What is Risk:
Risk = Threat x Vulnerability x Asset
The enterprise risk assessment and enterprise risk management processes comprise the heart of the information security framework. These are the processes that establish the rules and guidelines of the security policy while transforming the objectives of an information security framework into specific plans for the implementation of key controls and mechanisms that minimize threats and vulnerabilities. Each part of the technology infrastructure should be assessed for its risk profile. From that assessment, a determination should be made to effectively and efficiently allocate the organization’s time and money toward achieving the most appropriate and best employed overall security policies. The process of performing such a risk assessment can be quite complex and should take into account secondary and other effects of action (or inaction) when deciding how to address security for the various IT resources.
Specifically, an enterprise security risk assessment is intended to be suitable for the following, which could be specific to any organization:
- A way to ensure that security risks are managed in a cost-effective manner
- A process framework for the implementation and management of controls to ensure that the specific security objectives of an organization are met
- A definition of new information security management processes
- Use by management to determine the status of information security management activities
- Use by internal and external auditors to determine the degree of compliance with the policies, directives and standards adopted by the organization
- For implementation of business-enabling information security
- To provide relevant information about information security to customers
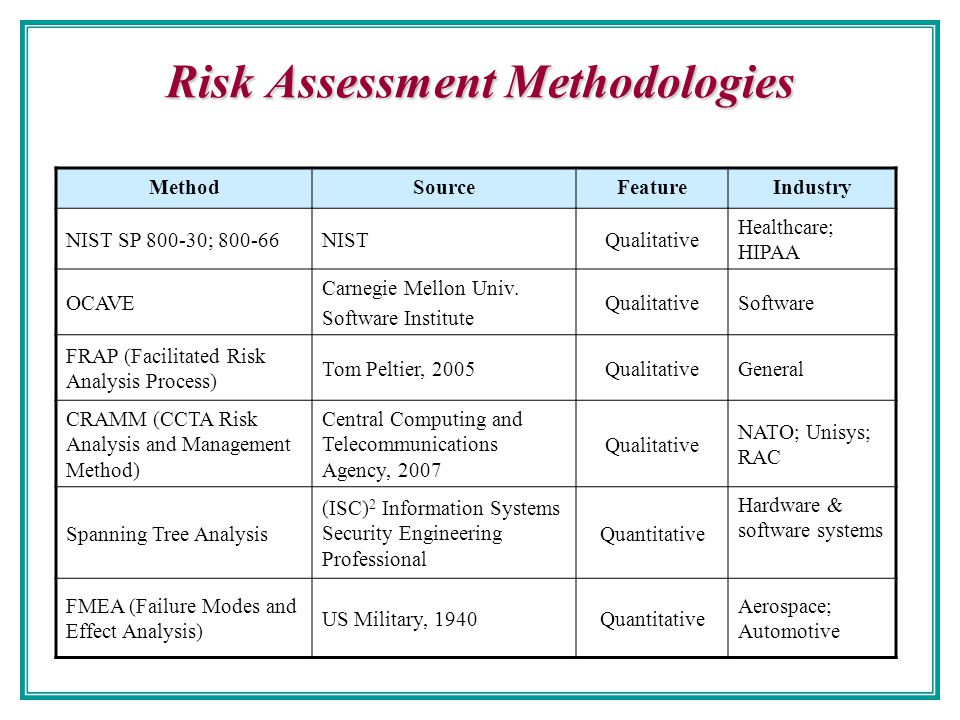
TRA Methodologies
TRA Process and Steps
The high-level five steps of the TRA process include:
- Request initiated
- Develop assessment scope, plan, and schedule
- Conduct assessment
- Review security plan, documentation, controls
- Identify business needs and changes to requirements that may affect overall IT and security direction.
- Review adequacy of existing security policies, standards, guidelines and procedures.
- Assess physical protection applied to computing equipment and other network components.
- Conduct technical and procedural review and analysis of the network architecture, protocols and components to ensure that they are implemented according to the security policies.
- Review and check the configuration, implementation and usage of remote access systems, servers, firewalls and external network connections, including the client Internet connection.
- Review logical access and other authentication mechanisms.
- Review current level of security awareness and commitment of staff within the organization.Review agreements involving services or products from vendors and contractors.
- Conduct vulnerability scans
- Analyze assets, threats and vulnerabilities, including their impacts and likelihood.
- Perform Threat Analysis (NIST 800-30 P12)
- Identify threat sources
- Identify threat events
- Identify vulnerabilities and the conditions needed to exploit them
- Identify the likelihood such attacks would succeed
- Identify the potential impact
- Identify Risks (NIST 800-30 P12)
- Determine the risk posed
- Risk Mitigation and Recommendations
- Develop practical technical recommendations to address the vulnerabilities identified, and reduce the level of security risk.
- Report/Results and completion
- Appendixes for following information
- Security requirements and objectives
- System or network architecture and infrastructure, such as a network diagram showing how assets are configured and interconnected
- Information available to the public or accessible from the organization’s web site
- Physical assets, such as hardware, including those in the data center, network, and communication components and peripherals (e.g., desktop, laptop, PDAs)
- Operating systems, such as PC and server operating systems, and network management systems
- Data repositories, such as database management systems and files
- A listing of all applications
- Network details, such as supported protocols and network services offered
- Security systems in use, such as access control mechanisms, change control, antivirus, spam control and network monitoring
- Security components deployed, such as firewalls and intrusion detection systems
- Processes, such as a business process, computer operation process, network operation process and application operation process
- Identification and authentication mechanisms
- Government laws and regulations pertaining to minimum security control requirements
- Documented or informal policies, procedures and guidelines
TRA Process Example
======================================================================
A Simple Example

======================================================================
Following example is from https://www.thesslstore.com/blog/cyber-risk-assessment/
Based on NIST
- Identify and document threat sources
For non-adversarial threats, you just need to weigh the potential impact should an event take place.
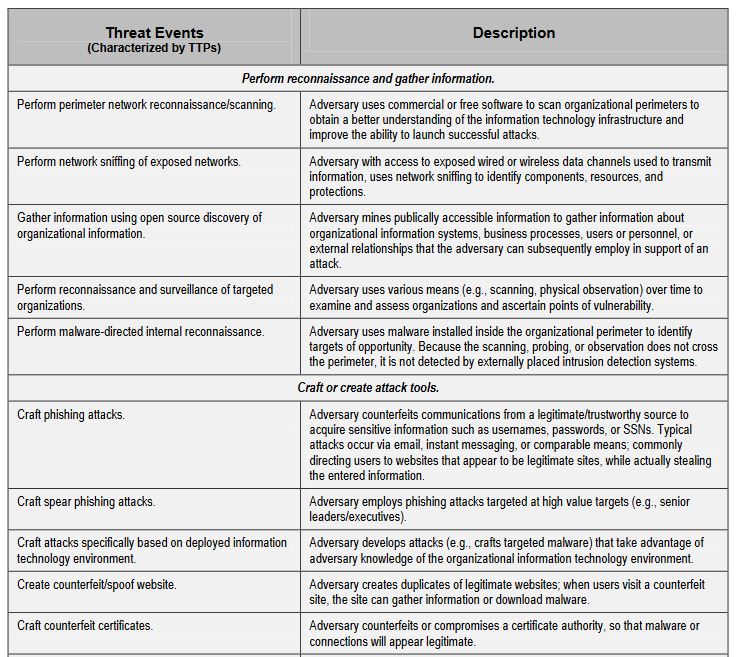
2. Identify Threat Events
From: https://www.thesslstore.com/blog/cyber-risk-assessment/
The example NIST gives is five pages long, which just reinforces how comprehensive you need to be. You can’t prepare for threats that you didn’t anticipate, so this step is absolutely crucial. Here are some types of threat that nearly every organization faces.
- Unauthorized access – This can be both adversarial and non-adversarial in nature, potentially occurring from an attack, malware or even just employee error.
- Misuse of information by authorized users – This is typically an insider threat that can occur when data is altered, deleted or used without approval.
- Data leaks/accidental exposure of PII – Personal Identifying Information, known as personal data in the EU, is considered breached anytime it is altered, deleted or disclosed to an unauthorized party. Even if it’s accidental.
- Loss of data – This dovetails with the previous points, it occurs when an organization loses or accidentally deletes data as a result of a botched backup or poor replication.
- Service/productivity disruptions – This one is pretty self-explanatory.
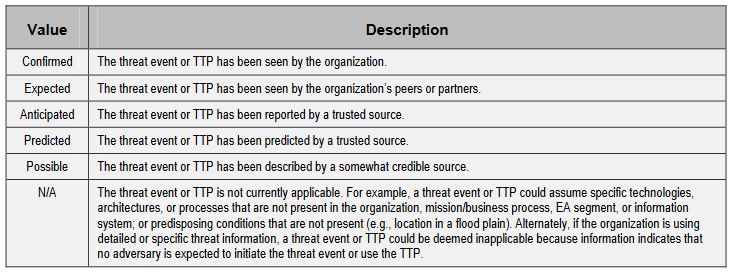
Scale used to assess the relevance of each threat.
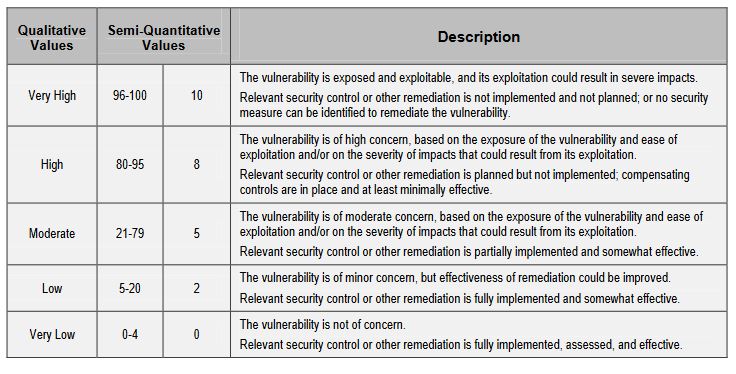
3. Identify vulnerabilities and the conditions needed to exloit them
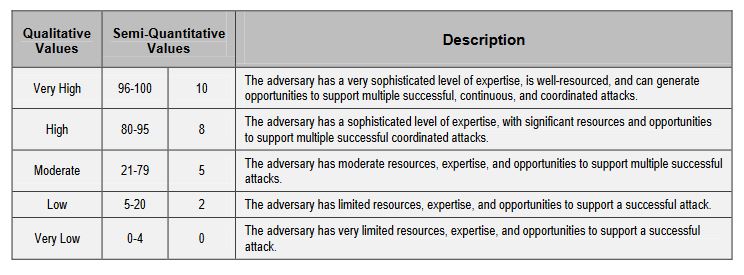
Here is the scale that NIST uses to determine what vulnerabilities coincide with that threats, and then factor in what - if any controls are in place to mitigate such an event.
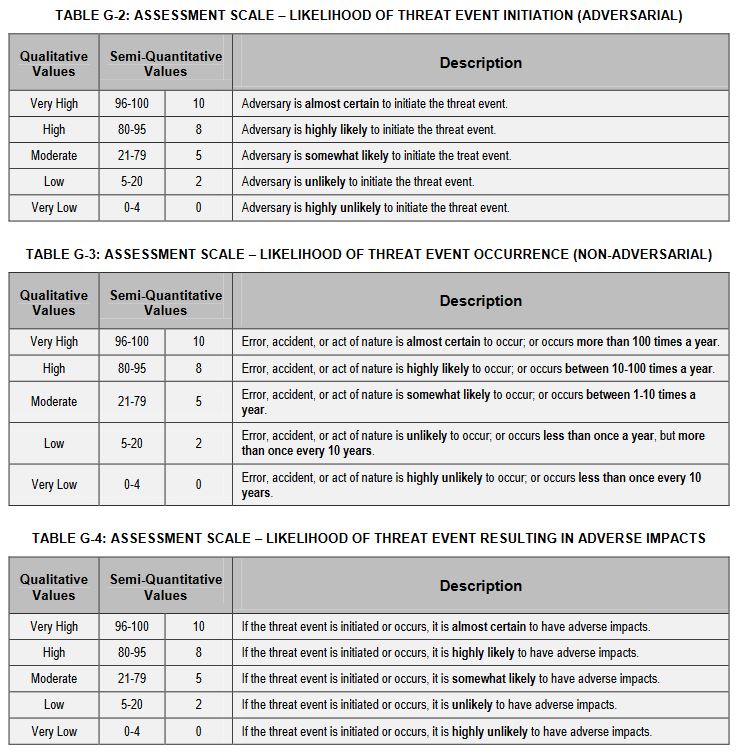
4. Identify the likelihood such attacks would succeed
5. Identify the potential impact
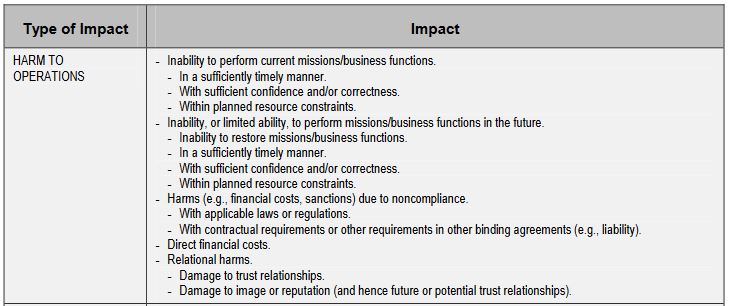
Create a two columns table and organize the different types of impact (harm to operations, harm to assets, etc) on one side, while listing the different ways that impact could play out. Here’s an example.
You’ll probably also want categories that cover harm to assets (you may even want to segment it further and get into physical assets, digital assets, etc.), harm to individuals or data subjects, harm to third-party organizations like your partners and if you’re feeling patriotic NIST also has a category for “harm to the Nation.”
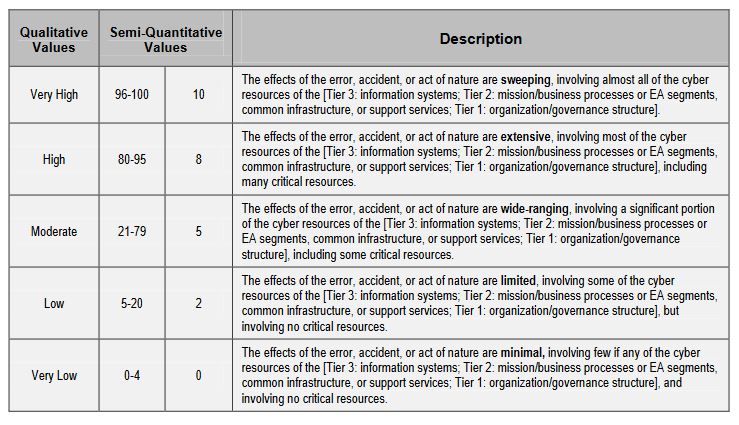
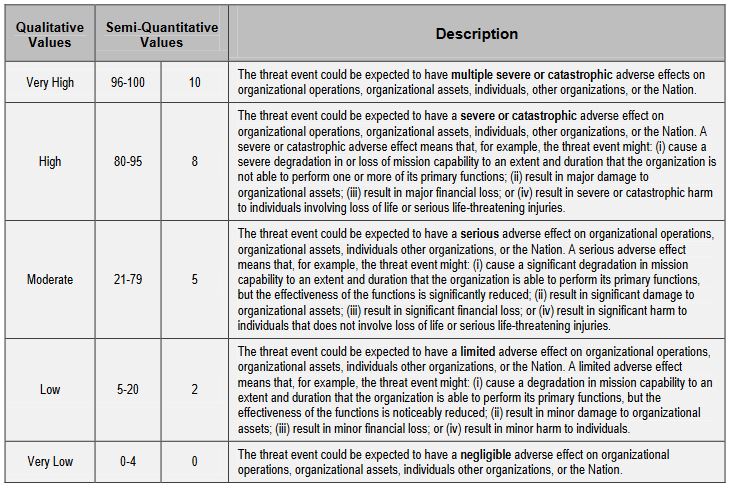
here is the scale that NIST proposes for measuring impact.
6. Determine your organizational risk
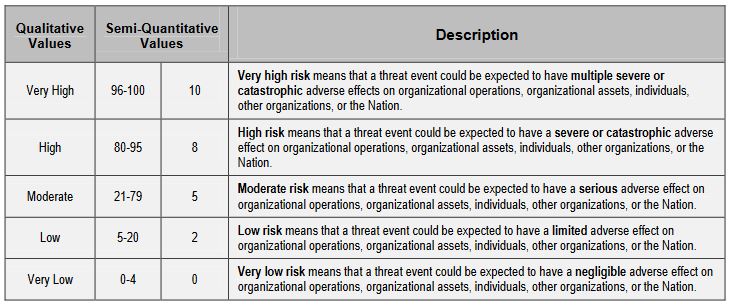
Your risk is ultimately going to be determined by the confluence of the likelihood of an event and the potential impact it poses. There are a number of ways to calculate this, you can use the scales provided by NIST, assigning numbers to likelihood and impact and then calculating it that way or you can use an alternative methodology that is supported by your industry or a regulatory body that oversees your organization. Since we’ve been citing NIST for this article, let’s use their examples one last time. Here’s the scale NIST proposes for government entities to quantify level of risk:
Using the values for impact and likelihood in the NIST Special Publication 800-30, here’s what a completed Residual Risk Rating Assessment could look like.
| Identified Threat |
Impact
|
Likelihood
|
Value
|
Risk Calculation
|
| Unauthorized Access (Malicious or Accidental) |
High [100]
|
High
[1.0] |
100*1.0=100
|
Severe
|
| Misuse of Information by Authorized Users |
High [100]
|
Medium [.5]
|
100*.5=50
|
Elevated
|
| Data Leakage / Unintentional Exposure of Customer Information |
High [100]
|
Medium [.5]
|
100*.5=50
|
Elevated
|
| Failed Processes |
High [100]
|
Low
[.1] |
100*.1=10
|
Low (Normal)
|
| Loss of Data |
High [100]
|
Low
[.1] |
100*.1=10
|
Low (Normal)
|
| Disruption of Service or Productivity |
High [100]
|
Low
[.1] |
100*.1=10
|
Low (Normal)
|
TRA Tools
Network scanners
- Qualys Vulnerability Scanner
- Nessus vulnerability Scanner
- NMAP
- Acunetix Web Vulnerability Scanner
- Burp Suite
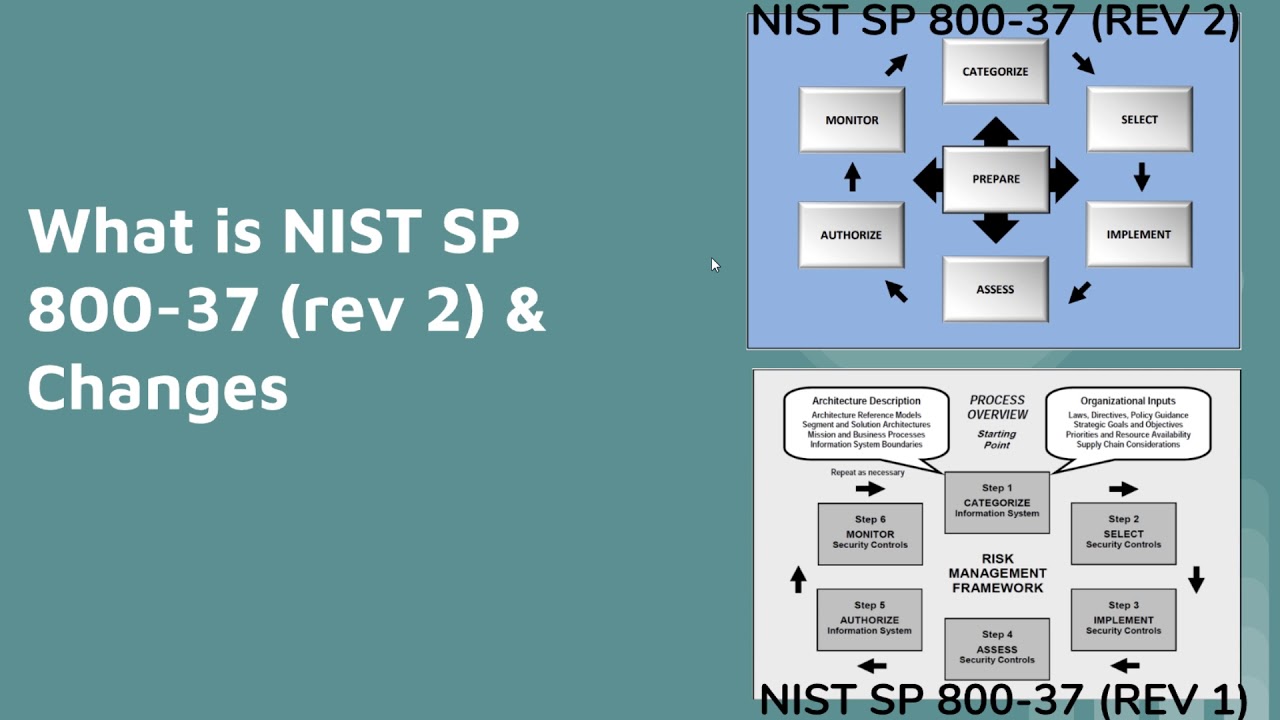
NIST SP 800-37 Risk Management Framework
References:
- NIST SP 800-37 Rev.2 - Risk Management Framework for Information Systems and Organization
- Guide for Conducting Risk Assessments - NIST 800-30
- An Overview of Threat and Risk Assessment - from SANS
- Performing a Security Risk Assessment - from ISACA







hi
ReplyDelete