This post summarize the configuration for allowing Point-2-site vpn users to access your remote peering network.
Related Post::
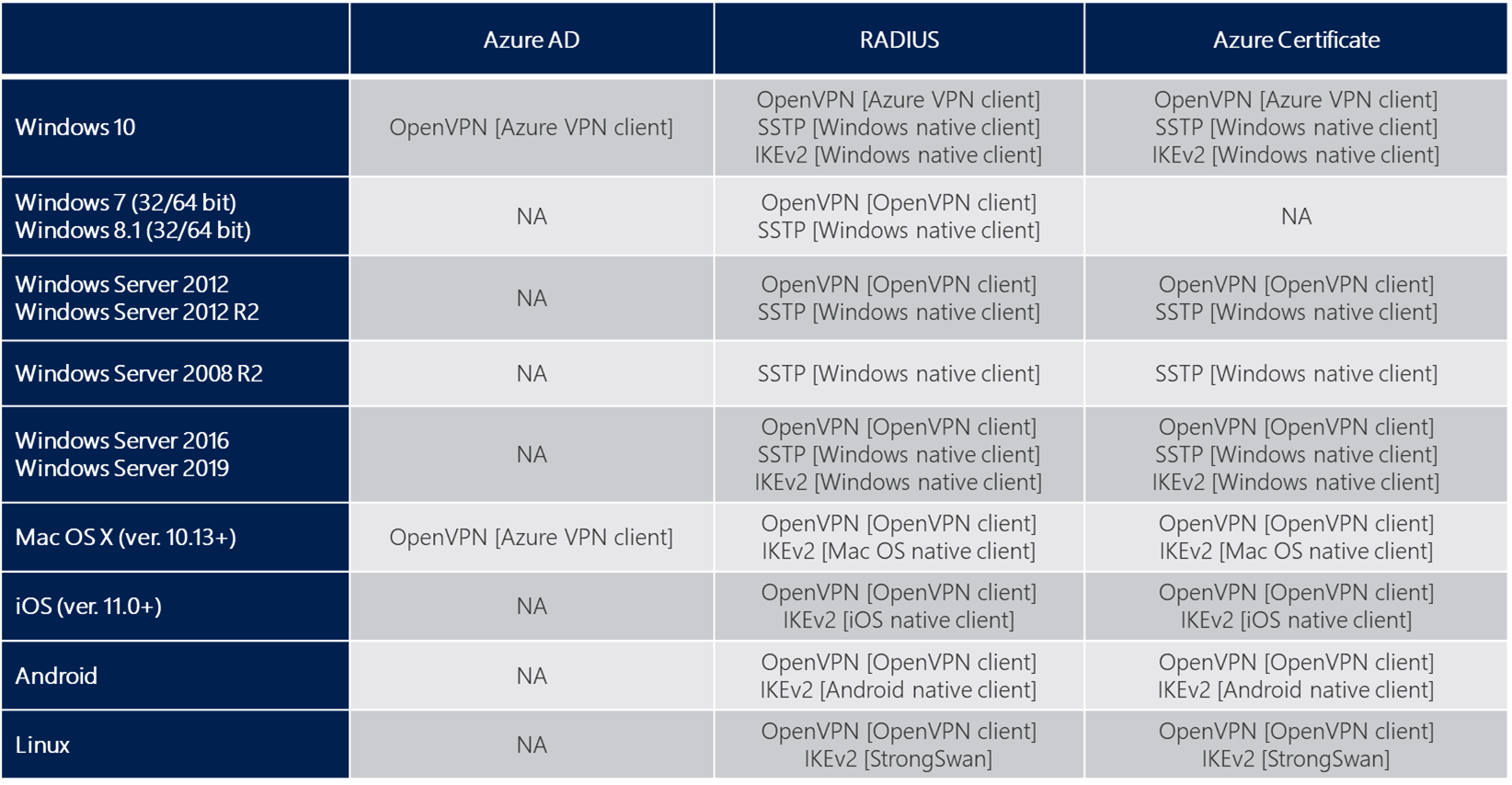
Diagram and Protocols
Azure supports three types of Point-to-site VPN options:
Secure Socket Tunneling Protocol (SSTP). SSTP is a Microsoft proprietary SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses.
OpenVPN. OpenVPN is a SSL-based solution that can penetrate firewalls since most firewalls open the outbound TCP port that 443 SSL uses.
IKEv2 VPN. IKEv2 VPN is a standards-based IPsec VPN solution that uses outbound UDP ports 500 and 4500 and IP protocol no. 50. Firewalls don't always open these ports, so there's a possibility of IKEv2 VPN not being able to traverse proxies and firewalls.
Steps to Configure Peering
Azure supports the following types of peering:
Virtual network peering: Connecting virtual networks within the same Azure region.
Global virtual network peering: Connecting virtual networks across Azure regions.
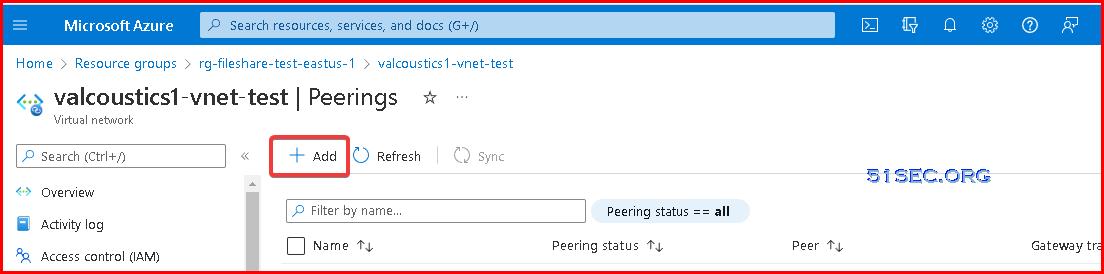
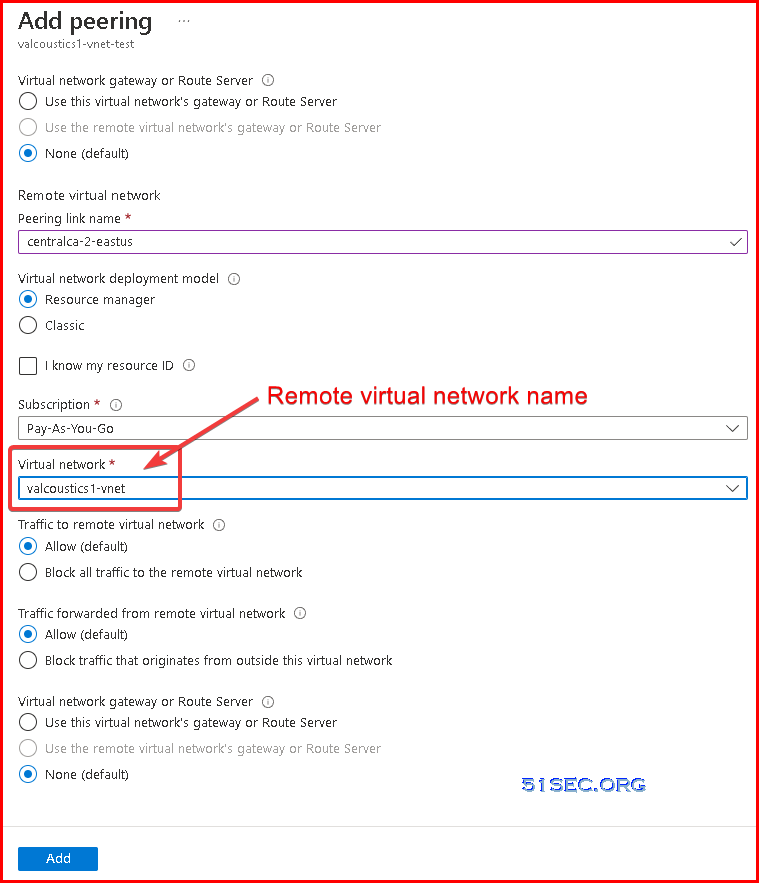
1 Go to your Azure virtual network, choose Peerings from left panel
2 Click add button
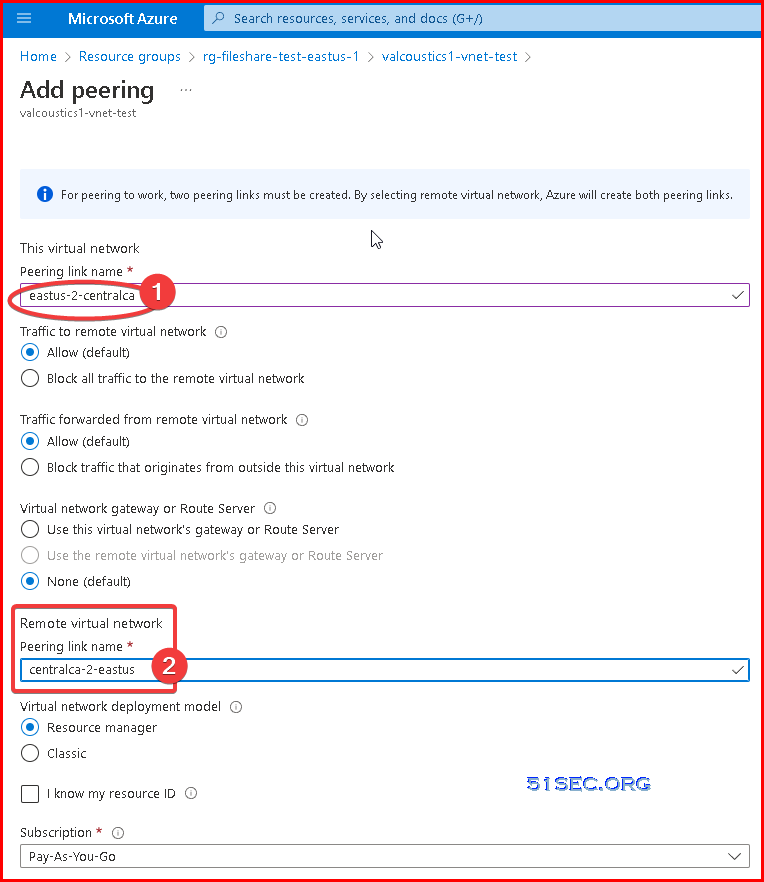
3 Enter local peering link name and remote peering link name. Azure will create two links for you in this one time setup.
4 Choose remote virtual network name
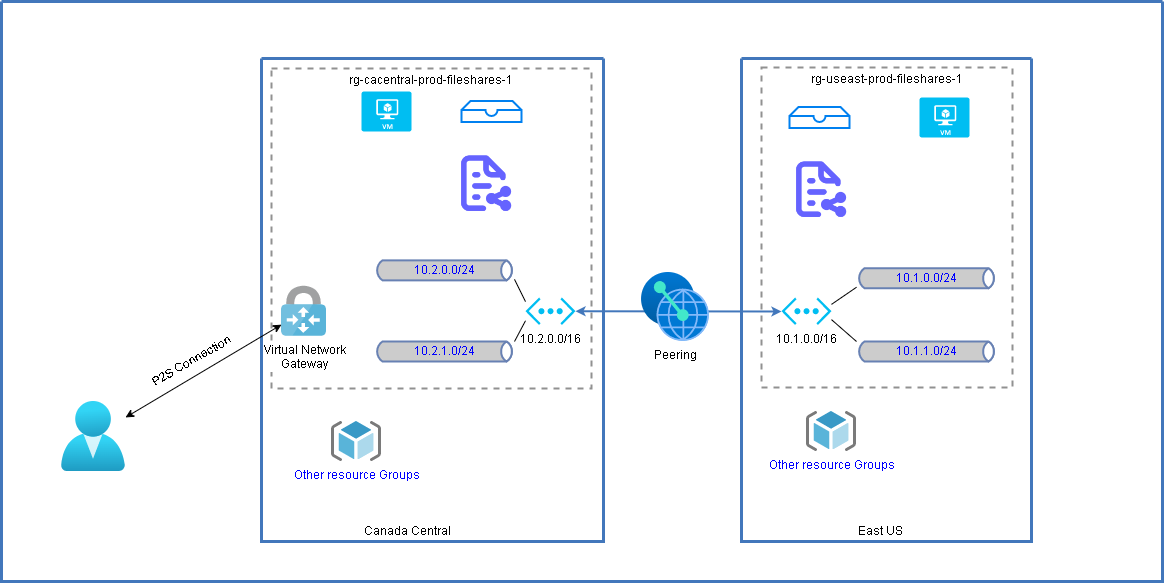
Once you completed peering, the VMs can talk each other in those two virtual networks (10.1.0.0/16 and 10.2.0.0/16) without further configuration.
Configure Peering Links
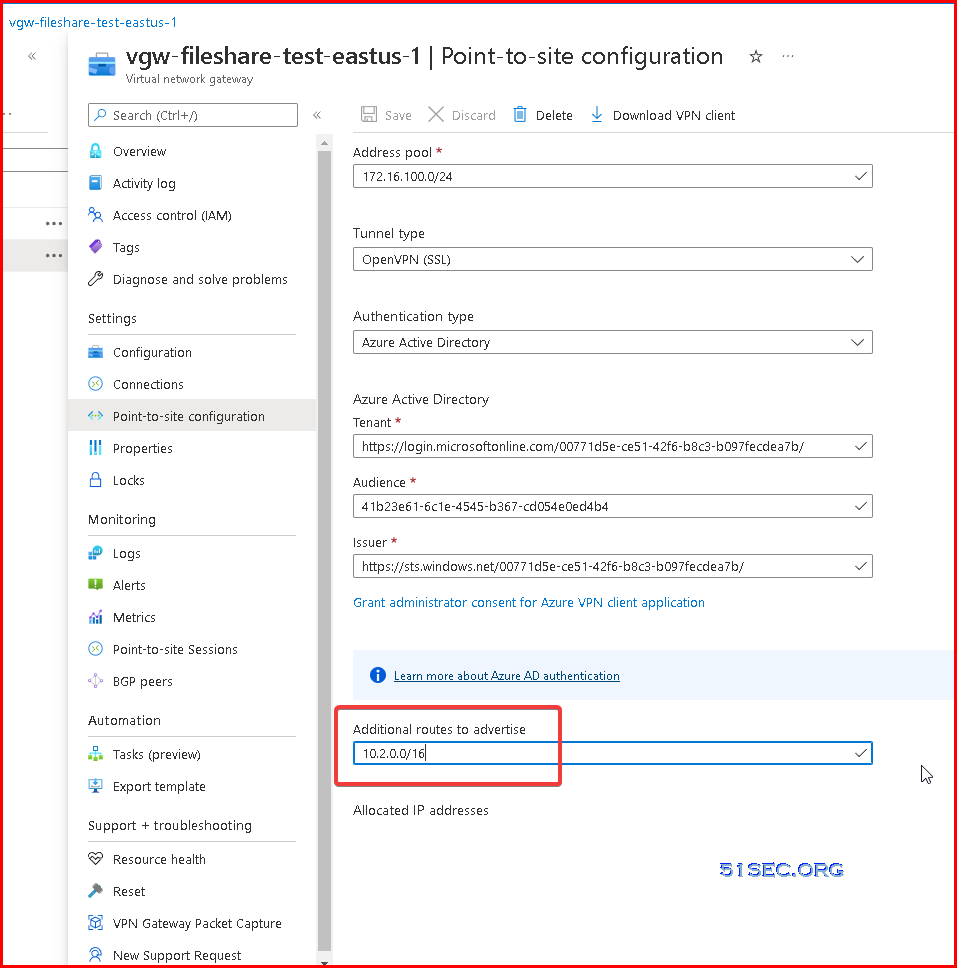
1 Add a route for peering network into Virtual Network Gateway ConfigurationNext step is to change gateway for both peering network.
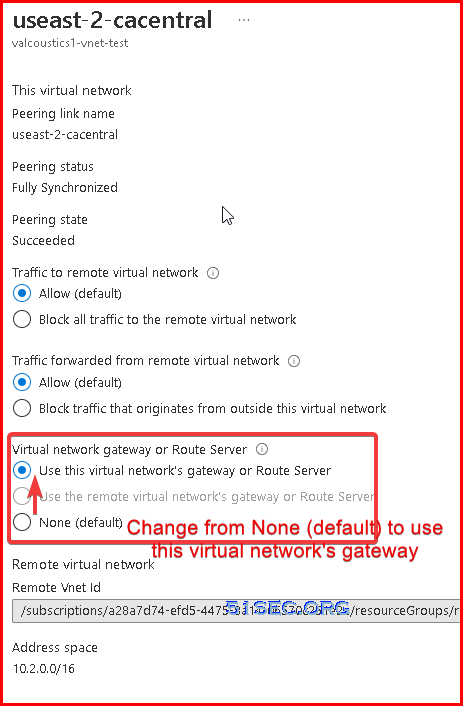
2 Change Peering configuration on local )
This will allow P2S users to access your remote peering network.Explanation for Virtual network gateway or Route server:
- Dynamic routes for virtual machines in a virtual network are programmed by virtual network gateways or Route Servers. Additionally, a virtual network gateway routes traffic between on-premises networks and Azure virtual networks. A virtual network gateway can be created for either VPN Gateway or ExpressRoute.
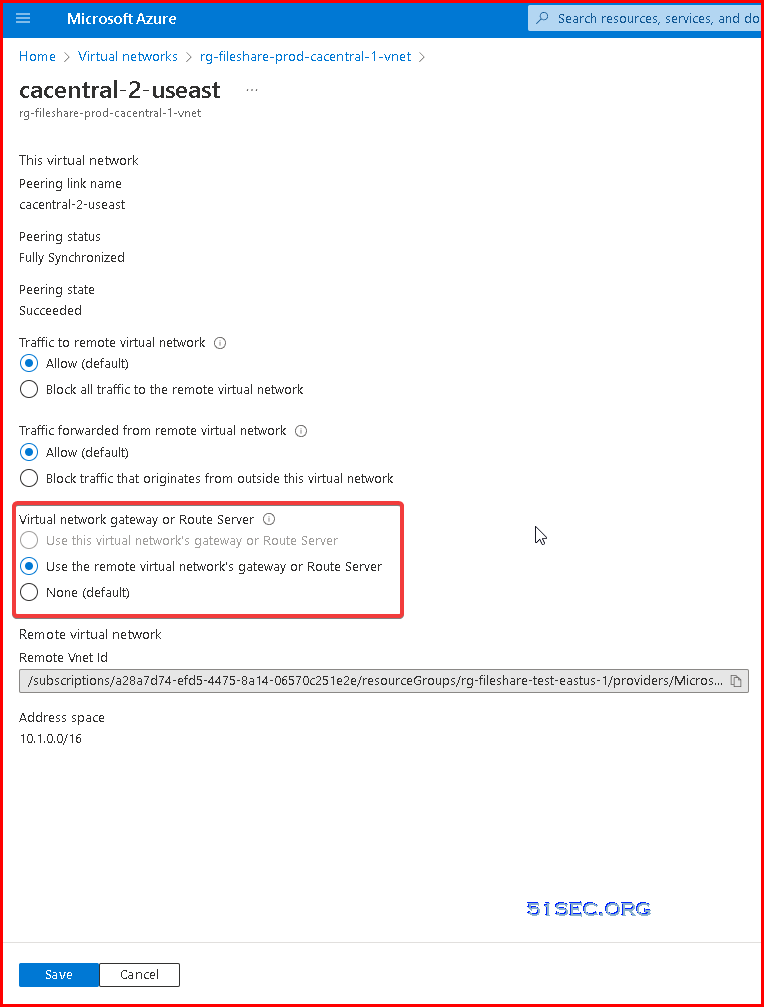
3 Change Peering configuration on remote
After above steps, your P2S users should be able to access remote site's network.







No comments:
Post a Comment