 Sysinternals from Web Browser:
Sysinternals from Web Browser:Basic Sysmon Usage commands:
Installation:
sysmon -i -accepteula [options]
- Extracts binaries into %systemroot%
- Registers event log manifest
- Enables default configuration
Note: Once this command runs, the Sysmon service is installed, running, and logging to the Event log at Applications and Service Logs > Microsoft > Windows > Sysmon > Operational.
Viewing and updating configuration:
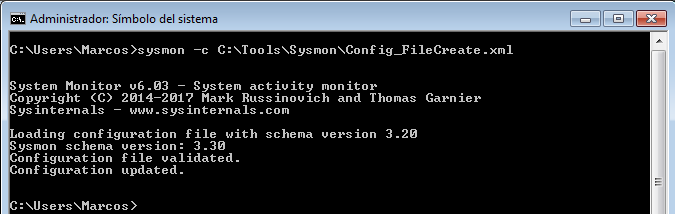
sysmon -c [options]
- Updates take effect immediately
- Options can be basic options or a configuration file
Register event manifest for viewing logs only:
sysmon -m
Uninstall:
sysmon -u
Help
Sysmon -h
sysmon -h config
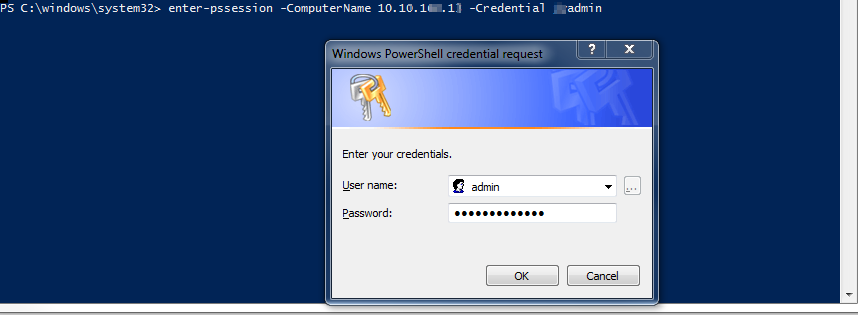
1. Get a Remote Sysmon Event
PS C:\windows\system32> enter-pssession -ComputerName testmachine1 -Credential admin1
[testmachine1]: PS C:\Users\admin1\Documents> cd ..
[testmachine1]: PS C:\Users\admin1> cd ..
[testmachine1]: PS C:\Users> cd ..
[testmachine1]: PS C:\> dir
Directory: C:\
Mode LastWriteTime Length Name
---- ------------- ------ ----
d---- 17/09/2018 4:31 PM 1e1e425df683e574801386fa411ca3
da--- 03/05/2018 1:32 PM Activexviewer
d---- 03/05/2018 1:31 PM Dell
d---- 03/05/2018 1:40 PM Desktop Authority
d---- 27/02/2018 11:27 AM Intel
d---- 13/07/2009 11:20 PM PerfLogs
d-r-- 20/09/2018 11:51 AM Program Files
d-r-- 18/09/2018 10:31 AM Program Files (x86)
d---- 18/09/2018 11:06 AM Temp
d-r-- 27/09/2018 9:40 AM Users
d---- 27/09/2018 9:46 AM Windows
-a--- 26/09/2018 2:02 PM 8922 SUService.log
[testmachine1]: PS C:\Users> Get-WinEvent -FilterHashtable @{logname="Microsoft-Windows-Sysmon/Operational";id=3;} | Where {
$_.message -like "*10.10.1.2*" -and $_.message -like "*DestinationPort: *"} | Select-Object -Property message -First 1
| Format-List
Message : Network connection detected:
UtcTime: 2018-09-27 14:36:22.092
ProcessGuid: {88333078-C9A4-5BAB-0000-0010EB030000}
ProcessId: 4
Image: System
User: NT AUTHORITY\SYSTEM
Protocol: tcp
Initiated: false
SourceIsIpv6: false
SourceIp: 10.10.160.13
SourceHostname: testmachine1.atest.com
SourcePort: 5985
SourcePortName:
DestinationIsIpv6: false
DestinationIp: 10.10.1.2
DestinationHostname: anothertest.atest.com
DestinationPort: 56588
DestinationPortName:
[kl]: PS C:\Users>
2. Update Sysmon with config file
You also have the option of using a configuration file, which can further nail down what you would like to log.
C:\ISOScripting>Sysmon64.exe -h config System Monitor v7.02 - System activity monitor Copyright (C) 2014-2018 Mark Russinovich and Thomas Garnier Sysinternals - www.sysinternals.com Configuration usage (current schema is version: 4.00): Configuration files can be specified after the -i (installation) or -c (configuration) switches. They make it easier to deploy a preset configuration and to filter captured events. A simple configuration xml file looks like this: <Sysmon schemaversion="4.00"> <!-- Capture all hashes --> <HashAlgorithms>*</HashAlgorithms> <EventFiltering> <!-- Log all drivers except if the signature --> <!-- contains Microsoft or Windows --> <DriverLoad onmatch="exclude"> <Signature condition="contains">microsoft</Signature> <Signature condition="contains">windows</Signature> </DriverLoad> <!-- Do not log process termination --> <ProcessTerminate onmatch="include" /> <!-- Log network connection if the destination port equal 443 --> <!-- or 80, and process isn't InternetExplorer --> <NetworkConnect onmatch="include"> <DestinationPort>443</DestinationPort> <DestinationPort>80</DestinationPort> </NetworkConnect> <NetworkConnect onmatch="exclude"> <Image condition="end with">iexplore.exe</Image> </NetworkConnect> </EventFiltering> </Sysmon> The configuration file contains a schemaversion attribute on the Sysmon tag.This version is independent from the Sysmon binary version and allows the parsing of older configuration files. The current schema version is shown in the sample configuration. Configuration entries are directly under the Sysmon tag and filters are under the EventFiltering tag. Configuration entries are similar to command line switches, and have their configuration entry described in the Sysmon usage output. Parameters are optional based on the tag. If a command line switch also enables an event, it needs to be configured though its filter tag. Event filtering allows you to filter generated events. In many cases events can be noisy and gathering everything is not possible. For example, you might be interested about network connections only for a certain process, but not all of them. You can filter the output on the host reducing the data to collect. Each event has its own filter tag under EventFiltering: Id Tag Event 1 ProcessCreate Process Create 2 FileCreateTime File creation time changed 3 NetworkConnect Network connection detected 5 ProcessTerminate Process terminated 6 DriverLoad Driver loaded 7 ImageLoad Image loaded 8 CreateRemoteThread CreateRemoteThread detected 9 RawAccessRead RawAccessRead detected 10 ProcessAccess Process accessed 11 FileCreate File created 12 RegistryEvent Registry object added or deleted 13 RegistryEvent Registry value set 14 RegistryEvent Registry object renamed 15 FileCreateStreamHash File stream created 17 PipeEvent Pipe Created 18 PipeEvent Pipe Connected 19 WmiEvent WmiEventFilter activity detected 20 WmiEvent WmiEventConsumer activity detected 21 WmiEvent WmiEventConsumerToFilter activity detected You can also find these tags in the event viewer on the task name. The onmatch filter is applied if events are matched. It can be changed with the "onmatch" attribute for the filter tag. If the value is 'include', it means only matched events are included. If it is set to 'exclude', the event will be included except if a rule match. Each tag under the filter tag is a fieldname from the event. Each field entry is tested against generated events, if one match the rule is applied and the rest is ignored. For example this rule will discard any process event where the IntegrityLevel is medium: <ProcessCreate onmatch="exclude"> <IntegrityLevel>Medium</IntegrityLevel> </ProcessCreate> Field entries can use other conditions to match the value. The conditions areas follow (all are case insensitive): is Default, values are equals. is not Values are different. contains The field contains this value. excludes The field does not contain this value. begin with The field begins with this value. end with The field ends with this value. less than Lexicographical comparison is less than zero. more than Lexicographical comparison is more than zero. image Match an image path (full path or only image name). For example: lsass.exe will match c:\windows\system32\lsass.exe. You can use a different condition by specifying it as an attribute. This excludes network activity from processes with iexplore.exe in their path: <NetworkConnect onmatch="exclude"> <Image condition="contains">iexplore.exe</Image> </NetworkConnect> You can use both include and exclude rules for the same tag, where exclude rules override include rules. Within a rule, filter conditions have OR behavior, In the sample configuration shown earlier, the networking filter uses both an include and exclude rule to capture activity to port 80 and 443 by all processes except those that have iexplore.exe in their name. C:\ISOScripting>
Template for a super simple config.xml
<Sysmon schemaversion="4.00">
<HashAlgorithms>md5,sha256</HashAlgorithms> <!-- Both MD5 and SHA256 are the industry-standard algorithms for identifying files -->
<CheckRevocation/> <!-- Check loaded drivers, log if their code-signing certificate has been revoked, in case malware stole one to sign a kernel driver -->
<EventFiltering>
<!--SYSMON EVENT ID 1 : PROCESS CREATION [ProcessCreate]-->
<ProcessCreate onmatch="exclude">
</ProcessCreate>
<!--SYSMON EVENT ID 2 : FILE CREATION TIME RETROACTIVELY CHANGED IN THE FILESYSTEM [FileCreateTime]-->
<FileCreateTime onmatch="include">
</FileCreateTime>
<FileCreateTime onmatch="exclude">
</FileCreateTime>
<!--SYSMON EVENT ID 3 : NETWORK CONNECTION INITIATED [NetworkConnect]-->
<NetworkConnect onmatch="include">
<!--Destination : Suspicious-->
<DestinationIp condition="is">198.54.117.200</DestinationIp> <!--Specific rule-->
<DestinationIp condition="is">8.8.8.8</DestinationIp> <!--test verification rule-->
</NetworkConnect>
<NetworkConnect onmatch="exclude">
</NetworkConnect>
</EventFiltering>
</Sysmon>
A little bit more complicate one:
<Sysmon schemaversion="4.00">
<HashAlgorithms>SHA256</HashAlgorithms>
<EventFiltering>
<!-- Event ID 1: ProcessCreate -->
<ProcessCreate onmatch="exclude">
<IntegrityLevel>System</IntegrityLevel>
<!-- Google Chrome -->
<Image condition="Is">C:\Program Files (x86)\Google\Chrome\Application\chrome.exe</Image>
<Image condition="contains">Chrome\Application\chrome.exe</Image>
<!-- Other Chatty applications -->
<Image condition="contains">C:\Program Files (x86)\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe</Image>
<Image condition="contains">C:\Windows\SysWOW64\Macromed\Flash\FlashPlayerUpdateService.exe</Image>
<ParentImage condition="contains">C:\Program Files (x86)\Google\Update\GoogleUpdate.exe</ParentImage>
<CommandLine condition="contains">C:\Windows\system32\wbem\wmiprvse.exe -secured -Embedding</CommandLine>
<ParentCommandLine condition="contains">C:\Windows\system32\SearchIndexer.exe /Embedding</ParentCommandLine>
<ParentCommandLine condition="contains">C:\Windows\system32\SearchIndexer.exe /Embedding</ParentCommandLine>
</ProcessCreate>
<!-- Event ID: 2 FileCreateTime -->
<FileCreateTime onmatch="exclude">
<Image condition="end with">chrome.exe</Image>
<Image condition="end with">firefox.exe</Image>
<Image condition="end with">outlook.exe</Image>
<Image condition="end with">iexplore.exe</Image>
<Image condition="contains">C:\Windows\system32\msiexec.exe</Image>
<Image condition="contains">C:\Windows\syswow64\MsiExec.exe</Image>
</FileCreateTime>
<!-- Event ID 3: Network Connection -->
<NetworkConnect onmatch="exclude">
<DestinationIp condition="contains">169.254</DestinationIp>
<DestinationIp condition="contains">255.255.</DestinationIp>
<DestinationIp condition="contains">239.255.</DestinationIp>
<DestinationIp condition="begin with">10.</DestinationIp>
<DestinationIp condition="contains">127.0.</DestinationIp>
<DestinationIp condition="contains">0:0:0</DestinationIp>
<!--<Image condition="end with">iexplore.exe</Image> -->
<!--<Image condition="end with">chrome.exe</Image> -->
<Image condition="end with">excel.exe</Image>
<Image condition="end with">winword.exe</Image>
<Image condition="end with">lms.exe</Image>
<Image condition="end with">onenote.exe</Image>
<Image condition="contains">C:\Program Files\Mozilla Firefox\firefox.exe"</Image>
<Image condition="contains">C:\Program Files\Mozilla Firefox\firefox.exe</Image>
<DestinationPortName condition="end with">dhcpv6-client</DestinationPortName>
<DestinationPortName condition="end with">epmap</DestinationPortName>
<DestinationPortName condition="end with">llmnr</DestinationPortName>
<DestinationPortName condition="end with">netbios-dgm</DestinationPortName>
<DestinationPortName condition="end with">netbios-ns</DestinationPortName>
<DestinationPortName condition="end with">netbios-ns</DestinationPortName>
<SourcePortName condition="end with">llmnr</SourcePortName>
<SourcePortName condition="end with">epmap</SourcePortName>
<SourcePortName condition="end with">ws-discovery</SourcePortName>
<SourcePortName condition="end with">ssdp</SourcePortName>
</NetworkConnect>
<!-- Event ID: 5 Process Terminate. We're not logging process termination -->
<ProcessTerminate onmatch="include"/>
<!-- Event ID: 6 Driver Loaded: Log all drivers except if signature Contains Microsoft or Windows-->
<DriverLoad onmatch="exclude">
<Signature condition="contains">microsoft</Signature>
<Signature condition="contains">windows</Signature>
</DriverLoad>
<!-- Event ID: 8 Log CreateRemoteThread -->
<CreateRemoteThread onmatch="include">
<TargetImage condition="image">lsass.exe</TargetImage>
<TargetImage condition="image">winlogon.exe</TargetImage>
</CreateRemoteThread >
<!-- Event ID: 9 RawAccessRead -->
<RawAccessRead onmatch="exclude">
<Image>C:\Windows\System32\wbem\WmiPrvSE.exe</Image>
<Image>C:\Windows\System32\svchost.exe</Image>
</RawAccessRead>
<!-- Event ID: 11 FileCreate -->
<FileCreate onmatch="include">
<TargetFilename condition="end with">.exe</TargetFilename>
<TargetFilename condition="end with">.pdf</TargetFilename>
<TargetFilename condition="end with">.vbs</TargetFilename>
<TargetFilename condition="end with">.doc</TargetFilename>
<TargetFilename condition="end with">.hta</TargetFilename>
<TargetFilename condition="end with">.xls</TargetFilename>
</FileCreate>
<!-- Event ID: 12 Certain registry keys (AutoStart, Services,Debuggers) -->
<RegistryEvent onmatch="include">
<TargetObject condition="contains">Windows\CurrentVersion\Run</TargetObject>
<TargetObject condition="contains">Windows\CurrentVersion\Image File Execution Options</TargetObject>
<TargetObject condition="contains">CurrentControlSet\Services</TargetObject>
<TargetObject condition="contains">Microsoft\Windows NT\CurrentVersion\Winlogon</TargetObject>
<TargetObject condition="contains">Microsoft\Windows\CurrentVersion\Policies\Explorer</TargetObject>
<TargetObject condition="contains">Microsoft\Windows\CurrentVersion\RunOnce</TargetObject>
<TargetObject condition="contains">System\CurrentControlSet\Services\Tcpip\parameters</TargetObject>
</RegistryEvent>
<!-- Event ID: 15 FileCreateStreamHash Events -->
<FileCreateStreamHash onmatch="exclude">
<TargetFilename condition="end with">.directory</TargetFilename>
<TargetFilename condition="end with">.sxx</TargetFilename>
<TargetFilename condition="end with">.partial</TargetFilename>
</FileCreateStreamHash>
</EventFiltering>
</Sysmon>
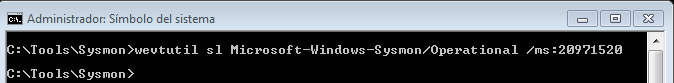
3. Change Sysmon Event Log Size
Change sysmon event log file size to 20M with wevtutil command:
wevtutil s1 Microsoft-Windows-Sysmon/Operational /ms:20971520
4. Third party tools: Sysmon View and Sysmon Shell
Sysmon View 1.4
Sysmon Shell 1.1
5. Deploy Sysmon in the domain environment
There is a script from "Deploying Sysmon through Group Policy (GPO)" and the process.
copy /z /y "\\domain.com\apps\config.xml" "C:\windows\"
sysmon -c c:\windows\config.xml
sc query "Sysmon" | Find "RUNNING"
If "%ERRORLEVEL%" EQU "1" (
goto startsysmon
)
:startsysmon
net start Sysmon
If "%ERRORLEVEL%" EQU "1" (
goto installsysmon
)
:installsysmon
"\\domain.com\apps\sysmon.exe" /accepteula -i c:\windows\config.xml
Right click your domain OU and
- Create GPO in this domain, and link it here
- Provide a name (Sysmon Deployment) , hit OK
- Right click your newly created GPO Sysmon Deployment and select Edit
- Navigate to Computer configuration > Policies > Windows Settings > Scripts > Startup
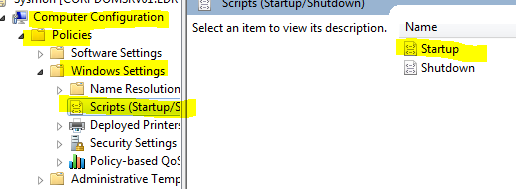
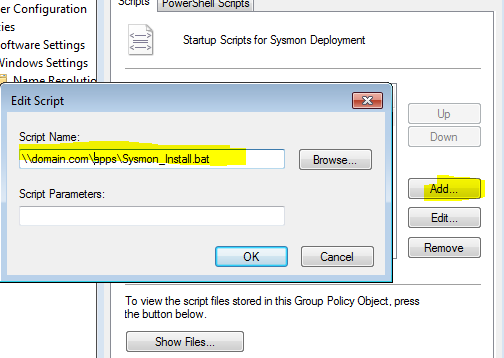
- Click on Startup and Add and browse to your script location \\domain.com\apps\Sysmon_Install.bat and finalize with OK
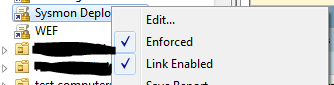
- Right click your newly created GPO and ensure that it’s enabled and enforced (if necessary)
References:
- Tracing Malicious Activity On Windows With Sysmon
- Sysmon-config - https://github.com/SwiftOnSecurity
- @SwiftOnSecurity’s amazingly well-documented Sysmon config
- Any Sysmon-related blog post from Carlos Perez
- Sysinternals Sysmon Unleashed
- Sysinternals Sysmon Suspicious Activity Guide
- Sysmon Configuration Repository - https://github.com/olafhartong/sysmon-modular
- Sysmon: how to set up, update and use?







No comments:
Post a Comment