Whether an organization is small with a relatively straightforward data environment or a larger entity with a data infrastructure that's far-reaching and complex, it's a good idea to identify and protect against security risks by establishing a security architecture program and the associated processes to implement it. A defined Security Architecture helps guide an enterprise’s investment strategy when it comes to all kinds of security initiatives.
Security Architecture Roadmaps provide a holistic view of a path to delivering on an well defined company business strategy and strategic plan. Roadmaps are strategy tailored, identifying strategy interdependencies between the elements required to deliver on the strategies. Roadmaps build on current state by providing a narrative describing strategic elements, including business goal and objective-aligned business, information, and security initiatives, often supplanted with time-based, layered, and aligned representations.
Related Posts:
Cybesecurity Strategic Planning
Cybesecurity Strategic Plan Cycle (around Mission):
- 1. Goals : Where does the oganization want to go?
- 2. Desired Outcomes: How will you get there?
- 3. Strategies: How do you measure success?
- 4. Measured Targets: How did we do?
- 5. Results : How can we improve?
Cybesecurity Strategic Plan Example:
Cybersecurity Planning:
- Strategic three year cycle and plan is made up of 3 tactical plans
- Tactical plans run one-year cycle
- Review of strategic plans begins 3 months before the current plan exires
- Management monitoring occurs quarterly
https://i.imgur.com/1GthZw4.png
Cybersecurity Operations
 |
| NIST : Five Functions |
Although voluntary and not intended to be an exhaustive checklist, the framework covers five critical areas of cybersecurity:
- Identify: looking at current data use and then evaluating and identifying risk;
- Protect: the elements that help protect a business;
- Detect: being aware of problems as they happen;
- Respond: the bases needing to be covered to make an adequate response to a problem;
- Recover: the steps needed to make an effective recovery of lost data.
All of these elements make up the ‘Core’ element of the framework, represented in a simplified form (without subcategories) here:
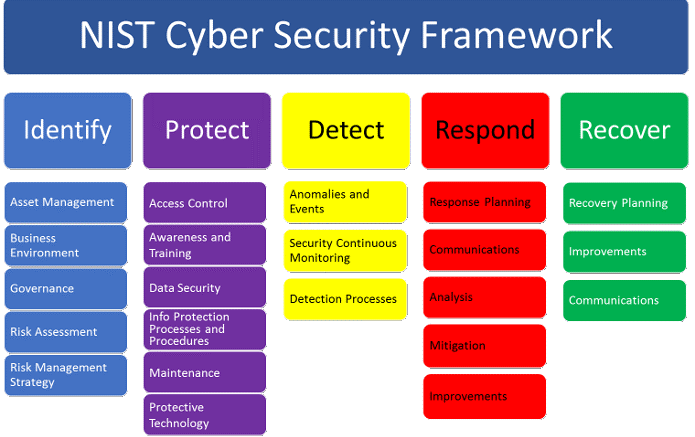
Identify ->Protect (Establish Enterprise Cybersecurity Management System)
Governance, Risk Management, Asset Management, Security Information & Event Management, Information Protection Practices, Vulnerability Management
->Detect (Identify, Investigate, Triage, Notify)
Continual Monitoring 24/365
->Respond (Observer-Orientate-Decide-Act, Notify, Contain, Preserve Evidence, Eradicate, Failover if required)
Playbook Activation, 15-minute acceptance, 2-hour resolution
->Recovery (Operations returned to normal)
Return to steady state, 2-hours
Return to regular operations
Post Incident review for conitunal improvement (Quality Management Feedback loop)
Project Chart
Project Definition- Project objectives
- Project benefits
- Project strategy
- Cirtical success factors
- Milestone
- Type of resource
- Skill set
- Effort
- Duration
- Target date
- Known constraints
- Beginning assumptions
- Risk assessment
Project Organizational Impacts
- Project Team
- Issue resolution team
- Departments impacted by the project
- Potential project priority
- User/Client responsibilities
SignOff
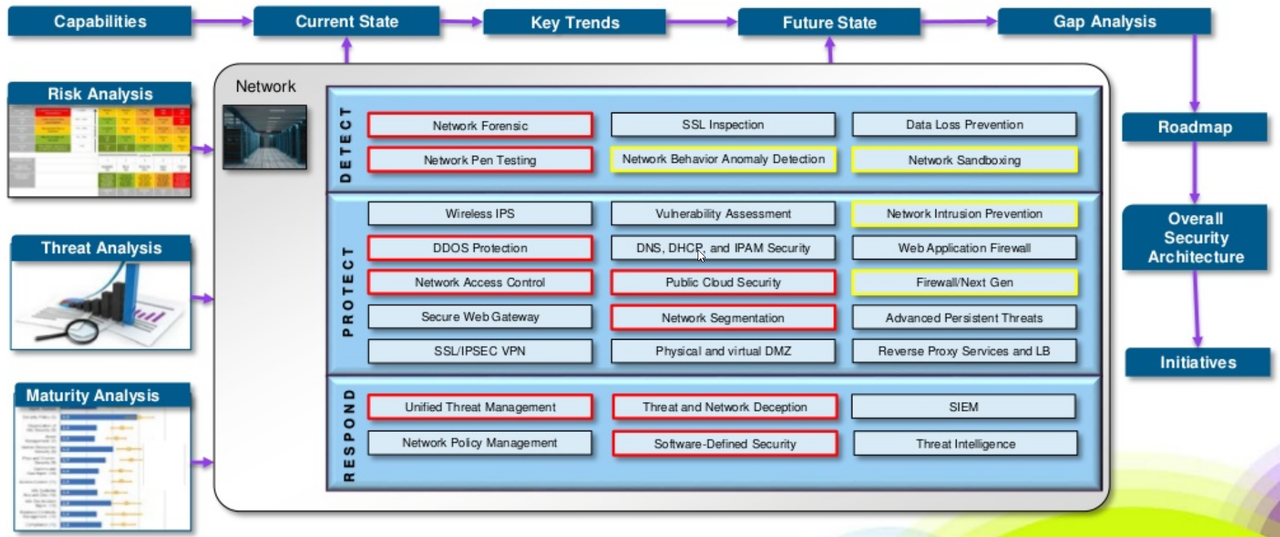
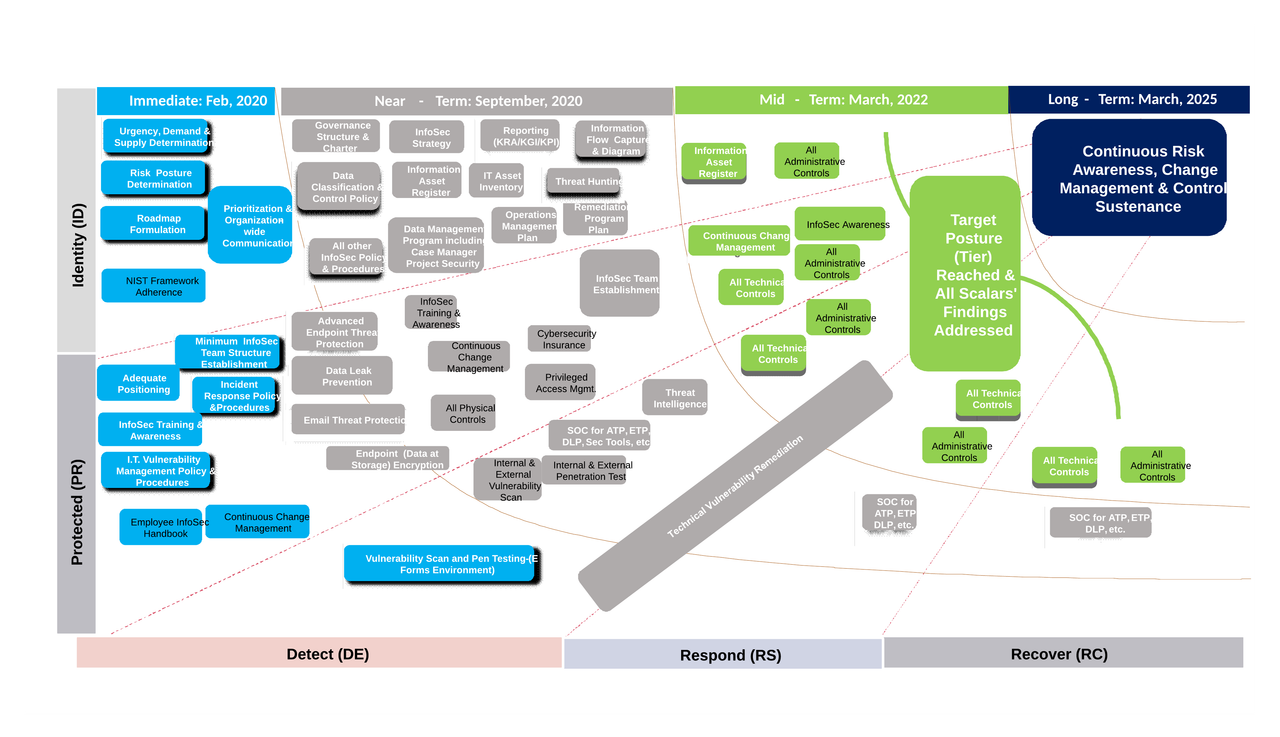
Security Architecture Roadmap Examples
1 Cybersecurity roadmap : Global healthcare security architecture(https://www.slideshare.net/cisoplatform7/cybersecurity-roadmap-global-healthcare-security-architecture)
2 Microsoft Cybersecurity Reference Architecture
The Microsoft Cybersecurity Reference Architecture describes Microsoft’s cybersecurity capabilities and how they integrate with existing security architectures and capabilities. We recently updated this diagram and wanted to share a little bit about the changes and the document itself to help you better utilize it.
(https://www.microsoft.com/security/blog/2018/06/06/cybersecurity-reference-architecture-security-for-a-hybrid-enterprise/)
3 Another example
Cyber Security Roadmap with Timeline
Tools
- IT Business Edge - Security Architecture Roadmap Tool
Download Link
References
- https://www.youtube.com/watch?v=4GTd5XFr2Rs - Cybersecurity annual planning and budgeting
- How to Plan for and Implement a Cybersecurity Strategy - https://www.youtube.com/watch?v=u-EQHbqWY60
- Cybersecurity reference architecture - https://learn.microsoft.com/en-us/security/ciso-workshop/ciso-workshop-module-1?view=o365-worldwide
- The Chief Information Security Officer (CISO) Workshop Training - https://learn.microsoft.com/en-us/security/ciso-workshop/the-ciso-workshop

















No comments:
Post a Comment