 One of the challenges in configuring firewall policies is the fact
that they rely on IP addresses and IP subnets rather than users or user groups.
In particular for next generation firewalls, that provide services like URL
filtering, there is a need to have policies based on users and user groups
rather than IP addresses. The Palo Alto UserID service provides a mapping
between users and the IP addresses they use. The service also maintains a list
of AD groups and keeps it in sync with the AD domain controllers. The UserID
agent is using the Windows login event logs to identify the current IP used by
a user. The specific Security event records the user id and the IP address
where the login comes from. The UserID agent is also capable of retrieving this
type of information from other authentication services but in our case we will
only use the AD logins. Since the users may login using any of the DCs in the
domain, the UserID agents has to poll all the domain controllers. In order to
compile the required information, the UserID agent needs the right to query the
AD users and their AD group membership, as well as the ability to read the Windows
Security event logs for events related to logins.
One of the challenges in configuring firewall policies is the fact
that they rely on IP addresses and IP subnets rather than users or user groups.
In particular for next generation firewalls, that provide services like URL
filtering, there is a need to have policies based on users and user groups
rather than IP addresses. The Palo Alto UserID service provides a mapping
between users and the IP addresses they use. The service also maintains a list
of AD groups and keeps it in sync with the AD domain controllers. The UserID
agent is using the Windows login event logs to identify the current IP used by
a user. The specific Security event records the user id and the IP address
where the login comes from. The UserID agent is also capable of retrieving this
type of information from other authentication services but in our case we will
only use the AD logins. Since the users may login using any of the DCs in the
domain, the UserID agents has to poll all the domain controllers. In order to
compile the required information, the UserID agent needs the right to query the
AD users and their AD group membership, as well as the ability to read the Windows
Security event logs for events related to logins.Topology
Palo Alto UserID Agent Configure Steps
Simplified Steps:
- Create
an AD account for the User-ID agent.
- On the
Windows server that is the agent host, configure a group policy to allow
the account configured at step 1 to log on as a service. The logon as a
service can also be granted just to the local computer by going to Local
Policies -> User Rights Assignments -> Log on as a service
- Add the
new account to the Event Log Reader builtin group (since the account needs
to access the Security event logs)
- Assign
the account R/W permissions to the folder where the agent is installed. By
default this is C:\Program Files(x86)\Palo Alto Networks. This allows the
account to read and change the configuration files.
- Give
the service account permissions to the User-ID Agent registry sub-tree:
- 32-bit
systems—HKEY_LOCAL_MACHINE\Software\Palo Alto Networks
- 64-bit
systems—HKEY_LOCAL_MACHINE\Software\WOW6432Node\Palo Alto Networks
- Disable
service account privileges that are not required:
- Deny
interactive logon for the User-ID service account
- Deny
remote access for the User-ID service account
Step 1 - Create an AD account for the
User-ID agent.
You must create a service account in your
domain that the agent will monitor.
1. Log in to the domain controller.
2. Right-click the Windows icon , Search for Active Directory Users and Computers, and launch the application.
3. In the navigation pane, open the domain tree,
right-click Managed Service Accounts and select NewUser.
(If your company does not use the above OU for service account, please create
it under the Users OU)
4. Enter the First Name, Last Name,
and User logon name of the user and click Next.
5. Enter the Password and Confirm
Password, then click Next and Finish.
username – panfwagent
PW - set
yourself and share
6. Keep this account password as never expire.
Step 2 - Add the account to the Builtin groups that
have privileges for accessing the services and hosts the User-ID agent will
monitor.
1. Right-click the service account you just added
and Add to a group.
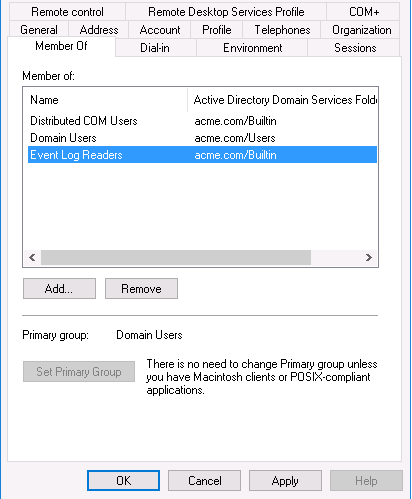 2. Enter the object names to select as follows to assign the account to groups.
Separate each entry with a semicolon.
2. Enter the object names to select as follows to assign the account to groups.
Separate each entry with a semicolon.
o
Event Log Readers or a custom group that has privileges for
reading Security log events. These privileges are required if the User-ID agent
will collect mapping information by monitoring Security logs.
o
Distributed COM Users group, which has privileges for launching,
activating, and using Distributed Component Object Model (DCOM) objects.
3. Check Names to
validate your entries and click OK twice.
YouTube Videos:
References
The PA User-Id Agent requires a dedicated AD service account:
- Configure service account: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/user-id/map-ip-addresses-to-users/create-a-dedicated-service-account-for-the-user-id-agent.html(Note: Skip Step 3)
- Configure user mapping: https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/user-id/map-ip-addresses-to-users/configure-user-mapping-using-the-windows-user-id-agent/install-the-windows-based-user-id-agent.html
- User ID Agent Compatibility Matrix: https://docs.paloaltonetworks.com/compatibility-matrix/user-id-agent.html
Configure the Windows-Based User-ID Agent for User Mapping







No comments:
Post a Comment