There are some other related posts in this blog:
Security Tools
DevOps
There are five type of main testing methodologies:
- Top Cyber Security Tools
- Top Internet / Network Tools
- Top Information Security Architect Related Resources
- Top Blog and Youtube Related Websites & Tools
- Top Application Security Tools
Web Application Vulnerability Scanner
Tools:
- Acunetix: Docs and Docker to be deployed on prem for testing
- Qualys : Free trial
- Rapid 7 - InisghtVM
- Security For Everyone - https://securityforeveryone.
com/ - Contrast : Community Version
- Nessus : Try Nessus Pro for free - https://www.tenable.com/try
- Hostedscan.com
- Securityforeveryone.com
Application Firewall
WAF
- Web Application and API Protection Reviews and Ratings
- Gartner Magic Quadrant for Web Application Firewalls
- Indusface WAS Free - https://apptrana.indusface.com/
- Cloudflare (Similar product is Sucuri at https://sucuri.net/, but no free version, only free trials)
- Free with support community forums and documentation
- 5 active Firewall Rules
- based on AS number, Cookie, Country, Continent, hostnae, IP Source Address, Referrer, request Medhods, Certificate, Bots, Threat Scores etc
- Action can be Block, JS Callenge, Captcha, Allow, and Bypass
- Simple Bot Mitigation
- Unmetered DDoS mitigation
- Globally Load Balaced CDN
- Universal SSL Certificate
- NGINX ModSecurity WAF - (Open Source WAF - ModSecurity at Github, For ModSecurity-Nginx at Github)
- Detect and stop a broad range of Layer 7 attacks
- SQL injection (SQLi), cross‑site scripting (XSS), and Local File Include (LFI)
- Cross‑site request forgery (CSRF), Remote File Include (RFI), remote code execution (RCE), and HTTP protocol violations
- Other common attack vectors
- Automatically block traffic from known malicious IP addresses:
- Look up IP addresses in Project Honey Pot database in real time and deny access to denylisted users
- Cache results from lookups for up to 24 hours to improve performance
- Set up your own honey pot of malicious IP addresses and contribute back to the community
- Get detailed logs for auditing and visibility:
- Detailed information about all transactions, including requests, responses, and details as to which rules were activated
- Remote syslogging for archival and centralized analysis
- AWS WAF - Similar product is Azure WAF
- The solution is just an add-on to an existing subscription to cloud services such as the Amazon content delivery network and Application Load Balancer.
- Web Traffic Filtering
- Bot Control
- API
- Real Time Visibility
- Integration with AWS Firewall Manager
- Web ACL $5 / month
- Rule $1 / month
- Request $0.60 per 1 million requests
- Imperva WAF (8 Times Leader in Gartner Report), similar product will be Akamai (best product for DDoS mitigation).
- Free Trial. But it will be very expensive after trial.
- Secure cloud and on-prem apps.
- Stop OWASP Top 10 and Automated Top 20.
- Attack detection
- SIEM integration
- Extensive reporting
Security Tools
- https://www.hardenize.com/ - Check your site's security situation.
- Static and Dynamic Analysis Tools: Fortify, AppScan
- Penetration Testing Tools: Burp Suite
- Fuzz Tools: OWASP Fuzz tool
- D盾_Web查杀 : 『D盾_防火墙』专为IIS设计的一个主动防御的保护软件,以内外保护的方式 防止网站和服务器给入侵,在正常运行各类网站的情 况下,越少的功能,服务器越安全的理念而设计! 限制了常见的入侵方法,让服务器更安全!
Application Vulnerabilities
- OWASP Top 10 (OWASP Top 10 (2010, 2013, 2017,2021))
- WASC TCv2 (WASC Threat Classification v2.0) Web Application Security Consortium Threat Classification
- CWE 25
- CWE™ (Common Weakness Enumeration) is a community-developed list of common software security weaknesses. It serves as a common language, a measuring stick for software security tools, and as a baseline for weakness identification, mitigation, and prevention efforts.a
Web Application Speed Testing
- https://www.dotcom-tools.com/
- https://gf.dev/website-audit - Website Audit for Best practices, Performance and SEO
- https://performance.sucuri.net/ - Test how fast is your site's performance from across the globe
- https://gtmetrix.com/ - See how your site performs, reveal why it's slow and discover optimization opportunities. It can compare multiple sites in one page.
- https://tools.pingdom.com/ - test the page load time, analyze it and find bottlenecks
- https://www.webpagetest.org - Run a free website speed test from multiple locations around the globe using real browser at real consumer connection speed.
- https://www.websitepulse.com/help/testtools.web-page-test.html
- https://www.site24x7.com/web-page-analyzer.html
Application Development
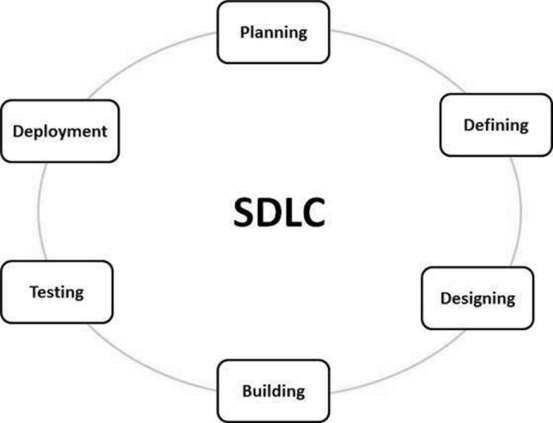
- SDLC : SDLC is Software Development Life Cycle. It is the process by which Information Systems or Software are developed and designed. Like every other process, SDLCs have various methods to complete the steps.
- One of the oldest ways to go about is the Waterfall method. The first known usage of Waterfall was in 1956 by Herbert D. Benington at Symposium on advanced programming methods for digital computers. One of the major competitions that Waterfall method faces is the Agile Method. The waterfall method goes through the phases of Conception, Initiation, Analysis, Design, Construction, Testing, Production/Implementation, and Maintenance one after the other like the motion of a waterfall. The team cannot move on to a phase till the previous phase is complete. The positive thing about this method, even though it is time consuming, is that if the bugs are found early on it saves a lot of time and money later. For instance if a bug is found in the conception or initiation phase then it can be corrected before going to the design phase rather than it being discovered while the software is getting designed and then has to be scrapped completely. This method requires intensive documentation in each phase and in that way the process is not dependent on any individual on the team. If a component of the team needs to be replaced, the new person can understand where the project is currently, easily.
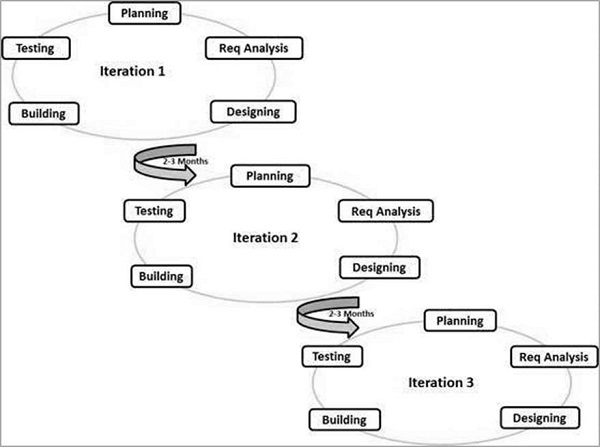
- The Agile method on the other hand is an iterative and incremental approach to software development. In this form of SDLC small modules of the final products are released for the users to review and then are changed accordingly. As per the name, this environment is flexible and can be changed according to the circumstances. Here different developers work on their own task simultaneously and then combine their work in the end. The focus is on delivering a working software rather than documentation. Since it’s iterative, that means it works in cycles. New things are discovered during each iteration and then can be improved upon or fixed before the next cycle begins. Communication, rather than documentation, is used and as such it is faster to work in an Agile environment. Agile methods seem best for developmental and non-sequential projects; as such they are ineffectual in some types of projects and is not taken seriously by a lot of companies.

| SDLC Model |
Advantage
|
Disadvantage
|
| WaterFall |
Simple and easy to understand and use Easy to manage due to the rigidity of the model. Each phase has specific deliverables and a review process. Phases are processed and completed one at a time. Works well for smaller projects where requirements are very well understood. Clearly defined stages. Well understood milestones. Easy to arrange tasks. Process and results are well documented. |
No working software is produced until late during the life cycle. High amounts of risk and uncertainty. Not a good model for complex and object-oriented projects. Poor model for long and ongoing projects. Not suitable for the projects where requirements are at a moderate to high risk of changing. So, risk and uncertainty is high with this process model. It is difficult to measure progress within stages. Cannot accommodate changing requirements. Adjusting scope during the life cycle can end a project. Integration is done as a "big-bang. at the very end, which doesn't allow identifying any technological or business bottleneck or challenges early. |
| Agile | Is a very realistic approach to software development. Promotes teamwork and cross training. Functionality can be developed rapidly and demonstrated. Resource requirements are minimum. Suitable for fixed or changing requirements Delivers early partial working solutions. Good model for environments that change steadily. Minimal rules, documentation easily employed. Enables concurrent development and delivery within an overall planned context. Little or no planning required. Easy to manage. Gives flexibility to developers. |
Not suitable for handling complex dependencies. More risk of sustainability, maintainability and extensibility. An overall plan, an agile leader and agile PM practice is a must without which it will not work. Strict delivery management dictates the scope, functionality to be delivered, and adjustments to meet the deadlines. Depends heavily on customer interaction, so if customer is not clear, team can be driven in the wrong direction. There is a very high individual dependency, since there is minimum documentation generated. Transfer of technology to new team members may be quite challenging due to lack of documentation. |
- REST based Services/Architecture VS RESTFUL Services/Architecture
- It should be stateless
- It should access all the resources from the server using only URI
- It does not have inbuilt encryption
- It does not have session
- It uses one and only one protocol that is HTTP
- For performing CRUD operations, it should use HTTP verbs such as get, post, put and delete
- It should return the result only in the form of JSON or XML, atom, OData etc. (lightweight data )
- SonarQube
- VeraCode
- Fortify SCA and Fortify WebInspect
- IBM AppScan
DevOps
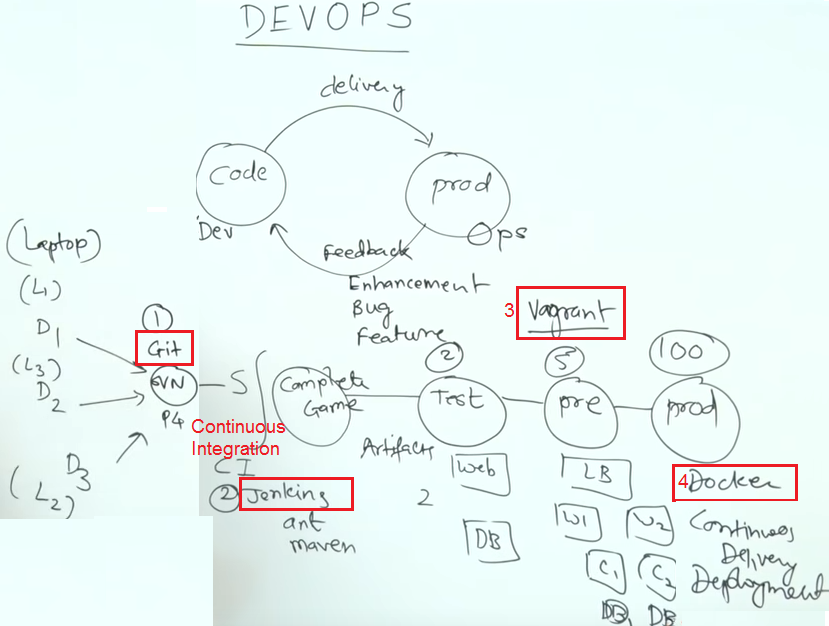 |
| From: https://www.youtube.com/watch?v=7LcFZNuZaVY |
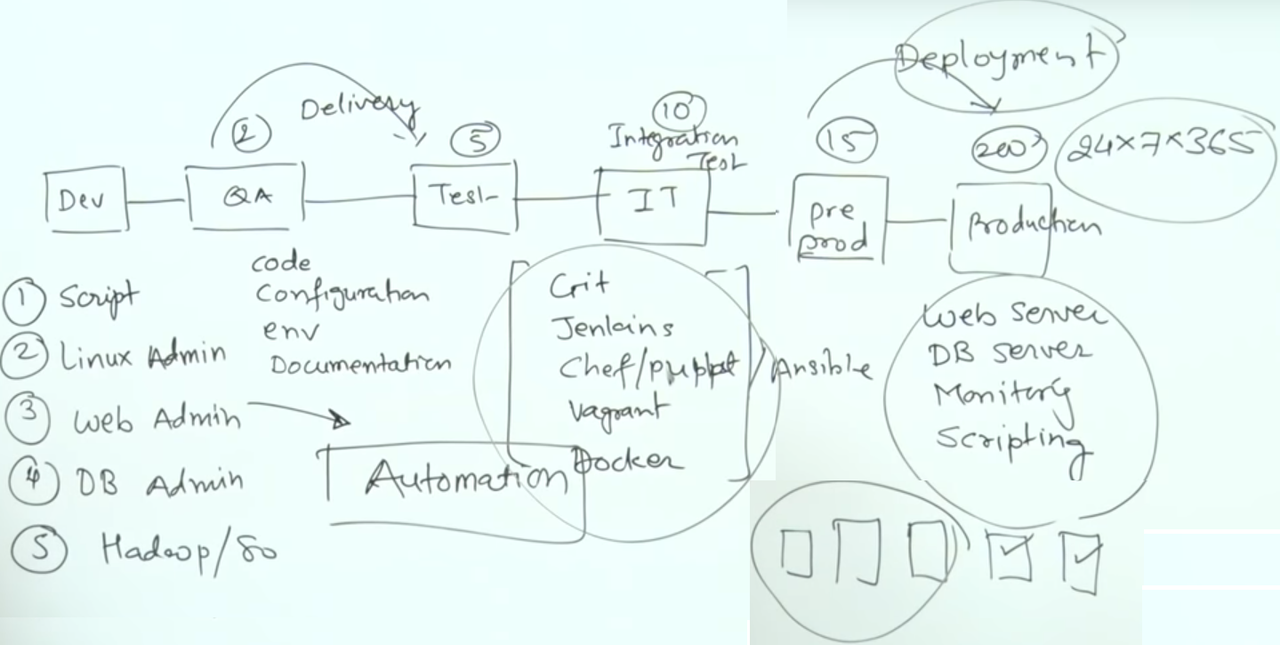 |
| From: https://www.youtube.com/watch?v=7LcFZNuZaVY |
Application Test Methodologies with Tools
Depends on where your application is, there are three categories for application testing. Each category will have a different types of testing.
Guru99 has a good liste for the types of testing (https://www.guru99.com/application-testing.html)
There are five type of main testing methodologies:
- Black Box Testing:
- White Box Testing:
- Gray Box Testing:
- Static Application Security Testing (SAST) – Big software organizations worldwide are gravitating towards CICD, Agile and DevOps setups. SAST solutions have all the characteristics to blend into these Software Life Cycle’s. Code can be scanned fast, vulnerabilities are located accurately and untouched code doesn’t have to be re-scanned.
- Dynamic Application Security Testing (DAST) – While DAST tools provide risk analysis and assist in the remediation efforts, developers don’t really know where exactly the vulnerabilities are located, not do they always now what countermeasures to implement. DAST methodology reporting is less than satisfactory in numerous instances.
Some popular testing Tools in the market:
- Xray
- Selenium
- Appium
- Cucumber
- Eggplant Functional
- Katalon Studio
Here are some extra tools recommended from Guru99 as well.
- Rational Robot (From The International Business Machines Corporation (IBM))
- IBM Rational Functional Tester
- HP Loadrunner (Performance Test Results produced by HP Loadrunner are used as a benchmark against other tools.)
- Apache Jmeter Application
Application Test Example:
One Good Practice from Security Compass:
Web Server Scans
- Full TCP /UDP Port Scans
- Web Server Scans
- Nikto (www.cirt.net)
- Spike Web Proxy (www.immunitiysec.com)
- Stealth Scanner (www.nstalker.com) Free/Commercial
- SSL Version (40/56/128 Bit)
- Administrator Port
- Internal IP
- Internal Port
- Internal Server Name
- Load Balancer
Web Application: Background Information on the site
- Identify Technologies used and application architecture
- Mirror site
- Sift through client side code (review comments and client side code)
- Authenticate to the site and browse the site
- Document all the links and pages on the site
Web Applications: Threat Analysis
Web Application: Begin Testing of the Web Application
- Configuration Management (Web Server)
- Backup Files (.bak / .inc/ .gz / .zip)
- Autehntication (ACLS on Files / ACLs on Data / Cookies)
- Session / Cookie Management
- Input Validation (XSS/SQL Injection / Field Overflows / Field Underflow)
- Hiddent Tags / Hidden Cookie variables / Hidden Pages
- File Upload ( File Type / Location of upload)
- Buffer Overflows (ISAPI/Modules)
- Cryptography
- Sensitive Data
Web Application: Search Engine Hacking
- groups.google.com
- yahoo.com
- archive.org
Authentication
Authorization
Session Management
User Management
Cryptography, PII, Critical Data
Data Validation
Data Handling
Error & Exception
Event Logging
Windows System/Appication Test Software
- Sandboxie, which lets you run programs independent of the rest of your system. That way they can't infect, access, or otherwise interfere with your Windows installation. It supports 64bits and Win8.
- PowerShadow works both pro-actively and protectively to shield you from anything that threatens the life of your computer system. Installation of PowerShadow is like planting an amazing protection mechanism called the Shadow Mode. It is designed to defend you against millions of viruses, spyware and Trojan horse that would love to invade your system.
Security Awareness Education
- Security Education Platform - Wombat, (Now it is part of Proofpoint) Leader in the Magic Quadrant for Security Awareness Computer-Based Training (CBT).
- Knowbe4
- Phishlabs.com - Fortra
Security Assessment Methodology
- B.A.S.E - SANS.org
- Baseline,
- Audit & Assess
- Secure the environment
- Evaluate & Education
- NIST 800-37 Risk Management Framework (RMF) - Six Main Steps + One Preparatory Step
- Prepare
- Categorize
- Select
- Implement
- Assess
- Authorize
- Monitor
Digital Forensic Investigation Tools
Standard Development and Productivity Tools
- Integrated Development Environments (IDEs) : Eclipse
- Version Control Systems: Git
- Defect/Issue Tracking Systems: Jira
Application Automation Tools
- Jenkins, an automation server that may be utilized either as simple CI servers, or turned into CD hubs for projects, with plugins that support integration with various tools in the CI/CD toolchain.
- Docker, a software container technology platform that enables its users to create, deploy, run, and manage applications within the containers. Docker containers run within the kernel of the host machine and they don’t require additional hypervisor load, so they are lightweight.
- Kubernetes is an open-source system for automating deployment, scaling, and management of containerized applications.
- Chef, a configuration management tool that delivers fast, scalable, and flexible automation of Web-scale IT. Chef automation tool uses ‘recipes’ for web-server configuration, databases and load balancers.
- Puppet, a flexible, cross-platform and open source DevOps configuration management tool that automates the delivery and operation of a software during its entire lifecycle.
- Ansible, a server and configuration management tool that makes IT automation simple as it ends repetitive tasks and enables faster application deployments. It automates configuration management, orchestration, application deployment, cloud provisioning, and a number of other IT requirements.
- Other tools/frameworks for adding security to the DevOps pipeline include Gauntlt and OWASP Zed Attack Proxy (ZAP). These tools may be used during deployment, allowing for automated security tests. Gauntlt provides hooks to a variety of organizational tools that are used for security testing such as nmap, curl, sqlmap, and others. There are also tools such as Splunk that should be mentioned here, primarily for continuous monitoring of the production environment for detection of cybersecurity threats.
DB Related Tools
- Generate Data for Testing - https://www.generatedata.com/
- https://www.guru99.com/application-testing.html








No comments:
Post a Comment