrators policy options, for adding or editing
Configuring the Drive Encryption - Client Administrators policy options, for deleting
Configuring the Drive Encryption - Registered Users policy options
Configuring the Drive Encryption - Single Sign-On policy options
Configuring the Drive Encryption - Self-Recovery policy options
Configuring the Drive Encryption - Startup policy options
Configuring the Drive Encryption - Logon History policy options
Configuring the Drive Encryption - Encryption policy options
Configuring the Drive Encryption - Client Monitor policy options
Configuring the Drive Encryption - Help Desk Recovery policy options
Configuring the Drive Encryption - Self-Encrypting Drives policy options
- Configuring the Removable Media Encryption installation settings
Configuring the Removable Media Encryption - Access and Encryption policy options
Configuring the Removable Media Encryption - Device and File Type Exclusions policy options
Configuring the Removable Media Encryption - Encryption Method policy options
Configuring the Removable Media Encryption - Default Passwords policy options
Configuring the Removable Media Encryption - Recovery Certificate policy options
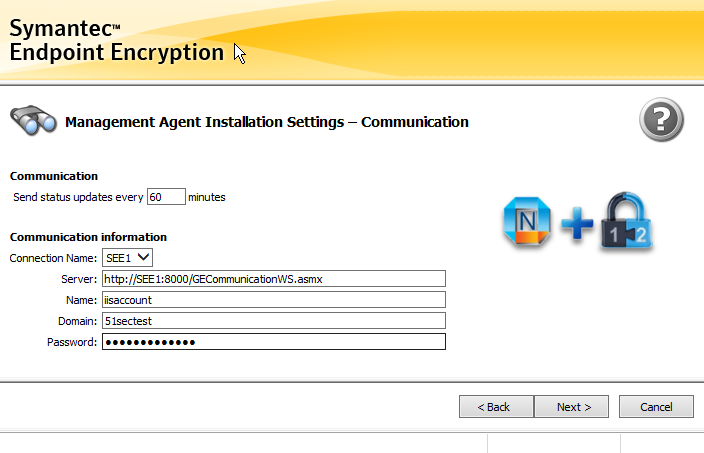
Configuring the Management Agent installation settings
Configuring the Removable Media Encryption - Recovery Certificate policy options
Configuring the Removable Media Encryption - Default Passwords policy options
Configuring the Removable Media Encryption - Portability policy options











No comments:
Post a Comment