This post summarizs some popular practical security architecture designs / concepts from different security vendors.
[Cybersecurity Architecture]
- Risk Management
- TOGAF Knowledges Collection
- Governance Overview
- Cybersecurity Architecture Practice
- Cybersecurity Architecture Knowledge Overview
- Architecture Category
Ransomware deployment life cycle in cloud environments
Top Modern Cyber Threats
STRIDE Model for identifying computer security threats.
| Threat | Desired property |
|---|---|
| Spoofing | Authenticity |
| Tampering | Integrity |
| Repudiation | Non-repudiability |
| Information disclosure | Confidentiality |
| Denial of service | Availability |
| Elevation of privilege | Authorization |
Check Point Infinity - A Practical Holistic Approach - Consolidated Security Architecture
A consolidated security architecture is a multi-layered approach to cyber security that protects all IT attack surfaces – networks, cloud, endpoints, mobile and IoT devices – sharing the same threat prevention technologies, management services, and threat intelligence. A consolidated security architecture is designed to resolve the complexities of growing connectivity and inefficient security. It provides complete threat prevention which seals security gaps, enables automatic, immediate threat intelligence sharing across all security environments, and a unified security management platform for an efficient security operation. Ultimately, a consolidated security architecture improves the overall security of an enterprise.
Check Point offers solutions for all of an organization’s security needs, including:
- Network Security: Check Point Quantum
- IoT Security: Check Point Quantum IoT Protect
- Cloud Security: Check Point CloudGuard
- Application Security: Check Point CloudGuard AppSec
- Endpoint Security: Check Point Harmony Endpoint
- Mobile Security: Check Point Harmony Mobile
ISACA Top-Down Approach
Using the Frameworks to Develop an Enterprise Security Architecture
The fair question is always, “Where should the enterprise start?”
If one looks at these frameworks, the process is quite clear. This must be a top-down approach—start by looking at the business goals, objectives and vision.
The initial steps of a simplified Agile approach to initiate an enterprise security architecture program are:
- Identify business objectives, goals and strategy
- Identify business attributes that are required to achieve those goals
- Identify all the risk associated with the attributes that can prevent a business from achieving its goals
- Identify the required controls to manage the risk
- Define a program to design and implement those controls:
- Define conceptual architecture for business risk:
- Governance, policy and domain architecture
- Operational risk management architecture
- Information architecture
- Certificate management architecture
- Access control architecture
- Incident response architecture
- Application security architecture
- Web services architecture
- Communication security architecture
- Define physical architecture and map with conceptual architecture:
- Platform security
- Hardware security
- Network security
- Operating system security
- File security
- Database security, practices and procedures
- Define component architecture and map with physical architecture:
- Security standards (e.g., US National Institute of Standards and Technology [NIST], ISO)
- Security products and tools (e.g., antivirus [AV], virtual private network [VPN], firewall, wireless security, vulnerability scanner)
- Web services security (e.g., HTTP/HTTPS protocol, application program interface [API], web application firewall [WAF])
- Define operational architecture:
- Implementation guides
- Administrations
- Configuration/patch management
- Monitoring
- Logging
- Pen testing
- Access management
- Change management
- Forensics, etc.
- Define conceptual architecture for business risk:
It is that simple. After all risk is identified and assessed, then the enterprise can start designing architecture components, such as policies, user awareness, network, applications and servers.
Figure 6 depicts the simplified Agile approach to initiate an enterprise security architecture program.

Using these frameworks can result in a successful security architecture that is aligned with business needs:
- COBIT principles and enablers provide best practices and guidance on business alignment, maximum delivery and benefits.
- The COBIT Process Assessment Model (PAM) provides a complete view of requirement processes and controls for enterprise-grade security architecture.
- SABSA layers and framework create and define a top-down architecture for every requirement, control and process available in COBIT.
- The TOGAF framework is useful for defining the architecture goals, benefits and vision, and setting up and implementing projects to reach those goals.
- The CMMI model is useful for providing a level of visibility for management and the architecture board, and for reporting the maturity of the architecture over time.
Three Phases Approach
- Phase 1 Develop Policies, Standards, and Best Practices
- Phase 2 Implementation of Phase 1
- Phase 3 Monitoring of Phases 1 and 2
Learning about these phases helps everyone understand on a deeper level how security architecture works and why it’s so important.

Phase 1 Developing an Organization’s Policies, Standards, and Best Practices
Security architects develop their organizational policies, standards, and best practices based on frameworks. These frameworks give guidelines like ‘sensitive data must be encrypted.’ However, there’s no indication of the encryption strength.
Back to the museum analogy: the framework would suggest that all objects worth between $2 to $3 million need “high security.” It's then up to the museum to decide how to define its high security.
Common frameworks include ISO 27001 for information security, NIST Cybersecurity Framework addressing threats and supporting business, and OWASP Top Ten for web application security.
After a company has developed and implemented the framework, it can take a step toward official certification. When they pass the audit, their customers are assured of the organization's level of safety. Over time, changes occur as the security architect adapts systems to stay secure and maintain the certifications.
For some frameworks, cybersecurity staff training is required. It’s an important step because the training helps ensure employees understand their responsibilities and supports maintaining security in the organization. When an organization fails to train, the certification and customer trust are at risk.
A nerdy note: A standard defines thresholds for compliance, and frameworks offer guidelines. But you’ll often find frameworks referred to as company standards.
Phase 2 Using the Building Blocks of Security and Applying Design Concepts
Once security architects define the organization’s policies and standards, the development teams design and implement the software. This stage applies these requirements and principles at the building block level.
Many organizations apply a principle called "Security by Design." This involves designing and implementing software components with built-in security controls, ensuring each part of the system is protected against attack. In a way, it’s like building something block by block with Lego. The developers design and construct various building blocks of code to include required security measures relevant to their functionality. When the finished solution is assembled, they have already accounted for many potential security issues.
For example, when considering an app, the cybersecurity architects write the safety rules for authentication and authorization. Such rules may include “Block users who repeatedly enter the wrong password” or “Always check if a user is logged in before giving them access to data.” The developers apply the rules as they make the building blocks. Then they use these existing blocks in other parts of the app, knowing they adhere to the security principles. Finally assembled, the blocks make a secure and robust application.
Phase 3 Monitoring for Changes, Updates, and Implementation
Security architects monitor their systems. They watch to ensure that standards are met, update these standards for new technologies, and keep track of exceptions.
Looking back at our museum building metaphor:
- Phase 1: The architects decide what safety features the building needs.
- Phase 2: The builders bring in raw materials and construct the walls.
- Phase 3: The building inspectors come back to check that the building is safe.
In other words, the security architects monitor phases 1 and 2 to ensure they meet their standards.
In addition, the security architects keep an eye on the list of existing issues that need to be fixed, also called technical debt. Old technologies provide much more surface exposure and are vulnerable to attack. Once or twice a year, a company-wide risk assessment for cyber defense should take place. This helps security architects consider costs and risks and then adapt accordingly.
Toolbox
Analytic Tools: current state, risk, and threat analysis (gap analysis)
Informational Tools: Data gathering and metrics
Design Tools: Documentation and modeling
- In one week,
- Examine security architecture process to find inefficiencies
- Begin thinking through how to improve
- In the first three months you should
- Adapt architecture process to include automation
- Where possible and leverage free tools to assist
- Within six months you should
- Begin to collect metrics of architecture process performance
- Analyze metrics to find areas for further refinement
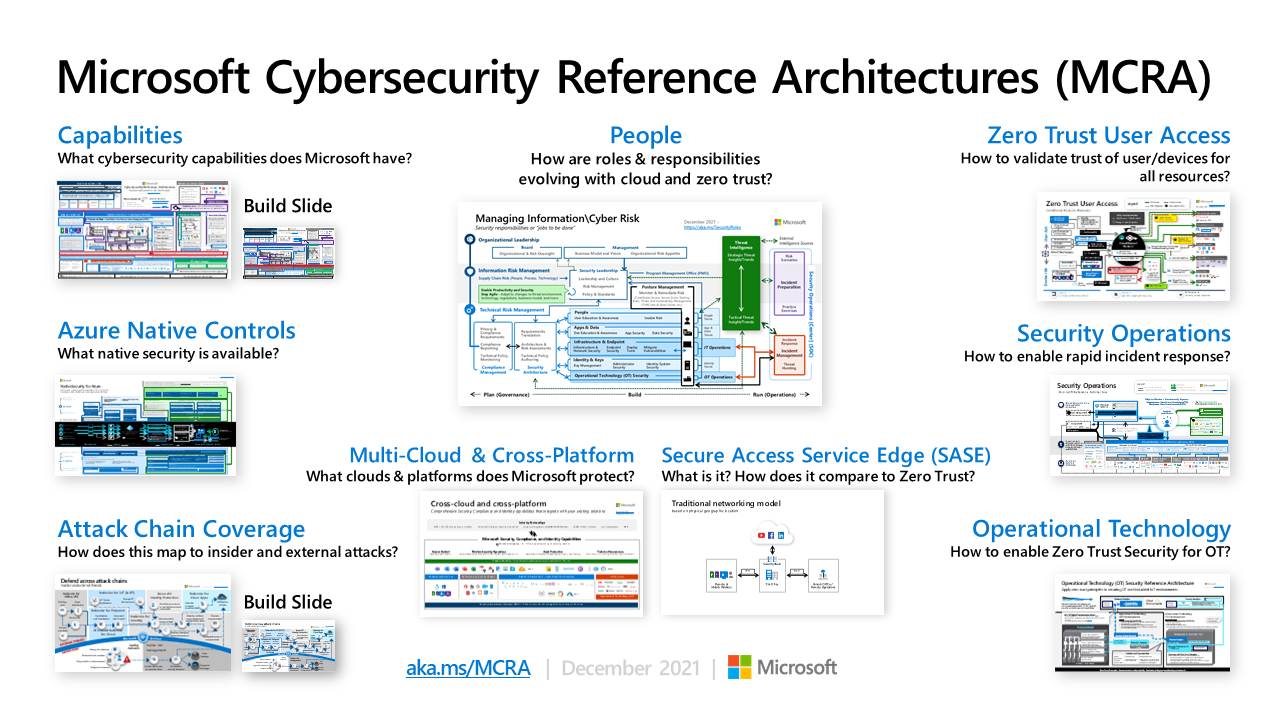
MCRA (Microsoft Cybersecurity Reference Architectures)
The reference architectures are primarily composed of detailed technical diagrams on Microsoft cybersecurity capabilities, zero trust user access, security operations, operational technology (OT), multi-cloud and cross-platform capabilities, attack chain coverage, azure native security controls, and security organizational functions.
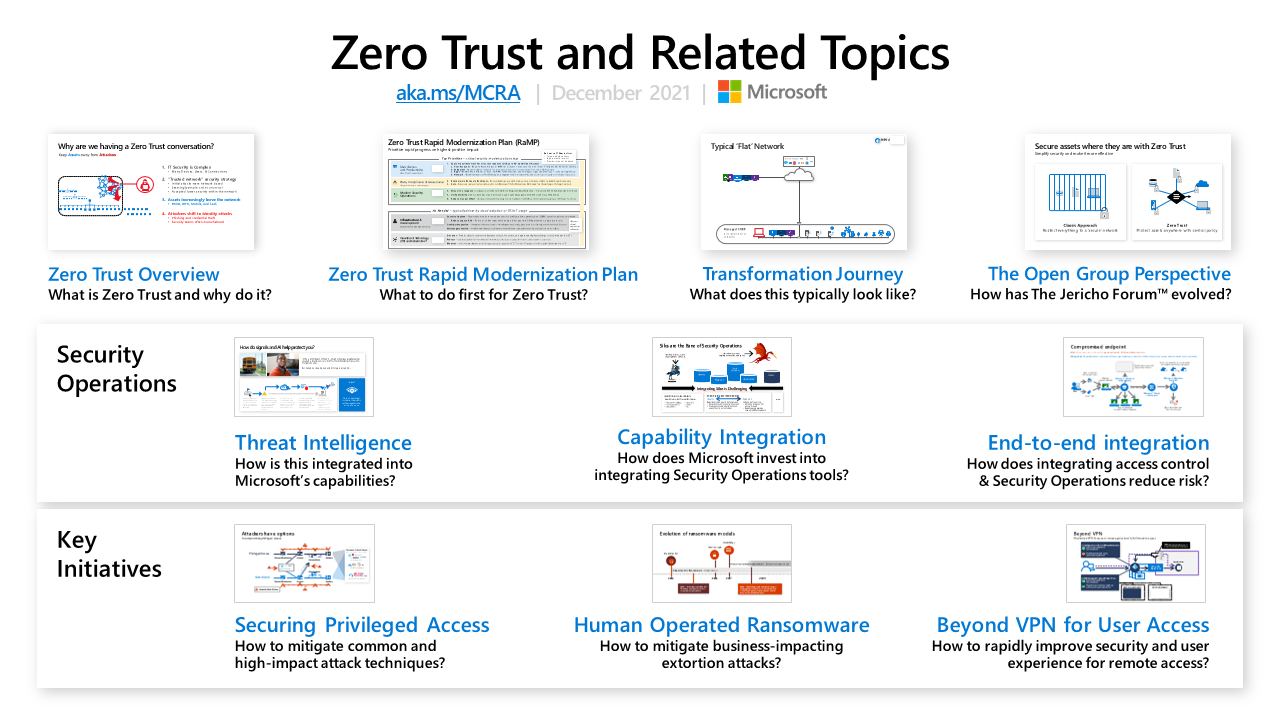
The MCRA also includes an overview of Zero Trust and a Zero Trust rapid modernization plan (RaMP). Additionally, this includes other key information on security operations and key initiatives like protecting from human operated ransomware, securing privileged access, moving beyond VPN, and more.








No comments:
Post a Comment