Layered Security & Defense In Depth

Layered security and defense in depth are two different concepts with a lot of overlap. They are not, however, competing concepts. A good layered security strategy is extremely important to protecting your information technology resources. A defense in depth approach to security widens the scope of your attention to security and encourages flexible policy that responds well to new conditions, helping ensure you are not blindsided by unexpected threats.
Related Posts:
- Canadian Cybersecurity and Privacy Framework
- [Cybersecurity Architecture] Policy / Standards / Procedures Framework with an Example
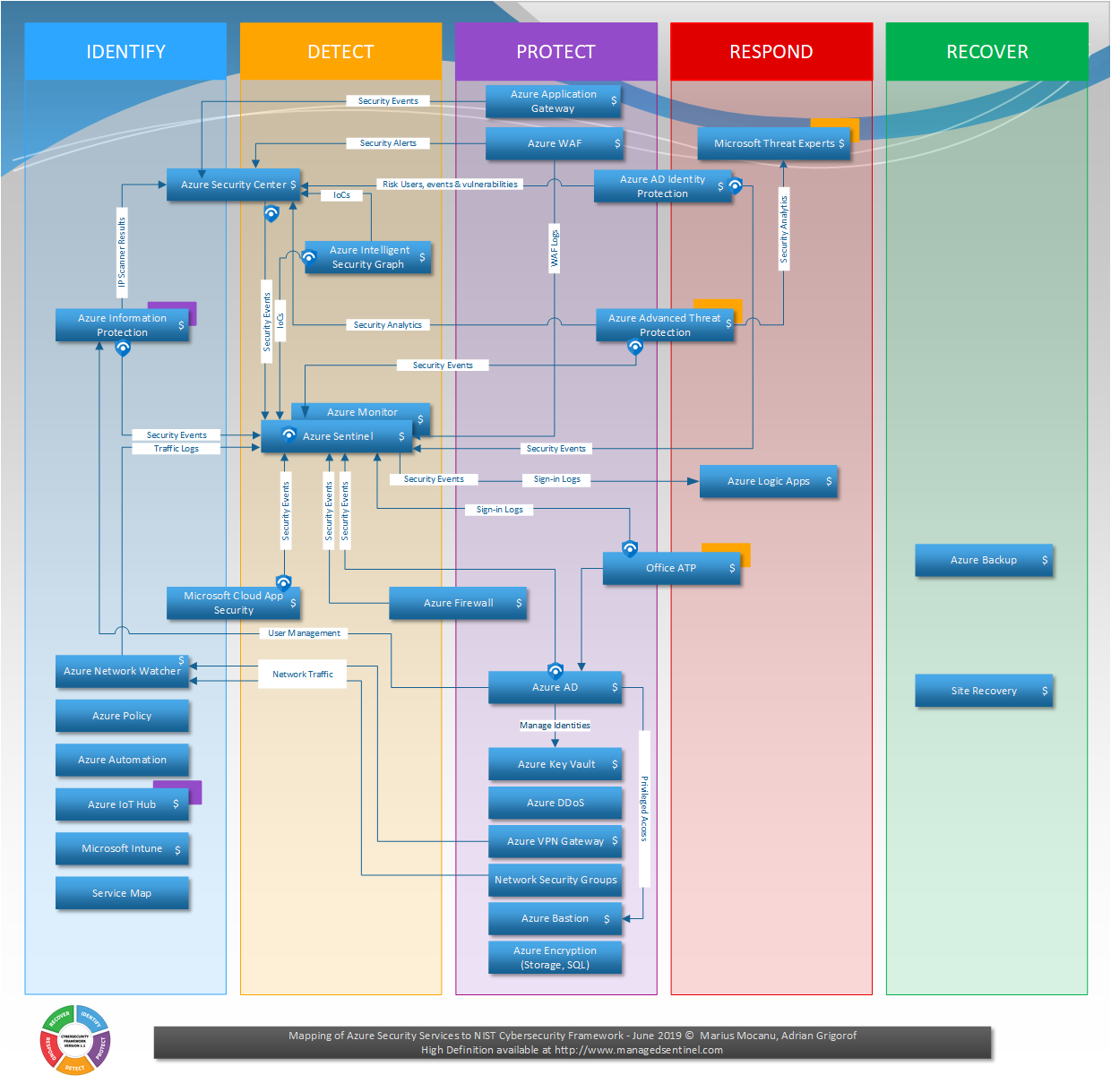
- Layered Security Architecture -Cyber Security Technology with NIST Cyber Security Framework
- Cyber Security Frameworks and Integrated with TOGAF
- EA (Enterprise Architecture) Framework Resources
Defense in depth: A layered approach to security
Reference : Microsoft Defense in Depth
Security layers
Defense in depth can be visualized as a set of concentric rings, with the data to be secured at the center. Each ring adds an additional layer of security around the data. This approach removes reliance on any single layer of protection and acts to slow down an attack and provide alert telemetry that can be acted upon, either automatically or manually. Let's take a look at each of the layers.
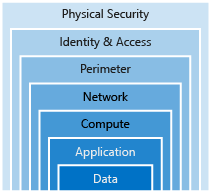
Data
Such as Databases, files, documents, Active Directory.
In almost all cases, attackers are after data:
- Stored in a database
- Stored on disk inside virtual machines
- Stored on a SaaS application such as Microsoft 365
- Stored in cloud storage
It's the responsibility of those storing and controlling access to data to ensure that it's properly secured. Often there are regulatory requirements that dictate the controls and processes that must be in place to ensure the confidentiality, integrity, and availability of the data.
Applications
Such as Enterprise software, software used on user workstations.- Ensure applications are secure and free of vulnerabilities
- Store sensitive application secrets in a secure storage medium
- Make security a design requirement for all application development
Integrating security into the application development life cycle will help reduce the number of vulnerabilities introduced in code. Encourage all development teams to ensure their applications are secure by default. Make security requirements non-negotiable.
Compute (Host)
Such as : Operating systems: servers running applications, user workstations.- Secure access to virtual machines
- Implement endpoint protection and keep systems patched and current
Malware, unpatched systems, and improperly secured systems open your environment to attacks. The focus in this layer is on making sure your compute resources are secure, and that you have the proper controls in place to minimize security issues.
Networking
- Limit communication between resources through segmentation and access controls
- Deny by default
- Restrict inbound internet access and limit outbound where appropriate
- Implement secure connectivity to on-premises networks
At this layer, the focus is on limiting the network connectivity across all your resources to only allow what is required. Segment your resources and use network level controls to restrict communication to only what is needed. By limiting this communication, you reduce the risk of lateral movement throughout your network.
Perimeter
- Use distributed denial-of-service (DDoS) protection to filter large-scale attacks before they can cause a denial of service for end users
- Use perimeter firewalls to identify and alert on malicious attacks against your network
At the network perimeter, it's about protecting from network-based attacks against your resources. Identifying these attacks, eliminating their impact, and alerting on them is important to keep your network secure.
Identity & access
- Control access to infrastructure, change control
- Use single sign-on and multi-factor authentication
- Audit events and changes
The identity & access layer is all about ensuring identities are secure, and that access granted is only what is needed, and changes are logged.
Physical security
- Physical building security and controlling access to computing hardware within the data center is the first line of defense.
With physical security, the intent is to provide physical safeguards against access to assets. This ensures that other layers can't be bypassed, and loss or theft is handled appropriately.
Each layer can implement one or more of the CIA concerns.
The common principles used to define a security posture are confidentiality, integrity, and availability, known collectively as CIA.
Confidentiality: Principle of least privilege. Restricts access to information only to individuals explicitly granted access. This information includes protection of user passwords, remote access certificates, and email content.
Integrity: The prevention of unauthorized changes to information at rest or in transit. A common approach used in data transmission is for the sender to create a unique fingerprint of the data using a one-way hashing algorithm. The hash is sent to the receiver along with the data. The data's hash is recalculated and compared to the original by the receiver to ensure the data wasn't lost or modified in transit.
Availability: Ensure services are available to authorized users. Denial of service attacks are a prevalent cause of loss of availability to users. Natural disasters also drive system design to prevent single points of failure and deploy multiple instances of an application to geo-dispersed locations.
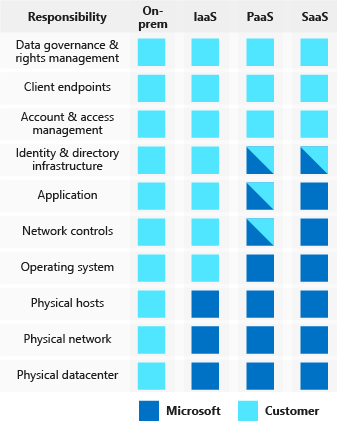
Shared responsibilities
As computing environments move from customer-controlled datacenters to cloud datacenters, the responsibility of security also shifts. Security is now a concern shared by both cloud providers and customers.
NIST CSF
The NIST Framework for Improving Critical Infrastructure Cybersecurity (NIST Cybersecurity Framework, or CSF) was originally published in February 2014 in response to Presidential Executive Order 13636, “Improving Critical Infrastructure Cybersecurity,” which called for the development of a voluntary framework to help organizations improve the cybersecurity, risk management, and resilience of their systems. NIST conferred with a broad range of partners from
 government, industry, and academia for over a year to build a consensus-based set of sound guidelines and practices.
government, industry, and academia for over a year to build a consensus-based set of sound guidelines and practices.The Cybersecurity Enhancement Act of 2014 reinforced the legitimacy and authority of the CSF by codifying it and its voluntary adoption into law, until the Presidential Executive Order on “Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure” signed on May 11, 2017, mandated the use of CSF for all U.S. federal entities.
While intended for adoption by the critical infrastructure sector, the foundational set of cybersecurity disciplines comprising the CSF have been supported by government and industry as a recommended baseline for use by any organization, regardless of its sector or size. Industry is increasingly referencing the CSF as a de facto cybersecurity standard.
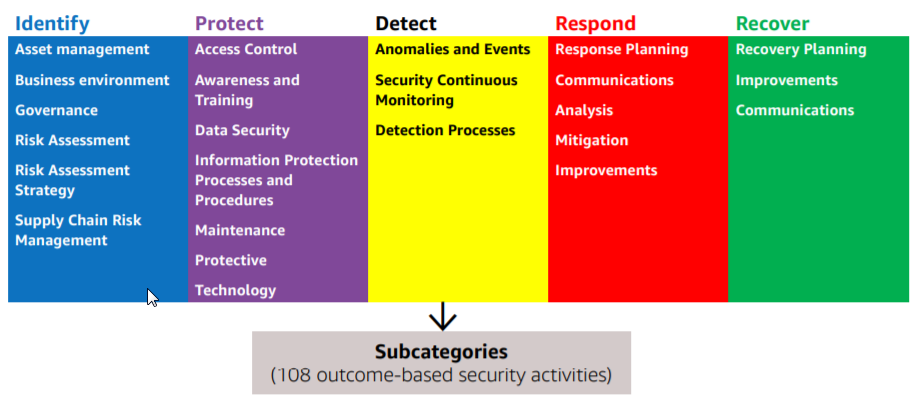
In Feb 2018, the International Standards Organization released “ISO/IEC 27103:2018 — Information technology— Security techniques -- Cybersecurity and ISO and IEC Standards.” This technical report provides guidance for implementing a cybersecurity framework leveraging existing standards. In fact, ISO 27103 promotes the same concepts and best practices reflected in the NIST CSF; specifically, a framework focused on security outcomes organized around five functions (Identify, Protect, Detect, Respond, Recover) and foundational activities that crosswalk to existing standards, accreditations and frameworks.

Align NIST CSF in AWS Cloud
NIST Cybersecurity Framework (CSF) Aligning to the NIST CSF in the AWS CloudAWS Services and Customer Responsibility Matrix for Alignment to the CSF
The AWS Services and Customer Responsibility Matrix for Alignment to the CSF spreadsheet assists customers with mapping their alignment to the NIST CSF. This spreadsheet is located under the Workbooks tab within the Resources section of the AWS Compliance website







No comments:
Post a Comment