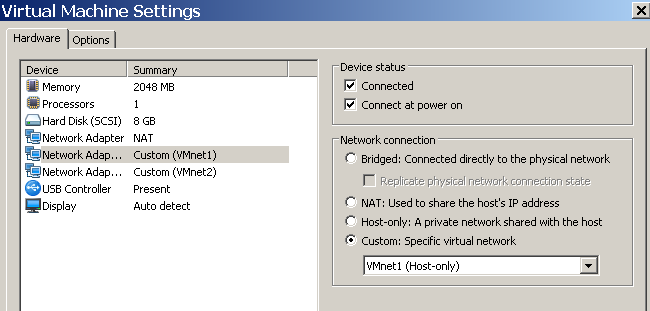
Connect VMs Together from VMWare Workstation & Hypwe-V Running in Same Host
Netsec
11/20/2022
0 Comments
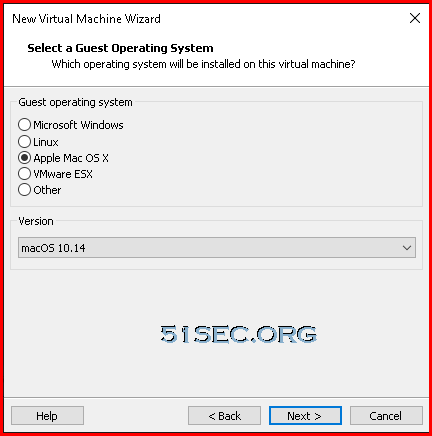
In my lab environment, I am havng a Windows host which enabled Hyper-V, also installed VMWare workstation Pro. It was very confusion for me ...
Read More