[Privacy] Four Steps to Achieve your Effective Data Privacy Program
Netsec
6/01/2025
0 Comments
With a veritable explosion of data breaches highlighted almost daily across the globe, and the introduction of heavy-handed privacy laws and...
Read More
![[Privacy] Four Steps to Achieve your Effective Data Privacy Program](https://i.51sec.org/2025/POWERPNT_sTM1a02z3n.png)




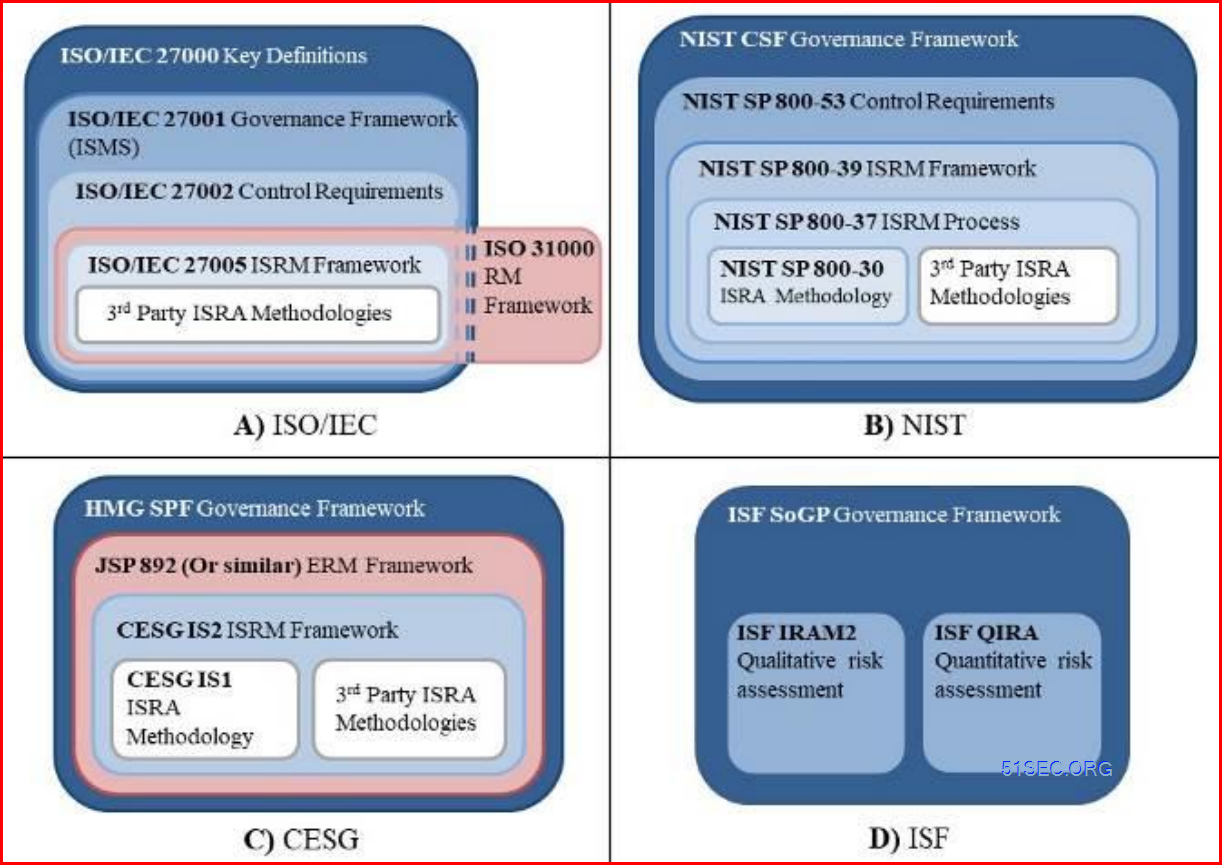



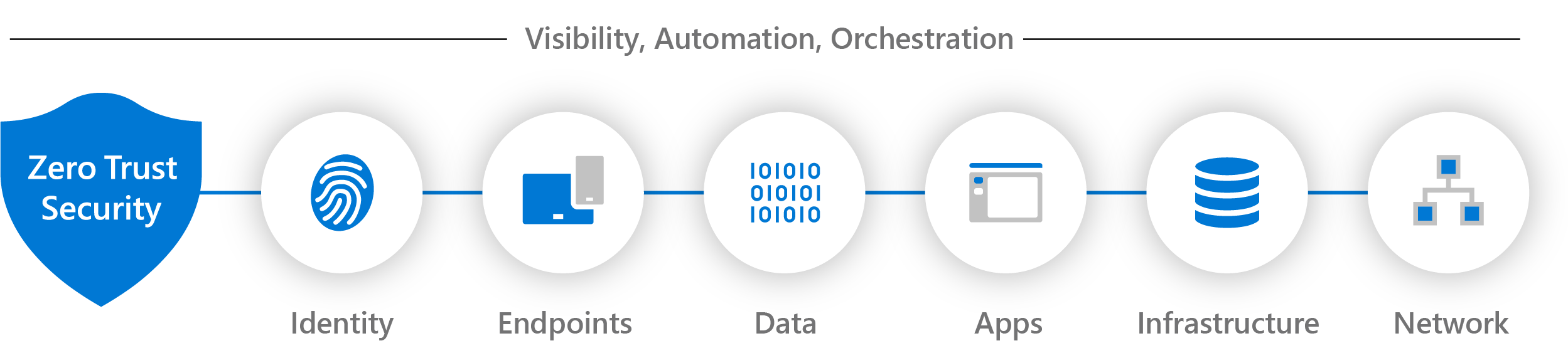



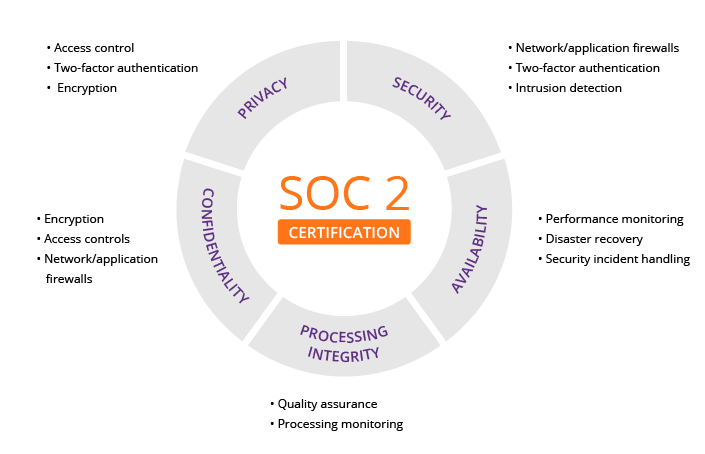
![[Cybersecurity Architecture] KPI, Metrics & Dashboards](https://i.imgur.com/8sOhcMI.png)

![[Cybersecurity Architecture] Strategic Planning & Roadmap Examples & Tools](https://i.imgur.com/q5nB6S5.png)
![[Cybersecurity Architecture] TOGAF Knowledges Collection](https://p.51sec.org/file/netsec/2023/02/chrome_GKxKnhby7A.png)






