Cybersecurity Policy
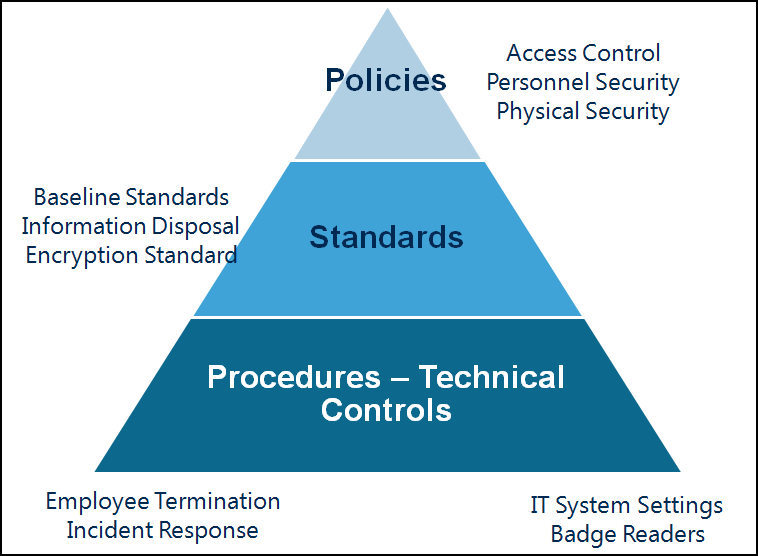
Policy relates to a decision of the governing body of an organisation. A policy is typically an internal organisational decision that aids how it functions. A policy is a formal statement of a principle that should be followed by its intended audience. Each policy should address an important issue concerning the achievement of the overall purpose of the organisation. So a policy on health and safety in the workplace addresses the relevance of safety to the enterprise and to whom the principles apply. The policy must link with the strategic objectives (such as improved service quality, reduced costs and fewer injuries).An example of a policy that you will typically find in organisations is: “Legal services review all third party contracts”. In this example, the decision from the governing body is that legal services review third party contracts. This means that no other department in the organisation has permission to review third-party contracts other than legal services.
Policy is mandatory.
1 Charter
2 Policy
| Acceptable Use Policy | Password Policy | |
| Backup Policy | Network Access Policy | |
| Incident Response Policy | Remote Access Policy | |
| Virtual Private Network (VPN) Policy | Guest Access Policy | |
| Wireless Policy | Third Party Connection Policy | |
| Network Security Policy | Encryption Policy | |
| Confidential Data Policy | Data Classification Policy | |
| Mobile Device Policy | Retention Policy | |
| Outsourcing Policy | Physical Security Policy | |
| E-mail Policy https://www.sans.org/information-security-policy/ |
3 Employment handbook
4 Others
Procedures & Controls
A procedure provides detailed mandatory steps (sometimes in the form of a checklist) someone needs to follow to achieve a recurring task or comply with a policy. These procedures can include step by step instructions or statements telling you where something needs to go. A procedure informs employees how to carry out or implement a policy. Procedures usually contain written instructions in logical numbered steps.- COVID-19 Guidance For Working Remotely
- Business Continuity Requests
- Credit Card Processing Procedures
- Data Privacy Procedures
- Patch Management Procedure
- Third Party Security Procedures
- Export Control
- Incident Response Procedure
- Vulnerability Management Procedure
- Policy Exception Procedure
- PCI DSS Assessment Procedure
- System Security Plan and Assessment Procedure
Standard
A standard specifies uniform uses of specific technologies or configurations. Here we are talking about a specific internal standard of an organisation. People sometimes talk about employment standards or rules (like rules of conduct or performance). These do fall within this category.
The other kind of standard is one that is issued by a third party (for example an industry body like ISO). For example, the ISO 27000 suite or data protection standards. Third-party rules (like professional rules) or codes (like the code of conduct of an association) are often associated with third-party standards.
An example of a standard is: “All contracts have the following typography: Font: Arial; Font Size: 8; Margin Type: Normal”. Standards are often standalone and referenced in policies. In your policy, you will find the following statement: “We use the contract standard to review our contracts”. In this example, the policy refers to the standard and the standard assists the target audience comply with the policy.
1 Name Convention
2 Patching and Updates
3 Vulnerability Scanning and Remediation Standard
4 Device, Server, Host Hardening
Examples:
- Approved Endpoint Software
- Data Protection Safeguards
- Data Protection Safeguards - Cloud Computing
- Data Protection Safeguards - Endpoints
- Data Protection Safeguards - Mobile Devices
- Data Protection Safeguards - Servers
- Data Categorization
- Encryption Standard
- Network Firewall Standards
- Terms of Use (login banner)
- SSH Server Standard
- Email Standard
- Web Server Standard
Guide / Guideline
A guideline provides general guidance, and additional advice and support for policies, standards or procedures. A guideline gives the reader guidance and additional information to help the audience. It will also assist the policymaker in explaining the policy to the policy audience in simpler terms. Many people confuse a guideline with a policy because a guideline contains similar content to a policy. The biggest difference between the two is that a guideline is voluntary and policy is always mandatory.
An example of a guideline is: “Before reviewing a contract, try to gather as much relevant information about the transaction as possible. Find out what the parties believe to be the significant risks“. One of the modules in our programme called having good policies in place is also an example of guidance for policies.
1 Operation Schedule
- Patching/Updating
- Scanning
- Compliance
2 Change Request
3 Risk Registrar
4 Incidence List
- Incidental Use Guidelines
Forms
Examples:
- Approved Change Request Form - IT Software
- Approved Change Request Form - OS upgrades
- Change Request Form
- Key Log Form
- Third Party Security Questionnaire
- Visitor Log
Compliance Documents
Example- NIST 800-171 - Protecting Controlled Unclassified Information in Nonfederal Systems and Organization







No comments:
Post a Comment