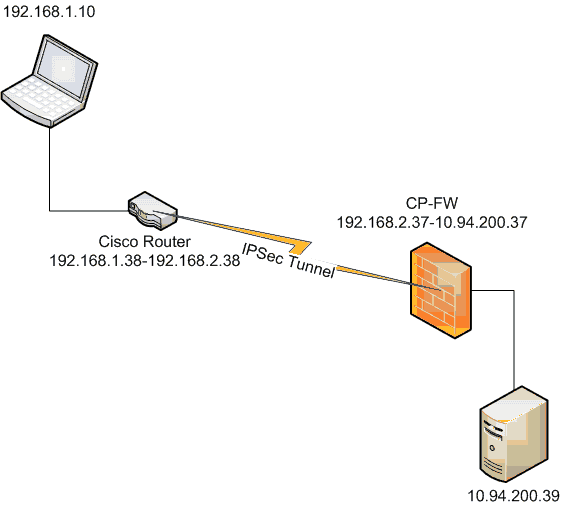
1. Checkpoint configuration
a. Set up Checkpoint Gateway IPv4 address as the peer address showing in the cisco router.
b. Create a new Interoperable Device for Cisco Router
d. Pre-shared key
e. Advanced ISAKMP Configurations and IPSec Configurations
f. Set up access-list
2. Cisco Router Configuration
crypto isakmp policy 10encr aes 256
authentication pre-share
group 2
crypto isakmp key cisco1234 address 192.168.2.37
!
crypto ipsec transform-set VPN1 esp-aes esp-sha-hmac
!
crypto map VPN-MAP 10 ipsec-isakmp
set peer 192.168.2.37
set transform-set VPN1
match address ACL-VPN
!
interface GigabitEthernet0/0
ip address 192.168.2.38 255.255.255.0
crypto map VPN-MAP
ip route 10.94.200.0 255.255.255.0 192.168.2.37
!
ip access-list extended ACL-VPN
permit ip 192.168.1.0 0.0.0.255 10.94.200.0 0.0.0.255
!














No comments:
Post a Comment