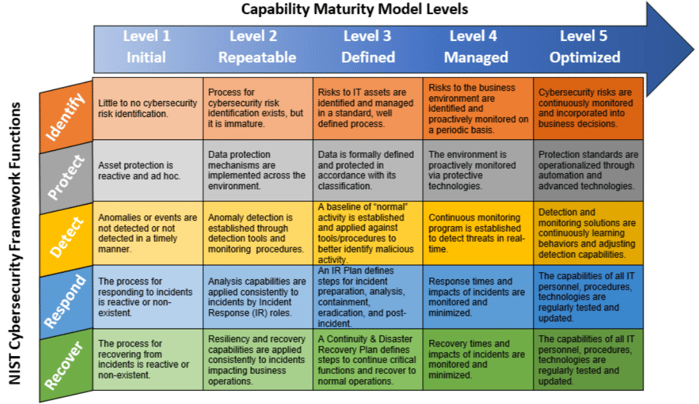
A security maturity model is a set of characteristics or indicators that represent capability and progression within an organization’s security program.
The Cyber Security Framework Implementation Tiers are not intended to be maturity levels. The Tiers are intended to provide guidance to organizations on the interactions and coordination between cybersecurity risk management and operational risk management. The key tenet of the Tiers is to allow organizations to take stock of their current activities from an organization wide point of view and determine if the current integration of cybersecurity risk management practices is sufficient given their mission, regulatory requirements, and risk appetite. Progression to higher Tiers is encouraged when such a change would reduce cybersecurity risk and would be cost-effective.
[Cybersecurity Architecture]
- Risk Management
- TOGAF Knowledges Collection
- Governance Overview
- Cybersecurity Architecture Practice
- Cybersecurity Architecture Knowledge Overview
- Architecture Category
NIST CSF Tiers
The NIST CSF Tiers represent how well an organization views cybersecurity risk and the processes in place to mitigate risks. This helps provide organizations a benchmark on how their current operations.
- Tier 1 – Partial: Organizational cybersecurity risk is not formalized and managed in an ad hoc and sometimes reactive manner. There is also limited awareness of cybersecurity risk management.
- Risk Management Processes: At Tier 1 organizations, cybersecurity risk management is typically performed in an ad hoc/reactive manner. Furthermore, cybersecurity activities are typically performed with little to no prioritization based on the degree of risk that those activities address.
- Integrated Risk Management Program: The lack of processes associated with cyber risk management makes the communication and management of that risk difficult for these organizations. As a result, the organization works with cybersecurity risk management on a case-by-case basis because of the lack of consistent information.
- External Participation: These organizations lack a greater understanding of their role in the greater business ecosystem - its position in the supply chain, dependents, and dependencies. Without an understanding of where it sits in the ecosystem, a Tier 1 organization does not share information with third-parties effectively (if at all) and is generally unaware of the supply chain risks that it accepts and passes on to other members of the ecosystem.
- Tier 2 – Risk-Informed: There may not be an organizational-wide policy for security risk management. Management handles cybersecurity risk management based on risks as they happen.
- Risk Management Processes: Risk management practices, while approved by management, are typically not established as organizational-wide policies within Tier 2 organizations. While risk management practices are not standard, they do directly inform the prioritization of cybersecurity activities alongside organizational risk objectives, the threat environment, and business requirements.
- Integrated Risk Management Program: The awareness of cybersecurity risk exists at the organizational level, but it is not standardized organization-wide, and the information around cybersecurity is only shared informally. While some consideration for cybersecurity exists in organizational objectives, it is not standard. A cyber risk assessment may occur, but it is not standard and periodically repeated.
- External Participation: Tier 2 organizations understand either their role in the ecosystem in terms of dependencies or dependents, but not both. Organizations like this typically receive information but do not share it out, and while they’re aware of the risk associated with their supply chain, they do not typically act on it.
- Tier 3 – Repeatable: A formal organizational risk management process is followed by a defined security policy.
- Risk Management Processes: Tier 3 organizations have formally approved risk management practices, and are expressed as policy. These practices are regularly updated based on changes in business requirements and changing threat landscape.
- Integrated Risk Management Program: In this tier, there is a higher-level organization-wide approach to managing cybersecurity risk. Risk-informed policies, processes, and procedures are defined, implemented, and reviewed. There are methods in place to consistently respond effectively to changes in risk, and personnel possess the knowledge and skills to perform their roles. Senior cybersecurity, board of directors, and business-side executives communicate regularly regarding cybersecurity events and risk.
- External Participation: Tier 3 organizations understand their role in the ecosystems and contribute to the broader understanding of risks. They collaborate with other entities regularly that coincide with internally generated information that is shared with other entities. These organizations are aware of the risks associated with their supply chains and act formally on those risks, including implementing written agreements to communicate baseline requirements, governance structures, and policy implementation and monitoring.
- Tier 4 – Adaptable: An organization at this stage will adapt its cybersecurity policies based on lessons learned and analytics-driven to provide insights and best practices. The organization is constantly learning from the security events that do occur in the organization and will share that information with a larger network.
- Risk Management Processes: These organizations adapt their cybersecurity practices based on previous and current cybersecurity activities, including lessons learned and predictive factors. They implement a process of continuous improvement - including incorporating advanced cybersecurity technologies and practices, actively adapting to a changing threat and technology landscape.
- Integrated Risk Management Program: Building on Tier 3, Tier 4 organizations clearly understand the link between organizational objectives and cybersecurity risk. Senior executives monitor cybersecurity risk in the same context as financial risk and other organizational risks. These organizations base budgeting decisions on an understanding of the current and potential risk environment. Cybersecurity risk is integrated into the organizational culture and evolves from an awareness of previous activities and continuous awareness.
- External Participation: Integrating itself further into the ecosystem beyond Tier 3, Tier 4 organizations receive, generate, and contribute to the understanding of the ecosystem around risk. Further integration of sharing information to internal and external stakeholders, the organization uses real-time information to understand and regularly act on supply chain risks. They also have a formalized process integrated into their documentation wit their dependencies and dependents.
the NIST CSF Implementation Tiers are not meant to be seen as a maturity model. Instead, look at these as benchmarking tools and clear directions to improve how your organization approaches cybersecurity.
You can use the NIST CSF to benchmark your current security posture. Going through each category and subcategories in the core Function can help you determine where you stand on the NIST CSF Tier scale.
Define Tier Levels
How to quickly improve your organization's Tiers level
Additionally, you may want to start implementing password policies such as requiring employees to use different passwords at work and home. Consider requiring all employees to use a password manager. Businesses in Tier 1 and 2 also typically offer annual or quarterly security awareness training. Employees are often the first line of defense, sometimes called the “human firewall.”
Small-to-medium businesses often use the Center for Internet Security (CIS) Top 20 Critical Security Controls as guidance or a checklist to help advance through the tiers. One important first step is to inventory all hardware and software in an environment. Anything with an IP address should be scanned and catalogued regularly. Scanning your environment can be done with many free tools found online.
If your budget permits and you want a more thorough scan, you can hire a third-party data security team to help identify many of the unknown devices or IP addresses in your business. These scanning experts specialize in very quickly auditing devices, apps, software, IoT, and cloud assets while providing your business with a prioritized list of action items that fits your IT staff capabilities and budget.
Once your inventory and auditing are complete, you can move into other areas of focus, such as securing configurations for network devices, ensuring your firewall is properly secured, hardening external devices, or controlling the use of administrative and user privileges. Maturing your cybersecurity posture can also include basic log collection to help you recover from ransomware. At a minimum, Tier 1 and 2 businesses will ensure that remote access and firewall activity is logged. They will also examine their data backup and recovery capabilities while developing an incident response plan.
There are many options to help organizations move from into Tier 1 or 2 with little investment of money or time. For example, low-cost security automation can help identify risks and vulnerabilities.
Maturity Models
Maturity Model History
How to use a cybersecurity maturity model
From: https://www.hhs.gov/sites/default/files/cybersecurity-maturity-model.pdf
Notable Cybersecurity Maturity Models:
C2M2, CSF, DOD CMMC
Comparison table for C2M2, CSF, DOD CMMC
COBIT 2019 Maturity Levels
The maturity model provided by the COBIT Management Guidelines for the 34 COBIT IT processes is becoming an increasingly popular tool to manage the timeless issue of balancing risk and control in a cost-effective manner. Control Objectives for Information and related Technology (COBIT) is published by the IT Governance Institute (ITGI) and Information Systems Audit and Control Foundation (ISACF).
The COBIT Maturity Model is an IT governance tool used to measure how well developed the management processes are with respect to internal controls. The maturity model allows an organization to grade itself from nonexistent (0) to optimized (5). Such capability can be exploited by auditors to help management fulfill its IT governance responsibilities, i.e., exercise effective responsibility over the use of IT just like any other part of the business. A fundamental feature of the maturity model is that it allows an organization to measure as-is maturity levels, and define to-be maturity levels as well as gaps to fill.
As a result, an organization can discover practical improvements to the system of internal controls of IT. However, maturity levels are not a goal, but rather they are a means to evaluate the adequacy of the internal controls with respect to company business objectives.
Figure 1—Capability Level for Processes

Figure 2—Maturity Level for Focus Area
- Initial—Unpredictable process that is poorly controlled and reactive
- Managed—Process is planned, documented and monitored at the project level and often are reactive
- Defined—Proactive process meant for organizations
- Quantitively Managed—Measured and controlled process
- Optimizing—Focus is on continuous process and improvement
Reaching Level 5 doesn’t mean that an organization’s maturity has peaked, however. It means that they are constantly monitoring and evolving their processes to make them better.
Standardized Definitions of Maturity (People, Process, Technology)
Another evaluation diagram for Maturity Level around PPT (People, Process, Technology):
From: https://security-architect.com/how-to-assess-security-maturity-and-roadmap-improvements/
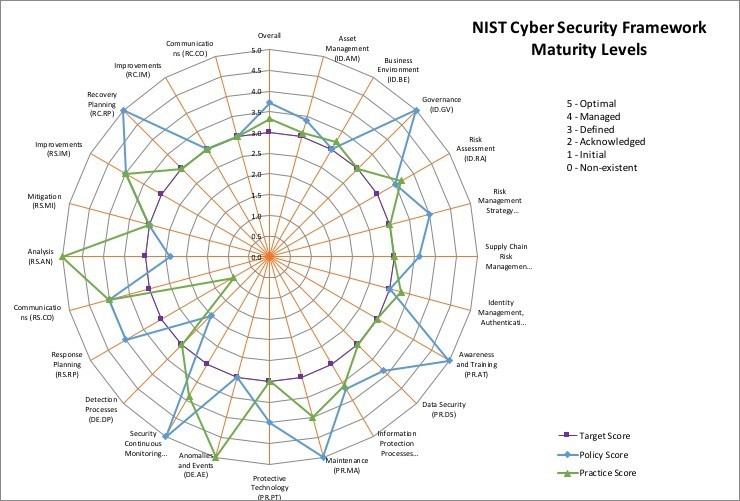
Maturity Level Evaluation Tool
1 NIST CSF Free Evaluation Tool:
Download page: https://johnmasserini.com/resources/downloads/
| Date | Name | Type | Description | Download Link | SHA256 Hash |
| 2022_02_28 | NIST CSF Maturity Tool 2.1 | XLS | Version 2.1. See the change log on the first tab. Download for the New Version of the NIST CSF Tool article. | NIST CSF Maturity Tool v2.1 | af372a22c8be59312995088dc83ca11595e491f56f01021fffb5b05d97e23a5e |
2 C2M2 - Cybersecurity Capability Maturity Model
C2M2, Version 2.1 aligns with recent strategic guidance to strengthen and improve the nation’s cybersecurity posture and capabilities and to reinforce the need for action towards systematic security and resilience. C2M2, Version 2.1 incorporates other enhancements to better align model domains and practices with internationally recognized cybersecurity standards and best practices, including the NIST Cybersecurity Framework Version 1.1 released in April 2018.
The C2M2 was developed by the U.S. Department of Energy for use by power and utility companies. However, any organization can use it to measure the maturity of their cybersecurity capabilities.
The Cybersecurity Capability Maturity Model (C2M2) can help organizations of all sectors, types, and sizes to evaluate and make improvements to their cybersecurity programs and strengthen their operational resilience.
Create Cybersecurity Program
Create Cybersecurity Program based on NIST CSF, improving Cybersecurity Program - Steps to gap remediation and improvement.
Note: Cyber Security: A Practical Application of NIST Cybersecurity Framework - https://www.youtube.com/watch?v=QAqSEI1ETEY
References
- BUILDING CYBERSECURITYCAPABILITY, MATURITY,RESILIENCE (CMMI Institute & ISACA)
- Free NIST CSF Maturity Tool
- NIST CSF Core Notes & Free NIST Maturity Tool
















No comments:
Post a Comment