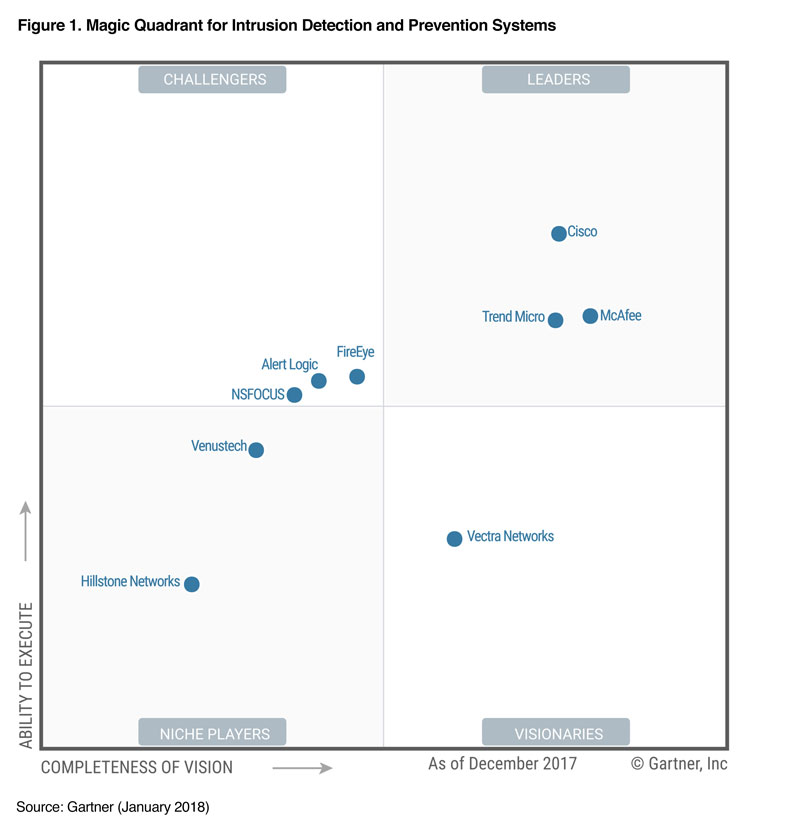
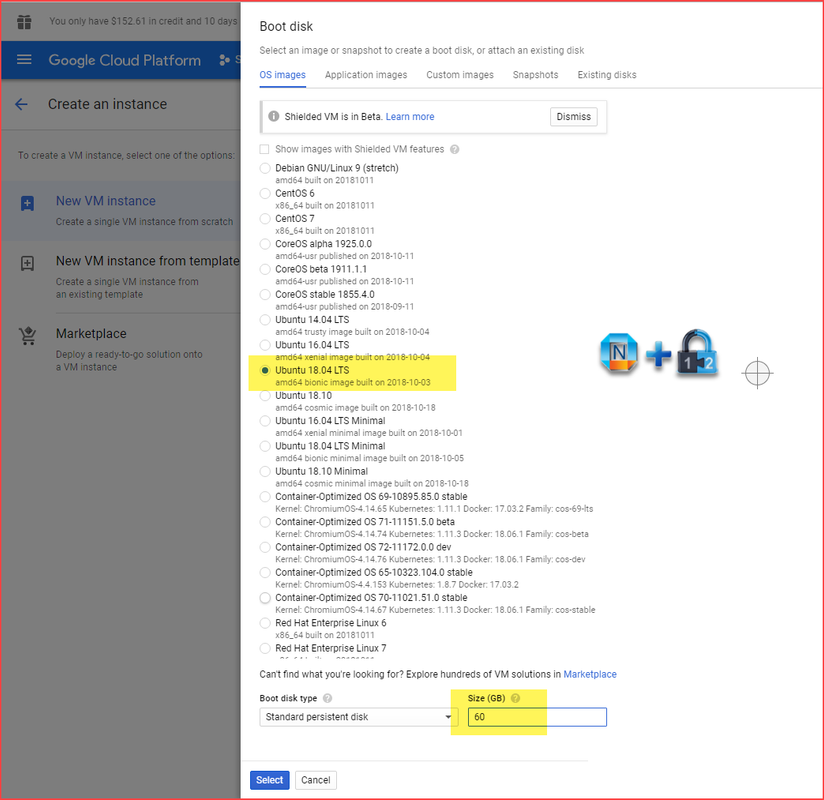
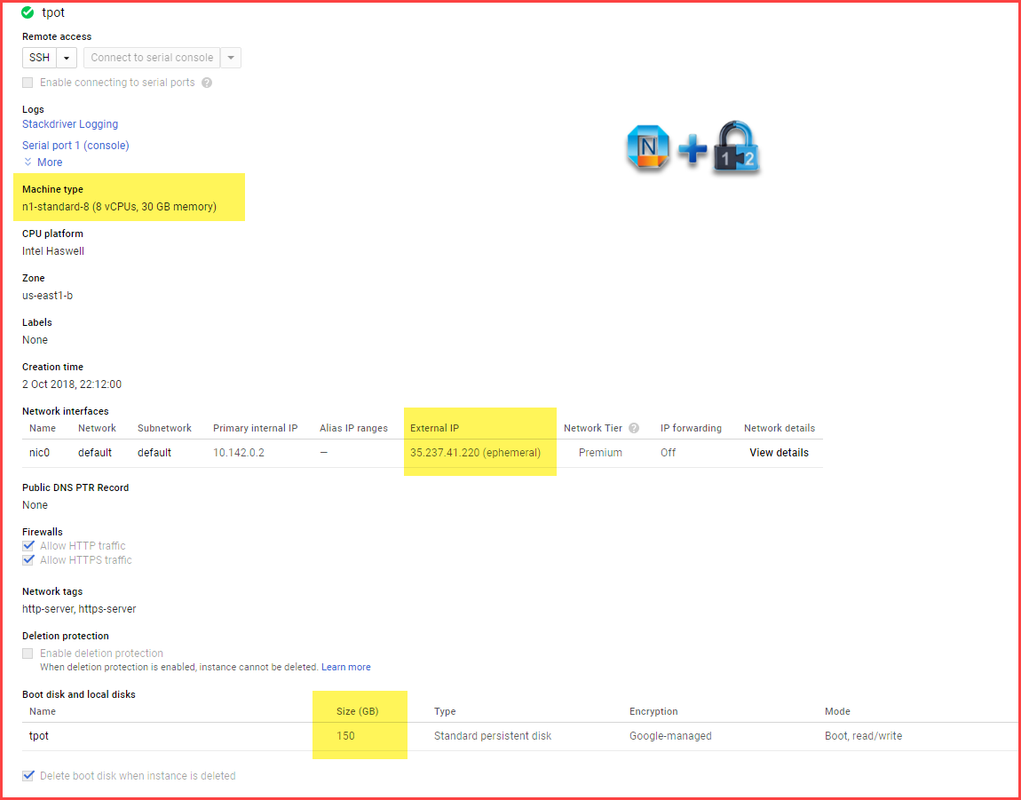
Configure Cisco Enterprise Access Point 1142N As Home AP
Netsec
11/10/2018
0 Comments
Early of 2018, I got a chance to buy a Cisco Wireless Access Point with only $30, which is a great deal for AIR-LAP1142N-x-K9 - Dual-band Co...
Read More