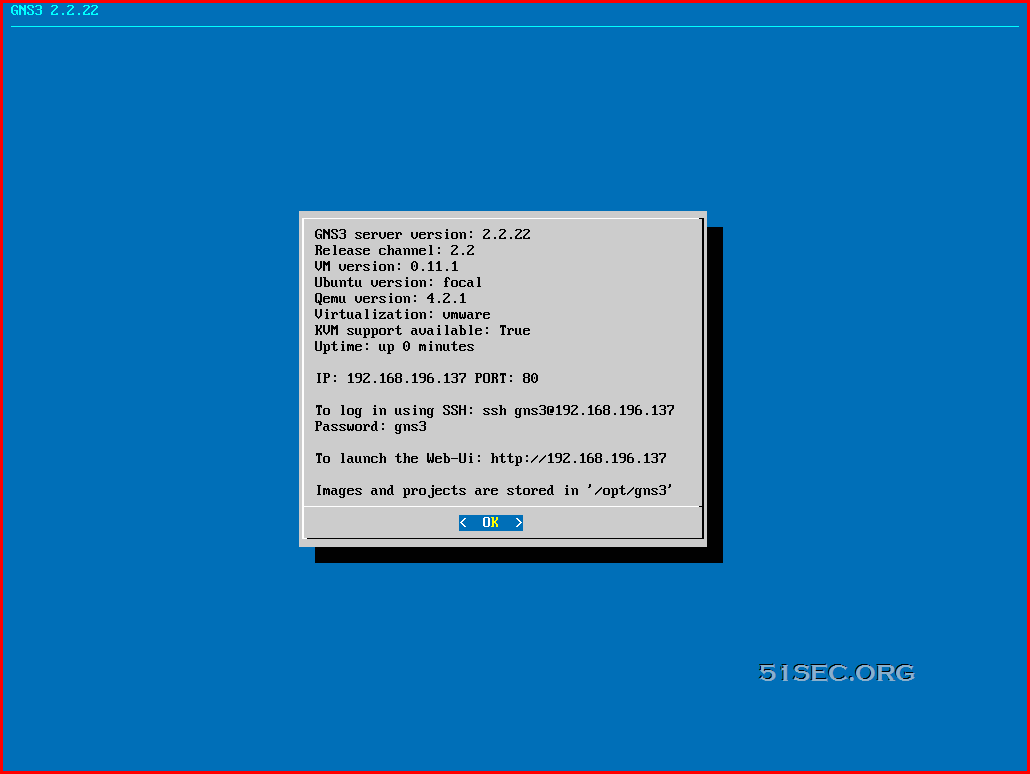
Smallest Firewall / Router VM (FreeSCO) For Your Home Lab (Image Size 1.4MB & Only Need RAM 16MB)
Netsec
12/03/2023
2 Comments
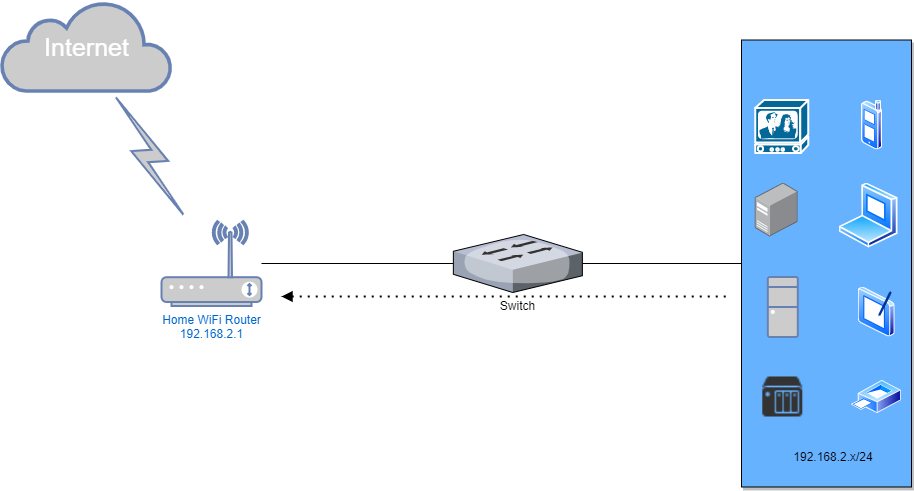
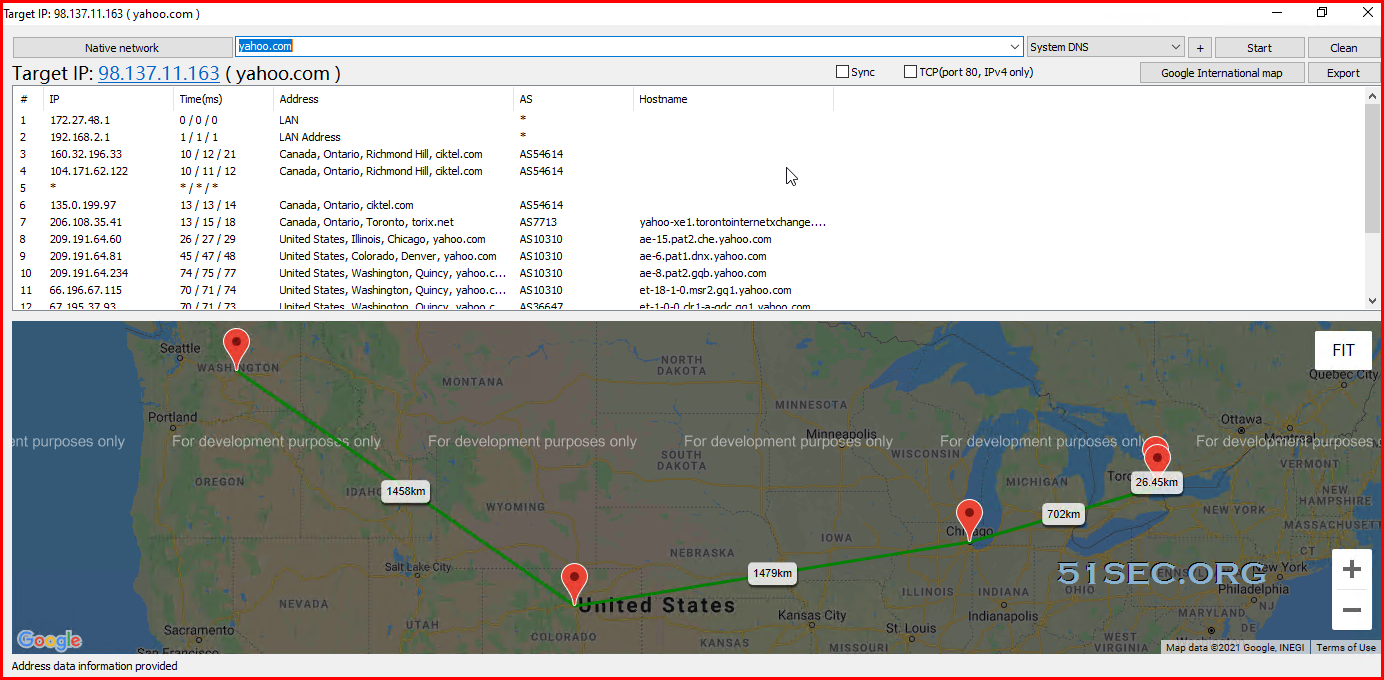
In my home lab virtual environment, VMware ESXi and Workstation used to host most of my testing virtual machines. To get those VMs working t...
Read More

![[Free VPS] EUServ IPv6-only Machine access to and from IPv4 World](https://i.ytimg.com/vi/hVnWhlxliIg/hqdefault.jpg)