Privilege Manager’s toolset is two-fold. First, Local Security discovers all accounts that exist on endpoints and allows Privilege Manager Administrators to control the exact membership of every local group. This will ensure the correct admin and root accounts are permanently set. Additionally, credentials will be controlled by enforcing password rotation on those accounts.
Second, Application Control allows Privilege Manager administrators to manage application activity on endpoint machines. Applications that require admin rights or root access can be automatically elevated, allowed applications are allow listed, and malicious applications are blocked.
Every implementation looks different when configuring Privilege Manager to work best for your organization. This post is to summarize some of examples to set up right policies in Privilege Manager application.
Related Post:
Best Practices
The following topics are available:
- Disaster Recovery
- Active Directory Import
- Using a Service Account to run the IIS App pool
- Prevent Read and Write Access to File Types or Locations
- Securing the IIS Server
- Updating to higher security algorithms
Notes:
Privilege Manager local accounts should be managed by Thycotic Secret Server.
License expired, the existing policies and new created policies will still wor, but not events.
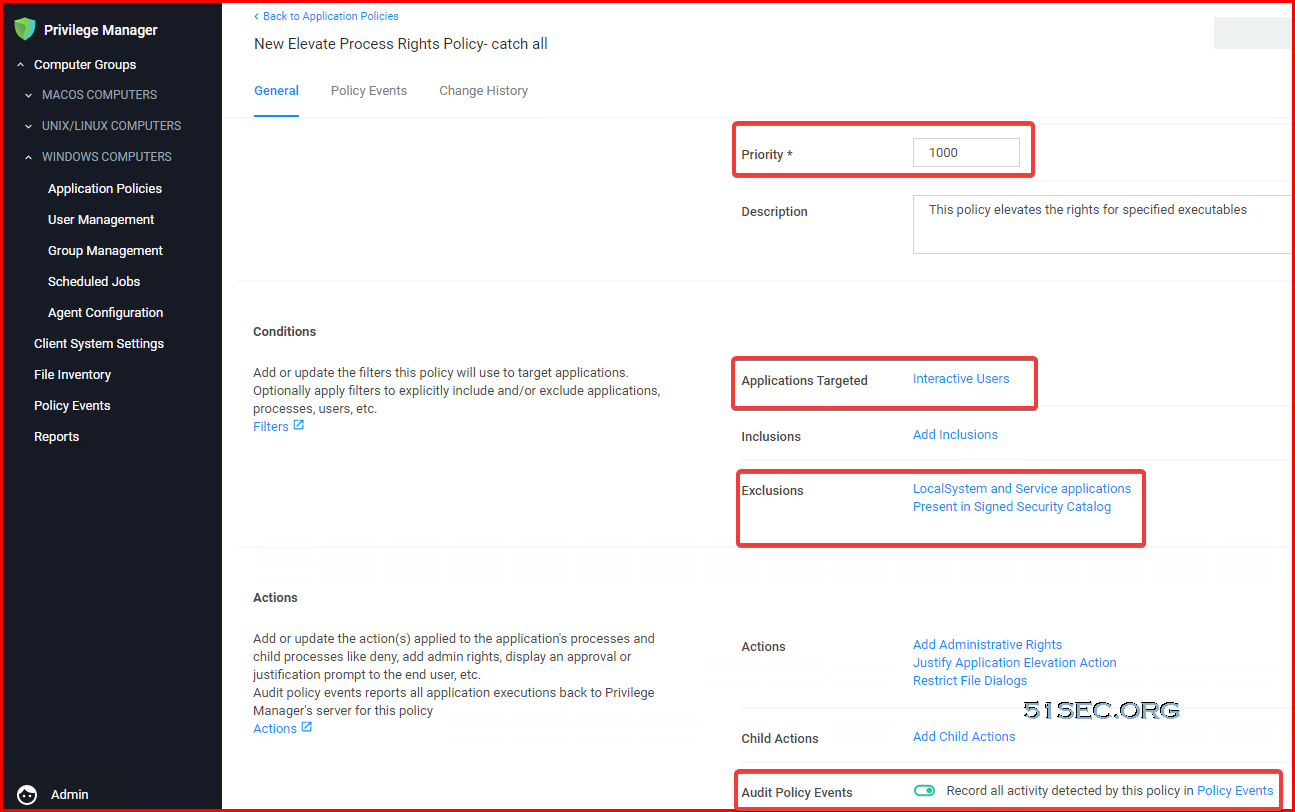
Catch All Policy
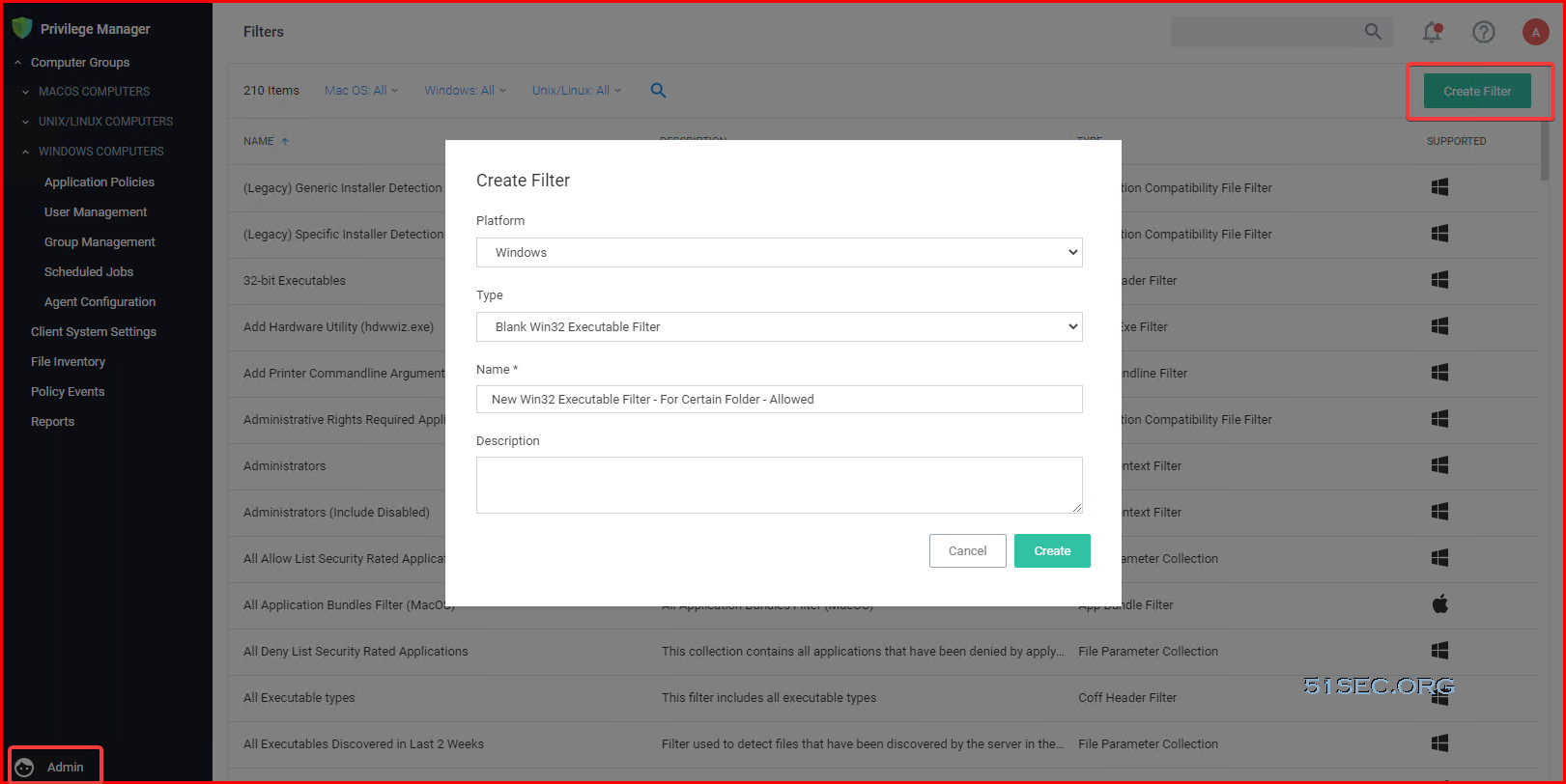
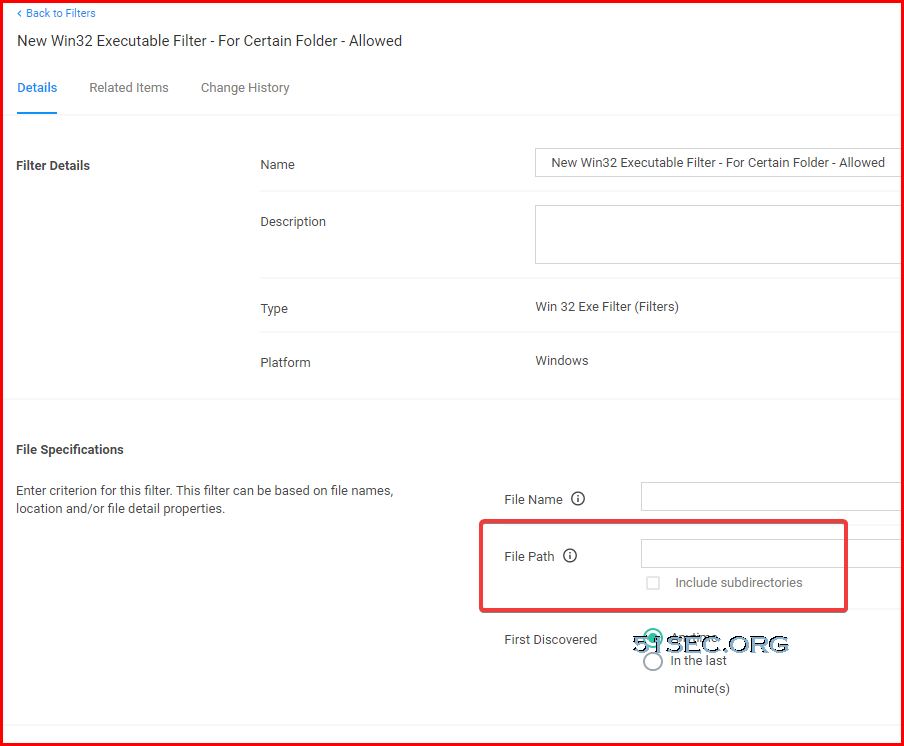
Custom Filter for Allowed Folder / Applications
To allow any application in certain folder to run, it requires to create a custom filter:
Then create an Allow policy:
- Setting up priority
- Change it to active
- Enable Auditing.
Set up Target Groups for your Policy
Policy Examples
Windows Computers - Application Policies
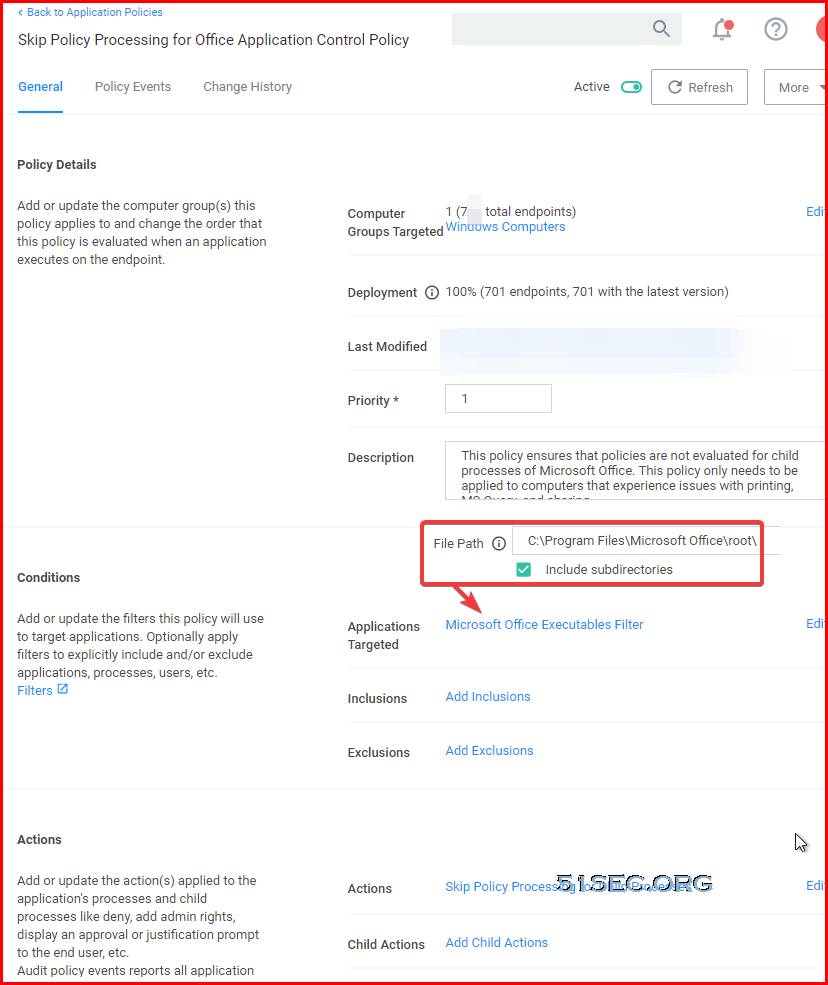
1. Unknow Type:- Skip Policy Processing for Office Application Control Policy
2. Allow
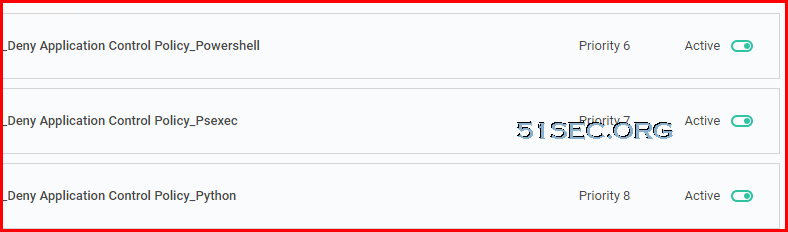
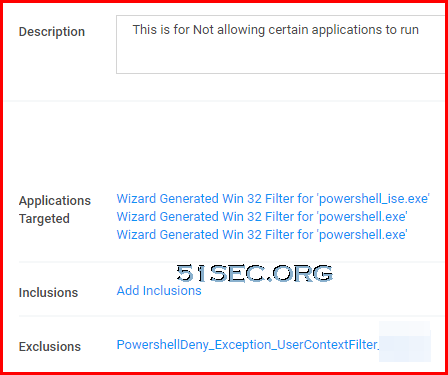
- Application Control Policy - Allow PowerShell, Psexec, Python for certain group users
3. Block
- Low priority Allow policy
- Elevate Process Rights Policy _BigIPClientInstaller
- This policy elevates the security rights for specified applications
- File name : BIGIPEdgeClient.exe
- Type: Win 32 Exe Filter (Filters)
6. Monitor
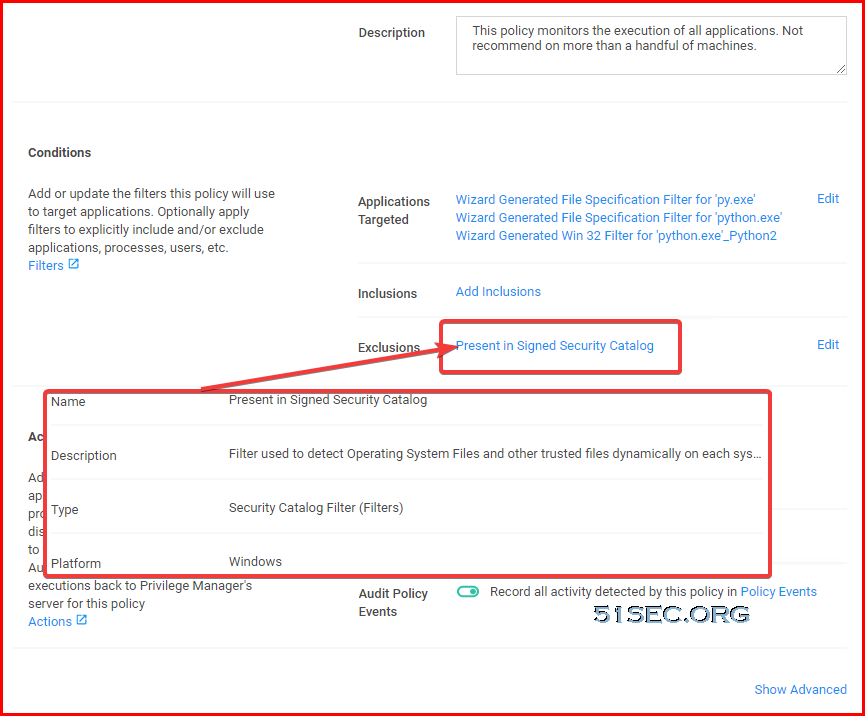
- Monitor Policy for Application - Python








No comments:
Post a Comment