3. Building a scalable AWS architecture (ELB, ASG, RDS)
- Understand NAT Instance vs NAT Gateway
- create your security groups
- create your EC2 keypari
- create your RDS SQL instance
- Bake your amazon machine image
- create your launch configuration
- create your auto-scaling group
- create your elastic load balancer
- test, break, fix, celebrate
You may need NAT for VPN. Two types NAT methods: NAT Instance and NAT Gateway
 |
| VPC: NAT Instance |
 |
| VPC: NAT Gateway |
It depends on how you want to use your NAT , either NAT instance or NAT gateway will work well. One thing to remember is when creating a NAT instance, you must disable source/destination check on the instance. NAT instance must be in a public subnet.
3.1 Create your security groups (Firewall)
The following diagram illustrates the layers of security provided by security groups and network ACLs. For example, traffic from an Internet gateway is routed to the appropriate subnet using the routes in the routing table. The rules of the network ACL associated with the subnet control which traffic is allowed to the subnet. The rules of the security group associated with an instance control which traffic is allowed to the instance.
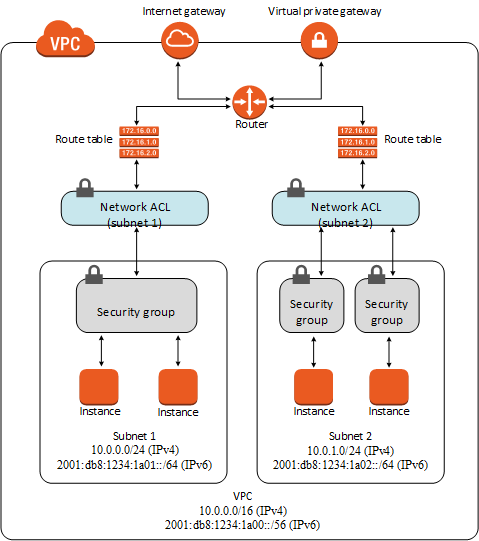 |
| Security Groups and Network ACLs |
The following AWS Doc table summarizes the basic differences between security groups and network ACLs.
| Security Group | Network ACL |
|---|---|
Operates at the instance level (first layer of defense)
|
Operates at the subnet level (second layer of defense)
|
Supports allow rules only
|
Supports allow rules and deny rules
|
Is stateful: Return traffic is automatically allowed, regardless of any rules
|
Is stateless: Return traffic must be explicitly allowed by rules
|
We evaluate all rules before deciding whether to allow traffic
|
We process rules in number order when deciding whether to allow traffic
|
Applies to an instance only if someone specifies the security group when launching the instance, or associates the security group with the instance later on
|
Automatically applies to all instances in the subnets it's associated with (backup layer of defense, so you don't have to rely on someone specifying the security group)
|
When you launch an instance in a VPC, you can assign up to five security groups to the instance. Security groups act at the instance level, not the subnet level. Therefore, each instance in a subnet in your VPC could be assigned to a different set of security groups. If you don't specify a particular group at launch time, the instance is automatically assigned to the default security group for the VPC.
Security groups are stateful — if you send a request from your instance, the response traffic for that request is allowed to flow in regardless of inbound security group rules. Responses to allowed inbound traffic are allowed to flow out, regardless of outbound rules.
3.2 Create your EC2 keypari
Amazon EC2 – The Amazon Elastic Compute Cloud (Amazon EC2) service enables you to launch virtual machine instances with a variety of operating systems. You can choose from existing Amazon Machine Images (AMIs) or import your own virtual machine images.
Access Amazon AWS EC2 Instances
3.3 Create your RDS SQL instance
3.4 Bake your amazon machine image
3.5 Create Auto Scaling Launch Configuration
3.6 Create your auto-scaling group
3.7 Create your elastic load balancer
Images / Snapshot
The major difference is between the type of service referred to. A snapshot is of an EBS volume where you are able to save state and reboot with the same data at a certain point in time.
An AMI is similar, but its for the EC2 instances themselves. You cannot take a snapshot of a non ebs backed instance, but you can create a AMI (system image) of one.
Generally I use EBS snapshots as backup solutions for a database volume and I use an AMI to save instance configuration
























No comments:
Post a Comment