This post shows a basic configuration step for a HA setup of two Firepower 1010.
FDM is a web-based, simplified, on-device manager. Because it is simplified, some FTD features are not supported using FDM. You should use FDM if you are only managing a small number of devices and don't need a multi-device manager. Note Both FDM and CDO can discover the configuration on the firewall, so you can use FDM and CDO to manage the same firewall. FMC is not compatible with other managers
- Firepower Threat Defense(FTD)
- Firepower Device Manager (FDM)
- Firepower Management Center (FMC)
- Cisco Defense Orchestrator (CDO)
Diagram

FDM Configuration
- Login to the FDM UI using the URL https://management-ip e.g https://192.168.10.24
- Accept any certificate errors presented by the web browser
- Enter the username of admin and the password you set previous
Configuration Overview
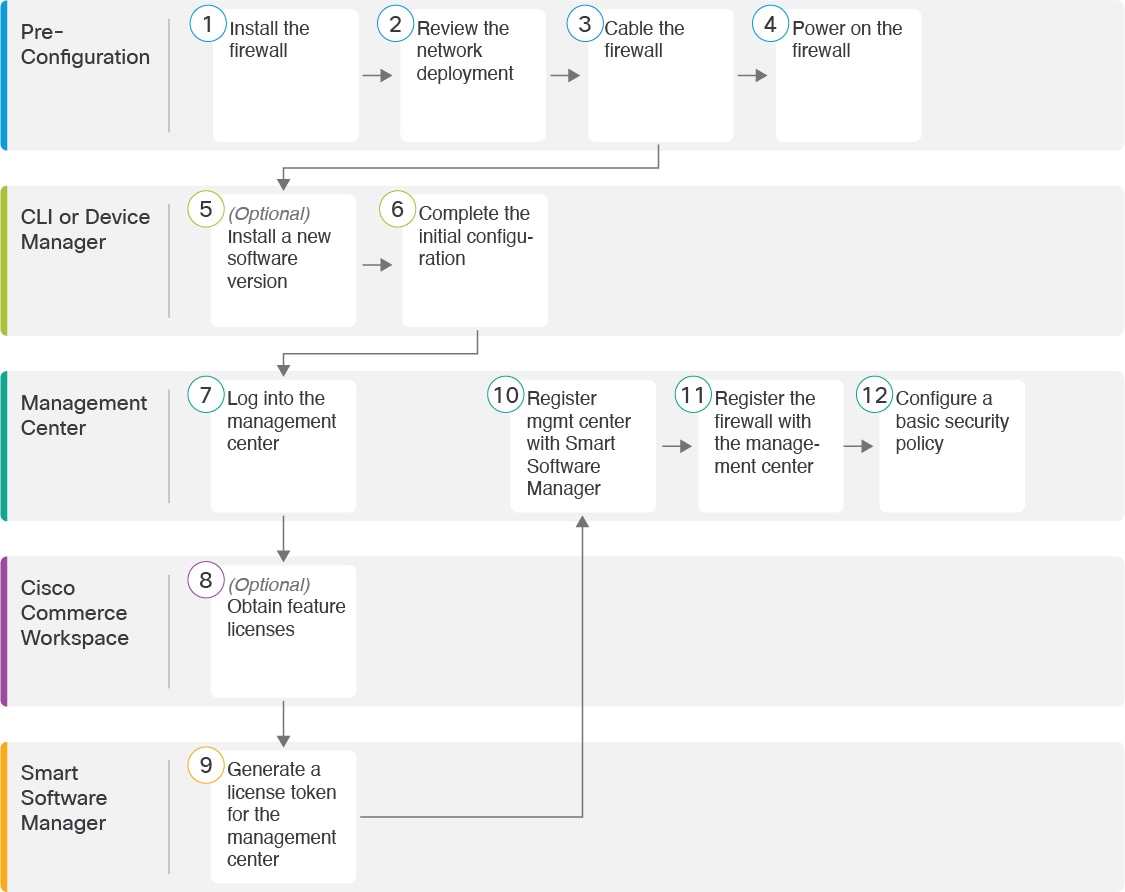
Pre-Configuration | Install the firewall. See the hardware installation guide. | |
Pre-Configuration | ||
Pre-Configuration | ||
Pre-Configuration | ||
CLI | ||
CLI or Device Manager | ||
Management Center | ||
Cisco Commerce Workspace | Obtain Licenses for the Management Center: Buy feature licenses. | |
Smart Software Manager | Obtain Licenses for the Management Center: Generate a license token for the management center. | |
Management Center | Obtain Licenses for the Management Center: Register the management center with the Smart Licensing server. | |
Management Center | ||
Management Center |
Basic Configuration
Cable Connections:
Interface configuration
Default Route configuration
Switchport Configuration
Vlan configuration
Trunk configuration
HA Configuration
Cable Connections
Failover link: - 172.16.40.1/30 172.16.40.1.2/30
Stateful link:172.16.50.1/30 172.16.50.2/30
Interface configuration:
References
- Cisco Firepower 1010 Getting Started Guide - Chapter: Threat Defense Deployment with the Management Center
- Cisco Firepower 1010 Initial Configuration via Setup Wizard
- Cisco Network Security Ordering Guide
- Home»AnyConnect»Cisco FTD Deploy AnyConnect (from FDM)
- Basic Interface Configuration for Firepower 1010Switch Ports










No comments:
Post a Comment