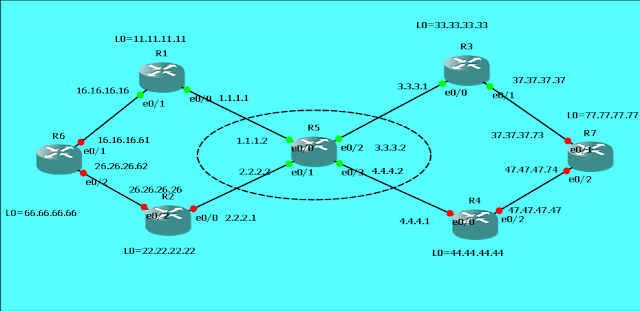
Same topology as GRE one:
- R1, R2, R3, R4, R5, R6, R7 all uses same IOS : c3640-ik9o3s-mz.124-10.bin. 3600 Software (C3640-IK9O3S-M), Version 12.4(10), RELEASE SOFTWARE (fc1)
- R5 is acting as Internet Router. It is only configured local interface ip address. No static and dynamic routing configured
- R1, R3 will be acted as a pair to configure GRE and IPSec Tunnel, and also configured as main link between R6 and R7
- R2, R4 will be acted as second pair to configure GRE and IPSec Tunnel. It will be set as secondly link between R6 and R7
- R5 Configuration:
R5#sh run1. R1 Configuration
interface Ethernet0/0
ip address 1.1.1.2 255.255.255.0
full-duplex
!
interface Ethernet0/1
ip address 2.2.2.2 255.255.255.0
full-duplex
!
interface Ethernet0/2
ip address 3.3.3.2 255.255.255.0
full-duplex
!
interface Ethernet0/3
ip address 4.4.4.2 255.255.255.0
full-duplex
!
R1#sh run
Building configuration...
Current configuration : 1336 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R1
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
no ip domain lookup
!
crypto isakmp policy 1
hash md5
authentication pre-share
crypto isakmp key cisco123 address 3.3.3.1
!
!
crypto ipsec transform-set myset esp-des esp-md5-hmac
mode transport
!
crypto map vpn 10 ipsec-isakmp
set peer 3.3.3.1
set transform-set myset
match address 101
!
interface Loopback0
ip address 11.11.11.11 255.255.255.0
!
interface Tunnel0
ip unnumbered Ethernet0/1
tunnel source Ethernet0/0
tunnel destination 3.3.3.1
!
interface Ethernet0/0
ip address 1.1.1.1 255.255.255.0
full-duplex
crypto map vpn
!
interface Ethernet0/1
ip address 16.16.16.16 255.255.255.0
shutdown
full-duplex
!
interface Ethernet0/2
no ip address
shutdown
full-duplex
!
interface Ethernet0/3
no ip address
shutdown
full-duplex
!
no ip http server
no ip http secure-server
!
ip route 3.3.3.0 255.255.255.0 1.1.1.2
ip route 33.33.33.0 255.255.255.0 Tunnel0
!
!
access-list 101 permit gre host 1.1.1.1 host 3.3.3.1
!
control-plane
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
end
2. R3 Configuration
R3#sh run3. Verification
Building configuration...
Current configuration : 1336 bytes
!
version 12.4
service timestamps debug datetime msec
service timestamps log datetime msec
no service password-encryption
!
hostname R3
!
boot-start-marker
boot-end-marker
!
!
no aaa new-model
memory-size iomem 5
!
!
ip cef
no ip domain lookup
!
crypto isakmp policy 1
hash md5
authentication pre-share
crypto isakmp key cisco123 address 1.1.1.1
!
!
crypto ipsec transform-set myset esp-des esp-md5-hmac
mode transport
!
crypto map vpn 10 ipsec-isakmp
set peer 1.1.1.1
set transform-set myset
match address 101
!
!
!
!
interface Loopback0
ip address 33.33.33.33 255.255.255.0
!
interface Tunnel0
ip unnumbered Ethernet0/1
tunnel source Ethernet0/0
tunnel destination 1.1.1.1
!
interface Ethernet0/0
ip address 3.3.3.1 255.255.255.0
full-duplex
crypto map vpn
!
interface Ethernet0/1
ip address 37.37.37.37 255.255.255.0
shutdown
full-duplex
!
interface Ethernet0/2
no ip address
shutdown
full-duplex
!
interface Ethernet0/3
no ip address
shutdown
full-duplex
!
no ip http server
no ip http secure-server
!
ip route 1.1.1.0 255.255.255.0 3.3.3.2
ip route 11.11.11.0 255.255.255.0 Tunnel0
!
!
access-list 101 permit gre host 3.3.3.1 host 1.1.1.1
!
control-plane
!
line con 0
exec-timeout 0 0
logging synchronous
line aux 0
line vty 0 4
login
!
!
end
R3#show crypto isakmp key
Keyring Hostname/Address Preshared Key
default 1.1.1.1 cisco123
R3#show crypto isakmp peers
Peer: 1.1.1.1 Port: 500 Local: 3.3.3.1
Phase1 id: 1.1.1.1
R3#show crypto isakmp policy
Global IKE policy
Protection suite of priority 1
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Message Digest 5
authentication method: Pre-Shared Key
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
Default protection suite
encryption algorithm: DES - Data Encryption Standard (56 bit keys).
hash algorithm: Secure Hash Standard
authentication method: Rivest-Shamir-Adleman Signature
Diffie-Hellman group: #1 (768 bit)
lifetime: 86400 seconds, no volume limit
R3#show crypto isakmp sa
dst src state conn-id slot status
3.3.3.1 1.1.1.1 QM_IDLE 1 0 ACTIVE
R1#ping 33.33.33.33 source 11.11.11.11
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 33.33.33.33, timeout is 2 seconds:
Packet sent with a source address of 11.11.11.11
.!!!!
Success rate is 80 percent (4/5), round-trip min/avg/max = 56/127/224 ms
R1#
R3#debug crypto isakmp
Crypto ISAKMP debugging is on
R3#
*Mar 1 01:00:50.155: ISAKMP (0:0): received packet from 1.1.1.1 dport 500 sport 500 Global (N) NEW SA
*Mar 1 01:00:50.159: ISAKMP: Created a peer struct for 1.1.1.1, peer port 500
*Mar 1 01:00:50.163: ISAKMP: New peer created peer = 0x64AAEB34 peer_handle = 0x80000003
*Mar 1 01:00:50.167: ISAKMP: Locking peer struct 0x64AAEB34, IKE refcount 1 for crypto_isakmp_process_block
*Mar 1 01:00:50.167: ISAKMP: local port 500, remote port 500
*Mar 1 01:00:50.171: insert sa successfully sa = 646DD910
*Mar 1 01:00:50.175: ISAKMP:(0:0:N/A:0):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 01:00:50.179: ISAKMP:(0:0:N/A:0):Old State = IKE_READY New State = IKE_R_MM1
*Mar 1 01:00:50.187: ISAKMP:(0:0:N/A:0): processing SA payload. message ID = 0
*Mar 1 01:00:50.191: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 01:00:50.195: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 01:00:50.195: ISAKMP (0:0): vendor ID is NAT-T v7
*Mar 1 01:00:50.195: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 01:00:50.199: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 157 mismatch
*Mar 1 01:00:50.199: ISAKMP:(0:0:N/A:0): vendor ID is NAT-T v3
*Mar 1 01:00:50.203: ISAKMP:(0:0:N/A:0): processing vendor id payload
*Mar 1 01:00:50.207: ISAKMP:(0:0:N/A:0): vendor ID seems Unity/DPD but major 123 mismatch
*Mar 1 01:00:50.211: ISAKMP:(0:0:N/A:0): vendor ID is NAT-T v2
*Mar 1 01:00:50.211: ISAKMP:(0:0:N/A:0):found peer pre-shared key matching 1.1.1.1
*Mar 1 01:00:50.211: ISAKMP:(0:0:N/A:0): local preshared key found
*Mar 1 01:00:50.211: ISAKMP : Scanning profiles for xauth ...
*Mar 1 01:00:50.211: ISAKMP:(0:0:N/A:0):Checking ISAKMP transform 1 against priority 1 policy
*Mar 1 01:00:50.211: ISAKMP: encryption DES-CBC
*Mar 1 01:00:50.211: ISAKMP: hash MD5
*Mar 1 01:00:50.211: ISAKMP: default group 1
*Mar 1 01:00:50.211: ISAKMP: auth pre-share
*Mar 1 01:00:50.211: ISAKMP: life type in seconds
*Mar 1 01:00:50.211: ISAKMP: life duration (VPI) of 0x0 0x1 0x51 0x80
*Mar 1 01:00:50.211: ISAKMP:(0:0:N/A:0):atts are acceptable. Next payload is 0
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 245 mismatch
*Mar 1 01:00:50.227: ISAKMP (0:134217729): vendor ID is NAT-T v7
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 157 mismatch
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): vendor ID is NAT-T v3
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): vendor ID seems Unity/DPD but major 123 mismatch
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): vendor ID is NAT-T v2
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM1 New State = IKE_R_MM1
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): constructed NAT-T vendor-07 ID
*Mar 1 01:00:50.227: ISAKMP:(0:1:SW:1): sending packet to 1.1.1.1 my_port 500 peer_port 500 (R) MM_SA_SETUP
*Mar 1 01:00:50.231: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 01:00:50.231: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM1 New State = IKE_R_MM2
*Mar 1 01:00:50.359: ISAKMP (0:134217729): received packet from 1.1.1.1 dport 500 sport 500 Global (R) MM_SA_SETUP
*Mar 1 01:00:50.367: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 01:00:50.371: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM2 New State = IKE_R_MM3
*Mar 1 01:00:50.375: ISAKMP:(0:1:SW:1): processing KE payload. message ID = 0
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = 0
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1):found peer pre-shared key matching 1.1.1.1
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1):SKEYID state generated
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): vendor ID is Unity
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): vendor ID is DPD
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): processing vendor id payload
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1): speaking to another IOS box!
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 01:00:50.399: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM3 New State = IKE_R_MM3
*Mar 1 01:00:50.403: ISAKMP:(0:1:SW:1): sending packet to 1.1.1.1 my_port 500 peer_port 500 (R) MM_KEY_EXCH
*Mar 1 01:00:50.407: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 01:00:50.411: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM3 New State = IKE_R_MM4
*Mar 1 01:00:50.531: ISAKMP (0:134217729): received packet from 1.1.1.1 dport 500 sport 500 Global (R) MM_KEY_EXCH
*Mar 1 01:00:50.539: ISAKMP:(0:1:SW:1):Input = IKE_MESG_FROM_PEER, IKE_MM_EXCH
*Mar 1 01:00:50.543: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM4 New State = IKE_R_MM5
*Mar 1 01:00:50.551: ISAKMP:(0:1:SW:1): processing ID payload. message ID = 0
*Mar 1 01:00:50.555: ISAKMP (0:134217729): ID payload
next-payload : 8
type : 1
address : 1.1.1.1
protocol : 17
port : 500
length : 12
*Mar 1 01:00:50.559: ISAKMP:(0:1:SW:1):: peer matches *none* of the profiles
*Mar 1 01:00:50.563: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = 0
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1): processing NOTIFY INITIAL_CONTACT protocol 1
spi 0, message ID = 0, sa = 646DD910
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1):SA authentication status:
authenticated
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1): Process initial contact,
bring down existing phase 1 and 2 SA's with local 3.3.3.1 remote 1.1.1.1 remote port 500
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1):SA authentication status:
authenticated
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1):SA has been authenticated with 1.1.1.1
*Mar 1 01:00:50.571: ISAKMP: Trying to insert a peer 3.3.3.1/1.1.1.1/500/, and inserted successfully 64AAEB34.
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_MAIN_MODE
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM5 New State = IKE_R_MM5
*Mar 1 01:00:50.571: ISAKMP:(0:1:SW:1):SA is doing pre-shared key authentication using id type ID_IPV4_ADDR
*Mar 1 01:00:50.571: ISAKMP (0:134217729): ID payload
next-payload : 8
type : 1
address : 3.3.3.1
protocol : 17
port : 500
length : 12
*Mar 1 01:00:50.575: ISAKMP:(0:1:SW:1):Total payload length: 12
*Mar 1 01:00:50.583: ISAKMP:(0:1:SW:1): sending packet to 1.1.1.1 my_port 500 peer_port 500 (R) MM_KEY_EXCH
*Mar 1 01:00:50.587: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PROCESS_COMPLETE
*Mar 1 01:00:50.587: ISAKMP:(0:1:SW:1):Old State = IKE_R_MM5 New State = IKE_P1_COMPLETE
*Mar 1 01:00:50.595: ISAKMP:(0:1:SW:1):Input = IKE_MESG_INTERNAL, IKE_PHASE1_COMPLETE
*Mar 1 01:00:50.599: ISAKMP:(0:1:SW:1):Old State = IKE_P1_COMPLETE New State = IKE_P1_COMPLETE
*Mar 1 01:00:50.671: ISAKMP (0:134217729): received packet from 1.1.1.1 dport 500 sport 500 Global (R) QM_IDLE
*Mar 1 01:00:50.675: ISAKMP: set new node -647448370 to QM_IDLE
*Mar 1 01:00:50.687: ISAKMP:(0:1:SW:1): processing HASH payload. message ID = -647448370
*Mar 1 01:00:50.687: ISAKMP:(0:1:SW:1): processing SA payload. message ID = -647448370
*Mar 1 01:00:50.691: ISAKMP:(0:1:SW:1):Checking IPSec proposal 1
*Mar 1 01:00:50.691: ISAKMP: transform 1, ESP_DES
*Mar 1 01:00:50.695: ISAKMP: attributes in transform:
*Mar 1 01:00:50.695: ISAKMP: encaps is 2 (Transport)
*Mar 1 01:00:50.695: ISAKMP: SA life type in seconds
*Mar 1 01:00:50.695: ISAKMP: SA life duration (basic) of 3600
*Mar 1 01:00:50.695: ISAKMP: SA life type in kilobytes
*Mar 1 01:00:50.695: ISAKMP: SA life duration (VPI) of 0x0 0x46 0x50 0x0
*Mar 1 01:00:50.695: ISAKMP: authenticator is HMAC-MD5
*Mar 1 01:00:50.695: ISAKMP:(0:1:SW:1):atts are acceptable.
*Mar 1 01:00:50.699: ISAKMP:(0:1:SW:1): processing NONCE payload. message ID = -647448370
*Mar 1 01:00:50.699: ISAKMP:(0:1:SW:1): processing ID payload. message ID = -647448370
*Mar 1 01:00:50.703: ISAKMP:(0:1:SW:1): processing ID payload. message ID = -647448370
*Mar 1 01:00:50.707: ISAKMP:(0:1:SW:1): asking for 1 spis from ipsec
*Mar 1 01:00:50.711: ISAKMP:(0:1:SW:1):Node -647448370, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 1 01:00:50.711: ISAKMP:(0:1:SW:1):Old State = IKE_QM_READY New State = IKE_QM_SPI_STARVE
*Mar 1 01:00:50.711: ISAKMP: received ke message (2/1)
*Mar 1 01:00:50.719: ISAKMP: Locking peer struct 0x64AAEB34, IPSEC refcount 1 for for stuff_ke
*Mar 1 01:00:50.723: ISAKMP:(0:1:SW:1): Creating IPSec SAs
*Mar 1 01:00:50.723: inbound SA from 1.1.1.1 to 3.3.3.1 (f/i) 0/ 0
(proxy 1.1.1.1 to 3.3.3.1)
*Mar 1 01:00:50.727: has spi 0xD57BF9FC and conn_id 0 and flags 4
*Mar 1 01:00:50.727: lifetime of 3600 seconds
*Mar 1 01:00:50.727: lifetime of 4608000 kilobytes
*Mar 1 01:00:50.727: has client flags 0x0
*Mar 1 01:00:50.727: outbound SA from 3.3.3.1 to 1.1.1.1 (f/i) 0/0
(proxy 3.3.3.1 to 1.1.1.1)
*Mar 1 01:00:50.727: has spi 1959940862 and conn_id 0 and flags C
*Mar 1 01:00:50.727: lifetime of 3600 seconds
*Mar 1 01:00:50.727: lifetime of 4608000 kilobytes
*Mar 1 01:00:50.727: has client flags 0x0
*Mar 1 01:00:50.727: ISAKMP:(0:1:SW:1): sending packet to 1.1.1.1 my_port 500 peer_port 500 (R) QM_IDLE
*Mar 1 01:00:50.731: ISAKMP:(0:1:SW:1):Node -647448370, Input = IKE_MESG_FROM_IPSEC, IKE_SPI_REPLY
*Mar 1 01:00:50.735: ISAKMP:(0:1:SW:1):Old State = IKE_QM_SPI_STARVE New State = IKE_QM_R_QM2
*Mar 1 01:00:50.743: ISAKMP: Locking peer struct 0x64AAEB34, IPSEC refcount 2 for from create_transforms
*Mar 1 01:00:50.747: ISAKMP: Unlocking IPSEC struct 0x64AAEB34 from create_transforms, count 1
*Mar 1 01:00:50.843: ISAKMP (0:134217729): received packet from 1.1.1.1 dport 500 sport 500 Global (R) QM_IDLE
*Mar 1 01:00:50.855: ISAKMP:(0:1:SW:1):deleting node -647448370 error FALSE reason "QM done (await)"
*Mar 1 01:00:50.859: ISAKMP:(0:1:SW:1):Node -647448370, Input = IKE_MESG_FROM_PEER, IKE_QM_EXCH
*Mar 1 01:00:50.859: ISAKMP:(0:1:SW:1):Old State = IKE_QM_R_QM2 New State = IKE_QM_PHASE2_COMPLETE
R3#
4. Packets
Captured packets on R5 interface
@R1
router ospf 100
router-id 11.11.11.11
log-adjacency-changes
network 11.11.11.0 0.0.0.255 area 0
network 16.16.16.0 0.0.0.255 area 0
@R3
router ospf 100
router-id 33.33.33.33
log-adjacency-changes
network 33.33.33.0 0.0.0.255 area 0
network 37.37.37.0 0.0.0.255 area 0
6. Show routes on both routers
@R1
R1#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
16.0.0.0/24 is subnetted, 1 subnets
C 16.16.16.0 is directly connected, Ethernet0/1
1.0.0.0/24 is subnetted, 1 subnets
C 1.1.1.0 is directly connected, Ethernet0/0
33.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
O 33.33.33.33/32 [110/11112] via 37.37.37.37, 00:00:45, Tunnel0
S 33.33.33.0/24 is directly connected, Tunnel0
3.0.0.0/24 is subnetted, 1 subnets
S 3.3.3.0 [1/0] via 1.1.1.2
37.0.0.0/24 is subnetted, 1 subnets
O 37.37.37.0 [110/11121] via 37.37.37.37, 00:00:47, Tunnel0
11.0.0.0/24 is subnetted, 1 subnets
C 11.11.11.0 is directly connected, Loopback0
@R3
R3#sh ip route
Codes: C - connected, S - static, R - RIP, M - mobile, B - BGP
D - EIGRP, EX - EIGRP external, O - OSPF, IA - OSPF inter area
N1 - OSPF NSSA external type 1, N2 - OSPF NSSA external type 2
E1 - OSPF external type 1, E2 - OSPF external type 2
i - IS-IS, su - IS-IS summary, L1 - IS-IS level-1, L2 - IS-IS level-2
ia - IS-IS inter area, * - candidate default, U - per-user static route
o - ODR, P - periodic downloaded static route
Gateway of last resort is not set
16.0.0.0/24 is subnetted, 1 subnets
O 16.16.16.0 [110/11121] via 16.16.16.16, 00:00:35, Tunnel0
1.0.0.0/24 is subnetted, 1 subnets
S 1.1.1.0 [1/0] via 3.3.3.2
33.0.0.0/24 is subnetted, 1 subnets
C 33.33.33.0 is directly connected, Loopback0
3.0.0.0/24 is subnetted, 1 subnets
C 3.3.3.0 is directly connected, Ethernet0/0
37.0.0.0/24 is subnetted, 1 subnets
C 37.37.37.0 is directly connected, Ethernet0/1
11.0.0.0/8 is variably subnetted, 2 subnets, 2 masks
O 11.11.11.11/32 [110/11112] via 16.16.16.16, 00:00:37, Tunnel0
S 11.11.11.0/24 is directly connected, Tunnel0
R3#sh ip os nei
Neighbor ID Pri State Dead Time Address Interface
11.11.11.11 0 FULL/ - 00:00:36 16.16.16.16 Tunnel0
R3#ping 16.16.16.16 source 37.37.37.37
Type escape sequence to abort.
Sending 5, 100-byte ICMP Echos to 16.16.16.16, timeout is 2 seconds:
Packet sent with a source address of 37.37.37.37
!!!!!
Success rate is 100 percent (5/5), round-trip min/avg/max = 60/95/164 ms
R3#








No comments:
Post a Comment