Steps to Scan and Fix your System
1 Download Malwarebytes
When the install completes or Malwarebytes is already installed do the following:
Open Malwarebytes, select > "settings" > "protection tab"
Scroll down to "Scan Options" ensure Scan for Rootkits and Scan within Archives are both on....
Go back to "DashBoard" select the Blue "Scan Now" tab......
When the scan completes deal with any found entries...
To get the log from Malwarebytes do the following:
- Click on the Report tab > from main interface.
- Double click on the Scan log which shows the Date and time of the scan just performed.
- Click Export > From export you have two options:
Copy to Clipboard - if seleted right click to your reply and select "Paste" log will be pasted to your reply
Text file (*.txt) - if selected you will have to name the file and save to a place of choice, recommend "Desktop" then attach to reply
- Please use "Copy to Clipboard, then Right click to your reply > select "Paste" that will copy the log to your reply…
Alternative: Dr. Web CureIt! : The Dr.Web CureIt! utility will cure an infected system once, but it is not designed to provide your PC with real-time protection from viruses.
Alternative download option: http://www.techspot.com/downloads/6731-farbar-recovery-scan-tool.html
Note: You need to run the version compatible with your system (32 bit or 64 bit). If you are not sure which version applies to your system download both of them and try to run them. Only one of them will run on your system, that will be the right version.
If your security alerts to FRST either, accept the alert or turn your security off to allow FRST to run. It is not malicious or infected in any way...
Be aware FRST must be run from an account with Administrator status...
Double-click to run it. When the tool opens click Yes to disclaimer.(Windows 8/10 users will be prompted about Windows SmartScreen protection - click More information and Run.)
- Make sure Addition.txt is checkmarked under "Optional scans"
- Press Scan button to run the tool....
- It will make a log (FRST.txt) in the same directory the tool is run. Please copy and paste it to your reply.
- The tool will also make a log named (Addition.txt) Please attach that log to your reply.
Edit fixlist.txt file and put it into the folder you saved FRST into. "Do not open that file when running FRST fix"
NOTE. It's important that both FRST and fixlist.txt are in the same location or the fix will not work.
fixlist.txt example:
Start
CloseProcesses:
CreateRestorePoint:
HKU\S-1-5-21-329538839-709975324-1257610972-1000\...\Run: [*hinzifmx<*>] => "C:\Users\New User\AppData\Local\f8acb\9ce63.lnk" <==== ATTENTION (Value Name with invalid characters)
C:\Users\New User\AppData\Local\f8acb
S3 gdrv; \??\C:\Windows\gdrv.sys [X]
FirewallRules: [{17277AF5-A816-4BBB-A57C-C21541B4875B}] => (Allow) LPort=2869
FirewallRules: [{8F312734-7E85-4F3A-B918-A3AE66575823}] => (Allow) LPort=1900
EmptyTemp:
Hosts:
CMD: ipconfig /flushDNS
end
Open FRST and press the Fix button just once and wait.
The tool will make a log on the Desktop (Fixlog.txt) or the folder it was ran from. Please post it to your reply.
3 Download AdwCleaner by Malwarebytes Or from this Mirror
- Right-click on AdwCleaner.exe and select Run as Administrator (for Windows Vista, 7, 8, 8.1 and 10 users)
- Accept the EULA (I accept), then click on Scan
- Let the scan complete. Once it's done, make sure that every item listed in the different tabs is checked and click on the Clean button. This will kill all the active processes
- Once the cleaning process is complete, AdwCleaner will ask to restart your computer, do it
- After the restart, a log will open when logging in. Please copy/paste the content of that log in your next reply
4 Download Microsoft's "Malicious Software Removal Tool"
Notes: Ensure to get the correct version for your system.
Right click on the Tool, select “Run as Administrator” the tool will expand to the options Window
In the "Scan Type" window, select Quick Scan
Perform a scan and Click Finish when the scan is done.
Retrieve the MSRT (Malicious Software Removal Tool) log as follows
1) Select the Windows key and R key together to open the "Run" function
2) Type or Copy/Paste the following command to the "Run Line" and Press Enter:
notepad c:\windows\debug\mrt.log
The log will include log details for each time MSRT has run, the most recent log by date and time will be needed ....
5 Download "Delfix by Xplode" and save it to your desktop.
Or use the following if first link is down: "Delfix link mirror"
If your security program alerts to Delfix either, accept the alert or turn your security off.
Double Click to start the program. If you are using Vista or higher, please right-click and choose run as administrator
Make Sure the following items are checked:
Now click on "Run" and wait patiently until the tool has completed.
The tool will create a log when it has completed. We don't need you to post this.
Any remnant files/logs from tools we have used can be deleted…
6 Read the following links to fully understand PC Security and Best Practices
Answers to Common Security Questions and best Practices
Do I need a Registry Cleaner?
Take care and surf safe
7 Download Microsoft Safety Scanner
Microsoft Safety Scanner is a scan tool designed to find and remove malware from Windows computers. Simply download it and run a scan to find malware and try to reverse changes made by identified threats.
Usage:
Or use the following if first link is down: "Delfix link mirror"
If your security program alerts to Delfix either, accept the alert or turn your security off.
Double Click to start the program. If you are using Vista or higher, please right-click and choose run as administrator
Make Sure the following items are checked:
- Remove disinfection tools <----- this will remove tools we may have used.
- Purge System Restore <--- this will remove all previous and possibly exploited restore points, a new point relative to system status at present will be created.
- Reset system settings <--- this will reset any system settings back to default that were changed either by us during cleansing or malware/infection
Now click on "Run" and wait patiently until the tool has completed.
The tool will create a log when it has completed. We don't need you to post this.
Any remnant files/logs from tools we have used can be deleted…
6 Read the following links to fully understand PC Security and Best Practices
Answers to Common Security Questions and best Practices
Do I need a Registry Cleaner?
Take care and surf safe
7 Download Microsoft Safety Scanner
Microsoft Safety Scanner is a scan tool designed to find and remove malware from Windows computers. Simply download it and run a scan to find malware and try to reverse changes made by identified threats.
Safety Scanner only scans when manually triggered and is available for use 10 days after being downloaded.
Kansa

- GitHub - Davehull/Kansa
- http://trustedsignal.blogspot.com/search/label/Kansa
- http://www.powershellmagazine.com/2014/07/18/kansa-a-powershell-based-incident-response-framework/
- Kansa: A PowerShell-based incident response framework
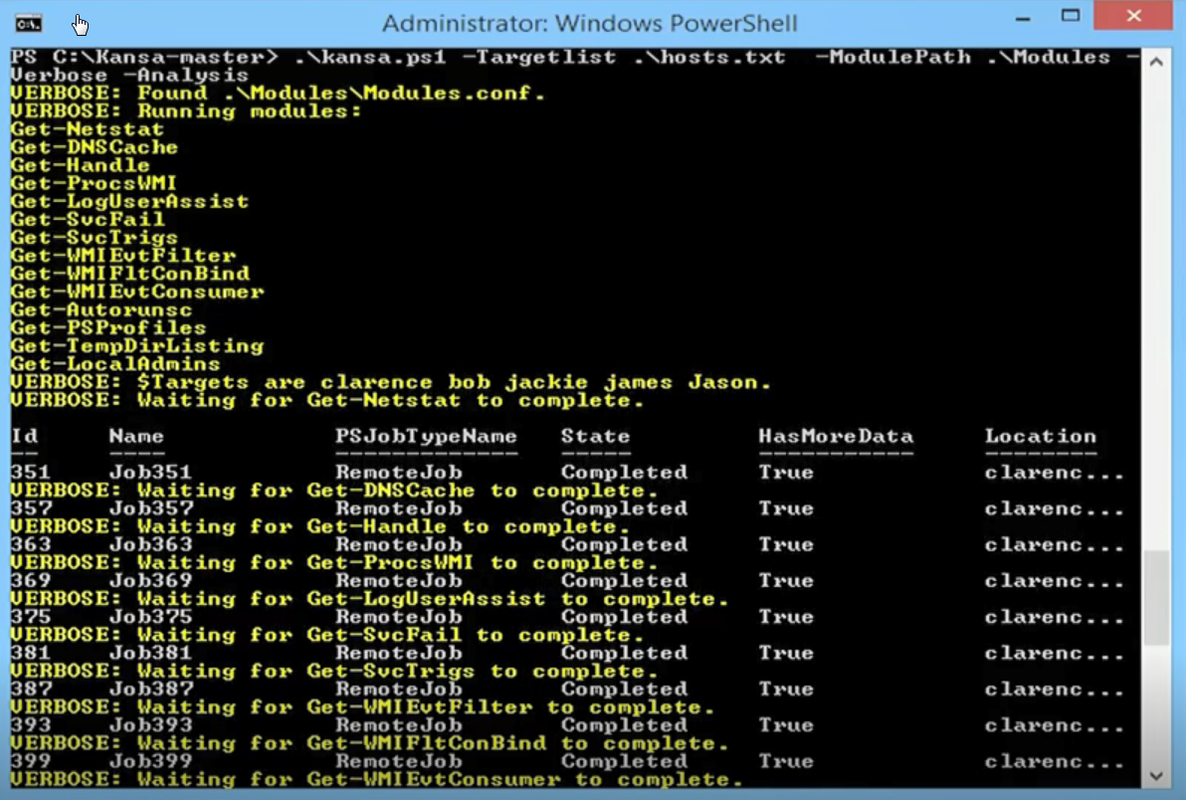
Usage:
PS C:\ISOScripting\Kansa-master\Kansa-master> .\kansa.ps1 -target testmachine1
VERBOSE: Found Modules\\Modules.conf.
VERBOSE: Running modules:
Get-PrefetchListing
Get-WMIRecentApps
Get-Netstat
Get-DNSCache
Get-ProcsWMI
Get-LogUserAssist
Get-SvcFail
Get-SvcTrigs
Get-WMIEvtFilter
Get-WMIFltConBind
Get-WMIEvtConsumer
Get-PSProfiles
Get-SchedTasks
Get-File
Get-LocalAdmins
VERBOSE: Waiting for Get-PrefetchListing to complete.
Id Name PSJobTypeName State HasMoreData Location Command
-- ---- ------------- ----- ----------- -------- -------
1 Job1 RemoteJob Completed True testmachine1 <#...
VERBOSE: Waiting for Get-WMIRecentApps to complete.
3 Job3 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-Netstat to complete.
5 Job5 RemoteJob Completed True testmachine1 <#...
VERBOSE: Waiting for Get-DNSCache to complete.
7 Job7 RemoteJob Completed True testmachine1 <#...
VERBOSE: Waiting for Get-ProcsWMI to complete.
9 Job9 RemoteJob Completed True testmachine1 <#...
VERBOSE: Waiting for Get-LogUserAssist to complete.
11 Job11 RemoteJob Failed True testmachine1 <#...
VERBOSE: Waiting for Get-SvcFail to complete.
13 Job13 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-SvcTrigs to complete.
15 Job15 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-WMIEvtFilter to complete.
17 Job17 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-WMIFltConBind to complete.
19 Job19 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-WMIEvtConsumer to complete.
21 Job21 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-PSProfiles to complete.
23 Job23 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-SchedTasks to complete.
25 Job25 RemoteJob Failed False testmachine1 <#...
VERBOSE: Waiting for Get-File C:\Windows\WindowsUpdate.log to complete.
27 Job27 RemoteJob Failed False testmachine1 <# ...
VERBOSE: Waiting for Get-LocalAdmins to complete.
29 Job29 RemoteJob Failed False testmachine1 <#...
Script completed with warnings or errors. See C:\ISOScripting\Kansa-master\Kansa-master\Output_20181029102057\Error.Log
for details.
PS C:\ISOScripting\Kansa-master\Kansa-master> ls
Directory: C:\ISOScripting\Kansa-master\Kansa-master
Mode LastWriteTime Length Name
---- ------------- ------ ----
d----- 29/10/2018 8:54 AM Analysis
d----- 29/10/2018 8:54 AM Modules
d----- 29/10/2018 10:18 AM Output_20181029101813
d----- 29/10/2018 10:18 AM Output_20181029101855
d----- 29/10/2018 10:19 AM Output_20181029101903
d----- 29/10/2018 10:20 AM Output_20181029102044
d----- 29/10/2018 10:27 AM Output_20181029102057
-a---- 29/10/2018 8:54 AM 89 .gitignore
-a---- 29/10/2018 8:54 AM 3217 CODE_OF_CONDUCT.md
-a---- 29/10/2018 8:54 AM 3540 contributing.md
-a---- 29/10/2018 8:54 AM 50110 kansa.ps1
-a---- 29/10/2018 8:54 AM 11323 LICENSE
-a---- 29/10/2018 8:54 AM 3212 MSLimitedPublicLicense.txt
-a---- 29/10/2018 8:54 AM 3770 README.md
PS C:\ISOScripting\Kansa-master\Kansa-master>
Awesome Incident Response
Tools can scan remote network drives
- SuperAntiSpyware - it can scan remote share network drives, which MalwareBytes can't do since 2015 , although it used to be
- EMCO Network Malware Cleaner -
- Emsisoft - Emsisoft Anit-Malware
Mimikatz
A little tool to play with Windows security http://blog.gentilkiwi.com/mimikatz
- https://github.com/gentilkiwi/mimikatz/releases/tag/2.1.1-20181209 - mostly this will be flagged as a threat
- https://github.com/PowerShellMafia/PowerSploit - You can use this powershell script version to avoid that.
Other Related Tools
- Wireshark(http://www.esecurityplanet.com/open-source-security/5-big-improvements-in-wireshark.html)
- OpenVAS(http://www.openvas.org)
- Nessus专业版
- Rapid7 Nexpose
- Qualys FreeScan
- Metasploit(https://www.rapid7.com/products/metasploit/download.jsp)
- John the Ripper(http://www.openwall.com/john/)
- Kali Linux(https://www.kali.org/downloads/)
- Pentoo (http://www.pentoo.ch/download/)
- Parrot Security OS(http://www.pentoo.ch/download/)
- BackBox (https://backbox.org/download)
- Samurai Web Testing Framework (https://sourceforge.net/projects/samurai/files/)
- Immunity Canvas(https://www.rapid7.com/products/metasploit/editions.jsp)
- Core Impact Pro(http://www.coresecurity.com/content/core-impact-overview)
Threat Analysis Companies
- Anomali
- Cisco Umbrella
- Maltego
- Recorded Future
- Soltra
- VirusTotal
- Any.Run - Interactive Online Malware Sandbox









No comments:
Post a Comment