It is a common use case to integrate your on-prem AD DS with your Azure Storage File Shares. This post summarize the necessary steps to simplify the procedures from Microsoft documentation in the following:
Follow the steps below to set up Azure Files for AD DS Authentication:
Part one: enable AD DS authentication on your storage account
Part three: configure Windows ACLs over SMB for directories and files
Part four: mount an Azure file share to a VM joined to your AD DS
Update the password of your storage account identity in AD DS
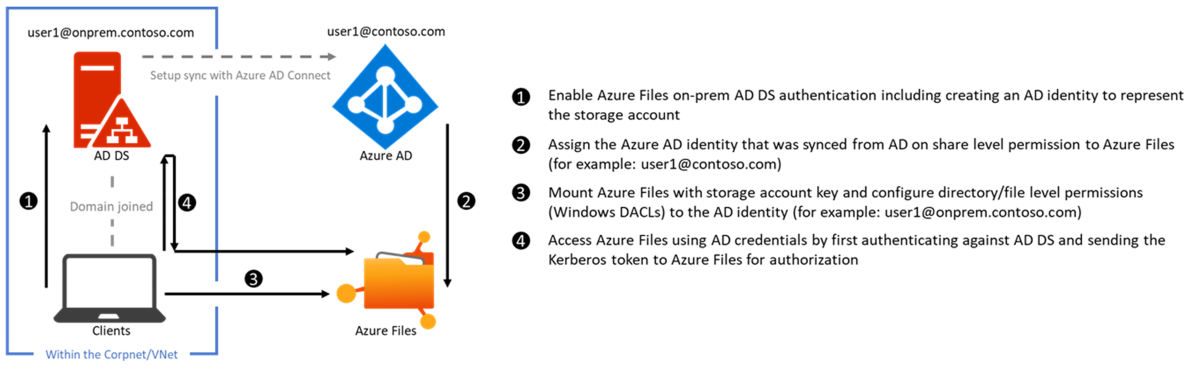
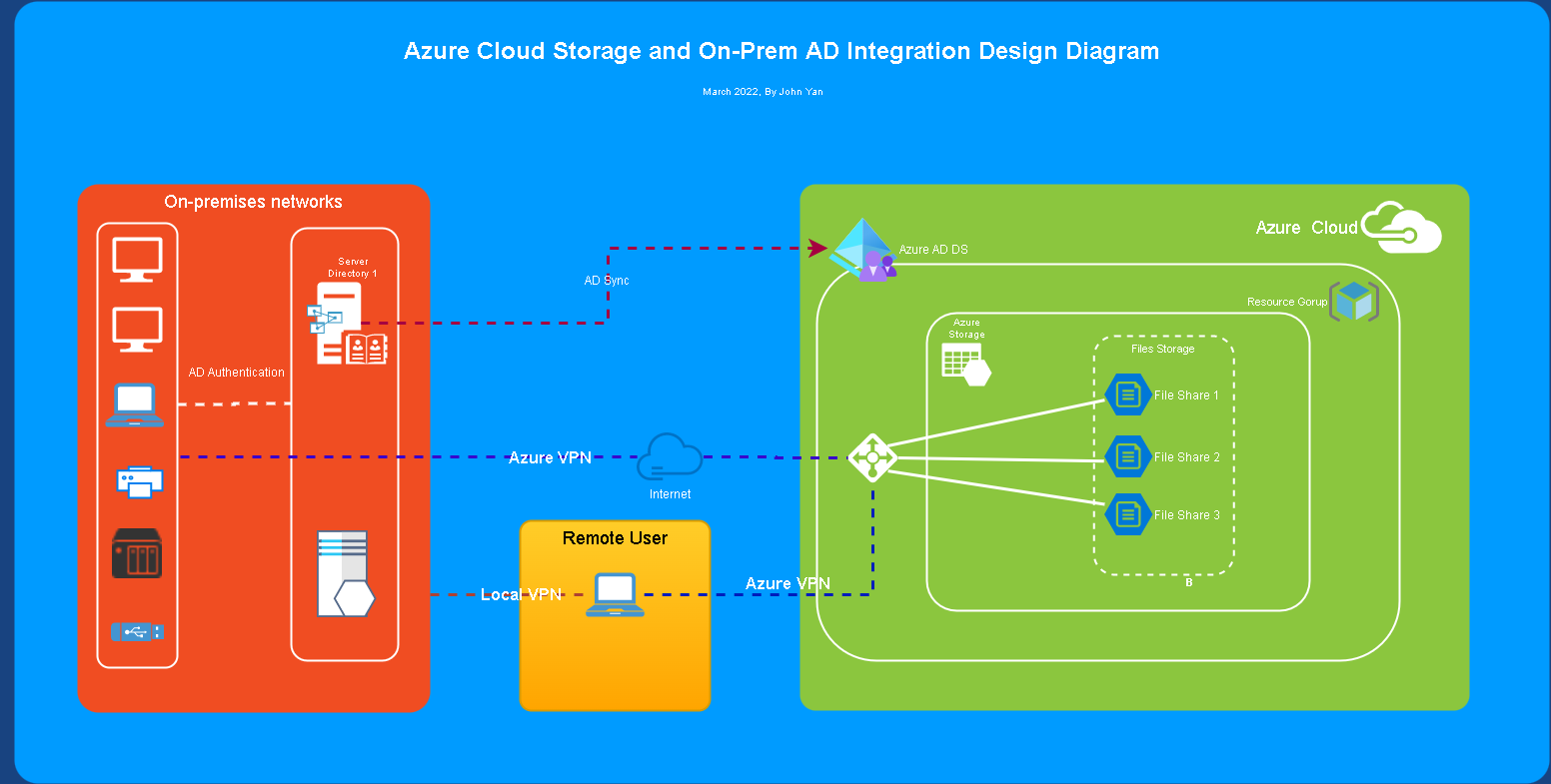
The following diagram illustrates the end-to-end workflow for enabling Azure AD authentication over SMB for Azure file shares.
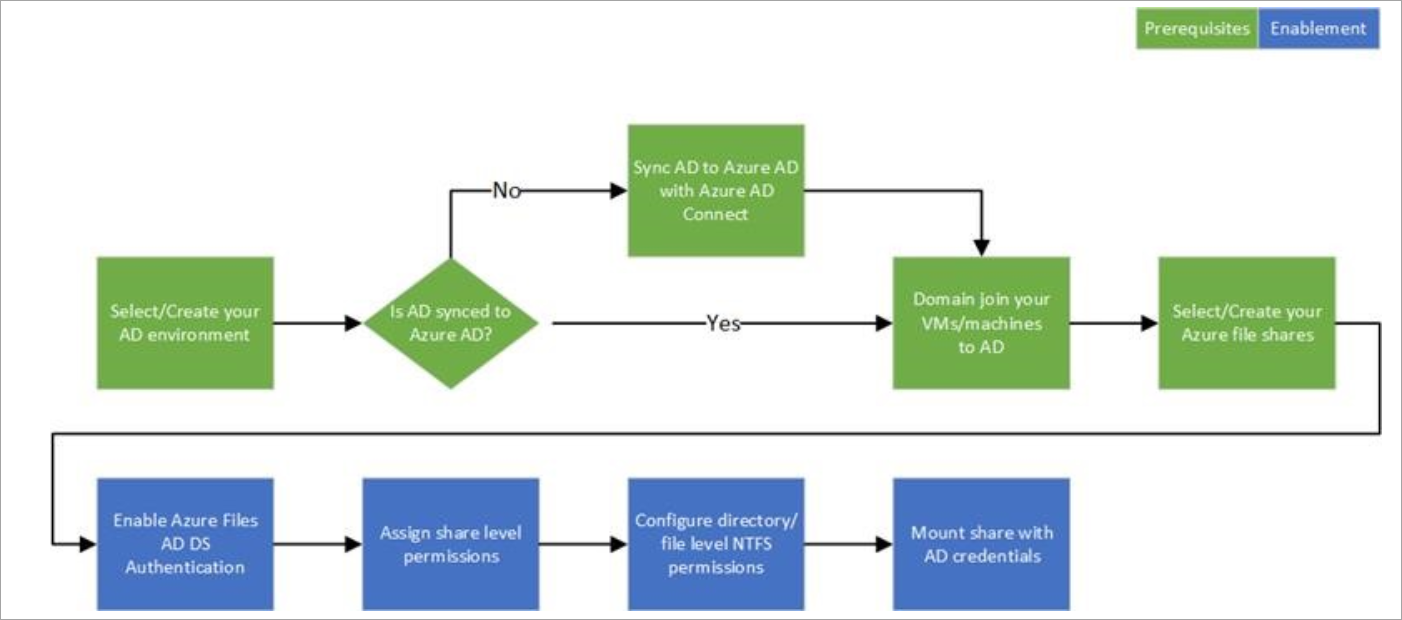
My Lab Diagram
Pre-requisites
1 AD DS environment is ready and sync it to Azure AD with Azure AD Connect.
2 Azure storage account and file share created.
3 Network connection is ready for your client machine, which means it can reach out to your Local AD DC and reach out to your Azure File Share (port 445). If not, you might need two VPNs, one vpn to local AD DC, and one vpn to Azure File Share (Private End Point)
Quick Steps
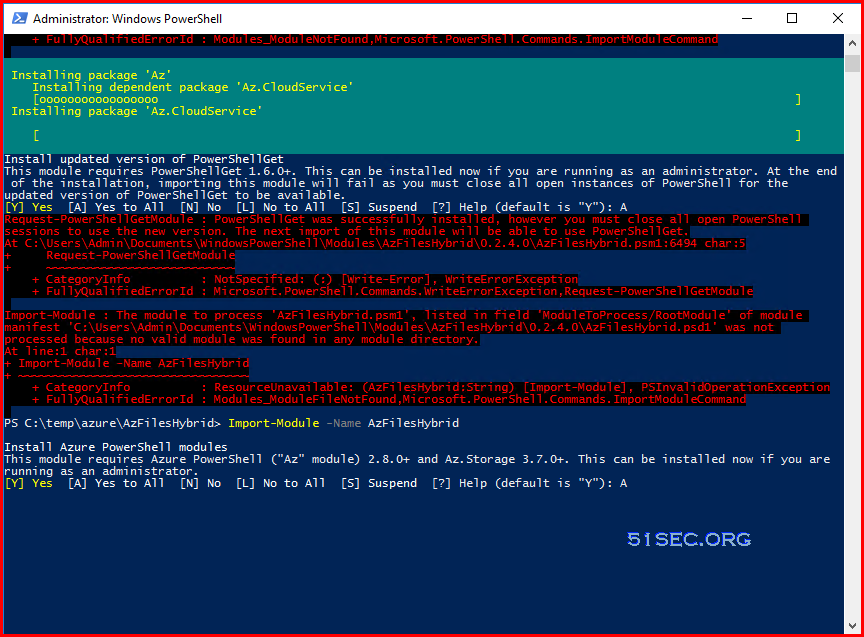
1 Download and unzip the AzFilesHybrid module (GA module: v0.2.0+)
For example, unzip it to c:\temp\azure folder
2 Install and execute the module. It will take a while to done during installing packages:
Import-Module -Name AzFilesHybrid
3 Connect to Azure Account
Connect-AzAccount
4 Run Join-AzStorageAccount Powershell command
-ResourceGroupName rg-FileShare-Test-EastUs-1 `
-StorageAccountName netsecfs `
-DomainAccountType ComputerAccount `
-OrganizationalUnitDistinguishedName "OU=StorageAccounts,DC=51sec,DC=corp"
PS C:\Windows\system32> cd C:\temp\jy\
PS C:\temp\jy> cd .\AzFilesHybrid\
PS C:\temp\jy\AzFilesHybrid> Import-Module -Name AzFilesHybrid
Security warning
Run only scripts that you trust. While scripts from the internet can be useful, this script can potentially harm your
computer. If you trust this script, use the Unblock-File cmdlet to allow the script to run without this warning
message. Do you want to run C:\Users\jon\Documents\WindowsPowerShell\Modules\AzFilesHybrid\0.2.4.0\AzFilesHybrid.psm1?
[D] Do not run [R] Run once [S] Suspend [?] Help (default is "D"): R
Install Azure PowerShell modules
This module requires Azure PowerShell ("Az" module) 2.8.0+ and Az.Storage 3.7.0+. This can be installed now if you are
running as an administrator.
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): A
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid> Connect-AzAccount
Account SubscriptionName TenantId Environment
------- ---------------- -------- -----------
[email protected] Pay-As-You-Go 00771de-ce1-4f6-bc3-b9fecde7b AzureCloud
PS C:\temp\jy\AzFilesHybrid> Join-AzStorageAccount `
>> -ResourceGroupName rg-FileShare-Test-EastUs-1 `
>> -StorageAccountName netsecfs `
>> -DomainAccountType ComputerAccount `
>> -OrganizationalUnitDistinguishedName "OU=StorageAccounts,DC=corp,DC=51sec,DC=org"
StorageAccountName ResourceGroupName PrimaryLocation SkuName Kind AccessTier CreationTime
------------------ ----------------- --------------- ------- ---- ---------- ------------
netsecfileshares rg-fileshare-test-eastus-1 eastus Standard_RAGRS StorageV2 Hot 3/26/2022 11:20:55 PM
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid>
PS C:\temp\jy\AzFilesHybrid> Debug-AzStorageAccountAuth -StorageAccountName netsecfileshares -ResourceGroupName rg-FileShar
e-Test-EastUs-1 -Verbose
VERBOSE: CheckPort445Connectivity - START
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Executing 'Test-NetConnection -ComputerName netsecfileshares.file.core.windows.net -Port 445'
VERBOSE: CheckPort445Connectivity - SUCCESS
VERBOSE: CheckDomainJoined - START
VERBOSE: Perform operation 'Enumerate CimInstances' with following parameters, ''namespaceName' =
root\cimv2,'className' = win32_computersystem'.
VERBOSE: Operation 'Enumerate CimInstances' complete.
VERBOSE: Session is running in a domain-joined environment.
VERBOSE: CheckDomainJoined - SUCCESS
VERBOSE: CheckADObject - START
VERBOSE: Perform operation 'Enumerate CimInstances' with following parameters, ''namespaceName' =
root\cimv2,'className' = win32_computersystem'.
VERBOSE: Operation 'Enumerate CimInstances' complete.
VERBOSE: Session is running in a domain-joined environment.
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Looking for an object with SID 'S-1-5-21-2488401269-1895120637-1421044794-10609' in domain
'corp.netsec.com' for storage account 'netsecfileshares'
VERBOSE: Found AD object: CN=netsecfileshares,OU=StorageAccountsOU,DC=corp,DC=netseccoustics,DC=com of class computer.
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Generated service principal name of cifs/netsecfileshares.file.core.windows.net
VERBOSE: CheckADObject - SUCCESS
VERBOSE: CheckGetKerberosTicket - START
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Generated service principal name of cifs/netsecfileshares.file.core.windows.net
VERBOSE: Running command 'klist.exe get cifs/netsecfileshares.file.core.windows.net'
VERBOSE:
VERBOSE: Current LogonId is 0:0xb90872
VERBOSE: A ticket to cifs/netsecfileshares.file.core.windows.net has been retrieved successfully.
VERBOSE:
VERBOSE: Cached Tickets: (2)
VERBOSE:
VERBOSE: #0> Client: jon @ CORP.netsec.com
VERBOSE: Server: krbtgt/CORP.netsec.com @ CORP.netsec.com
VERBOSE: KerbTicket Encryption Type: AES-256-CTS-HMAC-SHA1-96
VERBOSE: Ticket Flags 0x40e10000 -> forwardable renewable initial pre_authent name_canonicalize
VERBOSE: Start Time: 3/26/2022 19:25:37 (local)
VERBOSE: End Time: 3/27/2022 5:25:37 (local)
VERBOSE: Renew Time: 4/2/2022 19:25:37 (local)
VERBOSE: Session Key Type: AES-256-CTS-HMAC-SHA1-96
VERBOSE: Cache Flags: 0x1 -> PRIMARY
VERBOSE: Kdc Called: netsecDC04
VERBOSE:
VERBOSE: #1> Client: jon @ CORP.netsec.com
VERBOSE: Server: cifs/netsecfileshares.file.core.windows.net @ CORP.netsec.com
VERBOSE: KerbTicket Encryption Type: RSADSI RC4-HMAC(NT)
VERBOSE: Ticket Flags 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
VERBOSE: Start Time: 3/26/2022 19:25:37 (local)
VERBOSE: End Time: 3/27/2022 5:25:37 (local)
VERBOSE: Renew Time: 4/2/2022 19:25:37 (local)
VERBOSE: Session Key Type: RSADSI RC4-HMAC(NT)
VERBOSE: Cache Flags: 0
VERBOSE: Kdc Called: netsecDC04
VERBOSE: Azure Files Kerberos Ticket Health Check Summary:
VERBOSE: 1 Kerberos service tickets to Azure storage accounts were detected.
VERBOSE: Ticket #1 : Healthy
VERBOSE:
Client : jon @ CORP.netsec.com
Server : cifs/netsecfileshares.file.core.windows.net @ CORP.netsec.com
KerbTicket Encryption Type : RSADSI RC4-HMAC(NT)
Ticket Flags : 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time : 3/26/2022 19:25:37 (local)
End Time : 3/27/2022 5:25:37 (local)
Renew Time : 4/2/2022 19:25:37 (local)
Session Key Type : RSADSI RC4-HMAC(NT)
Azure Files Health Status : Healthy
Client : jon @ CORP.netsec.com
Server : cifs/netsecfileshares.file.core.windows.net @ CORP.netsec.com
KerbTicket Encryption Type : RSADSI RC4-HMAC(NT)
Ticket Flags : 0x40a10000 -> forwardable renewable pre_authent name_canonicalize
Start Time : 3/26/2022 19:25:37 (local)
End Time : 3/27/2022 5:25:37 (local)
Renew Time : 4/2/2022 19:25:37 (local)
Session Key Type : RSADSI RC4-HMAC(NT)
Azure Files Health Status : Healthy
VERBOSE: CheckGetKerberosTicket - SUCCESS
VERBOSE: CheckADObjectPasswordIsCorrect - START
VERBOSE: Perform operation 'Enumerate CimInstances' with following parameters, ''namespaceName' =
root\cimv2,'className' = win32_computersystem'.
VERBOSE: Operation 'Enumerate CimInstances' complete.
VERBOSE: Session is running in a domain-joined environment.
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Perform operation 'Enumerate CimInstances' with following parameters, ''namespaceName' =
root\cimv2,'className' = win32_computersystem'.
VERBOSE: Operation 'Enumerate CimInstances' complete.
VERBOSE: Session is running in a domain-joined environment.
VERBOSE: Looking for an object with SID 'S-1-5-21-2488401269-1895120637-1421044794-10609' in domain
'corp.netsec.com' for storage account 'netsecfileshares'
VERBOSE: Found AD object: CN=netsecfileshares,OU=StorageAccountsOU,DC=corp,DC=netseccoustics,DC=com of class computer.
VERBOSE: Found that kerb1 matches password for netsecfileshares in AD.
ResourceGroupName : rg-FileShare-Test-EastUs-1
StorageAccountName : netsecfileshares
KerbKeyName :
KeyMatches : False
ResourceGroupName : rg-FileShare-Test-EastUs-1
StorageAccountName : netsecfileshares
KerbKeyName : kerb1
KeyMatches : True
ResourceGroupName : rg-FileShare-Test-EastUs-1
StorageAccountName : netsecfileshares
KerbKeyName : kerb2
KeyMatches : False
VERBOSE: CheckADObjectPasswordIsCorrect - SUCCESS
VERBOSE: CheckSidHasAadUser - START
VERBOSE: Look up user jon in domain corp.netsec.com
VERBOSE: User in domain has SID = S-1-5-21-2488401269-1895120637-1421044794-9150
Install AzureAD PowerShell module
This cmdlet requires the Azure AD PowerShell module. This can be automatically installed now if you are running in an
elevated sessions.
[Y] Yes [A] Yes to All [N] No [L] No to All [S] Suspend [?] Help (default is "Y"): A
VERBOSE: Removing the imported "Find-Command" function.
VERBOSE: Removing the imported "Find-DscResource" function.
VERBOSE: Removing the imported "Find-Module" function.
VERBOSE: Removing the imported "Find-RoleCapability" function.
VERBOSE: Removing the imported "Find-Script" function.
VERBOSE: Removing the imported "Get-CredsFromCredentialProvider" function.
VERBOSE: Removing the imported "Get-InstalledModule" function.
VERBOSE: Removing the imported "Get-InstalledScript" function.
VERBOSE: Removing the imported "Get-PSRepository" function.
VERBOSE: Removing the imported "Install-Module" function.
VERBOSE: Removing the imported "Install-Script" function.
VERBOSE: Removing the imported "New-ScriptFileInfo" function.
VERBOSE: Removing the imported "Publish-Module" function.
VERBOSE: Removing the imported "Publish-Script" function.
VERBOSE: Removing the imported "Register-PSRepository" function.
VERBOSE: Removing the imported "Save-Module" function.
VERBOSE: Removing the imported "Save-Script" function.
VERBOSE: Removing the imported "Set-PSRepository" function.
VERBOSE: Removing the imported "Test-ScriptFileInfo" function.
VERBOSE: Removing the imported "Uninstall-Module" function.
VERBOSE: Removing the imported "Uninstall-Script" function.
VERBOSE: Removing the imported "Unregister-PSRepository" function.
VERBOSE: Removing the imported "Update-Module" function.
VERBOSE: Removing the imported "Update-ModuleManifest" function.
VERBOSE: Removing the imported "Update-Script" function.
VERBOSE: Removing the imported "Update-ScriptFileInfo" function.
VERBOSE: Removing the imported "PSGetPath" variable.
VERBOSE: Removing the imported "fimo" alias.
VERBOSE: Removing the imported "inmo" alias.
VERBOSE: Removing the imported "pumo" alias.
VERBOSE: Removing the imported "upmo" alias.
VERBOSE: Loading module from path 'C:\Program Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\AzureAD.psd1'.
VERBOSE: Loading 'FormatsToProcess' from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\AzureAD.Format.ps1xml'.
VERBOSE: Populating RepositorySourceLocation property for module AzureAD.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.AzureAD16.Graph.PowerShell.dll'.
VERBOSE: Exporting cmdlet 'Add-AzureADApplicationOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplication'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationExtensionProperty'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationServiceEndpoint'.
VERBOSE: Exporting cmdlet 'Get-AzureADDeletedApplication'.
VERBOSE: Exporting cmdlet 'Remove-AzureADDeletedApplication'.
VERBOSE: Exporting cmdlet 'New-AzureADApplication'.
VERBOSE: Exporting cmdlet 'New-AzureADApplicationExtensionProperty'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplication'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationExtensionProperty'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationOwner'.
VERBOSE: Exporting cmdlet 'Restore-AzureADDeletedApplication'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplication'.
VERBOSE: Exporting cmdlet 'Get-AzureADContact'.
VERBOSE: Exporting cmdlet 'Get-AzureADContactDirectReport'.
VERBOSE: Exporting cmdlet 'Get-AzureADContactManager'.
VERBOSE: Exporting cmdlet 'Get-AzureADContactMembership'.
VERBOSE: Exporting cmdlet 'Remove-AzureADContact'.
VERBOSE: Exporting cmdlet 'Remove-AzureADContactManager'.
VERBOSE: Exporting cmdlet 'Select-AzureADGroupIdsContactIsMemberOf'.
VERBOSE: Exporting cmdlet 'Get-AzureADContract'.
VERBOSE: Exporting cmdlet 'Add-AzureADDeviceRegisteredOwner'.
VERBOSE: Exporting cmdlet 'Add-AzureADDeviceRegisteredUser'.
VERBOSE: Exporting cmdlet 'Remove-AzureADDeviceRegisteredOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADDevice'.
VERBOSE: Exporting cmdlet 'Get-AzureADDeviceRegisteredOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADDeviceRegisteredUser'.
VERBOSE: Exporting cmdlet 'New-AzureADDevice'.
VERBOSE: Exporting cmdlet 'Remove-AzureADDevice'.
VERBOSE: Exporting cmdlet 'Remove-AzureADDeviceRegisteredUser'.
VERBOSE: Exporting cmdlet 'Set-AzureADDevice'.
VERBOSE: Exporting cmdlet 'Get-AzureADDeviceConfiguration'.
VERBOSE: Exporting cmdlet 'Get-AzureADObjectByObjectId'.
VERBOSE: Exporting cmdlet 'Enable-AzureADDirectoryRole'.
VERBOSE: Exporting cmdlet 'Add-AzureADDirectoryRoleMember'.
VERBOSE: Exporting cmdlet 'Get-AzureADDirectoryRoleMember'.
VERBOSE: Exporting cmdlet 'Get-AzureADDirectoryRole'.
VERBOSE: Exporting cmdlet 'Remove-AzureADDirectoryRoleMember'.
VERBOSE: Exporting cmdlet 'Get-AzureADDirectoryRoleTemplate'.
VERBOSE: Exporting cmdlet 'Confirm-AzureADDomain'.
VERBOSE: Exporting cmdlet 'Get-CrossCloudVerificationCode'.
VERBOSE: Exporting cmdlet 'Get-AzureADDomain'.
VERBOSE: Exporting cmdlet 'Get-AzureADDomainNameReference'.
VERBOSE: Exporting cmdlet 'Get-AzureADDomainServiceConfigurationRecord'.
VERBOSE: Exporting cmdlet 'Get-AzureADDomainVerificationDnsRecord'.
VERBOSE: Exporting cmdlet 'New-AzureADDomain'.
VERBOSE: Exporting cmdlet 'Remove-AzureADDomain'.
VERBOSE: Exporting cmdlet 'Set-AzureADDomain'.
VERBOSE: Exporting cmdlet 'Get-AzureADExtensionProperty'.
VERBOSE: Exporting cmdlet 'Add-AzureADGroupMember'.
VERBOSE: Exporting cmdlet 'Add-AzureADGroupOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADGroupAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Get-AzureADGroupMember'.
VERBOSE: Exporting cmdlet 'Get-AzureADGroupOwner'.
VERBOSE: Exporting cmdlet 'New-AzureADGroup'.
VERBOSE: Exporting cmdlet 'New-AzureADGroupAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADGroup'.
VERBOSE: Exporting cmdlet 'Remove-AzureADGroupAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADGroupMember'.
VERBOSE: Exporting cmdlet 'Remove-AzureADGroupOwner'.
VERBOSE: Exporting cmdlet 'Select-AzureADGroupIdsGroupIsMemberOf'.
VERBOSE: Exporting cmdlet 'Set-AzureADGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADOAuth2PermissionGrant'.
VERBOSE: Exporting cmdlet 'Remove-AzureADOAuth2PermissionGrant'.
VERBOSE: Exporting cmdlet 'Add-AzureADServicePrincipalOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipal'.
VERBOSE: Exporting cmdlet 'Get-AzureADServiceAppRoleAssignedTo'.
VERBOSE: Exporting cmdlet 'Get-AzureADServiceAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalCreatedObject'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalMembership'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalOAuth2PermissionGrant'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalOwnedObject'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalOwner'.
VERBOSE: Exporting cmdlet 'New-AzureADServicePrincipal'.
VERBOSE: Exporting cmdlet 'New-AzureADServiceAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADServicePrincipal'.
VERBOSE: Exporting cmdlet 'Remove-AzureADServiceAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADServicePrincipalOwner'.
VERBOSE: Exporting cmdlet 'Select-AzureADGroupIdsServicePrincipalIsMemberOf'.
VERBOSE: Exporting cmdlet 'Set-AzureADServicePrincipal'.
VERBOSE: Exporting cmdlet 'Revoke-AzureADSignedInUserAllRefreshToken'.
VERBOSE: Exporting cmdlet 'Get-AzureADSubscribedSku'.
VERBOSE: Exporting cmdlet 'Get-AzureADTenantDetail'.
VERBOSE: Exporting cmdlet 'Set-AzureADTenantDetail'.
VERBOSE: Exporting cmdlet 'Get-AzureADUser'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserCreatedObject'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserDirectReport'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserLicenseDetail'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserManager'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserMembership'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserOAuth2PermissionGrant'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserOwnedDevice'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserOwnedObject'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserRegisteredDevice'.
VERBOSE: Exporting cmdlet 'New-AzureADUser'.
VERBOSE: Exporting cmdlet 'New-AzureADUserAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADUser'.
VERBOSE: Exporting cmdlet 'Remove-AzureADUserAppRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADUserManager'.
VERBOSE: Exporting cmdlet 'Revoke-AzureADUserAllRefreshToken'.
VERBOSE: Exporting cmdlet 'Select-AzureADGroupIdsUserIsMemberOf'.
VERBOSE: Exporting cmdlet 'Set-AzureADUser'.
VERBOSE: Exporting cmdlet 'Set-AzureADUserLicense'.
VERBOSE: Exporting cmdlet 'Set-AzureADUserManager'.
VERBOSE: Exporting cmdlet 'Connect-AzureAD'.
VERBOSE: Exporting cmdlet 'Disconnect-AzureAD'.
VERBOSE: Exporting cmdlet 'Get-AzureADCurrentSessionInfo'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationLogo'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationLogo'.
VERBOSE: Exporting cmdlet 'Set-AzureADUserPassword'.
VERBOSE: Exporting cmdlet 'Get-AzureADContactThumbnailPhoto'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserThumbnailPhoto'.
VERBOSE: Exporting cmdlet 'Set-AzureADUserThumbnailPhoto'.
VERBOSE: Exporting cmdlet 'New-AzureADApplicationKeyCredential'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationKeyCredential'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationKeyCredential'.
VERBOSE: Exporting cmdlet 'New-AzureADApplicationPasswordCredential'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationPasswordCredential'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationPasswordCredential'.
VERBOSE: Exporting cmdlet 'Update-AzureADSignedInUserPassword'.
VERBOSE: Exporting cmdlet 'New-AzureADServicePrincipalKeyCredential'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalKeyCredential'.
VERBOSE: Exporting cmdlet 'Remove-AzureADServicePrincipalKeyCredential'.
VERBOSE: Exporting cmdlet 'New-AzureADServicePrincipalPasswordCredential'.
VERBOSE: Exporting cmdlet 'Get-AzureADServicePrincipalPasswordCredential'.
VERBOSE: Exporting cmdlet 'Remove-AzureADServicePrincipalPasswordCredential'.
VERBOSE: Exporting cmdlet 'Get-AzureADTrustedCertificateAuthority'.
VERBOSE: Exporting cmdlet 'New-AzureADTrustedCertificateAuthority'.
VERBOSE: Exporting cmdlet 'Set-AzureADTrustedCertificateAuthority'.
VERBOSE: Exporting cmdlet 'Remove-AzureADTrustedCertificateAuthority'.
VERBOSE: Exporting cmdlet 'Get-AzureADUserExtension'.
VERBOSE: Exporting cmdlet 'Set-AzureADUserExtension'.
VERBOSE: Exporting cmdlet 'Remove-AzureADUserExtension'.
VERBOSE: Exporting cmdlet 'Add-AzureADMSApplicationOwner'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSApplication'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSApplicationExtensionProperty'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSApplicationOwner'.
VERBOSE: Exporting cmdlet 'New-AzureADMSApplication'.
VERBOSE: Exporting cmdlet 'New-AzureADMSApplicationExtensionProperty'.
VERBOSE: Exporting cmdlet 'New-AzureADMSApplicationKey'.
VERBOSE: Exporting cmdlet 'New-AzureADMSApplicationPassword'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSApplication'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSApplicationExtensionProperty'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSApplicationKey'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSApplicationOwner'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSApplicationPassword'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSApplication'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSApplicationLogo'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationProxyApplication'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationProxyApplicationConnectorGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationProxyConnector'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationProxyConnectorGroupMember'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationProxyConnectorMemberOf'.
VERBOSE: Exporting cmdlet 'New-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationProxyApplicationConnectorGroup'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSApplicationVerifiedPublisher'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSApplicationVerifiedPublisher'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSAuthorizationPolicy'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSAuthorizationPolicy'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSGroupPermissionGrant'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Exporting cmdlet 'New-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSPermissionGrantPolicy'.
VERBOSE: Exporting cmdlet 'New-AzureADMSPermissionGrantPolicy'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSPermissionGrantPolicy'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSPermissionGrantPolicy'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSRoleAssignment'.
VERBOSE: Exporting cmdlet 'New-AzureADMSRoleAssignment'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSRoleAssignment'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSRoleDefinition'.
VERBOSE: Exporting cmdlet 'New-AzureADMSRoleDefinition'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSRoleDefinition'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSRoleDefinition'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSConditionalAccessPolicy'.
VERBOSE: Exporting cmdlet 'New-AzureADMSConditionalAccessPolicy'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSConditionalAccessPolicy'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSConditionalAccessPolicy'.
VERBOSE: Exporting cmdlet 'Add-AzureADMSServicePrincipalDelegatedPermissionClassification'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSServicePrincipalDelegatedPermissionClassification'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSServicePrincipalDelegatedPermissionClassification'.
VERBOSE: Exporting cmdlet 'Add-AzureADMSLifecyclePolicyGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Exporting cmdlet 'New-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSLifecyclePolicyGroup'.
VERBOSE: Exporting cmdlet 'Reset-AzureADMSLifeCycleGroup'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSIdentityProvider'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSIdentityProvider'.
VERBOSE: Exporting cmdlet 'New-AzureADMSIdentityProvider'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSIdentityProvider'.
VERBOSE: Exporting cmdlet 'New-AzureADMSInvitation'.
VERBOSE: Exporting cmdlet 'Add-AzureADMSAdministrativeUnitMember'.
VERBOSE: Exporting cmdlet 'Add-AzureADMSScopedRoleMembership'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSAdministrativeUnit'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSAdministrativeUnitMember'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSScopedRoleMembership'.
VERBOSE: Exporting cmdlet 'New-AzureADMSAdministrativeUnit'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSAdministrativeUnit'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSAdministrativeUnitMember'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSScopedRoleMembership'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSAdministrativeUnit'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSDeletedGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSDeletedDirectoryObject'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSDeletedDirectoryObject'.
VERBOSE: Exporting cmdlet 'Restore-AzureADMSDeletedDirectoryObject'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSLifecyclePolicyGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSGroup'.
VERBOSE: Exporting cmdlet 'New-AzureADMSGroup'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSGroup'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSGroup'.
VERBOSE: Exporting cmdlet 'Get-AzureADMSNamedLocationPolicy'.
VERBOSE: Exporting cmdlet 'New-AzureADMSNamedLocationPolicy'.
VERBOSE: Exporting cmdlet 'Remove-AzureADMSNamedLocationPolicy'.
VERBOSE: Exporting cmdlet 'Set-AzureADMSNamedLocationPolicy'.
VERBOSE: Exporting cmdlet 'New-AzureADApplicationProxyApplication'.
VERBOSE: Exporting cmdlet 'Remove-AzureADApplicationProxyApplication'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationProxyApplication'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationProxyApplicationConnectorGroup'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationProxyApplicationCustomDomainCertificate'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationProxyApplicationSingleSignOn'.
VERBOSE: Exporting cmdlet 'Set-AzureADApplicationProxyConnector'.
VERBOSE: Exporting cmdlet 'Get-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Exporting alias 'Get-AzureADApplicationProxyConnectorGroupMembers'.
VERBOSE: Importing cmdlet 'Add-AzureADApplicationOwner'.
VERBOSE: Importing cmdlet 'Add-AzureADDeviceRegisteredOwner'.
VERBOSE: Importing cmdlet 'Add-AzureADDeviceRegisteredUser'.
VERBOSE: Importing cmdlet 'Add-AzureADDirectoryRoleMember'.
VERBOSE: Importing cmdlet 'Add-AzureADGroupMember'.
VERBOSE: Importing cmdlet 'Add-AzureADGroupOwner'.
VERBOSE: Importing cmdlet 'Add-AzureADMSAdministrativeUnitMember'.
VERBOSE: Importing cmdlet 'Add-AzureADMSApplicationOwner'.
VERBOSE: Importing cmdlet 'Add-AzureADMSLifecyclePolicyGroup'.
VERBOSE: Importing cmdlet 'Add-AzureADMSScopedRoleMembership'.
VERBOSE: Importing cmdlet 'Add-AzureADMSServicePrincipalDelegatedPermissionClassification'.
VERBOSE: Importing cmdlet 'Add-AzureADServicePrincipalOwner'.
VERBOSE: Importing cmdlet 'Confirm-AzureADDomain'.
VERBOSE: Importing cmdlet 'Connect-AzureAD'.
VERBOSE: Importing cmdlet 'Disconnect-AzureAD'.
VERBOSE: Importing cmdlet 'Enable-AzureADDirectoryRole'.
VERBOSE: Importing cmdlet 'Get-AzureADApplication'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationExtensionProperty'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationKeyCredential'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationLogo'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationOwner'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationPasswordCredential'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationProxyApplication'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationProxyApplicationConnectorGroup'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationProxyConnector'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationProxyConnectorGroupMember'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationProxyConnectorMemberOf'.
VERBOSE: Importing cmdlet 'Get-AzureADApplicationServiceEndpoint'.
VERBOSE: Importing cmdlet 'Get-AzureADContact'.
VERBOSE: Importing cmdlet 'Get-AzureADContactDirectReport'.
VERBOSE: Importing cmdlet 'Get-AzureADContactManager'.
VERBOSE: Importing cmdlet 'Get-AzureADContactMembership'.
VERBOSE: Importing cmdlet 'Get-AzureADContactThumbnailPhoto'.
VERBOSE: Importing cmdlet 'Get-AzureADContract'.
VERBOSE: Importing cmdlet 'Get-AzureADCurrentSessionInfo'.
VERBOSE: Importing cmdlet 'Get-AzureADDeletedApplication'.
VERBOSE: Importing cmdlet 'Get-AzureADDevice'.
VERBOSE: Importing cmdlet 'Get-AzureADDeviceConfiguration'.
VERBOSE: Importing cmdlet 'Get-AzureADDeviceRegisteredOwner'.
VERBOSE: Importing cmdlet 'Get-AzureADDeviceRegisteredUser'.
VERBOSE: Importing cmdlet 'Get-AzureADDirectoryRole'.
VERBOSE: Importing cmdlet 'Get-AzureADDirectoryRoleMember'.
VERBOSE: Importing cmdlet 'Get-AzureADDirectoryRoleTemplate'.
VERBOSE: Importing cmdlet 'Get-AzureADDomain'.
VERBOSE: Importing cmdlet 'Get-AzureADDomainNameReference'.
VERBOSE: Importing cmdlet 'Get-AzureADDomainServiceConfigurationRecord'.
VERBOSE: Importing cmdlet 'Get-AzureADDomainVerificationDnsRecord'.
VERBOSE: Importing cmdlet 'Get-AzureADExtensionProperty'.
VERBOSE: Importing cmdlet 'Get-AzureADGroup'.
VERBOSE: Importing cmdlet 'Get-AzureADGroupAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Get-AzureADGroupMember'.
VERBOSE: Importing cmdlet 'Get-AzureADGroupOwner'.
VERBOSE: Importing cmdlet 'Get-AzureADMSAdministrativeUnit'.
VERBOSE: Importing cmdlet 'Get-AzureADMSAdministrativeUnitMember'.
VERBOSE: Importing cmdlet 'Get-AzureADMSApplication'.
VERBOSE: Importing cmdlet 'Get-AzureADMSApplicationExtensionProperty'.
VERBOSE: Importing cmdlet 'Get-AzureADMSApplicationOwner'.
VERBOSE: Importing cmdlet 'Get-AzureADMSAuthorizationPolicy'.
VERBOSE: Importing cmdlet 'Get-AzureADMSConditionalAccessPolicy'.
VERBOSE: Importing cmdlet 'Get-AzureADMSDeletedDirectoryObject'.
VERBOSE: Importing cmdlet 'Get-AzureADMSDeletedGroup'.
VERBOSE: Importing cmdlet 'Get-AzureADMSGroup'.
VERBOSE: Importing cmdlet 'Get-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Importing cmdlet 'Get-AzureADMSGroupPermissionGrant'.
VERBOSE: Importing cmdlet 'Get-AzureADMSIdentityProvider'.
VERBOSE: Importing cmdlet 'Get-AzureADMSLifecyclePolicyGroup'.
VERBOSE: Importing cmdlet 'Get-AzureADMSNamedLocationPolicy'.
VERBOSE: Importing cmdlet 'Get-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Importing cmdlet 'Get-AzureADMSPermissionGrantPolicy'.
VERBOSE: Importing cmdlet 'Get-AzureADMSRoleAssignment'.
VERBOSE: Importing cmdlet 'Get-AzureADMSRoleDefinition'.
VERBOSE: Importing cmdlet 'Get-AzureADMSScopedRoleMembership'.
VERBOSE: Importing cmdlet 'Get-AzureADMSServicePrincipalDelegatedPermissionClassification'.
VERBOSE: Importing cmdlet 'Get-AzureADOAuth2PermissionGrant'.
VERBOSE: Importing cmdlet 'Get-AzureADObjectByObjectId'.
VERBOSE: Importing cmdlet 'Get-AzureADServiceAppRoleAssignedTo'.
VERBOSE: Importing cmdlet 'Get-AzureADServiceAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipal'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalCreatedObject'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalKeyCredential'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalMembership'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalOAuth2PermissionGrant'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalOwnedObject'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalOwner'.
VERBOSE: Importing cmdlet 'Get-AzureADServicePrincipalPasswordCredential'.
VERBOSE: Importing cmdlet 'Get-AzureADSubscribedSku'.
VERBOSE: Importing cmdlet 'Get-AzureADTenantDetail'.
VERBOSE: Importing cmdlet 'Get-AzureADTrustedCertificateAuthority'.
VERBOSE: Importing cmdlet 'Get-AzureADUser'.
VERBOSE: Importing cmdlet 'Get-AzureADUserAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Get-AzureADUserCreatedObject'.
VERBOSE: Importing cmdlet 'Get-AzureADUserDirectReport'.
VERBOSE: Importing cmdlet 'Get-AzureADUserExtension'.
VERBOSE: Importing cmdlet 'Get-AzureADUserLicenseDetail'.
VERBOSE: Importing cmdlet 'Get-AzureADUserManager'.
VERBOSE: Importing cmdlet 'Get-AzureADUserMembership'.
VERBOSE: Importing cmdlet 'Get-AzureADUserOAuth2PermissionGrant'.
VERBOSE: Importing cmdlet 'Get-AzureADUserOwnedDevice'.
VERBOSE: Importing cmdlet 'Get-AzureADUserOwnedObject'.
VERBOSE: Importing cmdlet 'Get-AzureADUserRegisteredDevice'.
VERBOSE: Importing cmdlet 'Get-AzureADUserThumbnailPhoto'.
VERBOSE: Importing cmdlet 'Get-CrossCloudVerificationCode'.
VERBOSE: Importing cmdlet 'New-AzureADApplication'.
VERBOSE: Importing cmdlet 'New-AzureADApplicationExtensionProperty'.
VERBOSE: Importing cmdlet 'New-AzureADApplicationKeyCredential'.
VERBOSE: Importing cmdlet 'New-AzureADApplicationPasswordCredential'.
VERBOSE: Importing cmdlet 'New-AzureADApplicationProxyApplication'.
VERBOSE: Importing cmdlet 'New-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Importing cmdlet 'New-AzureADDevice'.
VERBOSE: Importing cmdlet 'New-AzureADDomain'.
VERBOSE: Importing cmdlet 'New-AzureADGroup'.
VERBOSE: Importing cmdlet 'New-AzureADGroupAppRoleAssignment'.
VERBOSE: Importing cmdlet 'New-AzureADMSAdministrativeUnit'.
VERBOSE: Importing cmdlet 'New-AzureADMSApplication'.
VERBOSE: Importing cmdlet 'New-AzureADMSApplicationExtensionProperty'.
VERBOSE: Importing cmdlet 'New-AzureADMSApplicationKey'.
VERBOSE: Importing cmdlet 'New-AzureADMSApplicationPassword'.
VERBOSE: Importing cmdlet 'New-AzureADMSConditionalAccessPolicy'.
VERBOSE: Importing cmdlet 'New-AzureADMSGroup'.
VERBOSE: Importing cmdlet 'New-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Importing cmdlet 'New-AzureADMSIdentityProvider'.
VERBOSE: Importing cmdlet 'New-AzureADMSInvitation'.
VERBOSE: Importing cmdlet 'New-AzureADMSNamedLocationPolicy'.
VERBOSE: Importing cmdlet 'New-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Importing cmdlet 'New-AzureADMSPermissionGrantPolicy'.
VERBOSE: Importing cmdlet 'New-AzureADMSRoleAssignment'.
VERBOSE: Importing cmdlet 'New-AzureADMSRoleDefinition'.
VERBOSE: Importing cmdlet 'New-AzureADServiceAppRoleAssignment'.
VERBOSE: Importing cmdlet 'New-AzureADServicePrincipal'.
VERBOSE: Importing cmdlet 'New-AzureADServicePrincipalKeyCredential'.
VERBOSE: Importing cmdlet 'New-AzureADServicePrincipalPasswordCredential'.
VERBOSE: Importing cmdlet 'New-AzureADTrustedCertificateAuthority'.
VERBOSE: Importing cmdlet 'New-AzureADUser'.
VERBOSE: Importing cmdlet 'New-AzureADUserAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplication'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationExtensionProperty'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationKeyCredential'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationOwner'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationPasswordCredential'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationProxyApplication'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationProxyApplicationConnectorGroup'.
VERBOSE: Importing cmdlet 'Remove-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Importing cmdlet 'Remove-AzureADContact'.
VERBOSE: Importing cmdlet 'Remove-AzureADContactManager'.
VERBOSE: Importing cmdlet 'Remove-AzureADDeletedApplication'.
VERBOSE: Importing cmdlet 'Remove-AzureADDevice'.
VERBOSE: Importing cmdlet 'Remove-AzureADDeviceRegisteredOwner'.
VERBOSE: Importing cmdlet 'Remove-AzureADDeviceRegisteredUser'.
VERBOSE: Importing cmdlet 'Remove-AzureADDirectoryRoleMember'.
VERBOSE: Importing cmdlet 'Remove-AzureADDomain'.
VERBOSE: Importing cmdlet 'Remove-AzureADGroup'.
VERBOSE: Importing cmdlet 'Remove-AzureADGroupAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Remove-AzureADGroupMember'.
VERBOSE: Importing cmdlet 'Remove-AzureADGroupOwner'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSAdministrativeUnit'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSAdministrativeUnitMember'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSApplication'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSApplicationExtensionProperty'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSApplicationKey'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSApplicationOwner'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSApplicationPassword'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSApplicationVerifiedPublisher'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSConditionalAccessPolicy'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSDeletedDirectoryObject'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSGroup'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSIdentityProvider'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSLifecyclePolicyGroup'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSNamedLocationPolicy'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSPermissionGrantPolicy'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSRoleAssignment'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSRoleDefinition'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSScopedRoleMembership'.
VERBOSE: Importing cmdlet 'Remove-AzureADMSServicePrincipalDelegatedPermissionClassification'.
VERBOSE: Importing cmdlet 'Remove-AzureADOAuth2PermissionGrant'.
VERBOSE: Importing cmdlet 'Remove-AzureADServiceAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Remove-AzureADServicePrincipal'.
VERBOSE: Importing cmdlet 'Remove-AzureADServicePrincipalKeyCredential'.
VERBOSE: Importing cmdlet 'Remove-AzureADServicePrincipalOwner'.
VERBOSE: Importing cmdlet 'Remove-AzureADServicePrincipalPasswordCredential'.
VERBOSE: Importing cmdlet 'Remove-AzureADTrustedCertificateAuthority'.
VERBOSE: Importing cmdlet 'Remove-AzureADUser'.
VERBOSE: Importing cmdlet 'Remove-AzureADUserAppRoleAssignment'.
VERBOSE: Importing cmdlet 'Remove-AzureADUserExtension'.
VERBOSE: Importing cmdlet 'Remove-AzureADUserManager'.
VERBOSE: Importing cmdlet 'Reset-AzureADMSLifeCycleGroup'.
VERBOSE: Importing cmdlet 'Restore-AzureADDeletedApplication'.
VERBOSE: Importing cmdlet 'Restore-AzureADMSDeletedDirectoryObject'.
VERBOSE: Importing cmdlet 'Revoke-AzureADSignedInUserAllRefreshToken'.
VERBOSE: Importing cmdlet 'Revoke-AzureADUserAllRefreshToken'.
VERBOSE: Importing cmdlet 'Select-AzureADGroupIdsContactIsMemberOf'.
VERBOSE: Importing cmdlet 'Select-AzureADGroupIdsGroupIsMemberOf'.
VERBOSE: Importing cmdlet 'Select-AzureADGroupIdsServicePrincipalIsMemberOf'.
VERBOSE: Importing cmdlet 'Select-AzureADGroupIdsUserIsMemberOf'.
VERBOSE: Importing cmdlet 'Set-AzureADApplication'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationLogo'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationProxyApplication'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationProxyApplicationConnectorGroup'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationProxyApplicationCustomDomainCertificate'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationProxyApplicationSingleSignOn'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationProxyConnector'.
VERBOSE: Importing cmdlet 'Set-AzureADApplicationProxyConnectorGroup'.
VERBOSE: Importing cmdlet 'Set-AzureADDevice'.
VERBOSE: Importing cmdlet 'Set-AzureADDomain'.
VERBOSE: Importing cmdlet 'Set-AzureADGroup'.
VERBOSE: Importing cmdlet 'Set-AzureADMSAdministrativeUnit'.
VERBOSE: Importing cmdlet 'Set-AzureADMSApplication'.
VERBOSE: Importing cmdlet 'Set-AzureADMSApplicationLogo'.
VERBOSE: Importing cmdlet 'Set-AzureADMSApplicationVerifiedPublisher'.
VERBOSE: Importing cmdlet 'Set-AzureADMSAuthorizationPolicy'.
VERBOSE: Importing cmdlet 'Set-AzureADMSConditionalAccessPolicy'.
VERBOSE: Importing cmdlet 'Set-AzureADMSGroup'.
VERBOSE: Importing cmdlet 'Set-AzureADMSGroupLifecyclePolicy'.
VERBOSE: Importing cmdlet 'Set-AzureADMSIdentityProvider'.
VERBOSE: Importing cmdlet 'Set-AzureADMSNamedLocationPolicy'.
VERBOSE: Importing cmdlet 'Set-AzureADMSPermissionGrantConditionSet'.
VERBOSE: Importing cmdlet 'Set-AzureADMSPermissionGrantPolicy'.
VERBOSE: Importing cmdlet 'Set-AzureADMSRoleDefinition'.
VERBOSE: Importing cmdlet 'Set-AzureADServicePrincipal'.
VERBOSE: Importing cmdlet 'Set-AzureADTenantDetail'.
VERBOSE: Importing cmdlet 'Set-AzureADTrustedCertificateAuthority'.
VERBOSE: Importing cmdlet 'Set-AzureADUser'.
VERBOSE: Importing cmdlet 'Set-AzureADUserExtension'.
VERBOSE: Importing cmdlet 'Set-AzureADUserLicense'.
VERBOSE: Importing cmdlet 'Set-AzureADUserManager'.
VERBOSE: Importing cmdlet 'Set-AzureADUserPassword'.
VERBOSE: Importing cmdlet 'Set-AzureADUserThumbnailPhoto'.
VERBOSE: Importing cmdlet 'Update-AzureADSignedInUserPassword'.
VERBOSE: Importing alias 'Get-AzureADApplicationProxyConnectorGroupMembers'.
VERBOSE: Found AAD user '[email protected]' for SID S-1-5-21-2488401269-1895120637-1421044794-9150
VERBOSE: CheckSidHasAadUser - SUCCESS
VERBOSE: CheckAadUserHasSid - START
VERBOSE: Missing required parameter ObjectId for CheckAadUserHasSid requires ObjectId parameter to be present, skipping
CheckAadUserHasSid
VERBOSE: CheckStorageAccountDomainJoined - START
VERBOSE: Found storage Account 'netsecfileshares' in Resource Group 'rg-FileShare-Test-EastUs-1'
VERBOSE: Storage account netsecfileshares is already joined in domain corp.netsec.com.
VERBOSE: CheckStorageAccountDomainJoined - SUCCESS
VERBOSE: CheckUserRbacAssignment - START
VERBOSE: Populating RepositorySourceLocation property for module AzureAD.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.Azure.AD.CommonLibrary.dll'.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.AzureAD16.Graph.PowerShell.Custom.dll'.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.AzureAD16.Graph.Client.dll'.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.MS.GraphV10.PowerShell.dll'.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.MS.GraphV10.PowerShell.Custom.dll'.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.MS.GraphV10.Client.dll'.
VERBOSE: Loading module from path 'C:\Program
Files\WindowsPowerShell\Modules\AzureAD\2.0.2.140\Microsoft.Open.AzureAD16.Graph.PowerShell.dll'.
VERBOSE: Look up user jon in domain corp.netsec.com
VERBOSE: Look up groups of user S-1-5-21-2488401269-1895120637-1421044794-9150 in domain corp.netsec.com
Debug-AzStorageAccountAuth : CheckUserRbacAssignment - FAILED
At line:1 char:1
+ Debug-AzStorageAccountAuth -StorageAccountName netsecfileshares -Resourc ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException
+ FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,Debug-AzStorageAccountAuth
Debug-AzStorageAccountAuth : The server is not operational
At line:1 char:1
+ Debug-AzStorageAccountAuth -StorageAccountName netsecfileshares -Resourc ...
+ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~
+ CategoryInfo : NotSpecified: (:) [Write-Error], WriteErrorException
+ FullyQualifiedErrorId : Microsoft.PowerShell.Commands.WriteErrorException,Debug-AzStorageAccountAuth
VERBOSE: CheckUserFileAccess - START
VERBOSE: Missing required parameter FilePath for CheckUserFileAccess, skipping CheckUserFileAccess
Summary of checks:
Name Result
---- ------
CheckDomainJoined Passed
CheckGetKerberosTicket Passed
CheckUserRbacAssignment Failed
CheckAadUserHasSid Skipped
CheckADObjectPasswordIsCorrect Passed
CheckADObject Passed
CheckUserFileAccess Skipped
CheckPort445Connectivity Passed
CheckStorageAccountDomainJoined Passed
CheckSidHasAadUser Passed
Issues found:
---- CheckUserRbacAssignment ----
The server is not operational
PS C:\temp\jy\AzFilesHybrid>
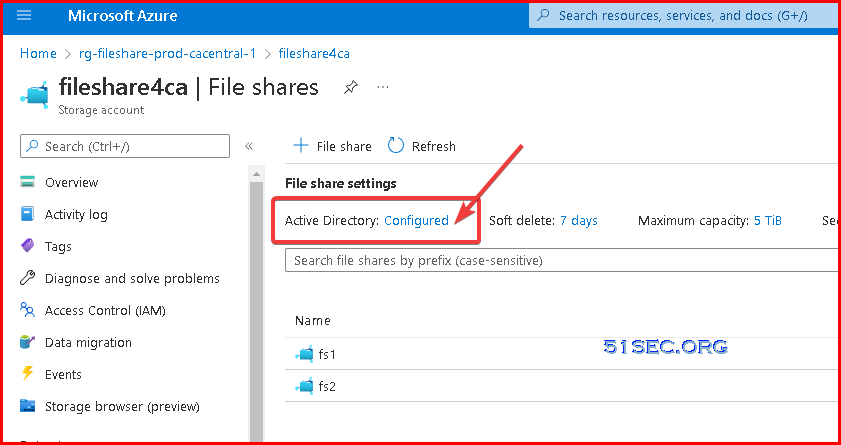
Once this step completed successfully, you should be able to see file shares has been configured with Active Directory.
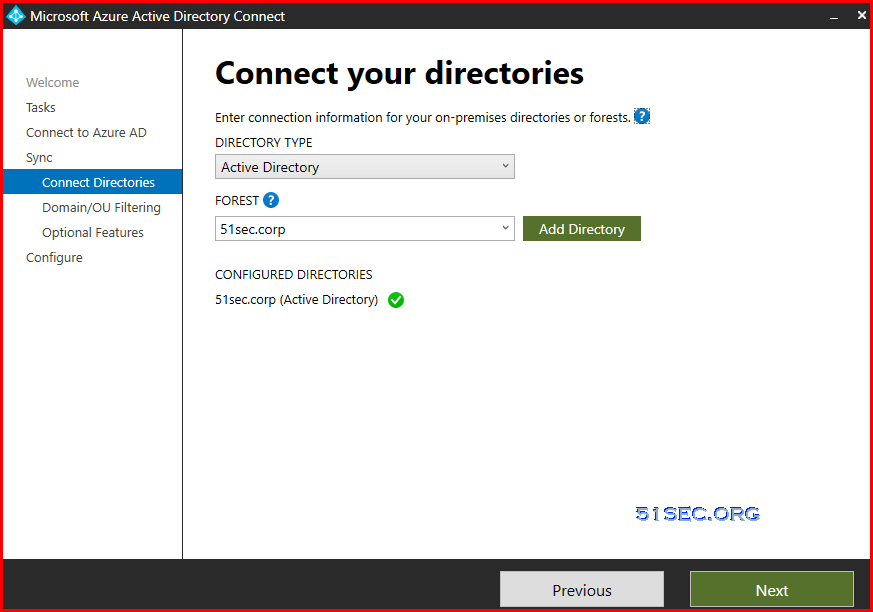
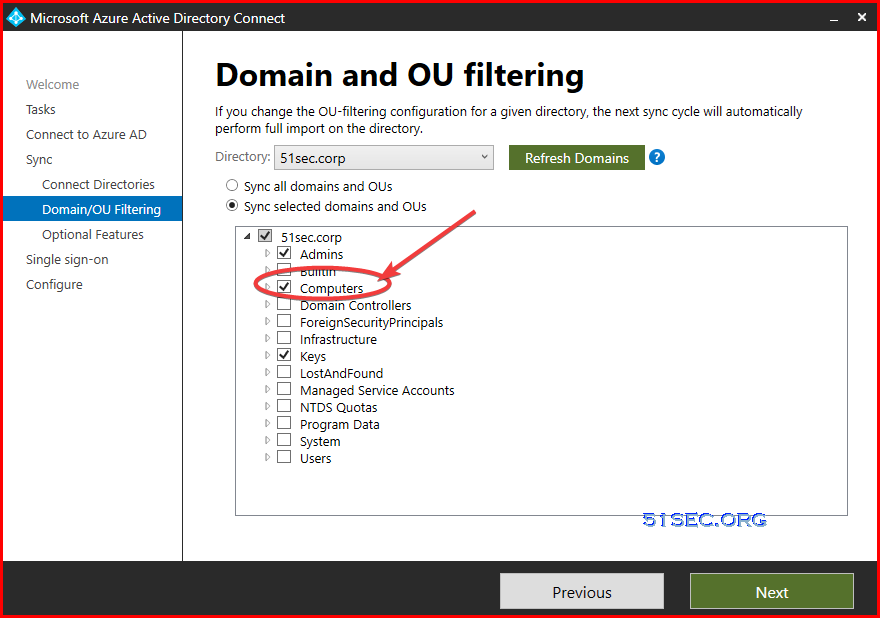
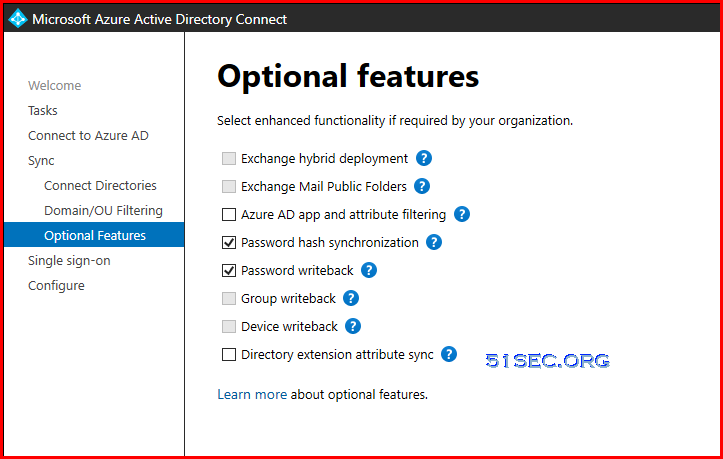
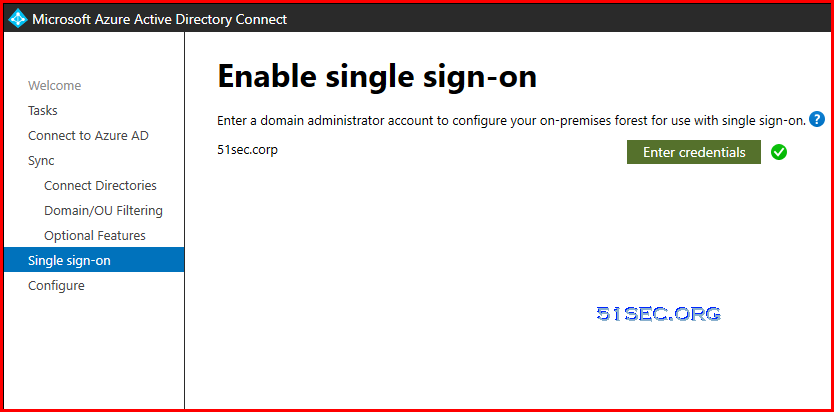
AD Connect Installation and Configuration
Please refer this post for Azure AD connect installation and configuration.
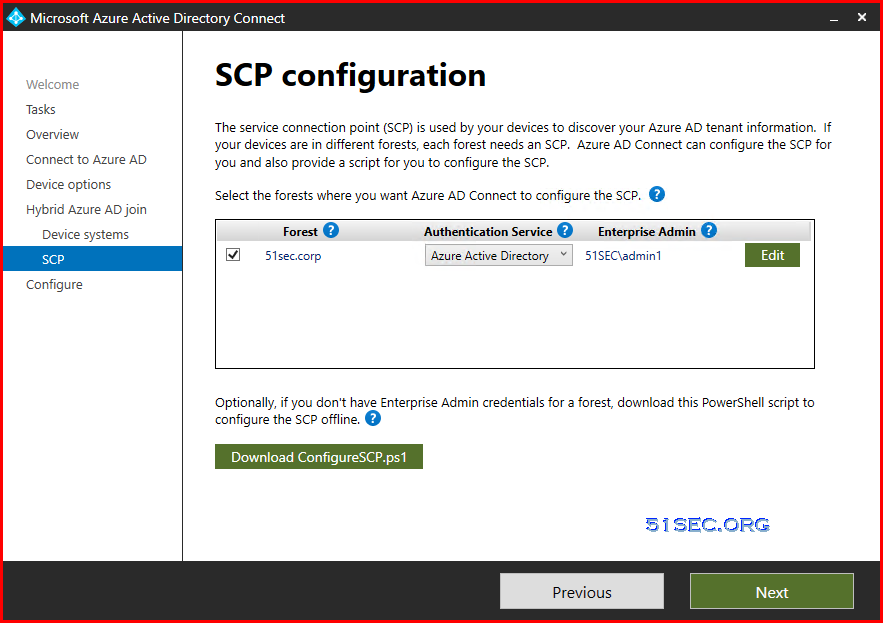
Hybrid Azure AD Joined Device Configuration
Choose Configuredevice options to start configuring Hybrid joined device configuration.
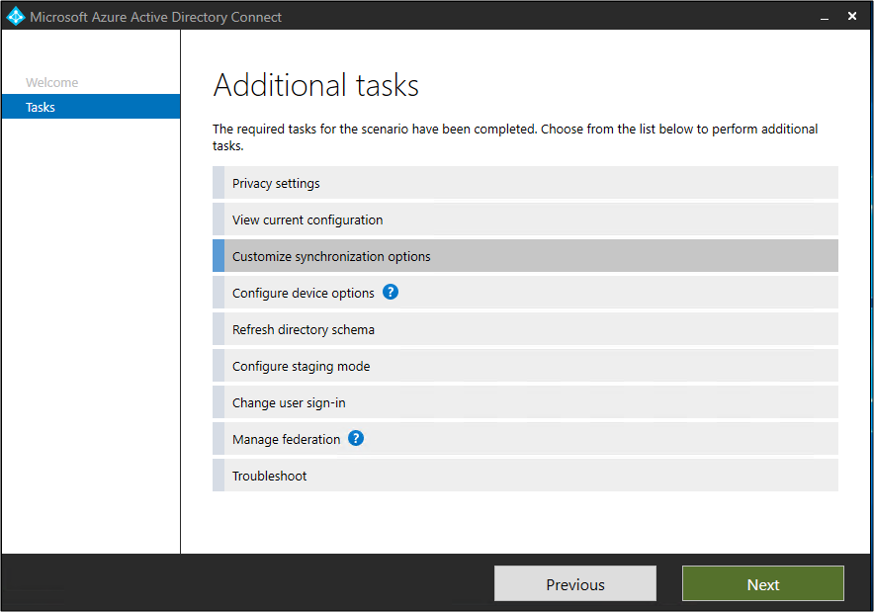
You will need a global admin account to log into Azure AD. Also you will need a local ad account which is part of enterprise admins group to log into local AD.
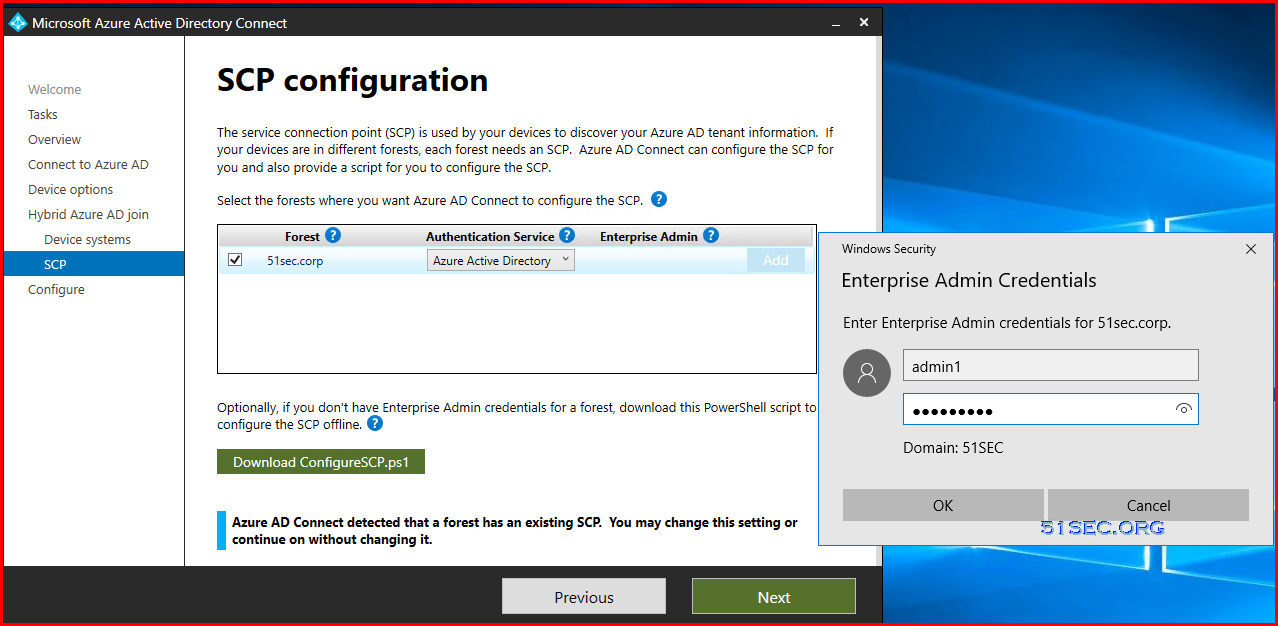
Also make sure you synced computers and users into AAD using Customize Synchronization Options from AD connect.
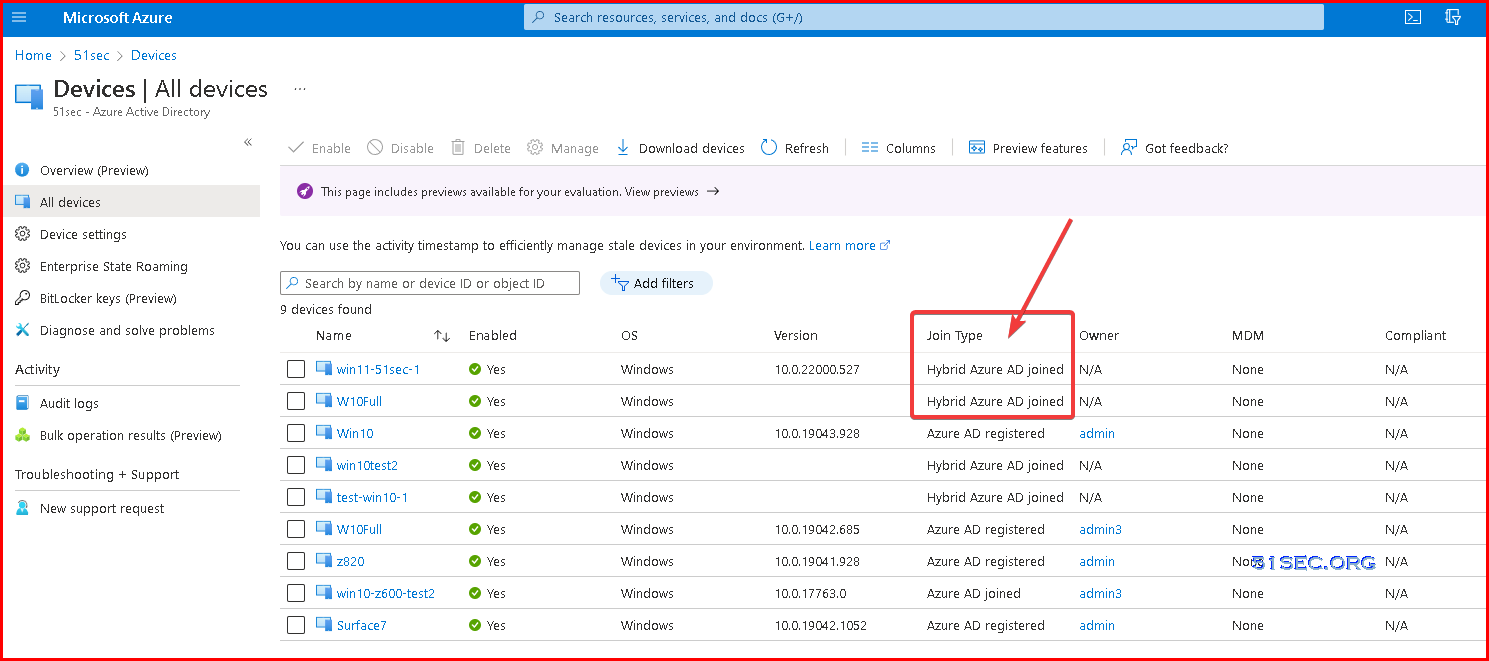
Verification Hybrid Joined Devices.
After a couple of minutes, check your AD joined machine to see if AAD joined enabled.
- from command line
- from AAD devices
Before enabled Hybrid Joined Device:
C:\Users\test1>dsregcmd /status +----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+ AzureAdJoined : NO
EnterpriseJoined : NO
DomainJoined : YES
DomainName : 51SEC
Device Name : win11-51sec-1.51sec.corp +----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+ NgcSet : NO
WorkplaceJoined : NO
WamDefaultSet : NO +----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+ AzureAdPrt : NO
AzureAdPrtAuthority : NO
EnterprisePrt : NO
EnterprisePrtAuthority : NO +----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+ Diagnostics Reference : www.microsoft.com/aadjerrors
User Context : UN-ELEVATED User
Client Time : 2022-03-28 02:27:38.000 UTC
AD Connectivity Test : PASS
AD Configuration Test : FAIL [0x80070005]
DRS Discovery Test : SKIPPED
DRS Connectivity Test : SKIPPED
Token acquisition Test : SKIPPED
Fallback to Sync-Join : ENABLED Previous Registration : 2022-03-28 02:04:01.000 UTC
Registration Type : sync
Error Phase : join
Client ErrorCode : 0x801c03f3
Server ErrorCode : invalid_request
Server ErrorSubCode : error_missing_device
Server Operation : DeviceRenew
Server Message : The device object by the given id (ca565a27-6db8-4a55-9e5e-d96427e8cd2e) is not found.
Https Status : 400
Request Id : 04bb2d88-30f9-44cc-a456-d84ca34dcf16
Executing Account Name : WIN11-51SEC-1\test1 +----------------------------------------------------------------------+
| IE Proxy Config for Current User |
+----------------------------------------------------------------------+ Auto Detect Settings : YES
Auto-Configuration URL :
Proxy Server List :
Proxy Bypass List : +----------------------------------------------------------------------+
| WinHttp Default Proxy Config |
+----------------------------------------------------------------------+ Access Type : DIRECT +----------------------------------------------------------------------+
| Ngc Prerequisite Check |
+----------------------------------------------------------------------+ IsDeviceJoined : NO
IsUserAzureAD : NO
PolicyEnabled : NO
PostLogonEnabled : YES
DeviceEligible : YES
SessionIsNotRemote : YES
CertEnrollment : none
PreReqResult : WillNotProvision For more information, please visit https://www.microsoft.com/aadjerrors
C:\Users\test1>
After enabled Hybrid Joined Device:
C:\Users\test1>dsregcmd /status
+----------------------------------------------------------------------+
| Device State |
+----------------------------------------------------------------------+
AzureAdJoined : YES
EnterpriseJoined : NO
DomainJoined : YES
DomainName : 51SEC
Device Name : win11-51sec-1.51sec.corp
+----------------------------------------------------------------------+
| Device Details |
+----------------------------------------------------------------------+
DeviceId : ca565a27-6db8-4a55-9e5e-d96427e8cd2e
Thumbprint : 014E8C97B0A2553E6B32F3A03B7C931F290A3652
DeviceCertificateValidity : [ 2022-03-28 01:57:43.000 UTC -- 2032-03-28 02:27:43.000 UTC ]
KeyContainerId : 7eacafad-c157-472f-8834-f011bafa97c3
KeyProvider : Microsoft Platform Crypto Provider
TpmProtected : YES
DeviceAuthStatus : SUCCESS
+----------------------------------------------------------------------+
| Tenant Details |
+----------------------------------------------------------------------+
TenantName :
TenantId : 8ed8617a-5de3-44d8-a8f4-737c89fa9bbc
AuthCodeUrl : https://login.microsoftonline.com/8ed8617a-5de3-44d8-a8f4-737c89fa9bbc/oauth2/authorize
AccessTokenUrl : https://login.microsoftonline.com/8ed8617a-5de3-44d8-a8f4-737c89fa9bbc/oauth2/token
MdmUrl :
MdmTouUrl :
MdmComplianceUrl :
SettingsUrl :
JoinSrvVersion : 2.0
JoinSrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/device/
JoinSrvId : urn:ms-drs:enterpriseregistration.windows.net
KeySrvVersion : 1.0
KeySrvUrl : https://enterpriseregistration.windows.net/EnrollmentServer/key/
KeySrvId : urn:ms-drs:enterpriseregistration.windows.net
WebAuthNSrvVersion : 1.0
WebAuthNSrvUrl : https://enterpriseregistration.windows.net/webauthn/8ed8617a-5de3-44d8-a8f4-737c89fa9bbc/
WebAuthNSrvId : urn:ms-drs:enterpriseregistration.windows.net
DeviceManagementSrvVer : 1.0
DeviceManagementSrvUrl : https://enterpriseregistration.windows.net/manage/8ed8617a-5de3-44d8-a8f4-737c89fa9bbc/
DeviceManagementSrvId : urn:ms-drs:enterpriseregistration.windows.net
+----------------------------------------------------------------------+
| User State |
+----------------------------------------------------------------------+
NgcSet : NO
WorkplaceJoined : NO
WamDefaultSet : NO
+----------------------------------------------------------------------+
| SSO State |
+----------------------------------------------------------------------+
AzureAdPrt : NO
AzureAdPrtAuthority :
EnterprisePrt : NO
EnterprisePrtAuthority :
+----------------------------------------------------------------------+
| Diagnostic Data |
+----------------------------------------------------------------------+
AadRecoveryEnabled : NO
Executing Account Name : WIN11-51SEC-1\test1
KeySignTest : PASSED
+----------------------------------------------------------------------+
| IE Proxy Config for Current User |
+----------------------------------------------------------------------+
Auto Detect Settings : YES
Auto-Configuration URL :
Proxy Server List :
Proxy Bypass List :
+----------------------------------------------------------------------+
| WinHttp Default Proxy Config |
+----------------------------------------------------------------------+
Access Type : DIRECT
+----------------------------------------------------------------------+
| Ngc Prerequisite Check |
+----------------------------------------------------------------------+
IsDeviceJoined : YES
IsUserAzureAD : NO
PolicyEnabled : NO
PostLogonEnabled : YES
DeviceEligible : YES
SessionIsNotRemote : YES
CertEnrollment : none
PreReqResult : WillNotProvision
For more information, please visit https://www.microsoft.com/aadjerrors
C:\Users\test1>
Windows Client Configuration
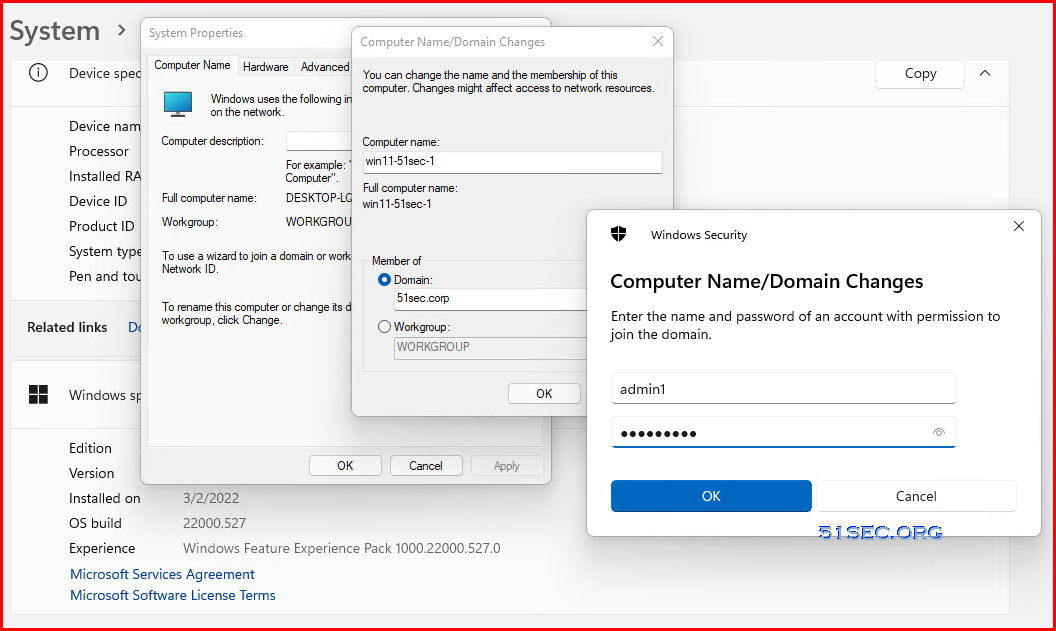
Please make sure your Windows client machine joined local AD DS.
If your Windows client machine is not having direct connection to your local AD DC, you will need a vpn to connect back to your AD DC.
There is a challenge to get your remote workgroup machine to join into your local onprem AD, even with VPN installed and connected.
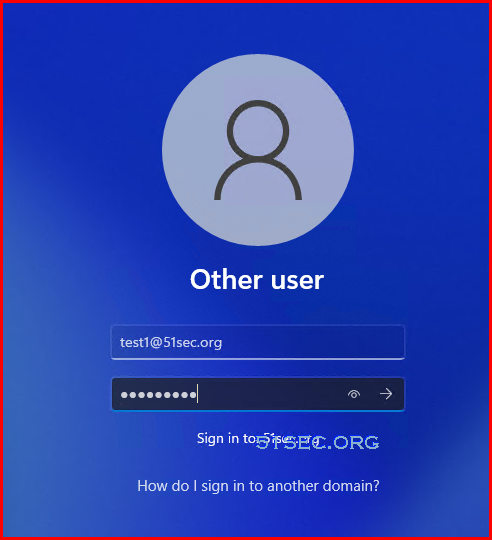
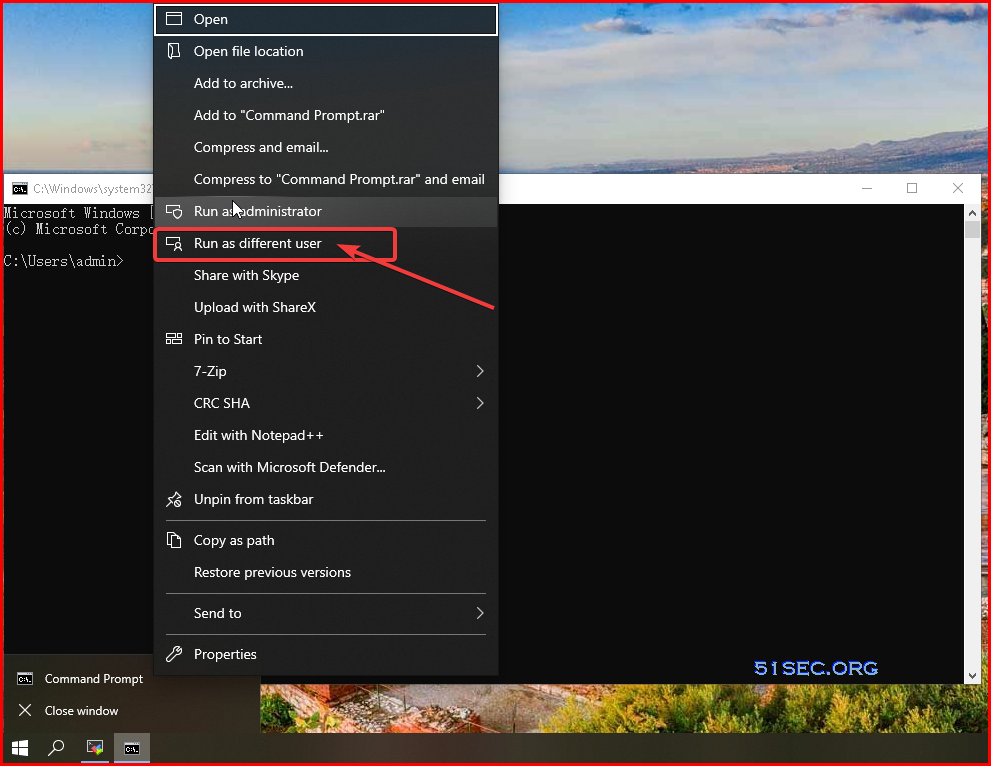
Before you log in to your machine using your AD account, you will have to log in your machine using local admin account and shift right click an application to open it using a different user. That will allow system to create a Domain user profile to allow this domain user to log in without a connection to AD DC.
Following screenshot is an example of CMD application.
Azure Point to Site (P2S) VPN Configuration
If your Internet ISP blocked port 445, you will need to create a Azure VPN Gateway to create a tunnel to have your client machine connecting to your File Shares. You might also need to create private end point for your storage account.
- Point-to-Site (P2S) VPN gateway connections, which are VPN connections between Azure and an individual client. This solution is primarily useful for devices that are not part of your organization's on-premises network, such as telecommuters who want to be able to mount their Azure file share from home, a coffee shop, or hotel while on the road. To use a P2S VPN connection with Azure Files, a P2S VPN connection will need to be configured for each client that wants to connect. To simplify the deployment of a P2S VPN connection, see Configure a Point-to-Site (P2S) VPN on Windows for use with Azure Files and Configure a Point-to-Site (P2S) VPN on Linux for use with Azure Files.
In addition to the default public endpoint for a storage account, Azure Files provides the option to have one or more private endpoints. A private endpoint is an endpoint that is only accessible within an Azure virtual network. When you create a private endpoint for your storage account, your storage account gets a private IP address from within the address space of your virtual network, much like how an on-premises file server or NAS device receives an IP address within the dedicated address space of your on-premises network.
An individual private endpoint is associated with a specific Azure virtual network subnet. A storage account may have private endpoints in more than one virtual network.
Please refer following post to configure your P2S VPN.
Mount File Shares
Mount the file share from a domain-joined VM
The following process verifies that your file share and access permissions were set up correctly and that you can access an Azure file share from a domain-joined VM. Be aware that the share-level Azure role assignment can take some time to take effect.
Sign in to the domain-joined VM using the Azure AD identity to which you granted permissions. Be sure to sign in with Azure AD credentials. If the drive is already mounted with the storage account key, you'll need to disconnect the drive or sign in again.
Run the PowerShell script below or use the Azure portal to persistently mount the Azure file share and map it to drive Z: on Windows. If Z: is already in use, replace it with an available drive letter. Because you've been authenticated, you won't need to provide the storage account key. The script will check to see if this storage account is accessible via TCP port 445, which is the port SMB uses. Remember to replace <storage-account-name> and <file-share-name> with your own values. For more information, see Use an Azure file share with Windows.
Always mount Azure file shares using file.core.windows.net, even if you set up a private endpoint for your share. Using CNAME for file share mount isn't supported for identity-based authentication.
$connectTestResult = Test-NetConnection -ComputerName <storage-account-name>.file.core.windows.net -Port 445
if ($connectTestResult.TcpTestSucceeded) {
cmd.exe /C "cmdkey /add:`"<storage-account-name>.file.core.windows.net`" /user:`"localhost\<storage-account-name>`""
New-PSDrive -Name Z -PSProvider FileSystem -Root "\\<storage-account-name>.file.core.windows.net\<file-share-name>" -Persist
} else {
Write-Error -Message "Unable to reach the Azure storage account via port 445. Check to make sure your organization or ISP is not blocking port 445, or use Azure P2S VPN, Azure S2S VPN, or Express Route to tunnel SMB traffic over a different port."
}
Mount the file share from a non-domain-joined VM
Non-domain-joined VMs can access Azure file shares using Azure AD DS authentication only if the VM has line-of-sight to the domain controllers for Azure AD DS, which are located in Azure. This usually requires setting up a site-to-site or point-to-site VPN to allow this connectivity. The user accessing the file share must have an identity and credentials (an Azure AD identity synced from Azure AD to Azure AD DS) in the Azure AD DS managed domain.
When mounting the file share, the user must provide explicit credentials such as DOMAINNAME\username where DOMAINNAME is the Azure AD DS domain and username is the identity’s user name in Azure AD DS. This will help route Kerberos ticket requests from the client to the correct domain controller in the Azure AD DS domain.
Mount the Azure file share with File Explorer
Open File Explorer by opening it from the Start Menu, or by pressing the Win+E shortcut.
Navigate to This PC on the left-hand side of the window. This will change the menus available in the ribbon. Under the Computer menu, select Map network drive.

Select the drive letter and enter the UNC path to your Azure file share. The UNC path format is
\\<storageAccountName>.file.core.windows.net\<fileShareName>. For example:\\anexampleaccountname.file.core.windows.net\file-share-name. Check the Connect using different credentials checkbox. Select Finish.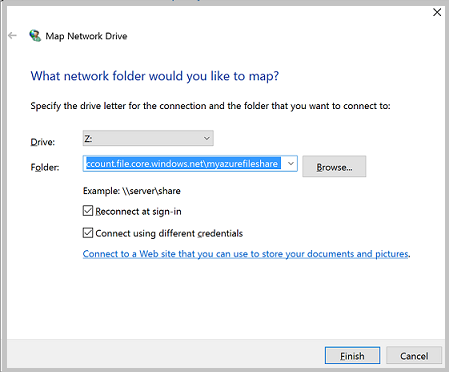
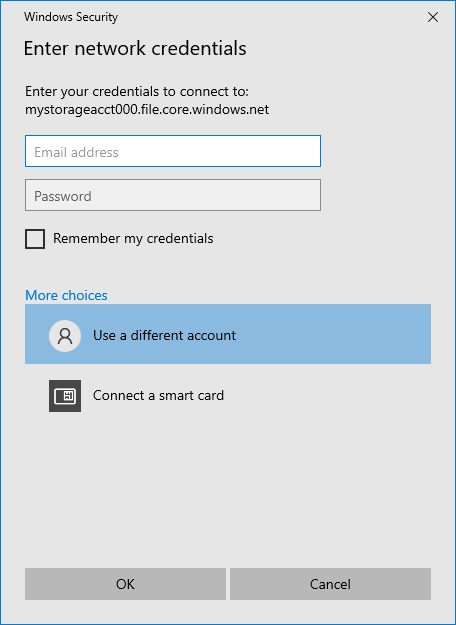
Select More choices > Use a different account. Under Email address, use the storage account name, and use a storage account key as the password. Select OK.
Use Azure file share as desired.
When you're ready to dismount the Azure file share, right-click on the entry for the share under the Network locations in File Explorer and select Disconnect.
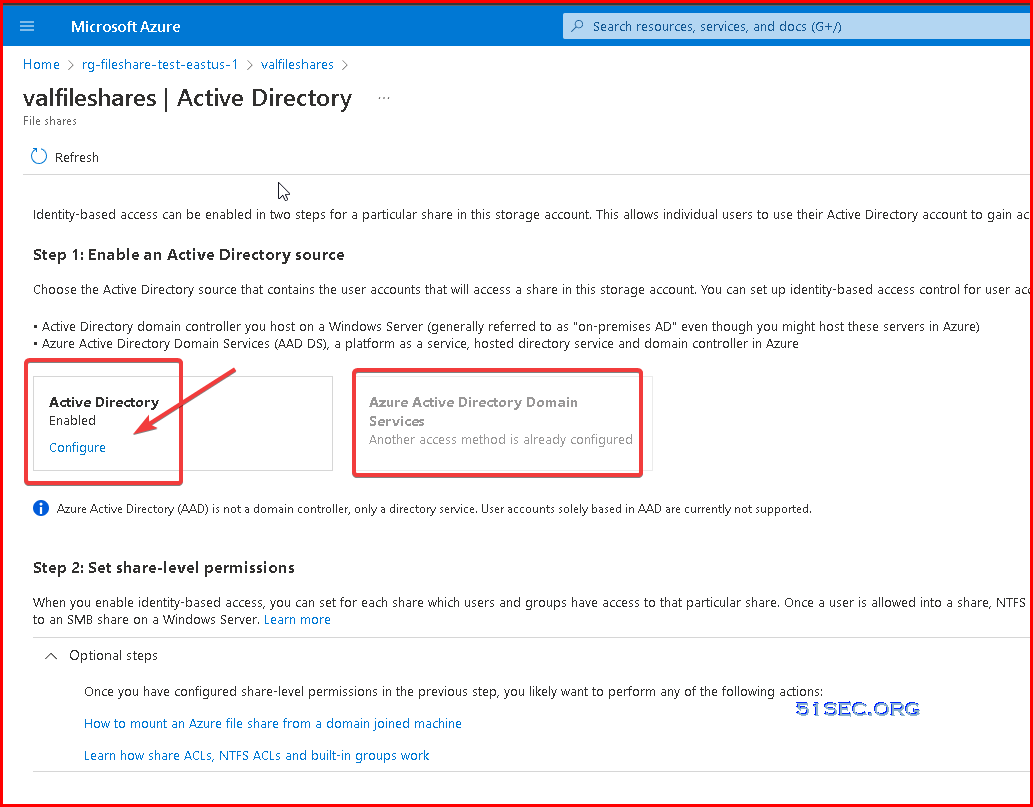
Notes
- For Azure File Shares, you can only choose your Active Diretory source either from local AD DS or from Azure AD DS. Following screenshot is an example which enabled to intergrate with local AD DS
- Azure Files Identity-Based Authentication Options for SMB Access
How to remove cached credentials with storage account key and delete existing SMB connections before initializing new connection with Azure AD or AD credentials?
You can follow the two step process below to remove the saved credential associated with the storage account key and remove the SMB connection:
Run the cmdlet below in Windows Cmd.exe to remove the credential. If you cannot find one, it means that you have not persisted the credential and can skip this step.
cmdkey /delete:Domain:target=storage-account-name.file.core.windows.net
Delete the existing connection to the file share. You can specify the mount path as either the mounted drive letter or the storage-account-name.file.core.windows.net path.
net use <drive-letter/share-path> /delete
- P2S VPN Home User Not able to resolve private endpoint ip (for example, storage account's file shares : .file.core.Windows.net) to your private IP
Some posts might suggest to modify VPN client XML file to include DNS server configuration and DNS suffix recorrs, but home router's dns will still resolve .file.core.windows.net to a public ip.
To resolve issue:
- Configure a DNS VM or enable Private DNS resolver (SaaS)
- Configure a new zone to resolve ,file.core.windows.net with your storage account's name to an internal private ip
- If home user's ethernet interface's network metric value is lower than P2S interface's metric value, change P2S interfae's metric vaule to lower. For example, default P2S interface metric is 45, ethernet is 25, so you might want to change to change your p2s interface metric value to 20 or lower.
References:
1. https://learn.microsoft.com/en-us/answers/questions/938429/how-to-resolve-private-dns-zone-names-while-using.html
2. How to configure the DNS servers in the config file.
References
- Overview - on-premises Active Directory Domain Services authentication over SMB for Azure file shares
- Azure Point-to-Site VPN Configuration
- Using Azure AD to Log Into Computer and Assign Share Folder Permission
- Remote AAD Joined Machine Access Azure Storage File Share Using Cloud Tiering
- Install Azure AD Connect to Integrate On-Prem ADFS with AAD (Hybrid Identity)
- Mount Azure Blob Storage into Local Windows File System
- Deploy Azure File Sync on Cloud VM and Mount Azure File Share to Machine Without Port 445
- Mount Azure Cloud VM File Share Folder With Tcp Port 445 Blocked By ISP
- Setup Hybrid Azure Active Directory John and Login For Your Client Machines









No comments:
Post a Comment