IT vs Information Security vs Cyber Security vs Business Continuity vs Risk Management
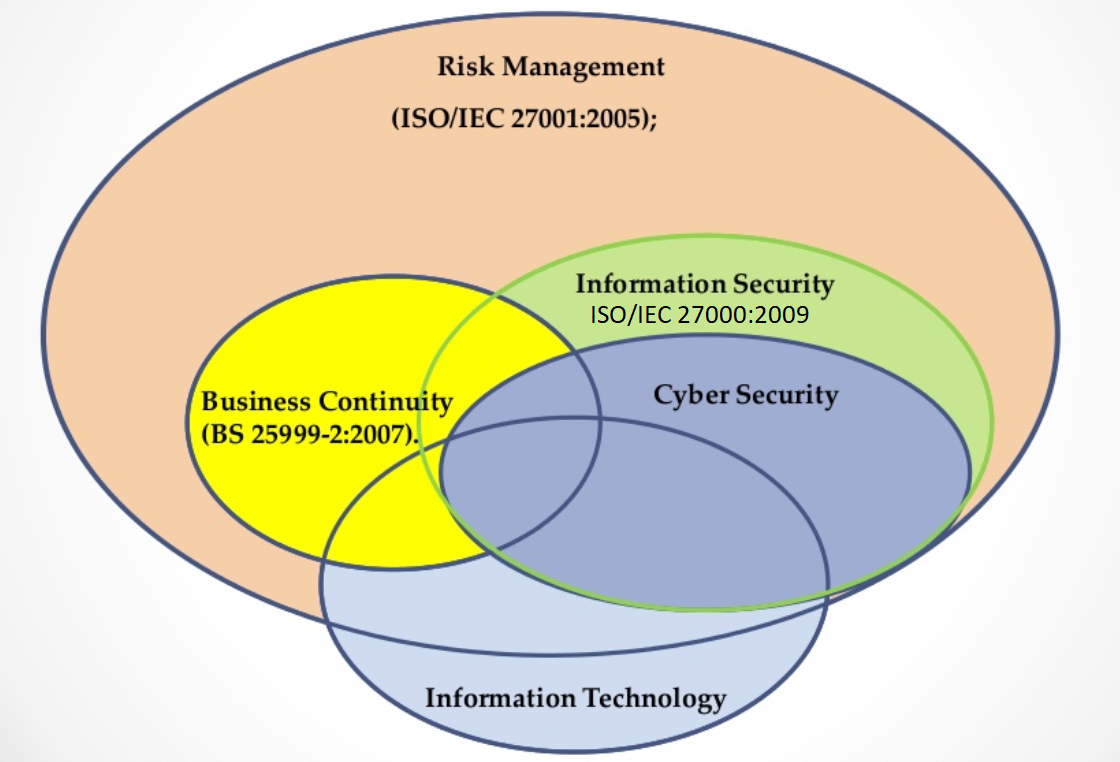 |
| IT vs Information Security vs Cyber Security vs Business Continuity vs Risk Management From: 9 steps to Cyber Security |
Feneric Enterprise Security Architecture System Diagram:
======================================================================
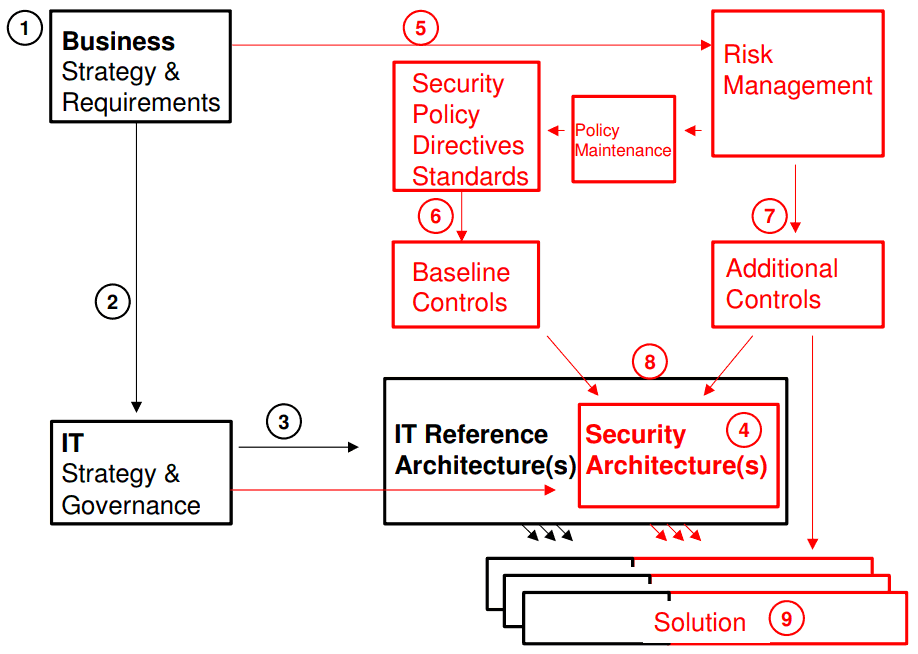
Following diagram is from
Information Security Society Switzerland's paper "What is Security Architecture"
Relationships & Dependencies between security architecture and relevand IT architecture:
1. Designing a security architecture should be a response to Business strategy and requirements.
2. The IT Strategy should be a response to the Business strategy and requirements.
3. The IT Reference Architecture(s) should be a response to the IT Strategy and Governance. The reference architecture will usually address multiple platforms.
4. The Reference Security Architecture(s) is part of the IT Architecture even if it is published as a separate document.
5. IT Security Risk Management, process and criteria. Are derived from the Business strategy and requirements.
6. A set of Baseline Controls is generated based on the Security Policy, Directives, Standards etc. By
Baseline Controls we understand mandatory minimum standards for the organisation. Input comes from the legal/regulatory environment, Benchmarking and published security “good practice” etc. see section 5 below.
7. Additional controls are derived from the Risk management process.
8. The security Architecture is the embodiment of the baseline and the additional security controls. It can also be defined to include the policies, directives, standards and the risk management process.
9. Some organisations use the term solution architecture to refer to the specific implementations derived from the reference architecture.
=============================================================
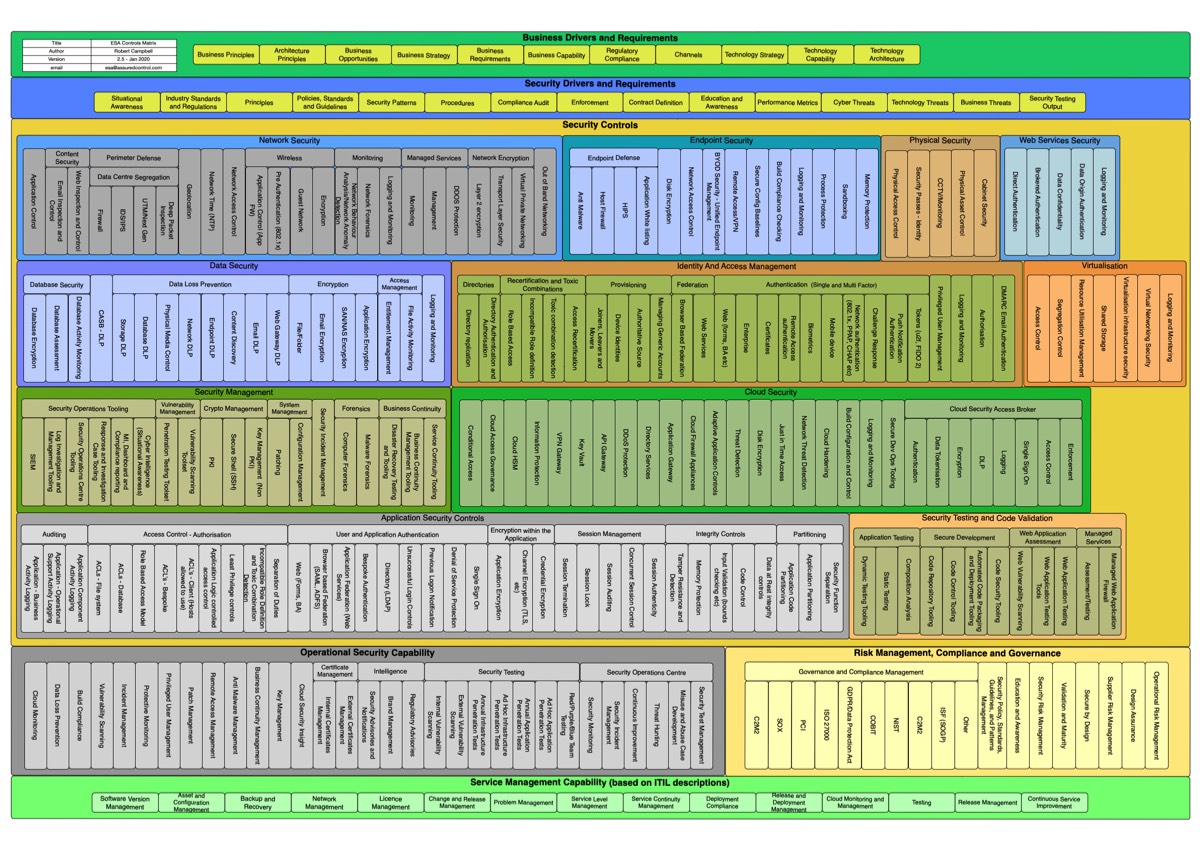
Enterprise Security Architecture - Security Controls Matrix.
- from Rob Campbell's website.
=============================================================
Security Layers - Protecting data in the modern age
- Physical layer:Fence, lobby, security guards, physical locks, badge readers, monitoring, vent & air conditioning, physical safes
- Perimeter Layer:Firewalls and NGFW, VPN, Reverse Proxies / Forward Proxies, IDS, SSO, MFA
- Network Layer: IPS, Email Security, Window Communication Control, WAD, Data acquisition network (DAN/SIEM), NAC & Logical Access Conrols, NTP, Wireless Network Security, Password Mgmt (Vaults), SOC, DLP, ATP
- Host Layer: Host based FWs, Anti Virus/Malware, Vulnerabilities scanning & Patching, CMDB and asset mgmt, server access control, OS hardening guidlines, MDM, PAM, Device Encryption, DLP
- Application Layer: SSL certs (data in flight), Role Base Access Control (RBAC/ABAC), Application Code review, Key mgmt systems, Sourcecode mgmt security
- Data Layer: Data encryption, Data Loss Prevention (DLP), Distributed denial of service, data backup / recovery
- Compliance Layer - Policy, Procedures, & Awareness
- Governance, Risk and Compliance Tools
- Business continuity and disaster recovery
- Certifications: SOC2, ISO27001, Privacy Shield, GDPR
- Change management
- Identity management and Identity Governance
- Security Awareness Training
- Incident Management
- HR Backgroudd Checks
- ...etc
===========================================================
Zero Trust networks
- ScaleFT provides Zero Trust software which you can use to secure your internal servers and services.- BeyondCorp
5 Steps to create a zero trust network
1. Identify your toxic data sources
2. Map the transaction flows regarding toxic data
3. Architect a zero trust network based on the toxic data sources and the way it's used transitionally
4. Write your rules on your segmentation gateway based on expected behavior of the data (users and applications)
5. Monitor the network; inspect and log the traffic; update rules based on the intelligence you get from your security analytics systems
==============================================================
Data Classification Model:
| Information type | Data Classification | Confidentiality Impact | Integrity Impact | Availability Impact |
| Health Care Delivery Services | Confidential | HIGH | HIGH | HIGH |
| Health Care Administration | Confidential | HIGH | MID | MID |
| Inventory Control | Confidential | HIGH | MID | MID |
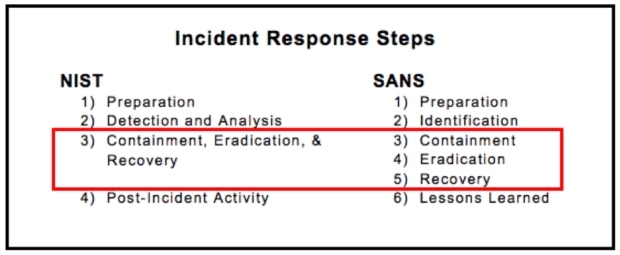
Incident Response Process
- Preparation
- Detection and Analysis
- Containment, Eradication, and Recovery
- Post-Incident Activity
NIST 800-61 Computer Security Incident Handling Guide.
2 The SANS Incident Response Process consists of six steps:
- Preparation
- Identification
- Containment
- Eradication
- Recovery
- Lessons Learned







No comments:
Post a Comment