There are some other related posts in this blog:
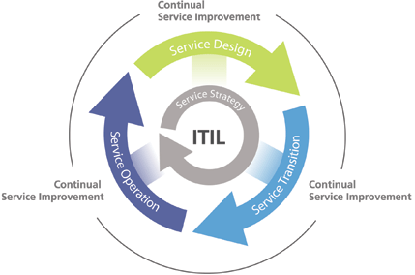
1.1 ITIL v3 :
1.2 IBM Maximo Asset Management : Maximo Asset Management is an Enterprise Asset Management system that provides comprehensive support for asset, maintenance, resource and parts supply chain management needs. Video Link . Includes following modules:
1.4 Marval IT Service Management (ITSM) MSM Software: MSM is an integrated, innovative, multi-level IT service management (ITSM) software solution - a secure, reliable, scalable and stable ITSM technology that supports IT business services and growth strategies of your organisation.
An information security framework is a series of documented processes that are used to define policies and procedures around the implementation and ongoing management of information security controls in an enterprise environment. These frameworks are basically a "blueprint" for building an information security program to manage risk and reduce vulnerabilities. Information security pros can utilize these frameworks to define and prioritize the tasks required to build security into an organization.
2.1 ISO27000
The ISO 27000 series of standards have been specifically reserved by ISO for information security matters.

2.2 COBIT
COBIT (Control Objectives for Information and Related Technologies) is a good-practice framework created by international professional association ISACA for information technology (IT) management and IT governance. COBIT provides an implementable "set of controls over information technology and organizes them around a logical framework of IT-related processes and enablers."
COBIT 5 is the only business framework for the governance and management of enterprise IT. , providing an end-to-end business view of the governance of enterprise IT that reflects the central role of information and technology in creating value for enterprises. In April 2012, COBIT 5 was released.
COBIT components include:
2.3 NIST SP 800 - CYBERSECURITY FRAMEWORK (CSF)
National Institute of Standards and Technology (U.S. Department of Commerce)
"Security and Privacy Controls for Federal Information Systems and Organizations," provides a catalog of security controls for all U.S. federal information systems except those related to national security. The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles.
The Framework Core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand. The Core guides organizations in managing and reducing their cybersecurity risks in a way that complements an organization’s existing cybersecurity and risk management processes.
The Framework Implementation Tiers assist organizations by providing context on how an organization views cybersecurity risk management. The Tiers guide organizations to consider the appropriate level of rigor for their cybersecurity program and are often used as a communication tool to discuss risk appetite, mission priority, and budget.
Framework Profiles are an organization’s unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core. Profiles are primarily used to identify and prioritize opportunities for improving cybersecurity at an organization.
-----------------------------------------------------------------------------------------------------------------------
There is overlap between those frameworks so "crosswalks" can be built to show compliance with different regulatory standards. For example, ISO 27002 defines information security policy in section 5; COBIT defines it in the section "Plan and Organize"; Sarbanes Oxley defines it as "Internal Environment"; HIPAA defines it as "Assigned Security Responsibility"; and PCI DSS defines it as "Maintain an Information Security Policy." By using a common framework like ISO 27000, a company can then use this crosswalk process to show compliance with multiple regulations such as HIPAA, Sarbanes Oxley, PCI DSS and GLBA, to name a few.
2.4 CIS CSC (Center for Internet Security - Critical Security Controls)
The Center for Internet Security Critical Security Controls for Effective Cyber Defense is a publication of best practice guidelines for computer security. The project was initiated early in 2008 as a response to extreme data losses experienced by organizations in the US defense industrial base and recently.[1] The publication was initially developed by the SANS Institute, ownership was transferred to the Council on Cyber Security (CCS) in 2013 and then transferred to Center for Internet Security (CIS) in 2015. It was earlier known as the Consensus Audit Guidelines and it is also known as the CIS CSC, CIS 20, CCS CSC, SANS Top 20 or CAG 20.The CIS Critical Security Controls provide a highly practical and useful framework for every organization to use for both implementation and assessment. Because the Controls are developed by the community and based on actual threat data, they are an authoritative, industry-friendly, and vendor-neutral approach to assessment and auditing of security. (V7.0)
2.5 ISA (International Society of Automation)
The International Society of Automation (ISA) volunteers have worked long and hard to adapt the National Institute of Standards (NIST) for information technology (IT) systems to the security and operational requirements of operating technologies (OT). The ISA99 committee has produced policies and practices that, when implemented properly, go a long way towards achieving the security needed for industrial automated control systems.
ISA/IEC-62443 is a series of standards, technical reports, and related information that define procedures for implementing electronically secure Industrial Automation and Control Systems (IACS).
For businesses operating in Canada, information security is a must, like any other businesses operating elsewhere. While data breach notifications are not mandatory (except in Alberta and Ontario, New Brunswick, Newfoundland for health information), this may change with the possible passing of Digital Privacy Act, and with PCI compliance being a must to conduct business online, information security is vital.
4.1 Federal Privacy Laws
4.3 Ontario Privacy Laws
The Information and Privacy Commissioner of Ontario is responsible for overseeing and enforcing the following provincial access and privacy laws:
4.4 Other Related Laws in Ontario
Industry Standards
Data Center Standard
Independently verified Compliance:
TRA (Threat and Risk Assessment)
- Top Cyber Security Tools
- Top Internet / Network Tools
- Top Information Security Architect Related Resources
- Top Blog and Youtube Related Websites & Tools
- Top Application Security Tools
IT Service
1.1 ITIL v3 :
- ITIL service strategy - specifies that each stage of the service lifecycle must stay focused upon the business case, with defined business goals, requirements and service management principles.
- ITIL service design - provides guidance for the production and maintenance of IT policies, architectures and documents.
- ITIL service transition - focuses upon change management role and release practices, providing guidance and process activities for transitioning services into the business environment.
- ITIL service operation - focuses upon delivery and control process activities based on a selection of service support and service delivery control points.
- ITIL continual service improvement - focuses upon the process elements involved in identifying and introducing service management improvements, as well as issues surrounding service retirement.
1.2 IBM Maximo Asset Management : Maximo Asset Management is an Enterprise Asset Management system that provides comprehensive support for asset, maintenance, resource and parts supply chain management needs. Video Link . Includes following modules:
- Asset management
- Work management
- Inventory mnagement
- Procurement management
- Contract Management
- Service management
- KPIs/Reporting/Analysis
- Security/Administration
- Service-Oriented Architecture Platform
1.4 Marval IT Service Management (ITSM) MSM Software: MSM is an integrated, innovative, multi-level IT service management (ITSM) software solution - a secure, reliable, scalable and stable ITSM technology that supports IT business services and growth strategies of your organisation.
Security Framework
An information security framework is a series of documented processes that are used to define policies and procedures around the implementation and ongoing management of information security controls in an enterprise environment. These frameworks are basically a "blueprint" for building an information security program to manage risk and reduce vulnerabilities. Information security pros can utilize these frameworks to define and prioritize the tasks required to build security into an organization.
2.1 ISO27000
The ISO 27000 series of standards have been specifically reserved by ISO for information security matters.
- ISO27001:This is the specification for an information security management system (an ISMS) which replaced the old BS7799-2 standard.
- ISO/IEC 27001:2013 has ten short clauses, plus a long annex, which cover:
- 1. Scope of the standard
- 2. How the document is referenced
- 3. Reuse of the terms and definitions in ISO/IEC 27000
- 4. Organizational context and stakeholders
- 5. Information security leadership and high-level support for policy
- 6. Planning an information security management system; risk assessment; risk treatment
- 7. Supporting an information security management system
- 8. Making an information security management system operational
- 9. Reviewing the system's performance
- 10. Corrective action
- Annex A: List of controls and their objectives
- There are now 114 controls in 14 clauses and 35 control categories; the 2005 standard had 133 controls in 11 groups.
- A.5: Information security policies (2 controls)
- A.6: Organization of information security (7 controls)
- A.7: Human resource security - 6 controls that are applied before, during, or after employment
- A.8: Asset management (10 controls)
- A.9: Access control (14 controls)
- A.10: Cryptography (2 controls)
- A.11: Physical and environmental security (15 controls)
 A.12: Operations security (14 controls)
A.12: Operations security (14 controls)- A.13: Communications security (7 controls)
- A.14: System acquisition, development and maintenance (13 controls)
- A.15: Supplier relationships (5 controls)
- A.16: Information security incident management (7 controls)
- A.17: Information security aspects of business continuity management (4 controls)
- A.18: Compliance; with internal requirements, such as policies, and with external requirements, such as laws (8 controls)
- ISO 27002:This is the 27000 series standard number of what was originally the ISO 17799 standard (which itself was formerly known as BS7799-1)..
- ISO 27003:This will be the official number of a new standard intended to offer guidance for the implementation of an ISMS (IS Management System) .
- ISO 27004:This standard covers information security system management measurement and metrics, including suggested ISO27002 aligned controls..
- ISO 27005: This is the methodology independent ISO standard for information security risk management..
- ISO 27006: This standard provides guidelines for the accreditation of organizations offering ISMS certification.

2.2 COBIT
COBIT (Control Objectives for Information and Related Technologies) is a good-practice framework created by international professional association ISACA for information technology (IT) management and IT governance. COBIT provides an implementable "set of controls over information technology and organizes them around a logical framework of IT-related processes and enablers."
COBIT 5 is the only business framework for the governance and management of enterprise IT. , providing an end-to-end business view of the governance of enterprise IT that reflects the central role of information and technology in creating value for enterprises. In April 2012, COBIT 5 was released.
COBIT components include:
- Framework: Organizes IT governance objectives and good practices by IT domains and processes and link them to business requirements.
- Process descriptions: A reference process model and common language for everyone in an organization. The processes map to responsibility areas of plan, build, run, and monitor.
- Control objectives: Provides a complete set of high-level requirements to be considered by management for effective control of each IT process.
- Management guidelines: Helps assign responsibility, agree on objectives, measure performance, and illustrate interrelationship with other processes.
- Maturity models: Assesses maturity and capability per process and helps to address gaps.
2.3 NIST SP 800 - CYBERSECURITY FRAMEWORK (CSF)
National Institute of Standards and Technology (U.S. Department of Commerce)
"Security and Privacy Controls for Federal Information Systems and Organizations," provides a catalog of security controls for all U.S. federal information systems except those related to national security. The Cybersecurity Framework consists of three main components: the Core, Implementation Tiers, and Profiles.
The Framework Core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand. The Core guides organizations in managing and reducing their cybersecurity risks in a way that complements an organization’s existing cybersecurity and risk management processes.
The Framework Implementation Tiers assist organizations by providing context on how an organization views cybersecurity risk management. The Tiers guide organizations to consider the appropriate level of rigor for their cybersecurity program and are often used as a communication tool to discuss risk appetite, mission priority, and budget.
Framework Profiles are an organization’s unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core. Profiles are primarily used to identify and prioritize opportunities for improving cybersecurity at an organization.
-----------------------------------------------------------------------------------------------------------------------
There is overlap between those frameworks so "crosswalks" can be built to show compliance with different regulatory standards. For example, ISO 27002 defines information security policy in section 5; COBIT defines it in the section "Plan and Organize"; Sarbanes Oxley defines it as "Internal Environment"; HIPAA defines it as "Assigned Security Responsibility"; and PCI DSS defines it as "Maintain an Information Security Policy." By using a common framework like ISO 27000, a company can then use this crosswalk process to show compliance with multiple regulations such as HIPAA, Sarbanes Oxley, PCI DSS and GLBA, to name a few.
2.4 CIS CSC (Center for Internet Security - Critical Security Controls)
The Center for Internet Security Critical Security Controls for Effective Cyber Defense is a publication of best practice guidelines for computer security. The project was initiated early in 2008 as a response to extreme data losses experienced by organizations in the US defense industrial base and recently.[1] The publication was initially developed by the SANS Institute, ownership was transferred to the Council on Cyber Security (CCS) in 2013 and then transferred to Center for Internet Security (CIS) in 2015. It was earlier known as the Consensus Audit Guidelines and it is also known as the CIS CSC, CIS 20, CCS CSC, SANS Top 20 or CAG 20.The CIS Critical Security Controls provide a highly practical and useful framework for every organization to use for both implementation and assessment. Because the Controls are developed by the community and based on actual threat data, they are an authoritative, industry-friendly, and vendor-neutral approach to assessment and auditing of security. (V7.0)
- CSC 1: Inventory of Authorized and Unauthorized Devices
- CSC 2: Inventory of Authorized and Unauthorized Software
- CSC 3: Secure Configurations for Hardware and Software on Mobile Devices, Laptops, Workstations, and Servers
- CSC 4: Continuous Vulnerability Assessment and Remediation
- CSC 5: Controlled Use of Administrative Privileges
- CSC 6: Maintenance, Monitoring, and Analysis of Audit Logs
- CSC 7: Email and Web Browser Protections
- CSC 8: Malware Defenses
- CSC 9: Limitation and Control of Network Ports, Protocols, and Services
- CSC 10: Data Recovery Capability
- CSC 11: Secure Configurations for Network Devices such as Firewalls, Routers, and Switches
- CSC 12: Boundary Defense
- CSC 13: Data Protection
- CSC 14: Controlled Access Based on the Need to Know
- CSC 15: Wireless Access Control
- CSC 16: Account Monitoring and Control
- CSC 17: Security Skills Assessment and Appropriate Training to Fill Gaps
- CSC 18: Application Software Security
- CSC 19: Incident Response and Management
- CSC 20: Penetration Tests and Red Team Exercises
2.5 ISA (International Society of Automation)
The International Society of Automation (ISA) volunteers have worked long and hard to adapt the National Institute of Standards (NIST) for information technology (IT) systems to the security and operational requirements of operating technologies (OT). The ISA99 committee has produced policies and practices that, when implemented properly, go a long way towards achieving the security needed for industrial automated control systems.
ISA/IEC-62443 is a series of standards, technical reports, and related information that define procedures for implementing electronically secure Industrial Automation and Control Systems (IACS).
Security Models
- CIA Triad : Confidentiality, integrity and availability, also known as the CIA triad, is a model designed to guide policies for information security within an organization. The model is also sometimes referred to as the AIC triad (availability, integrity and confidentiality) to avoid confusion with the Central Intelligence Agency. The elements of the triad are considered the three most crucial components of security. Confidentiality is a set of rules that limits access to information, integrity is the assurance that the information is trustworthy and accurate, and availability is a guarantee of reliable access to the information by authorized people.
- Cisco offers the integrated security solution, which delivers services above and beyond the "one size fits all" model. In addition, Cisco services are designed to deliver value throughout the entire network life cycle that includes the stages of prepare, plan, design, implement, operate, and optimize (PPDIOO). the Cisco PPDIOO model, encompasses all the steps from network vision to optimization, enabling Cisco to provide a broader portfolio of support and end-to-end solutions to its customers.
- Cisco Network Security Design Steps: Following a structured set of steps when developing and implementing network security will help you address the varied concerns that play a part in security design. Many security strategies have been developed in a haphazard way and have failed to actually secure assets and to meet a customer's primary goals for security. Breaking down the process of security design into the following steps will help you effectively plan and execute a security strategy:
- Identify network assets.
- Analyze security risks.
- Analyze security requirements and tradeoffs.
- Develop a security plan.
- Define a security policy.
- Develop procedures for applying security policies.
- Develop a technical implementation strategy.
- Achieve buy-in from users, managers, and technical staff.
- Train users, managers, and technical staff.
- Implement the technical strategy and security procedures.
- Test the security and update it if any problems are found.
- Maintain security.
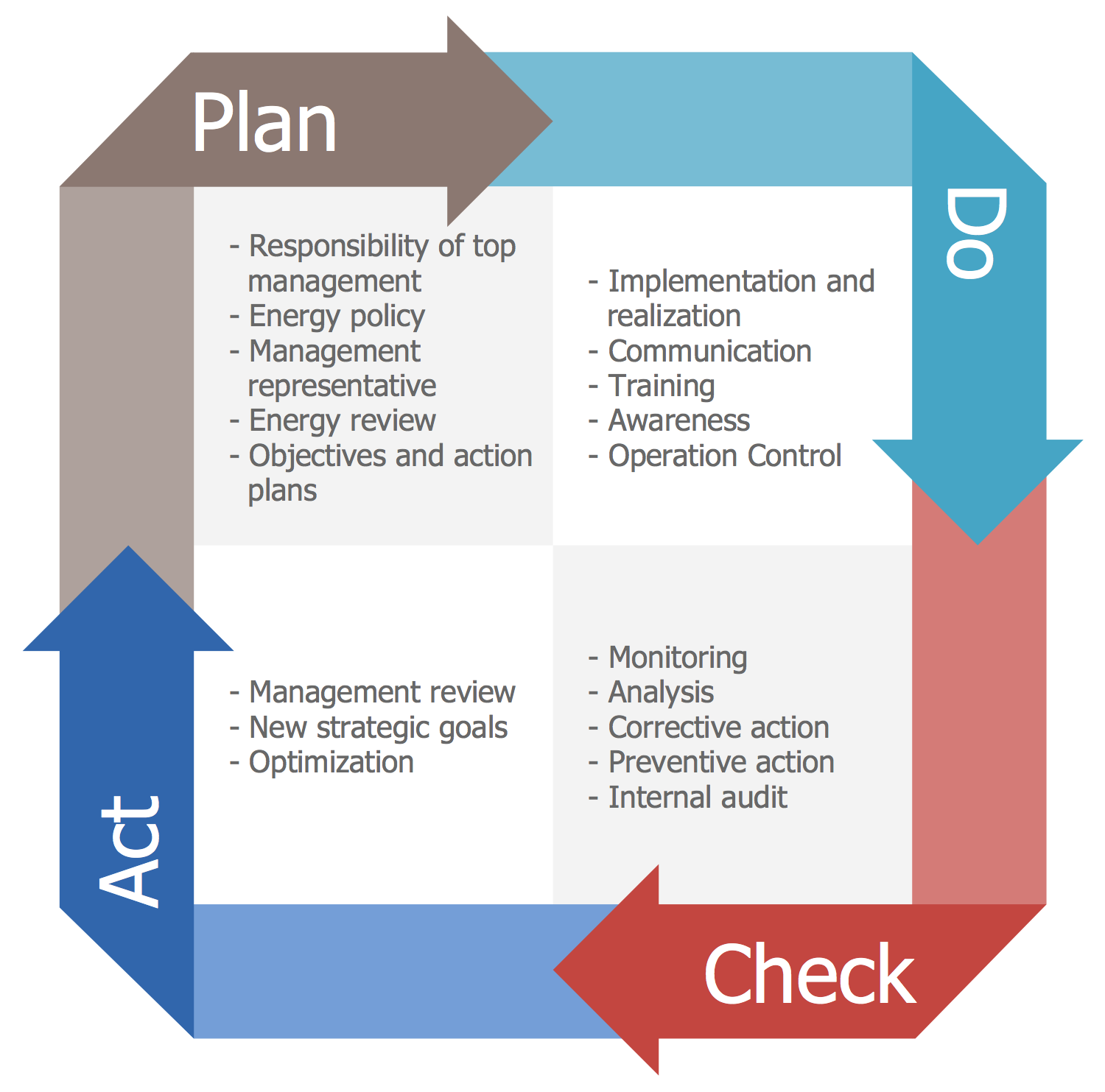
- PDCA (plan-do-check-act): PDCA (plan-do-check-act, sometimes seen as plan-do-check-adjust) is a repetitive four-stage model for continuous improvement (CI) in business process management.PDCA was popularized by Dr. W. Edwards Deming, an American engineer, statistician and management consultant. Deming is often considered the father of modern quality control (QC).
Information Security Related Laws, Acts, Industry Standards (Canada)
4.1 Federal Privacy Laws
- The Personal Information Protection and Electronic Documents Act (PIPEDA) - which covers how businesses handle personal information.
- PIPEDA sets the ground rules for how private-sector organizations collect, use, and disclose personal information in the course of for-profit, commercial activities across Canada. It also applies to the personal information of employees of federally-regulated businesses such as:banks, airlines, telecommunications companies. Ratified in 2004.
- In 2015, the Canadian government passed the Digital Privacy Act (DPA), giving Canadian businesses mandatory breach notification requirements and harsh penalties if they don’t adhere. As of November 1, 2018, organizations in Canada subject to the Personal Information Protection and Electronic Documents Act (PIPEDA) will face strict and onerous new privacy breach response requirements with respect to any data security safeguard breach. Under the Digital Privacy Act, every organization that collects, uses and discloses personal information in the course of commercial activity in Canada (with a few exceptions) must follow new mandatory data breach record-keeping, reporting and notification rules – or face significant non-compliance consequences.
- The Privacy Act - which covers how the federal government handles personal information; The Privacy Act only applies to federal government institutions listed in the Privacy Act Schedule of Institutions. It applies to all of the personal information that the federal government collects, uses, and discloses. This includes personal information about federal employees.
- Criminal Code of Canada
- Unauthorized use of a Computer (s. 342.1);
- Identity Theft (s56.1, s402.1);
- Mischief s. 430.(1.1);
- Obscenity (s. 163);Corrupting Morals s. 163);
- Making, Distributing, Selling, or Possession of Child Pornography s. 163.1).
- Luring Children (s. 172.1);
- Interception of Private Communication (s. 184);
- Making Threats (s. 264);
- Harassment (s. 264.1);
- Promoting Hatred (s. 319);
- Theft of Telecommunications Services (s. 326)
- Devices to Break into Computers (s. 342.2);
- Possession of Credit Card Data (s. 342.3)
- Personation (s403);
- Making Likenesses of bank notes with computer assistance (s. 457);
- Counselling the Commission of an Offence (s. 464); and
- Directing Criminal Offences for Criminal Organizations (s. 467.13),
- Copyright Act
- Copyright Modernization Act
Legislation relevant to Policy on Government Security includes the following:
- Access to Information Act
- Canada Evidence Act
- Canada Labour Code
- Canada Occupational Health and Safety Regulations
- Canadian Charter of Rights and Freedoms
- Canadian Human Rights Act
- Canadian Security Intelligence Service Act
- Criminal Code
- Criminal Records Act
- Defence Production Act
- Department of Foreign Affairs and International Trade Act
- Emergency Management Act
- Federal Real Property and Federal Immovables Act
- Financial Administration Act
- Interpretation Act
- Library and Archives of Canada Act
- National Defence Act
- Privacy Act
- Public Servants Disclosure Protection Act
- Public Service Employment Act
- Public Service Labour Relations Act
- Royal Canadian Mounted Police Act
- Security of Information Act
- Statistics Act
- Youth Criminal Justice Act
Treasury Board policies, directives and standards relevant to this policy include the following:
- Access to Information, Policy on
- Communications Policy of the Government of Canada
- Contracting Policy
- Controlled Goods Directive
- Departmental Security Management, Directive on
- Evaluation, Policy on
- Identity Management, Directive on
- Information Management Roles and Responsibilities, Directive on
- Federal Identity Program
- Fire Protection, Investigation and Reporting, Policy on
- Foundation Framework for Treasury Board Policies
- Information and Technology, Policy Framework for
- Information Management, Policy on
- Integrated Risk Management Framework
- Internal Audit, Policy on
- Internal Controls, Policy
- Learning, Training, and Development, Policy on
- Long-term Capital Plans, Policy on
- Losses of Money and Offences and Other Illegal Acts Against the Crown, Policy on
- Management of Assets and Acquired Services, Policy Framework for the
- Management of Compensation, Policy Framework for the
- Management of Information Technology, Policy on
- Management of Materiel, Policy on
- Management of Real Property, Policy on
- Management, Resources and Results Structure, Policy on
- Occupational Safety and Health
- Official Languages for Human Resources Management, Policy on
- Official Languages Policy Framework
- Operational Security Standard—Business Continuity Planning (BCP) Program
- Operational Security Standard - Management of Information Technology Security (MITS)
- Operational Security Standard - Physical Security
- Personnel Security Standard
- Privacy Protection, Policy on
- Project Management Policy
- Risk Management, Policy on
- Security and Contracting Management Standard
- The Values and Ethics Code for the Public Service
4.3 Ontario Privacy Laws
The Information and Privacy Commissioner of Ontario is responsible for overseeing and enforcing the following provincial access and privacy laws:
- FIPPA - Freedom of Information and Protection of Privacy Act, Ontario’s provincial public sector privacy law; FIPPA (The Freedom of Information and Protection of Privacy Act) came into force on Jan 1, 1988.
- MFIPPA - Municipal Freedom of Information and Protection of Privacy Act, Ontario’s municipal public sector privacy law; MFIPPA became law 3 year later on jan 1, 1991
- PHIPA - Personal Health Information Protection Act, 2004, Ontario’s privacy law relating to health records that has been that has been deemed “substantially similar” to the federal private sector privacy law with respect to health information custodians. PHIPA includes schedules A and B came into force on Nov 1, 2004.
4.4 Other Related Laws in Ontario
- Archives and Recordkeeping Act, 2006
- Private Security and Investigative Services Act, 2005,
- Securities Act, R.S.O. 1990,
- Ontario Human Rights Code
- Technical standards
- Architecture standards
- Information standards
- Information Technology Service Management
- Green IT standards
- Networking standards
- Security standards
- Enterprise products
Other Law, Industry Related Standards
Information Security Related Laws, Acts, Industry Standards (U.S.)
- HIPAA (Health Insurance Portability and Accountability Act) :HIPAA (Health Insurance Portability and Accountability Act of 1996) is United States legislation that provides data privacy and security provisions for safeguarding medical information.
- The Sarbanes-Oxley Act of 2002, popularly known as SOX, also known as the "Public Company Accounting Reform and Investor Protection Act" (in the Senate) and "Corporate and Auditing Accountability, Responsibility, and Transparency Act" (in the House) and more commonly called Sarbanes–Oxley, Sarbox or SOX, is a United States federal law that set new or expanded requirements for all U.S. public company boards, management and public accounting firms. There are also a number of provisions of the Act that also apply to privately held companies; for example, the willful destruction of evidence to impede a Federal investigation. The bill, which contains eleven sections, was enacted as a reaction to a number of major corporate and accounting scandals, including Enron and WorldCom. The sections of the bill cover responsibilities of a public corporation’s board of directors, adds criminal penalties for certain misconduct, and required the Securities and Exchange Commission to create regulations to define how public corporations are to comply with the law.
Industry Standards
- Payment Card Industry Data Security Standard (PCI DSS) - The Payment Card Industry Data Security Standard (PCI DSS) is a widely accepted set of policies and procedures intended to optimize the security of credit, debit and cash card transactions and protect cardholders against misuse of their personal information. The PCI DSS was created jointly in 2004 by four major credit-card companies: Visa, MasterCard, Discover and American Express.
- Service Organization Control (SOC) 2 - SOC 2 is an auditing procedure that ensures your service providers securely manage your data to protect the interests of your organization and the privacy of its clients. For security-conscious businesses, SOC 2 compliance is a minimal requirement when considering a SaaS provider. The SOC 2 report focuses on a business’s non-financial reporting controls as they relate to security, availability, processing integrity, confidentiality, and privacy of a system, as opposed to SOC 1/SSAE 16 which is focused on the financial reporting controls.
- GDPR (European Union)- When the General Data Protection Regulation (GDPR) goes into effect on May 25, 2018, all companies doing business with individuals in the European Union must comply with the law’s far-reaching data privacy provisions.
Data Center Standard
- SAS 70 - The Statement on Auditing Standard No. 70 was the original audit to measure a data center’s financial reporting and recordkeeping controls.
- SSAE 16 - The Statement on Standards for Attestation Engagements No. 16 replaced SAS 70 in June 2011. A SSAE 16 audit measures the controls relevant to financial reporting.
- SOC 1 - The first of three new Service Organization Controls reports developed by the AICPA, this report measures the controls of a data center as relevant to financial reporting. It is essentially the same as a SSAE 16 audit.
- SOC 2 - This report and audit is completely different from the previous. SOC 2 measures controls specifically related to IT and data center service providers. The five controls are security, availability, processing integrity (ensuring system accuracy, completion and authorization), confidentiality and privacy. There are two types:
- Type 1 – A data center’s system and suitability of its design of controls, as reported by the company.
- Type 2 – Includes everything in Type 1, with the addition of verification of an auditor's opinion on the operating effectiveness of the controls.
- SOC 3- This report includes the auditor’s opinion of SOC 2 components with an additional seal of approval to be used on websites and other documents. The report is less detailed and technical than a SOC 2 report.
- EU-U.S. Privacy Shield - What is the EU-U.S. Privacy Shield? Privacy Shield replaces Safe Harbor as the new law maintaining the privacy and integrity of personal data. Different from HIPAA, PCI and SOX compliance requirements, Privacy Shield was developed by the U.S. Department of Commerce along with the European Commission on Data Protection.
Architecture Tools
- hiMate modelling tool
- UML modelling language
- IBM System Architect modelling tool
| Framework | Description |
|---|---|
| Open Group Architecture Framework Version 9 (TOGAF 9) | This framework is provided with the product. |
| Zachman Framework | This framework is provided with the product. |
| Department of Defense Architecture Framework Version 2.0 (DoDAF 2.0) | This framework from the U.S. federal government requires a DoDAF license. |
| Department of Defense Architecture Framework Version 1.5 (DoDAF 1.5) | The product supports both the standard version and the Activity Based Method (ABM) version of DoDAF 1.5. |
| Ministry of Defence Architecture Framework Version 1.2 (MODAF 1.2) | This framework from the UK federal government requires a MODAF license. |
| NATO Architecture Framework Version 3.0 (NAF 3.0) | This framework requires a NAF license. |
| Integrated Architecture Framework (IAF) | This framework from Capgemini requires an additional license and installation. |
| Federal Enterprise Architecture (FEA) reference models | These models require an FEA license. |
| Supply Chain Operations Reference (SCOR) reference models | These reference models require an additional license and the installation of an encyclopedia. |
| Telemanagement (TM) Forum reference models | These reference models include both Enhanced Telecom Operations Map (eTOM) models and New |
Compliance, Documents Mgmt, Project Mgmt
Independently verified Compliance:
- ISO27001
- ISO27018
- SOC 1,2,3 Type 2
- CSA STAR 1
Idustry-Specific Compliance:
- PCI DSS Level 1
- HIPAA BAA
- FERPA
- CDSA
- SOX
- FFIEC, CAT
- NERC CIP
- NIST SP 800-37 and 800-53
Tools:
- CompliantPro is a robust, extremely flexible, web-based compliance software system for proactively managing compliance to a variety of regulations and standards. The software provides the core functionality to manage processes for communicating, monitoring and documenting your diverse compliance activities.
- https://www.sciforma.com/ - Program and Portfolio Management
- OpenText
- Upland Eclipse PPM: Eclipse PPM is one of the better online project management solutions to help you achieve strategic alignment across multiple projects.

Audit
- SSAE 16
- SOC 2
- ISO 27001
- FedRAMP
- The Federal Risk and Authorization Management Program, or FedRAMP, is a program by which the U.S. federal government determines whether cloud products and services are secure enough to be used by federal agencies.Strictly speaking, FedRAMP is a risk management program. It was created to support the federal Cloud First policy, which was rolled out in 2011 and aimed to rationalize the federal government's sprawling, fragmented IT infrastructure by moving much of it to the cloud. The FedRAMP program seeks to make it clear how FISMA's requirements apply to cloud services.
- FISMA
- Federal Information Security Management Act (2002) assigns responsibilities to various agencies to ensure the security of data in the federal government. The act requires program officials, and the head of each agency, to conduct annual reviews of information security programs, with the intent of keeping risks at or below specified acceptable levels in a cost-effective, timely and efficient manner. The National Institute of Standards and Technology ( NIST ) outlines nine steps toward compliance with FISMA:
- Categorize the information to be protected.
- Select minimum baseline controls.
- Refine controls using a risk assessment procedure.
- Document the controls in the system security plan.
- Implement security controls in appropriate information systems.
- Assess the effectiveness of the security controls once they have been implemented.
- Determine agency-level risk to the mission or business case.
- Authorize the information system for processing.
- Monitor the security controls on a continuous basis.
- NIST SP 800-53A
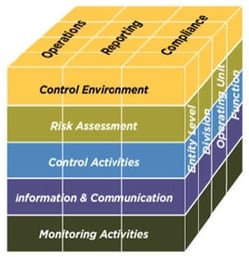
- COSO- Internal Control Guidence : the COSO framework has three dimensions:
- The nature of the control objectives i.e.
- operations,
- financial reporting,
- compliance
- The organizational breadth of the company i.e.,
- enterprise level,
- business unit level,
- activity / process level
- The five components of effective internal control i.e.
- Control Environment,
- Risk Assessment,
- Control Activities,
- Information and Communication and Monitoring
Privacy
- Privacy Shield
- EU GDPR
Investigations
- eDiscovery
- Forensics
Risk Frameworks
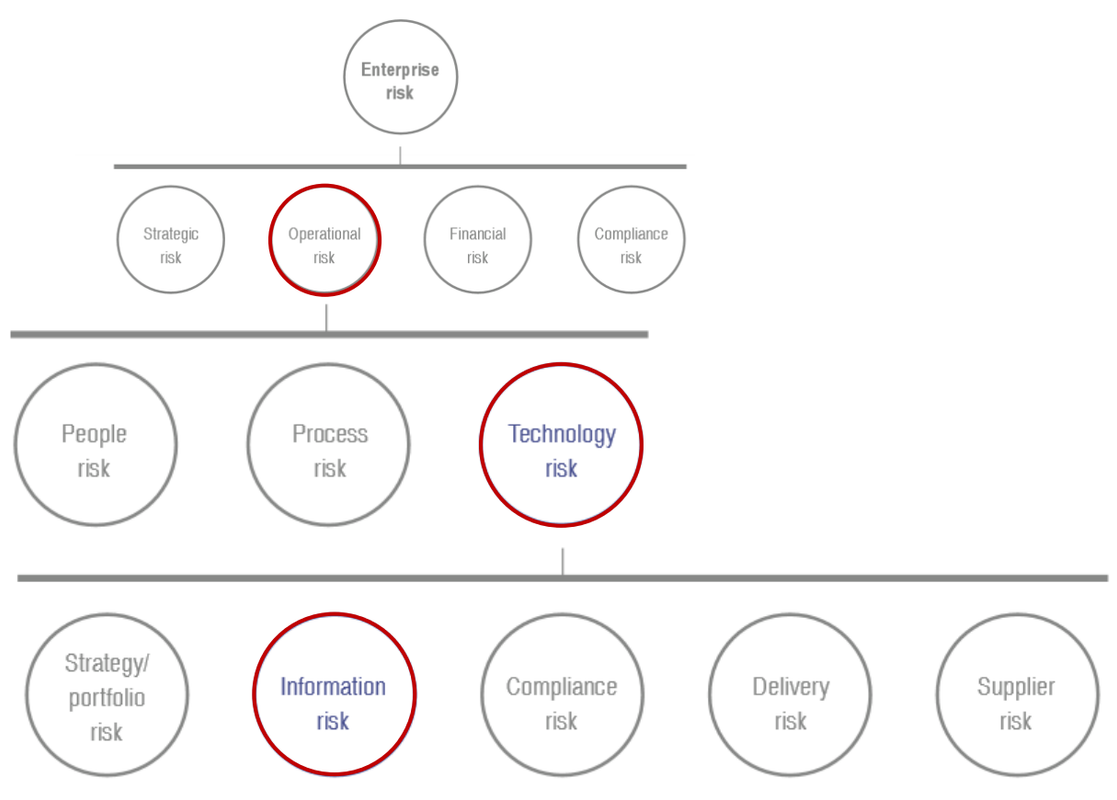 |
| Enterprise Risk to Operation Risk to Technology Risk to Information Risk |
- FAIR
- NIST RMF
- OCTAVE
- TARA
- COSO+WBCSD ERM (Enterprise Risk Management)
TRA (Threat and Risk Assessment)
- Harmonized TRA Methodology (TRA-1)
- Harmonized TRA (HTRA) Methodology (Threat and Risk Assessment Tool)
- Identify Assets
- Identify Threats
- Identify Vulnerabilities
- Calculate Residual Risks
- Monitor and Report
- Information Risk Assessment Methodology 2 (IRAM2)
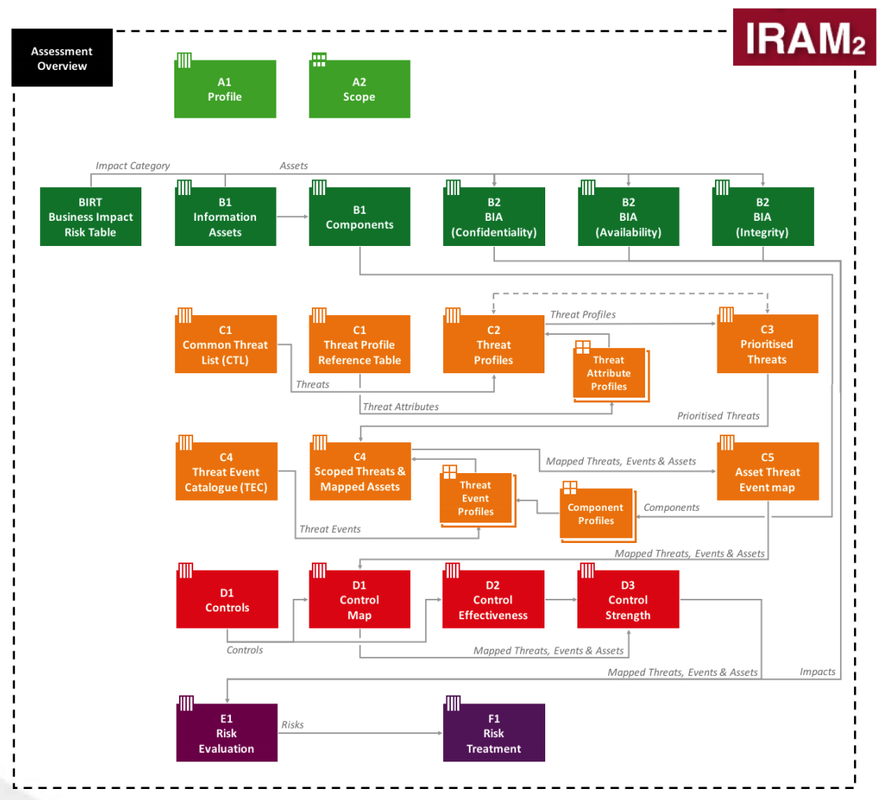
IRAM2 Components Review - Scoping
- Develop a profile of the environment
- Develop the scope for the assessment
- Business Impact Assessment
- Identify the information assets
- Assess business impact
- Threat Profiling
- Populate the threat landscape
- Profile threats
- Produce a prioritized threat landscape
- Scope and map threat events
- Identify and map assets impacted to threat events
- Vulnerability Assessment
- Identify vulnerabilities and related controls
- Assess effectiveness of identified controls
- Determine the control strength for each combination of threat event and component
- Risk Evaluation
- Derive the likelihood of success
- Derive the residual likelihood
- Determine the residual business impact rating
- Derive the residual risk rating
- Risk Treatment
- Evaluate each risk against the risk appetite
- Create a risk treatment plan
- Execute the risk treatment plan and validate results
Incident Responding
CyberSecurity Assessment Tools
- Federal Financial Institutions Examination Council (FFIEC) - Cybersecurity Assessment Tool
- Free NIST CSF Maturity Tool
- Microsoft Cybersecurity Reference Architectures
- The Chief Information Security Officer (CISO) Workshop Training








This comment has been removed by a blog administrator.
ReplyDeleteThis comment has been removed by a blog administrator.
ReplyDelete