This post summarize some NIST CSF related resources and tools.
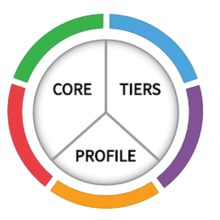
NIST Framework Components
The Cybersecurity Framework consists of three main components:
- The Framework Core provides a set of desired cybersecurity activities and outcomes using common language that is easy to understand.
- The Framework Implementation Tiers assist organizations by providing context on how an organization views cybersecurity risk management.
- Framework Profiles are an organization’s unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core.
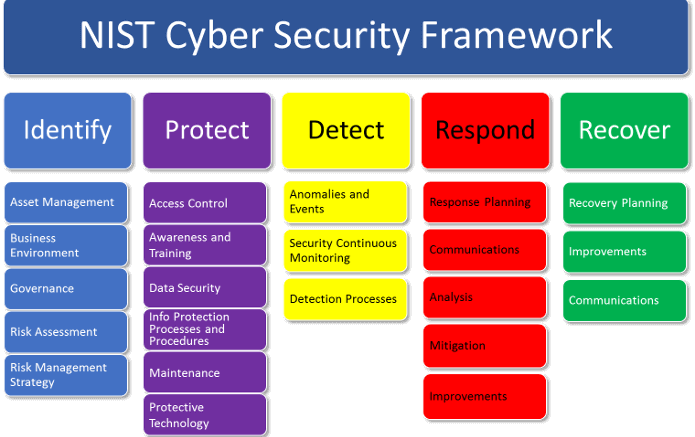
NIST Core
- Identity - Risk Assessment (Inventory, if you donot know what you have, you can protect them)
- Protect - Defensive Capabilities
- Detect - Advanced Threat Detection - (Active, Dynamic and Continuous monitoring)
- Respond - Strategic Response
- Recover - Disaster Recovery
How NIST CSF Core Category mapping to four main functions:
- Risk and Compliance (Governance) - What do I need to protect and how well am I doing it
- Security Architecture and Design - What is the business trying to do, how am I going to protect it, and how will I know it is working?
- Security Administratration - Who needs what access where, how much and how long for
- Security Operations - Detect, respond and what is coming our way
NIST CSF Tiers
The NIST CSF Tiers represent how well an organization views cybersecurity risk and the processes in place to mitigate risks. This helps provide organizations a benchmark on how their current operations.
- Tier 1 – Partial: Organizational cybersecurity risk is not formalized and managed in an ad hoc and sometimes reactive manner. There is also limited awareness of cybersecurity risk management.
- Tier 2 – Risk-Informed: There may not be an organizational-wide policy for security risk management. Management handles cybersecurity risk management based on risks as they happen.
- Tier 3 – Repeatable: A formal organizational risk management process is followed by a defined security policy.
- Tier 4 – Adaptable: An organization at this stage will adapt its cybersecurity policies based on lessons learned and analytics-driven to provide insights and best practices. The organization is constantly learning from the security events that do occur in the organization and will share that information with a larger network.
You can use the NIST CSF to benchmark your current security posture. Going through each category and subcategories in the core Function can help you determine where you stand on the NIST CSF Tier scale.
NIST Core Category (23) and Subcategory (108)
| Function | Category | Subcategory | Informative References |
| IDENTIFY (ID) | · CCS CSC 1 | ||
| · COBIT 5 BAI09.01, BAI09.02 | |||
| · ISA 62443-2-1:2009 4.2.3.4 | |||
| · ISA 62443-3-3:2013 SR 7.8 | |||
| · ISO/IEC 27001:2013 A.8.1.1, A.8.1.2 | |||
| · NIST SP 800-53 Rev. 4 CM-8 | |||
| · CCS CSC 2 | |||
| · COBIT 5 BAI09.01, BAI09.02, BAI09.05 | |||
| · ISA 62443-2-1:2009 4.2.3.4 | |||
| · ISA 62443-3-3:2013 SR 7.8 | |||
| · ISO/IEC 27001:2013 A.8.1.1, A.8.1.2 | |||
| · NIST SP 800-53 Rev. 4 CM-8 | |||
| · CCS CSC 1 | |||
| · COBIT 5 DSS05.02 | |||
| · ISA 62443-2-1:2009 4.2.3.4 | |||
| · ISO/IEC 27001:2013 A.13.2.1 | |||
| · NIST SP 800-53 Rev. 4 AC-4, CA-3, CA-9, PL-8 | |||
| · COBIT 5 APO02.02 | |||
| · ISO/IEC 27001:2013 A.11.2.6 | |||
| · NIST SP 800-53 Rev. 4 AC-20, SA-9 | |||
| · COBIT 5 APO03.03, APO03.04, BAI09.02 | |||
| · ISA 62443-2-1:2009 4.2.3.6 | |||
| · ISO/IEC 27001:2013 A.8.2.1 | |||
| · NIST SP 800-53 Rev. 4 CP-2, RA-2, SA-14 | |||
| · COBIT 5 APO01.02, DSS06.03 | |||
| · ISA 62443-2-1:2009 4.3.2.3.3 | |||
| · ISO/IEC 27001:2013 A.6.1.1 | |||
| · NIST SP 800-53 Rev. 4 CP-2, PS-7, PM-11 | |||
| · COBIT 5 APO08.04, APO08.05, APO10.03, APO10.04, APO10.05 | |||
| · ISO/IEC 27001:2013 A.15.1.3, A.15.2.1, A.15.2.2 | |||
| · NIST SP 800-53 Rev. 4 CP-2, SA-12 | |||
| · COBIT 5 APO02.06, APO03.01 | |||
| · NIST SP 800-53 Rev. 4 PM-8 | |||
| · COBIT 5 APO02.01, APO02.06, APO03.01 | |||
| · ISA 62443-2-1:2009 4.2.2.1, 4.2.3.6 | |||
| · NIST SP 800-53 Rev. 4 PM-11, SA-14 | |||
| · ISO/IEC 27001:2013 A.11.2.2, A.11.2.3, A.12.1.3 | |||
| · NIST SP 800-53 Rev. 4 CP-8, PE-9, PE-11, PM-8, SA-14 | |||
| · COBIT 5 DSS04.02 | |||
| · ISO/IEC 27001:2013 A.11.1.4, A.17.1.1, A.17.1.2, A.17.2.1 | |||
| · NIST SP 800-53 Rev. 4 CP-2, CP-11, SA-14 | |||
| · COBIT 5 APO01.03, EDM01.01, EDM01.02 | |||
| · ISA 62443-2-1:2009 4.3.2.6 | |||
| · ISO/IEC 27001:2013 A.5.1.1 | |||
| · NIST SP 800-53 Rev. 4 -1 controls from all families | |||
| · COBIT 5 APO13.12 | |||
| · ISA 62443-2-1:2009 4.3.2.3.3 | |||
| · ISO/IEC 27001:2013 A.6.1.1, A.7.2.1 | |||
| · NIST SP 800-53 Rev. 4 PM-1, PS-7 | |||
| · COBIT 5 MEA03.01, MEA03.04 | |||
| · ISA 62443-2-1:2009 4.4.3.7 | |||
| · ISO/IEC 27001:2013 A.18.1 | |||
| · NIST SP 800-53 Rev. 4 -1 controls from all families (except PM-1) | |||
| · COBIT 5 DSS04.02 | |||
| · NIST SP 800-53 Rev. 4 PM-9, PM-11 | |||
| · CCS CSC 4 | |||
| · COBIT 5 APO12.01, APO12.02, APO12.03, APO12.04 | |||
| · ISA 62443-2-1:2009 4.2.3, 4.2.3.7, 4.2.3.9, 4.2.3.12 | |||
| · ISO/IEC 27001:2013 A.12.6.1, A.18.2.3 | |||
| · ISA 62443-2-1:2009 4.2.3, 4.2.3.9, 4.2.3.12 | |||
| · ISO/IEC 27001:2013 A.6.1.4 | |||
| · NIST SP 800-53 Rev. 4 PM-15, PM-16, SI-5 | |||
| · COBIT 5 APO12.01, APO12.02, APO12.03, APO12.04 | |||
| · ISA 62443-2-1:2009 4.2.3, 4.2.3.9, 4.2.3.12 | |||
| · NIST SP 800-53 Rev. 4 RA-3, SI-5, PM-12, PM-16 | |||
| · COBIT 5 DSS04.02 | |||
| · ISA 62443-2-1:2009 4.2.3, 4.2.3.9, 4.2.3.12 | |||
| · NIST SP 800-53 Rev. 4 RA-2, RA-3, PM-9, PM-11, SA-14 | |||
| · COBIT 5 APO12.02 | |||
| · ISO/IEC 27001:2013 A.12.6.1 | |||
| · NIST SP 800-53 Rev. 4 RA-2, RA-3, PM-16 | |||
| · COBIT 5 APO12.05, APO13.02 | |||
| · NIST SP 800-53 Rev. 4 PM-4, PM-9 | |||
| · COBIT 5 APO12.04, APO12.05, APO13.02, BAI02.03, BAI04.02 | |||
| · ISA 62443-2-1:2009 4.3.4.2 | |||
| · NIST SP 800-53 Rev. 4 PM-9 | |||
| · COBIT 5 APO12.06 | |||
| · ISA 62443-2-1:2009 4.3.2.6.5 | |||
| · NIST SP 800-53 Rev. 4 PM-9 | |||
| · NIST SP 800-53 Rev. 4 PM-8, PM-9, PM-11, SA-14 | |||
| PROTECT (PR) | · CCS CSC 16 | ||
| · COBIT 5 DSS05.04, DSS06.03 | |||
| · ISA 62443-2-1:2009 4.3.3.5.1 | |||
| · NIST SP 800-53 Rev. 4 AC-2, IA Family | |||
| · COBIT 5 DSS01.04, DSS05.05 | |||
| · ISA 62443-2-1:2009 4.3.3.3.2, 4.3.3.3.8 | |||
| · ISO/IEC 27001:2013 A.11.1.1, A.11.1.2, A.11.1.4, A.11.1.6, A.11.2.3 | |||
| · NIST SP 800-53 Rev. 4 PE-2, PE-3, PE-4, PE-5, PE-6, PE-9 | |||
| PR.AC-3: Remote access is managed | · COBIT 5 APO13.01, DSS01.04, DSS05.03 | ||
| · ISA 62443-2-1:2009 4.3.3.6.6 | |||
| · ISA 62443-3-3:2013 SR 1.13, SR 2.6 | |||
| · ISO/IEC 27001:2013 A.6.2.2, A.13.1.1, A.13.2.1 | |||
| · NIST SP 800-53 Rev. 4 AC‑17, AC-19, AC-20 | |||
| · CCS CSC 12, 15 | |||
| · ISA 62443-2-1:2009 4.3.3.7.3 | |||
| · ISA 62443-3-3:2013 SR 2.1 | |||
| · ISO/IEC 27001:2013 A.6.1.2, A.9.1.2, A.9.2.3, A.9.4.1, A.9.4.4 | |||
| · NIST SP 800-53 Rev. 4 AC-2, AC-3, AC-5, AC-6, AC-16 | |||
| · ISA 62443-2-1:2009 4.3.3.4 | |||
| · ISA 62443-3-3:2013 SR 3.1, SR 3.8 | |||
| · ISO/IEC 27001:2013 A.13.1.1, A.13.1.3, A.13.2.1 | |||
| · NIST SP 800-53 Rev. 4 AC-4, SC-7 | |||
| PR.AT-1: All users are informed and trained | · CCS CSC 9 | ||
| · COBIT 5 APO07.03, BAI05.07 | |||
| · ISA 62443-2-1:2009 4.3.2.4.2 | |||
| · ISO/IEC 27001:2013 A.7.2.2 | |||
| · NIST SP 800-53 Rev. 4 AT-2, PM-13 | |||
| · CCS CSC 9 | |||
| · COBIT 5 APO07.02, DSS06.03 | |||
| · ISA 62443-2-1:2009 4.3.2.4.2, 4.3.2.4.3 | |||
| · ISO/IEC 27001:2013 A.6.1.1, A.7.2.2 | |||
| · NIST SP 800-53 Rev. 4 AT-3, PM-13 | |||
| · CCS CSC 9 | |||
| · COBIT 5 APO07.03, APO10.04, APO10.05 | |||
| · ISA 62443-2-1:2009 4.3.2.4.2 | |||
| · ISO/IEC 27001:2013 A.6.1.1, A.7.2.2 | |||
| · NIST SP 800-53 Rev. 4 PS-7, SA-9 | |||
| · CCS CSC 9 | |||
| · COBIT 5 APO07.03 | |||
| · ISA 62443-2-1:2009 4.3.2.4.2 | |||
| · ISO/IEC 27001:2013 A.6.1.1, A.7.2.2, | |||
| · NIST SP 800-53 Rev. 4 AT-3, PM-13 | |||
| · CCS CSC 9 | |||
| · COBIT 5 APO07.03 | |||
| · ISA 62443-2-1:2009 4.3.2.4.2 | |||
| · ISO/IEC 27001:2013 A.6.1.1, A.7.2.2, | |||
| · NIST SP 800-53 Rev. 4 AT-3, PM-13 | |||
| PR.DS-1: Data-at-rest is protected | · CCS CSC 17 | ||
| · COBIT 5 APO01.06, BAI02.01, BAI06.01, DSS06.06 | |||
| · ISA 62443-3-3:2013 SR 3.4, SR 4.1 | |||
| · ISO/IEC 27001:2013 A.8.2.3 | |||
| · NIST SP 800-53 Rev. 4 SC-28 | |||
| PR.DS-2: Data-in-transit is protected | · CCS CSC 17 | ||
| · COBIT 5 APO01.06, DSS06.06 | |||
| · ISA 62443-3-3:2013 SR 3.1, SR 3.8, SR 4.1, SR 4.2 | |||
| · NIST SP 800-53 Rev. 4 SC-8 | |||
| · COBIT 5 BAI09.03 | |||
| · ISA 62443-2-1:2009 4. 4.3.3.3.9, 4.3.4.4.1 | |||
| · ISA 62443-3-3:2013 SR 4.2 | |||
| · ISO/IEC 27001:2013 A.8.2.3, A.8.3.1, A.8.3.2, A.8.3.3, A.11.2.7 | |||
| · NIST SP 800-53 Rev. 4 CM-8, MP-6, PE-16 | |||
| · COBIT 5 APO13.01 | |||
| · ISA 62443-3-3:2013 SR 7.1, SR 7.2 | |||
| · ISO/IEC 27001:2013 A.12.3.1 | |||
| · NIST SP 800-53 Rev. 4 AU-4, CP-2, SC-5 | |||
| · CCS CSC 17 | |||
| · COBIT 5 APO01.06 | |||
| · ISA 62443-3-3:2013 SR 5.2 | |||
| · ISA 62443-3-3:2013 SR 3.1, SR 3.3, SR 3.4, SR 3.8 | |||
| · ISO/IEC 27001:2013 A.12.2.1, A.12.5.1, A.14.1.2, A.14.1.3 | |||
| · NIST SP 800-53 Rev. 4 SI-7 | |||
| · COBIT 5 BAI07.04 | |||
| · ISO/IEC 27001:2013 A.12.1.4 | |||
| · NIST SP 800-53 Rev. 4 CM-2 | |||
| · CCS CSC 3, 10 | |||
| · COBIT 5 BAI10.01, BAI10.02, BAI10.03, BAI10.05 | |||
| · ISA 62443-2-1:2009 4.3.4.3.2, 4.3.4.3.3 | |||
| · ISA 62443-3-3:2013 SR 7.6 | |||
| · NIST SP 800-53 Rev. 4 CM-2, CM-3, CM-4, CM-5, CM-6, CM-7, CM-9, SA-10 | |||
| · COBIT 5 APO13.01 | |||
| · ISA 62443-2-1:2009 4.3.4.3.3 | |||
| · ISO/IEC 27001:2013 A.6.1.5, A.14.1.1, A.14.2.1, A.14.2.5 | |||
| · COBIT 5 BAI06.01, BAI01.06 | |||
| · ISA 62443-2-1:2009 4.3.4.3.2, 4.3.4.3.3 | |||
| · ISA 62443-3-3:2013 SR 7.6 | |||
| · NIST SP 800-53 Rev. 4 CM-3, CM-4, SA-10 | |||
| · COBIT 5 APO13.01 | |||
| · ISA 62443-2-1:2009 4.3.4.3.9 | |||
| · ISA 62443-3-3:2013 SR 7.3, SR 7.4 | |||
| · ISO/IEC 27001:2013 A.12.3.1, A.17.1.2A.17.1.3, A.18.1.3 | |||
| · NIST SP 800-53 Rev. 4 CP-4, CP-6, CP-9 | |||
| · COBIT 5 DSS01.04, DSS05.05 | |||
| · ISO/IEC 27001:2013 A.11.1.4, A.11.2.1, A.11.2.2, A.11.2.3 | |||
| · NIST SP 800-53 Rev. 4 PE-10, PE-12, PE-13, PE-14, PE-15, PE-18 | |||
| · COBIT 5 BAI09.03 | |||
| · ISA 62443-2-1:2009 4.3.4.4.4 | |||
| · ISA 62443-3-3:2013 SR 4.2 | |||
| · ISO/IEC 27001:2013 A.8.2.3, A.8.3.1, A.8.3.2, A.11.2.7 | |||
| · NIST SP 800-53 Rev. 4 MP-6 | |||
| · COBIT 5 APO11.06, DSS04.05 | |||
| · NIST SP 800-53 Rev. 4 CA-2, CA-7, CP-2, IR-8, PL-2, PM-6 | |||
| · ISO/IEC 27001:2013 A.16.1.6 | |||
| · NIST SP 800-53 Rev. 4 AC-21, CA-7, SI-4 | |||
| · COBIT 5 DSS04.03 | |||
| · ISA 62443-2-1:2009 4.3.2.5.3, 4.3.4.5.1 | |||
| · ISO/IEC 27001:2013 A.16.1.1, A.17.1.1, A.17.1.2 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-8 | |||
| · ISA 62443-2-1:2009 4.3.2.5.7, 4.3.4.5.11 | |||
| · ISA 62443-3-3:2013 SR 3.3 | |||
| · ISO/IEC 27001:2013 A.17.1.3 | |||
| · NIST SP 800-53 Rev.4 CP-4, IR-3, PM-14 | |||
| · COBIT 5 APO07.01, APO07.02, APO07.03, APO07.04, APO07.05 | |||
| · ISA 62443-2-1:2009 4.3.3.2.1, 4.3.3.2.2, 4.3.3.2.3 | |||
| · ISO/IEC 27001:2013 A.7.1.1, A.7.3.1, A.8.1.4 | |||
| · NIST SP 800-53 Rev. 4 PS Family | |||
| · ISO/IEC 27001:2013 A.12.6.1, A.18.2.2 | |||
| · NIST SP 800-53 Rev. 4 RA-3, RA-5, SI-2 | |||
| · COBIT 5 BAI09.03 | |||
| · ISA 62443-2-1:2009 4.3.3.3.7 | |||
| · ISO/IEC 27001:2013 A.11.1.2, A.11.2.4, A.11.2.5 | |||
| · NIST SP 800-53 Rev. 4 MA-2, MA-3, MA-5 | |||
| · COBIT 5 DSS05.04 | |||
| · ISA 62443-2-1:2009 4.3.3.6.5, 4.3.3.6.6, 4.3.3.6.7, 4.4.4.6.8 | |||
| · ISO/IEC 27001:2013 A.11.2.4, A.15.1.1, A.15.2.1 | |||
| · NIST SP 800-53 Rev. 4 MA-4 | |||
| · CCS CSC 14 | |||
| · COBIT 5 APO11.04 | |||
| · ISA 62443-3-3:2013 SR 2.8, SR 2.9, SR 2.10, SR 2.11, SR 2.12 | |||
| · ISO/IEC 27001:2013 A.12.4.1, A.12.4.2, A.12.4.3, A.12.4.4, A.12.7.1 | |||
| · NIST SP 800-53 Rev. 4 AU Family | |||
| · COBIT 5 DSS05.02, APO13.01 | |||
| · ISA 62443-3-3:2013 SR 2.3 | |||
| · ISO/IEC 27001:2013 A.8.2.2, A.8.2.3, A.8.3.1, A.8.3.3, A.11.2.9 | |||
| · NIST SP 800-53 Rev. 4 MP-2, MP-4, MP-5, MP-7 | |||
| · COBIT 5 DSS05.02 | |||
| · ISO/IEC 27001:2013 A.9.1.2 | |||
| · NIST SP 800-53 Rev. 4 AC-3, CM-7 | |||
| · CCS CSC 7 | |||
| · COBIT 5 DSS05.02, APO13.01 | |||
| · ISO/IEC 27001:2013 A.13.1.1, A.13.2.1 | |||
| · NIST SP 800-53 Rev. 4 AC-4, AC-17, AC-18, CP-8, SC-7 | |||
| DETECT (DE) | · COBIT 5 DSS03.01 | ||
| · ISA 62443-2-1:2009 4.4.3.3 | |||
| · NIST SP 800-53 Rev. 4 AC-4, CA-3, CM-2, SI-4 | |||
| · ISA 62443-2-1:2009 4.3.4.5.6, 4.3.4.5.7, 4.3.4.5.8 | |||
| · ISO/IEC 27001:2013 A.16.1.1, A.16.1.4 | |||
| · NIST SP 800-53 Rev. 4 AU-6, CA-7, IR-4, SI-4 | |||
| · ISA 62443-3-3:2013 SR 6.1 | |||
| · NIST SP 800-53 Rev. 4 AU-6, CA-7, IR-4, IR-5, IR-8, SI-4 | |||
| DE.AE-4: Impact of events is determined | · COBIT 5 APO12.06 | ||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4, RA-3, SI -4 | |||
| · COBIT 5 APO12.06 | |||
| · ISA 62443-2-1:2009 4.2.3.10 | |||
| · NIST SP 800-53 Rev. 4 IR-4, IR-5, IR-8 | |||
| · CCS CSC 14, 16 | |||
| · COBIT 5 DSS05.07 | |||
| · ISA 62443-3-3:2013 SR 6.2 | |||
| · NIST SP 800-53 Rev. 4 AC-2, AU-12, CA-7, CM-3, SC-5, SC-7, SI-4 | |||
| · ISA 62443-2-1:2009 4.3.3.3.8 | |||
| · NIST SP 800-53 Rev. 4 CA-7, PE-3, PE-6, PE-20 | |||
| · ISA 62443-3-3:2013 SR 6.2 | |||
| · ISO/IEC 27001:2013 A.12.4.1 | |||
| · NIST SP 800-53 Rev. 4 AC-2, AU-12, AU-13, CA-7, CM-10, CM-11 | |||
| DE.CM-4: Malicious code is detected | · CCS CSC 5 | ||
| · COBIT 5 DSS05.01 | |||
| · ISA 62443-2-1:2009 4.3.4.3.8 | |||
| · ISA 62443-3-3:2013 SR 3.2 | |||
| · ISO/IEC 27001:2013 A.12.2.1 | |||
| · NIST SP 800-53 Rev. 4 SI-3 | |||
| · ISA 62443-3-3:2013 SR 2.4 | |||
| · ISO/IEC 27001:2013 A.12.5.1 | |||
| · NIST SP 800-53 Rev. 4 SC-18, SI-4. SC-44 | |||
| · COBIT 5 APO07.06 | |||
| · ISO/IEC 27001:2013 A.14.2.7, A.15.2.1 | |||
| · NIST SP 800-53 Rev. 4 CA-7, PS-7, SA-4, SA-9, SI-4 | |||
| · NIST SP 800-53 Rev. 4 AU-12, CA-7, CM-3, CM-8, PE-3, PE-6, PE-20, SI-4 | |||
| DE.CM-8: Vulnerability scans are performed | · COBIT 5 BAI03.10 | ||
| · ISA 62443-2-1:2009 4.2.3.1, 4.2.3.7 | |||
| · ISO/IEC 27001:2013 A.12.6.1 | |||
| · NIST SP 800-53 Rev. 4 RA-5 | |||
| · CCS CSC 5 | |||
| · COBIT 5 DSS05.01 | |||
| · ISA 62443-2-1:2009 4.4.3.1 | |||
| · ISO/IEC 27001:2013 A.6.1.1 | |||
| · NIST SP 800-53 Rev. 4 CA-2, CA-7, PM-14 | |||
| · ISA 62443-2-1:2009 4.4.3.2 | |||
| · ISO/IEC 27001:2013 A.18.1.4 | |||
| · NIST SP 800-53 Rev. 4 CA-2, CA-7, PM-14, SI-4 | |||
| DE.DP-3: Detection processes are tested | · COBIT 5 APO13.02 | ||
| · ISA 62443-2-1:2009 4.4.3.2 | |||
| · ISA 62443-3-3:2013 SR 3.3 | |||
| · ISO/IEC 27001:2013 A.14.2.8 | |||
| · NIST SP 800-53 Rev. 4 CA-2, CA-7, PE-3, PM-14, SI-3, SI-4 | |||
| · COBIT 5 APO12.06 | |||
| · ISA 62443-2-1:2009 4.3.4.5.9 | |||
| · ISA 62443-3-3:2013 SR 6.1 | |||
| · ISO/IEC 27001:2013 A.16.1.2 | |||
| · NIST SP 800-53 Rev. 4 AU-6, CA-2, CA-7, RA-5, SI-4 | |||
| · COBIT 5 APO11.06, DSS04.05 | |||
| · ISA 62443-2-1:2009 4.4.3.4 | |||
| · ISO/IEC 27001:2013 A.16.1.6 | |||
| · NIST SP 800-53 Rev. 4, CA-2, CA-7, PL-2, RA-5, SI-4, PM-14 | |||
| RESPOND (RS) | · COBIT 5 BAI01.10 | ||
| · CCS CSC 18 | |||
| · ISA 62443-2-1:2009 4.3.4.5.1 | |||
| · ISO/IEC 27001:2013 A.16.1.5 | |||
| · NIST SP 800-53 Rev. 4 CP-2, CP-10, IR-4, IR-8 | |||
| · ISA 62443-2-1:2009 4.3.4.5.2, 4.3.4.5.3, 4.3.4.5.4 | |||
| · ISO/IEC 27001:2013 A.6.1.1, A.16.1.1 | |||
| · NIST SP 800-53 Rev. 4 CP-2, CP-3, IR-3, IR-8 | |||
| · ISA 62443-2-1:2009 4.3.4.5.5 | |||
| · ISO/IEC 27001:2013 A.6.1.3, A.16.1.2 | |||
| · NIST SP 800-53 Rev. 4 AU-6, IR-6, IR-8 | |||
| · ISA 62443-2-1:2009 4.3.4.5.2 | |||
| · ISO/IEC 27001:2013 A.16.1.2 | |||
| · NIST SP 800-53 Rev. 4 CA-2, CA-7, CP-2, IR-4, IR-8, PE-6, RA-5, SI-4 | |||
| · ISA 62443-2-1:2009 4.3.4.5.5 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-8 | |||
| · NIST SP 800-53 Rev. 4 PM-15, SI-5 | |||
| · COBIT 5 DSS02.07 | |||
| · ISA 62443-2-1:2009 4.3.4.5.6, 4.3.4.5.7, 4.3.4.5.8 | |||
| · ISA 62443-3-3:2013 SR 6.1 | |||
| · ISO/IEC 27001:2013 A.12.4.1, A.12.4.3, A.16.1.5 | |||
| · NIST SP 800-53 Rev. 4 AU-6, CA-7, IR-4, IR-5, PE-6, SI-4 | |||
| · ISA 62443-2-1:2009 4.3.4.5.6, 4.3.4.5.7, 4.3.4.5.8 | |||
| · ISO/IEC 27001:2013 A.16.1.6 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4 | |||
| RS.AN-3: Forensics are performed | |||
| · ISO/IEC 27001:2013 A.16.1.7 | |||
| · NIST SP 800-53 Rev. 4 AU-7, IR-4 | |||
| · ISA 62443-2-1:2009 4.3.4.5.6 | |||
| · ISO/IEC 27001:2013 A.16.1.4 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-5, IR-8 | |||
| RS.MI-1: Incidents are contained | · ISA 62443-2-1:2009 4.3.4.5.6 | ||
| · ISA 62443-3-3:2013 SR 5.1, SR 5.2, SR 5.4 | |||
| · ISO/IEC 27001:2013 A.16.1.5 | |||
| · NIST SP 800-53 Rev. 4 IR-4 | |||
| RS.MI-2: Incidents are mitigated | · ISA 62443-2-1:2009 4.3.4.5.6, 4.3.4.5.10 | ||
| · ISO/IEC 27001:2013 A.12.2.1, A.16.1.5 | |||
| · NIST SP 800-53 Rev. 4 IR-4 | |||
| · ISO/IEC 27001:2013 A.12.6.1 | |||
| · NIST SP 800-53 Rev. 4 CA-7, RA-3, RA-5 | |||
| · COBIT 5 BAI01.13 | |||
| · ISA 62443-2-1:2009 4.3.4.5.10, 4.4.3.4 | |||
| · ISO/IEC 27001:2013 A.16.1.6 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-8 | |||
| RS.IM-2: Response strategies are updated | · NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-8 | ||
| RECOVER (RC) | · CCS CSC 8 | ||
| · COBIT 5 DSS02.05, DSS03.04 | |||
| · ISO/IEC 27001:2013 A.16.1.5 | |||
| · NIST SP 800-53 Rev. 4 CP-10, IR-4, IR-8 | |||
| · COBIT 5 BAI05.07 | |||
| · ISA 62443-2-1 4.4.3.4 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-8 | |||
| RC.IM-2: Recovery strategies are updated | · COBIT 5 BAI07.08 | ||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4, IR-8 | |||
| RC.CO-1: Public relations are managed | · COBIT 5 EDM03.02 | ||
| · COBIT 5 MEA03.02 | |||
| · NIST SP 800-53 Rev. 4 CP-2, IR-4 |
NIST CSF Profiles
Profiles are an organization's unique alignment of their organizational requirements and objectives, risk appetite, and resources against the desired outcomes of the Framework Core. Profiles can be used to identify opportunities for improving cybersecurity posture by comparing a “Current” Profile with a “Target” Profile.
Profiles are about optimizing the Cybersecurity Framework to best serve the organization. The Framework is voluntary, so there is no ‘right’ or ‘wrong’ way to do it. One way of approaching profiles is for an organization to map their cybersecurity requirements, mission objectives, and operating methodologies, along with current practices against the subcategories of the Framework Core to create a Current-State Profile. These requirements and objectives can be compared against the current operating state of the organization to gain an understanding of the gaps between the two.
Tools and Resources
- Axio Cybersecurity Program Assessment Tool
(A free assessment tool that assists in identifying an organization’s cyber posture.) - Baldrige Cybersecurity Excellence Builder
(A self-assessment tool to help organizations better understand the effectiveness of their cybersecurity risk management efforts and identity improvement opportunities in the context of their overall organizational performance.) - Cohesive
Networks' "Putting the NIST Cybersecurity Framework to
Work"
(A guide for using the NIST Framework to guide best practices for security audits, compliance, and communication.) - Facility Cybersecurity Facility Cybersecurity
framework (FCF)
(An assessment tool that follows the NIST Cybersecurity Framework and helps facility owners and operators manage their cyber security risks in core OT & IT controls.) - Information
Systems Audit and Control Association's Implementing the NIST Cybersecurity Framework and
Supplementary Toolkit
- ISACA's Cybersecurity: Based on the NIST Cybersecurity
Framework
(An audit program based on the NIST Cybersecurity Framework and covers sub-processes such as asset management, awareness training, data security, resource planning, recover planning and communications.) - Rivial
Security's Vendor Cybersecurity Tool
(A guide to using the Framework to assess vendor security.) - The Department
of Homeland Security Industrial Control Systems Cyber Emergency Response
Team's (ICS-CERT) Cyber Security Evaluation Tool (CSET) download, fact sheet, introductory CSET video, and walkthrough video of the Cybersecurity Framework approach within CSET
- University of Maryland Robert H. Smith School of
Business Supply Chain Management Center's CyberChain Portal-Based
Assessment Tool
(Provides guidelines to measure and assess cyber supply chain risk.) - Free NIST CSF Maturity Tool
Note: https://www.nist.gov/cyberframework/assessment-auditing-resources
References
- NIST CSF Core
- An Introduction to the Components of the Framework
- NIST Cybersecurity Framework (CSF) Aligning to the NIST CSF in the AWS Cloud
- NIST SP 800-53 Full Control List (contains nearly one thousand controls spread across 19 different controls families.)
- Free NIST CSF Maturity Tool











No comments:
Post a Comment