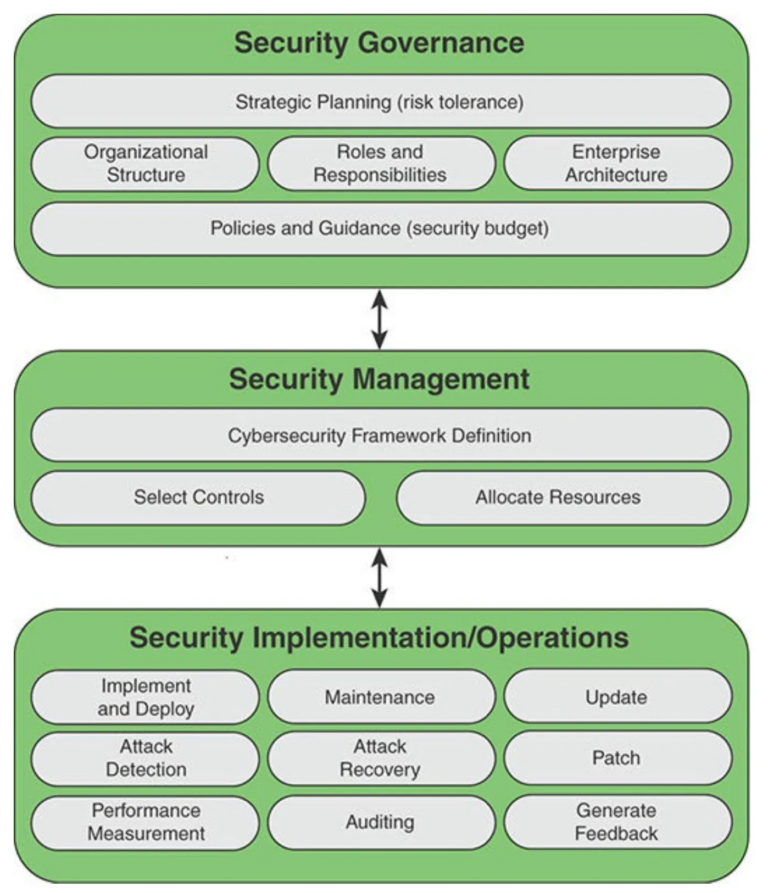
The system by which an organization directs and controls security governance, specifies the accountability framework and provides oversight to ensure that risks are adequately mitigated, while management ensures that controls are implemented to mitigate risks.
Based on ChatGPT, what is information security goverance?
Information security governance refers to the overall management and control of the processes and policies related to the protection of sensitive and confidential information within an organization. This includes defining and implementing best practices for data protection, ensuring compliance with relevant laws and regulations, and establishing a clear and effective decision-making structure for information security issues.
The goal of information security governance is to ensure the confidentiality, integrity, and availability of information, as well as to minimize the risk of cyber attacks and data breaches. This involves the participation and involvement of senior management and all stakeholders, as well as the integration of security into the overall governance framework of the organization.
Information security governance is a critical aspect of an organization's overall risk management strategy, and helps to ensure that the organization has the necessary processes and controls in place to protect its sensitive and confidential information.
Cybersecurity governance refers to the overall management and control of the processes and policies related to the protection of an organization's information systems, networks, and data from cyber threats and attacks. It involves the development and implementation of security strategies, policies, and procedures to ensure the confidentiality, integrity, and availability of information and systems.
The goal of cybersecurity governance is to ensure that an organization's information systems and data are protected from cyber threats, such as hacking, malware, and data breaches, and that the organization is in compliance with relevant laws and regulations.
Cybersecurity governance is a critical aspect of an organization's overall risk management strategy, and requires the participation and involvement of senior management and all stakeholders. This includes the integration of cybersecurity into the organization's overall governance framework, as well as the allocation of resources and the development of effective decision-making processes for cybersecurity issues.
A successful cybersecurity governance program requires a comprehensive approach that involves regular risk assessments, regular monitoring and review of security controls, and the continuous improvement of security policies and processes.
- Risk Management
- TOGAF Knowledges Collection
- Governance Overview
- Cybersecurity Architecture Practice
- Cybersecurity Architecture Knowledge Overview
- Architecture Category
Introduction
Traditionally, cybersecurity is viewed through the lens of a technical or operational issue to be handled in the technology space. Cybersecurity planning needs to fully transition from a back-office operational function to its own area aligned with law, privacy and enterprise risk. The CISO should have a seat at the table alongside the CIO, COO, CFO and CEO. This helps the C-suite understand cybersecurity as an enterprise-wide risk management issue -- along with the legal implications of cyber-risks -- and not solely a technology issue.
The C-suite can then set the appropriate tone for the organization, which is the cornerstone of any good governance program. Establishing the right tone at the top is much more than a compliance exercise. It ensures everyone is working according to plan, as a team, to deliver business activities and ensure the protection of assets within the context of a risk management program and security strategy.
Historically, cybersecurity was managed by implementing a solution to solve a problem or mitigate a risk. Many cybersecurity departments have technical security safeguards, such as firewalls or intrusion detection, but often lack basic cybersecurity governance policies, best practices and processes. Where they do exist, policies or processes are often outdated or ignored.
Many cybersecurity departments also have poor or inadequate cybersecurity awareness training programs that fail to address all levels of an organization. As we have learned from recent breaches, many organizations have inadequate hardening and patching programs. Poor access control practices, such as uncontrolled group passwords, shared accounts, proliferated admin privileges, shared root access and the absence of an authorization process except at a low operational level, also are problematic.
Elements of the Information Security System:
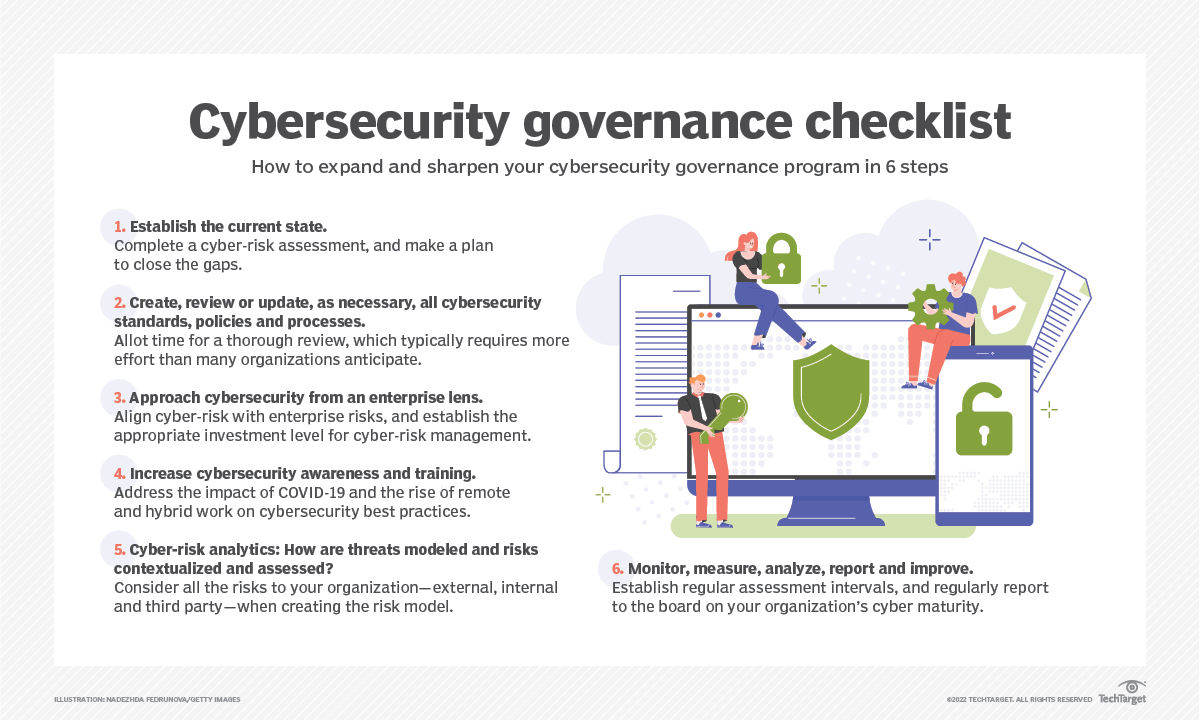
Here are six steps that can help an organization grow and sharpen its cybersecurity governance program:
- Establish the current state.
- Complete a cyber-risk assessment to understand the gaps, and create a roadmap to close those gaps.
- Complete a maturity assessment.
- Create, review and update all cybersecurity standards, policies and processes.
- Many describe this as low-hanging fruit -- and it is -- but it is a heavy lift. Take the time needed to establish the structure and expectations of cybersecurity governance.
- Approach cybersecurity from an enterprise lens.
- Understand what data needs to be protected.
- How are the cyber-risks aligned with enterprise risk management?
- What is the relative priority of cybersecurity investment as compared with other types of investments?
- Increase cybersecurity awareness and training.
- With the rise in remote work driven by COVID-19 and the ongoing adoption of hybrid work models, we are no longer just training our internal employees. With so many people working from home and many children attending school online, it is critical that the entire family understands good cyber hygiene.
- Cyber-risk analytics: How are threats modeled and risks contextualized and assessed?
- When creating the risk model, consider all the risks to your organization -- external, internal and third party.
- Monitor, measure, analyze, report and improve.
- This is not a one-and-done exercise. Establish regular assessment intervals, measure what matters, analyze the data and create an improvement plan.
- Report to the board on cyber maturity and the cyber-risk posture across the organization.
Build Cyber Security Governance Step Example
1. Create Cybersecurity Transformation
distracts attention from real (but unobtrusive) APT attacks. More complex dependencies may exist in cybersecurity systems that will only come to light if the transformation is seen as a systemic and holistic exercise.
2. ESTABLISHING CYBERSECURITY GOVERNANCE
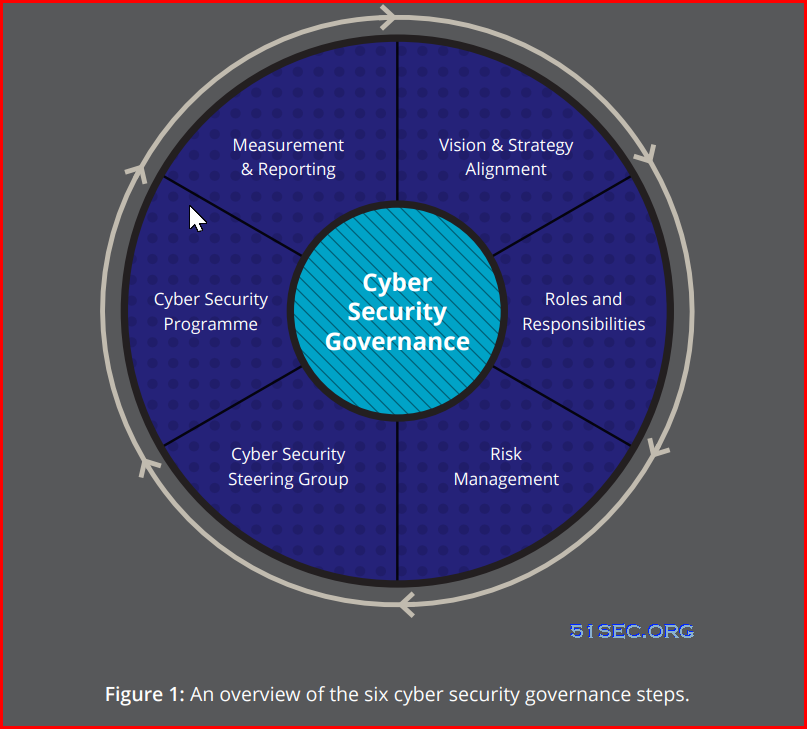
Cybersecurity governance is both preventive and corrective. It covers the preparations and precautions taken against cybercrime, cyberwarfare and other relevant forms of attack. At the same time, cybersecurity governance determines the processes and procedures needed to deal with actual incidents caused by an attack or security breach. In this context, governance principles and provisions must be reasonably flexible to allow for the fact that attacks are often unconventional, generally against the rules, and most often designed to circumvent exactly those procedures and common understandings within the organization that keep the business running. Establish Cybersecurity governance with following six‐step approach as explained below:
STEP 1: IDENTIFY STAKEHOLDER NEEDS
- • Determine the internal and external (usually restricted) stakeholders and their interest in organizational Cybersecurity.
- • Incorporate confidentiality needs and mandated secrecy in the identification process.
- • Understand how cybersecurity should support overall enterprise objectives and protect stakeholder interests.
- • Identify reporting requirements for communicating and reporting about cybersecurity (contents, detail).
- • Clearly define and articulate instances of reliance on the work of others (for external auditors).
- • Define and formally note confidentiality and secrecy requirements for external auditors.
STEP 2: MANAGE CYBERSECURITY TRANSFORMATION STRATEGY.
- • Review legal and regulatory provisions in cybercrime and cyberwarfare
- • Identify the senior management tolerance level in relation to attacks and breaches.
- • Validate business needs (express and implied) with regard to attacks and breaches
- • Identify and articulate any game changers or paradigm shifts in cybersecurity.
- • Document systemic weaknesses in cybersecurity as regards the business and its objectives
- • Identify and validate strategy for cybersecurity (“zero tolerance” vs. “living with it”)
- • Identify adaptability, responsiveness and resilience of strategy in terms of cybersecurity attacks and breaches
- • Identify any rigid/brittle governance elements that may inadvertently be conducive to cybercrime and cyberwarfare (e.g., instances of over control)
- • Define the expectations, in alignment with strategy (“zero tolerance” vs. “living with it”), with regard to cybersecurity, including ethics and culture.
- • Highlight any ethical/cultural discontinuities that exist or emerge.
- • Define the target culture for cybersecurity, and develop a cybersecurity awareness program.
- • Obtain management commitment for the selected strategy
STEP 3: DEFINE CYBERSECURITY STRUCTURE
Structure
- • Define the Cybersecurity organizational structure – an appropriate platform/committee, in alignment with information security and information risk functions.
- • Highlight any barriers or other organizational segregation of duties/information.
- • Mandate an appropriate cybersecurity function, including incident and attack response
Roles and Responsibilities
- • Determine an optimal decision‐making model for cybersecurity— this may be distinct and different from “ordinary” information security
- • Define high‐level RACI (responsible, accountable, consulted, informed) model for cybersecurity function, including any external resources.
- • Consider any extended decision rights that may be applicable in crisis/ incident handling situations.
- • Determine cybersecurity obligations, responsibilities and tasks of other organizational roles (including groups and individuals).
- • Ensure cybersecurity participation at the steering committee level.
- • Embed cybersecurity transformation activities in the steering committee agenda.
Communications
- • Establish escalation points for attacks, breaches and incidents (information security, crisis management, etc.)
- • Define escalation paths for cybersecurity activities and transformational steps (e.g., new vulnerabilities and threats).
- • Establish fast‐track/crisis mode decision procedures with escalation to senior management.
- • Identify the means and channels to communicate cybersecurity issues and information.
- • Prioritize cybersecurity reporting to stakeholders by applying the principles of least privilege and need‐to‐know basis.
- • Develop appropriate guidance for associates.
Integration
- • Integrate, to the appropriate extent, the cybersecurity direction into the overall information security direction, and highlight areas of cybersecurity that are deliberately kept separate and distinct.
- • Establish interfaces between the cybersecurity function and other information security roles.
- • Embed cybersecurity reporting into the generic reporting methods for information security.
STEP 4: MANAGE CYBERSECURITY RISKS
- • Determine risk appetite/tolerance levels in terms of cybercrime and cyberwarfare attacks and breaches at the board/management level.
- • Align risk tolerance levels against the overall strategy (“zero tolerance” vs. “living with it”).
- • Compare cybersecurity and generic information security risk tolerance levels and highlight inconsistencies.
- • Integrate cybersecurity risk assessment and management within overall information security management.
STEP 5: OPTIMIZE CYBERSECURITY RESOURCES
- • Evaluate the effectiveness of cybersecurity resources in comparison with information security and information risk needs.
- • Validate cybersecurity resources in terms of specific goals and objectives.
- • Ensure that cybersecurity resource management is aligned to overarching information security needs.
- • Include external resource management.
STEP 6: MONITOR CYBERSECURITY EFFECTIVENESS
- • Track cybersecurity outcomes and effects, particularly with a view to changes in attacks/breaches/incidents.
- • Compare outcomes against transformation steps and milestones – initial (current state) and future (target state) expectations.
- • Integrate cybersecurity measurements and metrics into routine compliance check mechanisms.
- • Evaluate threats and vulnerabilities relevant to cybersecurity, and incorporate the changing threat landscape into cybersecurity strategy.
- • Monitor the risk profile for attacks/breaches and the corresponding risk appetite to achieve optimal balance between cybersecurity risk and business opportunities.
- • Measure the effectiveness of cybersecurity resources (internal and external) against defined information security needs, goals and objectives.
Cybersecurity: Governance vs Management
Cyber security governance should not be confused with cyber security management. Cyber security management is concerned with making decisions to mitigate risks; governance determines who is authorized to make decisions. Governance specifies the accountability framework and provides oversight to ensure that risks are adequately mitigated, while management ensures that controls are implemented to mitigate risks. Management recommends security strategies. Governance ensures that security strategies are aligned with business objectives and consistent with regulations.NIST describes IT governance as the process of establishing and maintaining a framework to provide assurance that information security strategies are aligned with and support business objectives, are consistent with applicable laws and regulations through adherence to policies and internal controls, and provide assignment of responsibility, all in an effort to manage risk.
Governance: doing the right thing.
Management: doing things right.
Governance | Management |
|---|---|
Oversight | Implementation |
Authorizes decision rights | Authorized to make decisions |
Enact policy | Enforce policy |
Accountability | Responsibility |
Strategic planning | Project planning |
Resource allocation | Resource utilization |
Governance vs Operation
Making the organizational move from a divided hierarchy to one in which strategy informs operation (and operation informs strategy) is a difficult challenge. Communication is key to effectively managing expectations, messaging, and security posture throughout the process.
Detect, prioritize, and control
Operational controls – the real-life response to a cybersecurity incident – should be the focus of any security program. Managing these controls and reporting to a governance structure may not require the knowledge of operationalization, but instead may rely on an agreed-upon level of confidence in respect to risk management involving both governance and operational leadership.
In addition to working alongside governance experts, operational controls managers should measure their security posture against a framework or baseline such as the CIS Controls™ or NIST Cyber Security Framework. Conducting such an assessment is important, as understanding your organization’s compliance levels is key to finding weaknesses in the organizational controls as well as the prioritization of investment for strengthening controls.
A previous blog post discussed calculating your risk-reduction ROI; after identifying weaker controls, we can start to use this single calculation to define what provides the greatest level of return on investment as well as the greatest reduction in risk. In future blog posts, risk will be discussed with respect to quantitative analysis, using a Monte Carlo simulation to demonstrate how a single risk and control mitigation can provide an overall reduction in risk to the whole organization.
With clearer reporting and analysis of risk reduction, we can bridge the gap between governance and operational security, leading to better strategic decision making and a more unified approach to the cyber threat landscape.
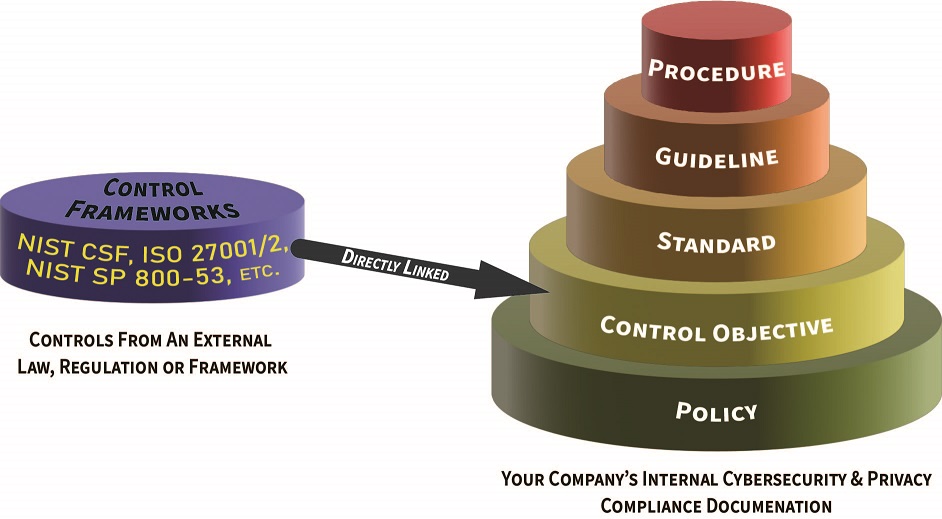
Policy vs Standard vs Control vs Procedure
Plan - Do - Check - Act model
The ICGM utilizes a Plan, Do, Check & Act (PCDA) approach that is a logical way to design a governance structure:
- Plan. The overall GRC/IRM process beings with planning. This planning will define the policies, standards and controls for the organization. It will also directly influence the tools and services that an organization purchases, since technology purchases should address needs that are defined by policies and standards.
- Do. Arguably, this is the most important section for cybersecurity and privacy practitioners. Controls are the “security glue” that make processes, applications, systems and services secure. Procedures (also referred to as control activities) are the processes how the controls are actually implemented and performed. The Secure Controls Framework (SCF) can be an excellent starting point for a control set if your organization lacks a comprehensive set of cybersecurity and privacy controls.
- Check. In simple terms, this is situational awareness. Situational awareness is only achieved through reporting through metrics and reviewing the results of audits/assessments.
- Act. This is essentially risk management, which is an encompassing area that deals with addressing two main concepts (1) real deficiencies that currently exist and (2) possible threats to the organization.
- Plan – Policies & Standards
- Do – Controls & Procedures
- Check – Reporting & Assessments
- Act – Risk Management
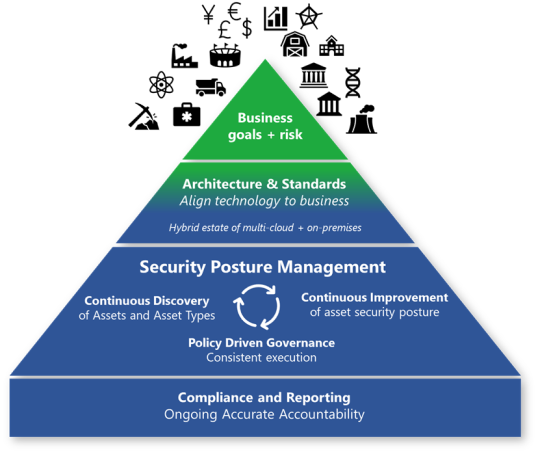
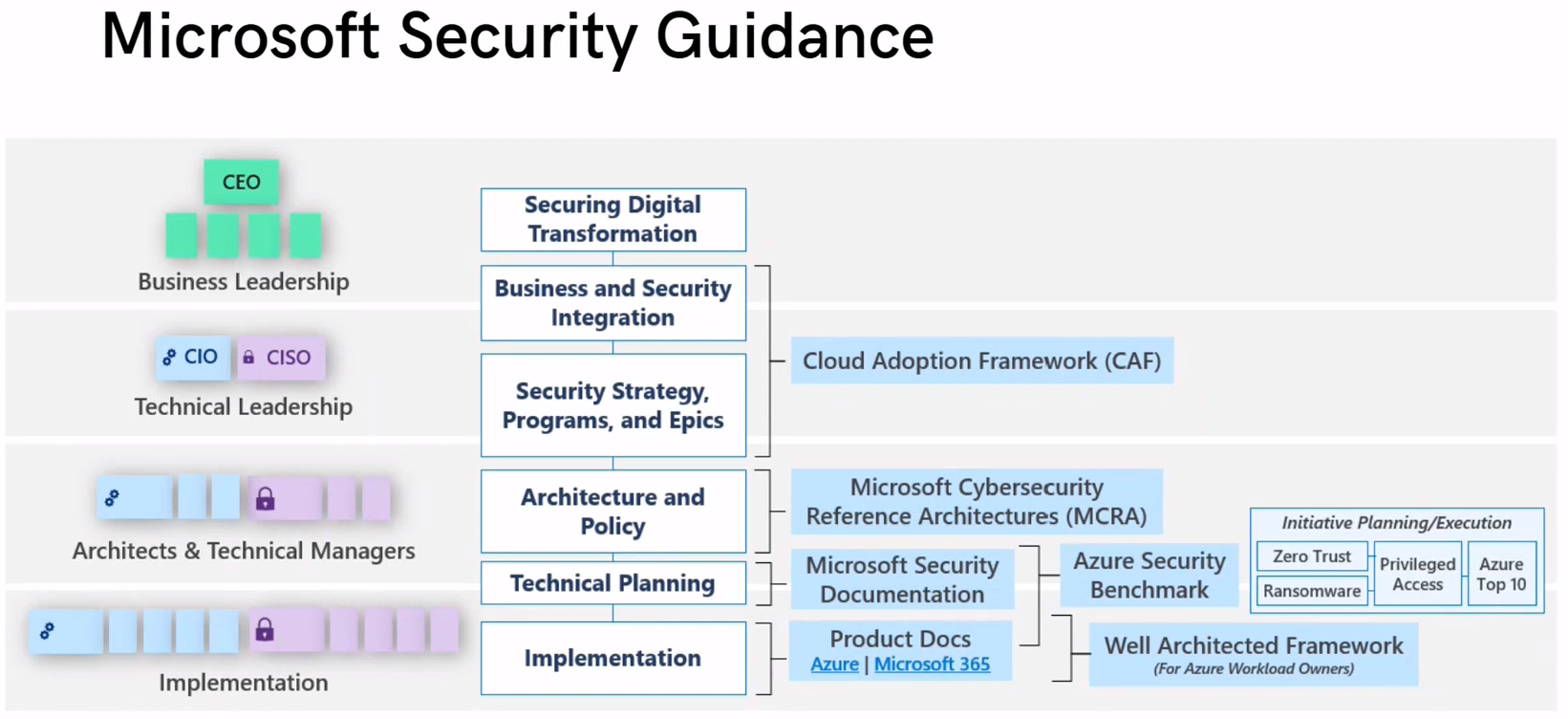
Microsoft Security Goverance
Governance and security operations provide complementary types of visibility.
- Security operations provide insight into the immediate risk of active attacks.
- Security governance provides a broad or long view of risk from potential future attacks and attack vectors.
Hierarchical Cybersecurity Governance Framework (HCGF)
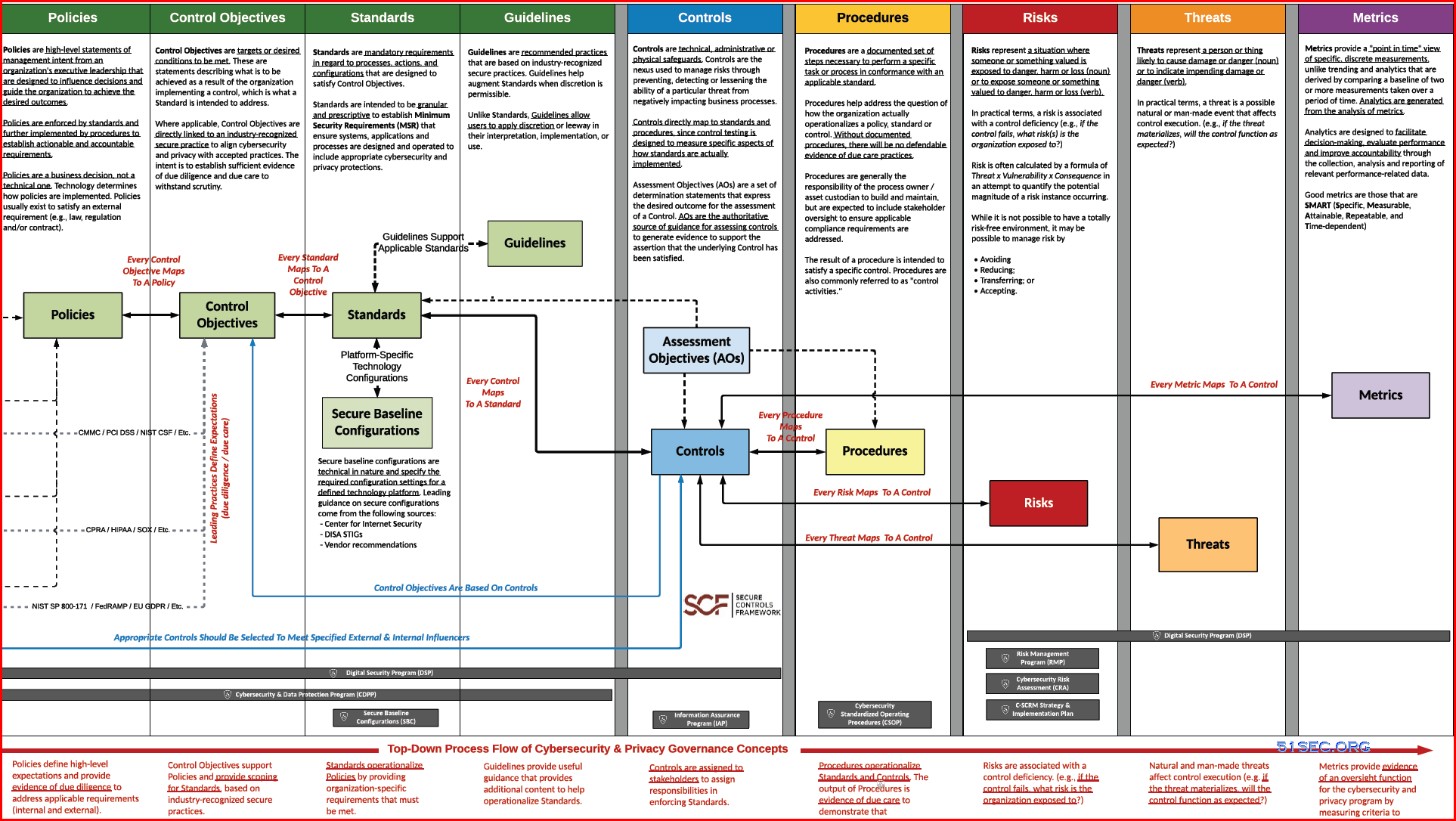
In an effort to help clarify this concept, ComplianceForge Hierarchical Cybersecurity Governance Framework™ (HCGF) takes a comprehensive view towards the necessary documentation components that are key to being able to demonstrate evidence of due diligence and due care. This framework addresses the interconnectivity of policies, control objectives, standards, guidelines, controls, risks, procedures & metrics. The Secure Controls Framework (SCF) fits into this model by providing the necessary cybersecurity and privacy controls an organization needs to implement to stay both secure and compliant.
ComplianceForge has simplified the concept of the hierarchical nature of cybersecurity and privacy documentation in the following downloadable diagram to demonstrate the unique nature of these components, as well as the dependencies that exist:








No comments:
Post a Comment