 Working on LogRhythm - Cloud SIEM project. LogRhythm's SIEM solution combines enterprise log management, security analytics, user entity and behavioral analytics (UEBA), network traffic and behavioral analytics (NTBA) and security automation and orchestration. That integrated approach can make for efficient security operations, from threat detection to incident response.
Working on LogRhythm - Cloud SIEM project. LogRhythm's SIEM solution combines enterprise log management, security analytics, user entity and behavioral analytics (UEBA), network traffic and behavioral analytics (NTBA) and security automation and orchestration. That integrated approach can make for efficient security operations, from threat detection to incident response.Because SIEM is a core security infrastructure with access to data from across the enterprise, there are a large variety of SIEM use cases. Below are common SIEM use case examples, from traditional uses such as compliance, to cutting edge use cases such as insider threat detection and IoT security.
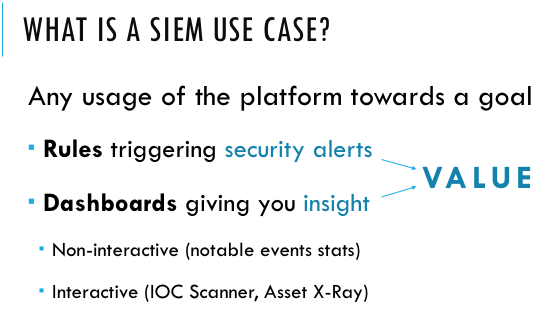
A List for Use Cases
| 1 | Single User Adding Multiple Accounts to Privileged Group(S) | 8 |
| 2 | Audit Disabled by Admin | 8 |
| 3 | Actioned Terminated/Disabled Account Activity | 8 |
| 4 | Distributed Brute Force Authentication Success (Windows) | 7 |
| 5 | Lateral Movement with Account Sweep | 7 |
| 6 | Concurrent VPN from Multiple Locations | 7 |
| 7 | Windows RunAs Privilege Escalation | 7 |
| 8 | Attack then Outbound Connection | 7 |
| 9 | User/Configuration Changes outside business hours | 7 |
| 10 | Configuration or Policy Change | 7 |
| 11 | Exfiltration: Large Outbound Transfer | 6 |
| 12 | Domain Password Policy was changed | 6 |
| 13 | P2P Activity Detected | 6 |
| 14 | Privileged Account Authentication Failures outside Business Hours | 6 |
| 15 | Temporary Account Used | 6 |
| 16 | Account and Group Management Activity | 6 |
| 17 | Authentication after Security Event | 5 |
| 18 | Critical/Error Alert | 5 |
| 19 | Spamming Bot | 5 |
| 20 | Suspicious Outbound Web Traffic Detected | 5 |
| 21 | Internal Distributed Authentication Failure | 4 |
| 22 | Expired/Disabled VPN Login Attempt | 4 |
| 23 | Pivot Behaviour - Windows Service | 4 |
| 24 | Internal Attack then Account Creation | 4 |
| 25 | Repeated Attacks against Host | 4 |
| 26 | Data Exfiltration | 4 |
| 27 | Single User Being Added to Multiple Unique Privileged Groups | 3 |
| 28 | Malware Outbreak | 3 |
| 29 | Privileged Account Authentication Activity | 3 |
| 30 | Antivirus Failure | 2 |
| 31 | Malware: Not Cleaned | 2 |
| 32 | User Privilege/Permission Changes on database | 2 |







No comments:
Post a Comment