- SEP's Layers Protection Technologies
- Mgmt Failover and Load Balancing
- Multiple Sites Design
- Difference between user mode and computer mode
SEP's Layers Protection Technologies
1: Network-based protectionNetwork Threat Protection:
■ Firewall
■ Protocol-aware IPS Virus and Spyware Protection:
■ Browser protection
2: File-based protection
Virus and Spyware Protection:
■ Antivirus engine
■ Auto-Protect
■ Bloodhound
3: Reputation-based protection
Virus and Spyware Protection:
■ Domain reputation score
■ File reputation (Insight)
4: Behavioral-based protection
■ Proactive Threat Protection (Virus and Spyware Protection policy): SONAR
5: Repair and remediation tools
Power Eraser:
■ Boot to clean operating system
■ Power Eraser uses aggressive heuristics
■ Threat-specific tools
6: Exploit mitigation
Generic Exploit Mitigation
7: Others
System Lockdown
Application control
Device control
Mgmt Failover and Load Balancing
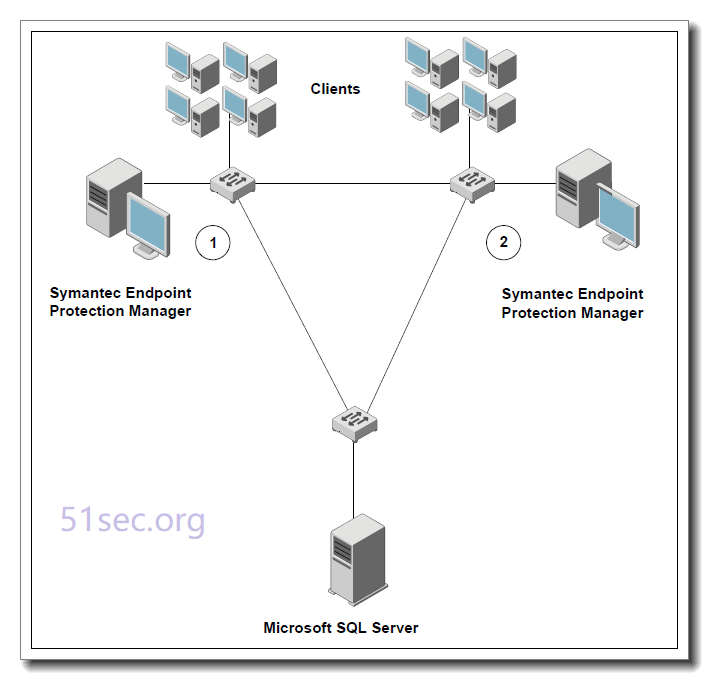
Failover configurations are used to maintain communication when clients cannot communicate with a Symantec Endpoint Protection Manager. Load balancing is used to distribute client management between management servers. You can configure failover and load balancing by assigning priorities to management servers in management server lists.You can install two or more management servers that communicate with one Microsoft SQL Server database and configure them for failover or load balancing. Since you can install only one Symantec Endpoint Protection Manager to communicate with the embedded database, you can set up failover only if you
Managing failover and load balancing replicate with another site. When you use replication with an embedded database, Symantec recommends that you do not configure load balancing, as data
inconsistency and loss may result.
By default, the management servers are assigned the same priority when configured for failover and load balancing. You can only configure load balancing when a site includes more than one management server.
Three methods to provide both load balancing and roaming:
■ Enable DNS and put a domain name as the only entry in a custom management server list.
■ Enable the Symantec Endpoint Protection location awareness feature and use a custom management server list for each location. Create at least one location for each of your sites.
■ Use a hardware device that provides failover or load balancing. Many of these devices also offer a setup for roaming.
Load balancing occurs between the servers that are assigned to priority 1 in a management server list. If more than one server is assigned to priority 1, the clients randomly choose one of the servers and establish communication with it. If all priority 1 servers fail, clients connect with the server assigned to priority 2.
Using different priority, mgmt server can do failover. If all mgmt servers are same priority, they are working on load balancing mode.
Typical Failover/Load balancing Design
One MS SQL server , not embedded version
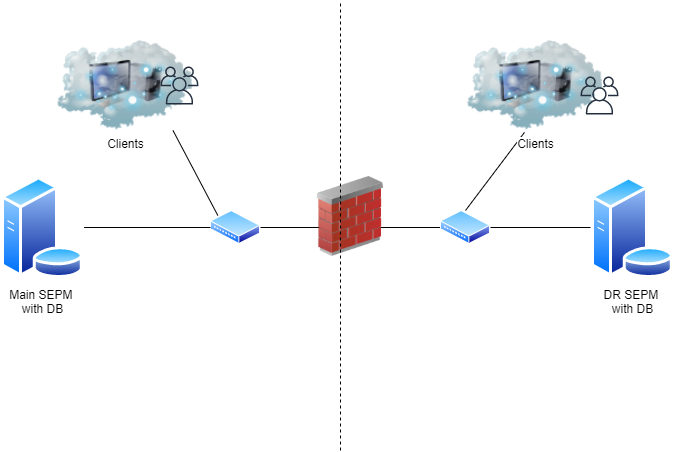
Multiple Sites Design
Or using two embedded MS SQL servers with multiple Sites.
Replication enables data to be duplicated between databases on separate sites so that both databases contain the same information. If one database fails, you can manage each site by using the information on the database from the second site.
Replication partners can use either an embedded database or a Microsoft SQL Server database. If you use an embedded database, you can only connect one Symantec Endpoint Protection Manager. If you use the Microsoft SQL Server database, you can connect multiple management servers that share one database. Only one of the management servers needs to be set up as a replication partner.
Failover with different priorities
Load balanceing with same priority
For example, you may want to set up one site at your main office (site 1) and a second site (site 2). Site 2 is a partner to site 1. The databases on site 1 and site 2 are reconciled by using the replication schedule. If a change is made on site 1, it automatically appears on site 2 after replication occurs. If a change is made on site 2, it automatically appears on site 1 after replication occurs.
Note: when do Replicate Now from SEPM -> Admin -> Servers -> Replication Partners -> Site 51SEC-BCP-SEPM1, it is always from remote (51SEC-BCP-SEPM1) to local SEPM server.
Difference between user mode and computer mode
Check these Articles:
About user mode and computer mode
Understanding computer and user mode in Symantec Endpoint Protection
You can set up clients as users or computers, depending on how you want the policies to work. Clients that are set up as users are in user mode. Clients that are set up as computers are in computer mode. Clients that are set up as users are based on the name of the user who logs on to the network. Clients that are set up as computers are based on the computer that logs on to the network. You set up clients as users or computers by adding the users and computers to an existing group. After a user or a computer is added to a group, it assumes the policies that were assigned to the group.
The policies that are in force depend on the mode in which the client software runs:
Computer mode
The client protects the computer with the same policies, regardless of which user is logged on to the computer. The policy follows the group that the computer is in. Computer mode is the default setting.
User mode
User mode
The policies change, depending on which user is logged on to the client. The policy follows the user.
If the client software runs in user mode, the client computer software gets the policies from the group of which the user is a member. If the client software runs in computer mode, the client gets the policies from the group of which the computer is a member.
After you add a computer, it defaults to computer mode. Computer mode always takes precedence








asdwrwe
ReplyDelete