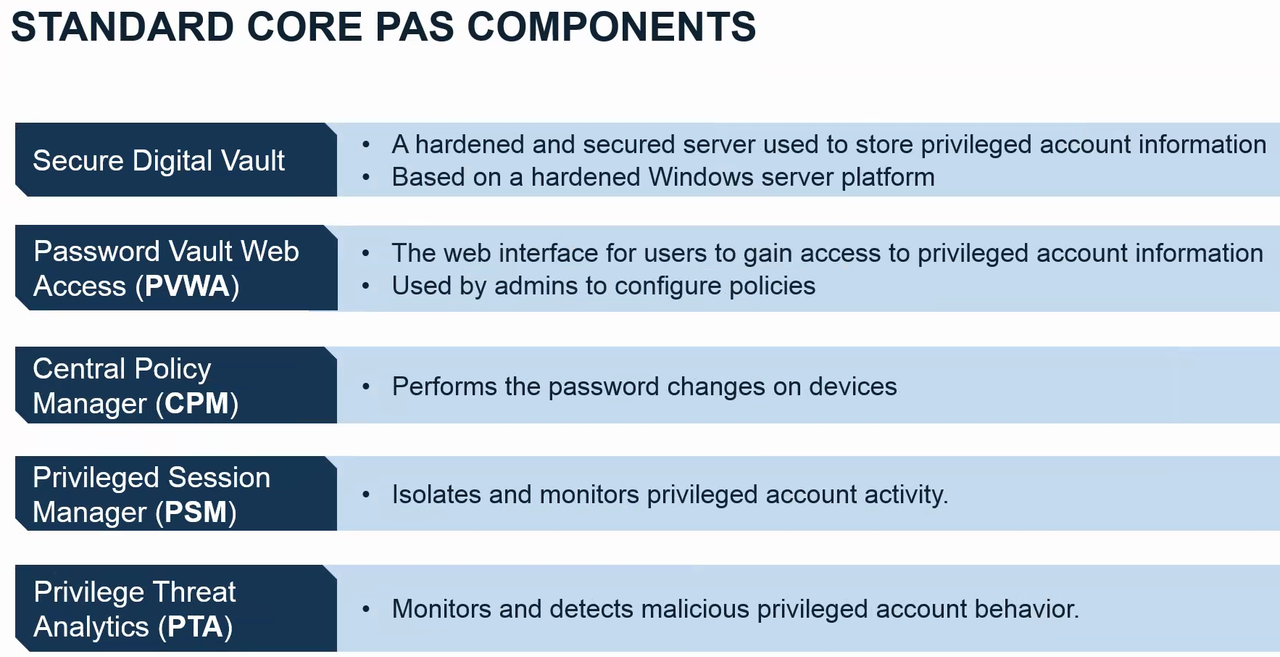
- Enterprise Password Vault
- Central Policy Manager (CPM)
- Password Vault Web Access (PVWA)
- Privileged Session Manager (PSM)
Why PAM: ROI Example
Key Economic Benefits (from Delinea ROI Calculations report)Anytown Manufacturing Corporation:
Industry: Manufacturing
Annual revenue: $1.4 b
Total employees: 1376
IT security personnel: 18
Four key areas of cost reductions:
- Cyber insurance compliance
- Regulatory compliance
- Data breach damages
- Privileged account managment support
Cells in grey depict average statistics provided by all interviewed customers. cells in blue depict annual cost reductions.
AMC (Anytown Manufacturing Corporation) achieves ROI of 1,322% or 12.22x its PAM first-year investment. In other words, for every $1 AMC spends with PAM, it achieves $12.22 in return.
Another cost reduction is using PAM can reduce cost associated with investigating false alarms.
Architecture
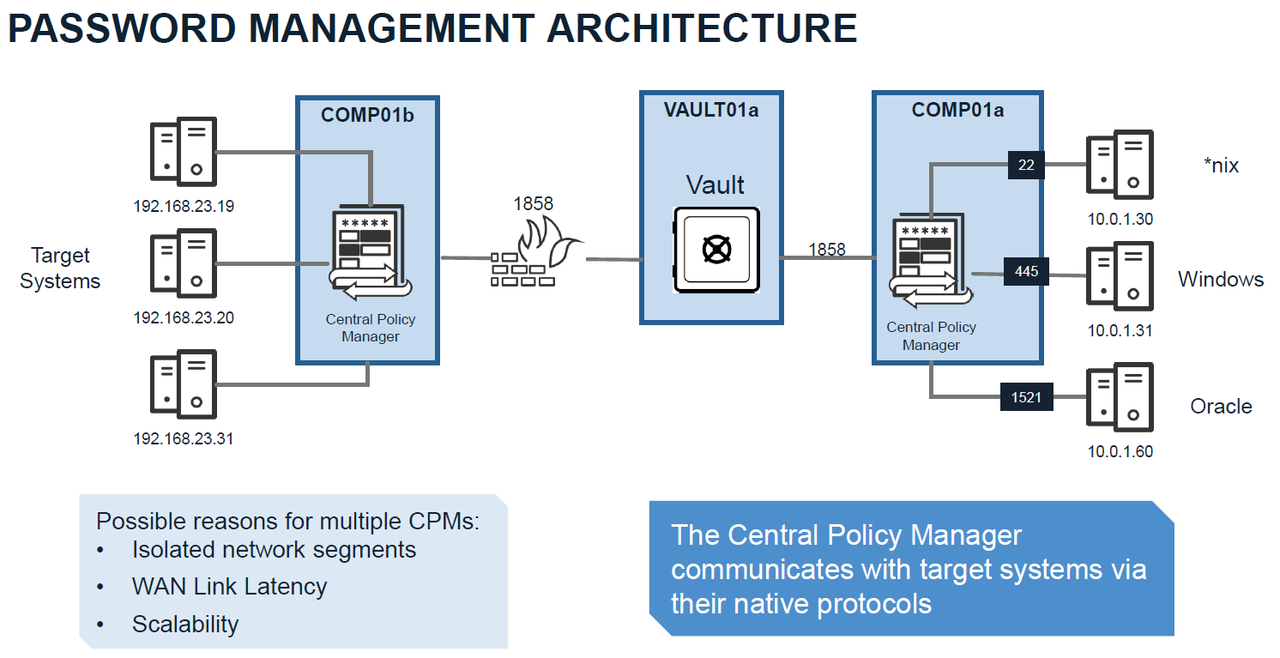
Password Management Architecture
Session Manager Architecture
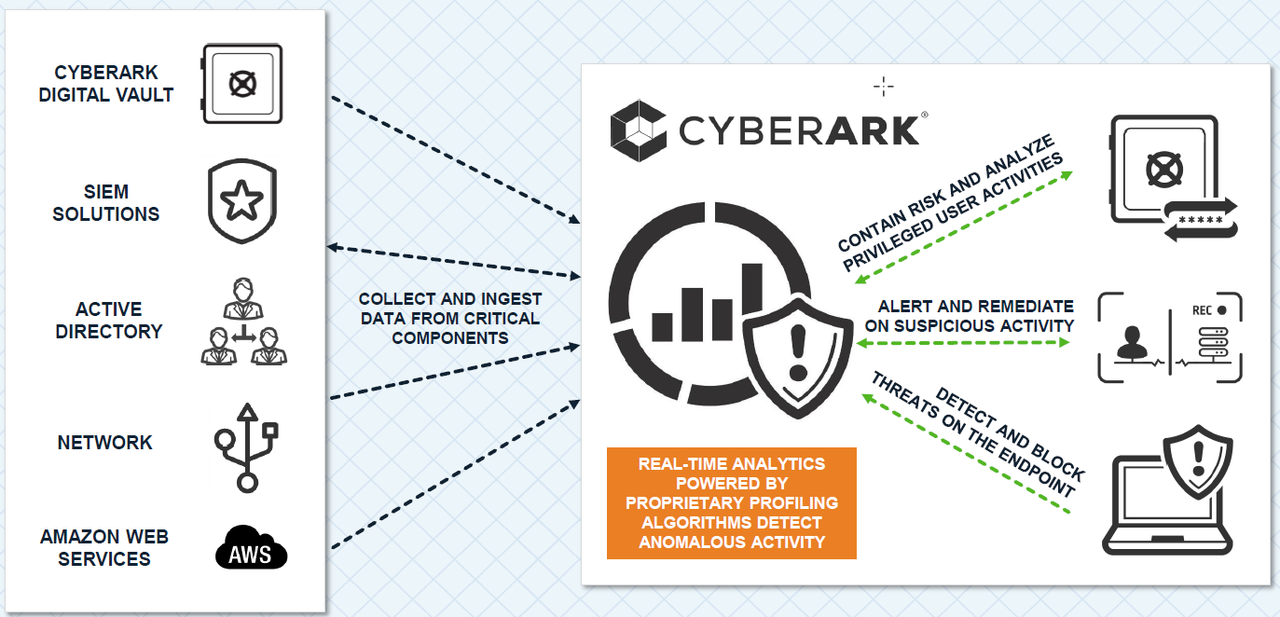
Privileged Threat Analytics Architecture
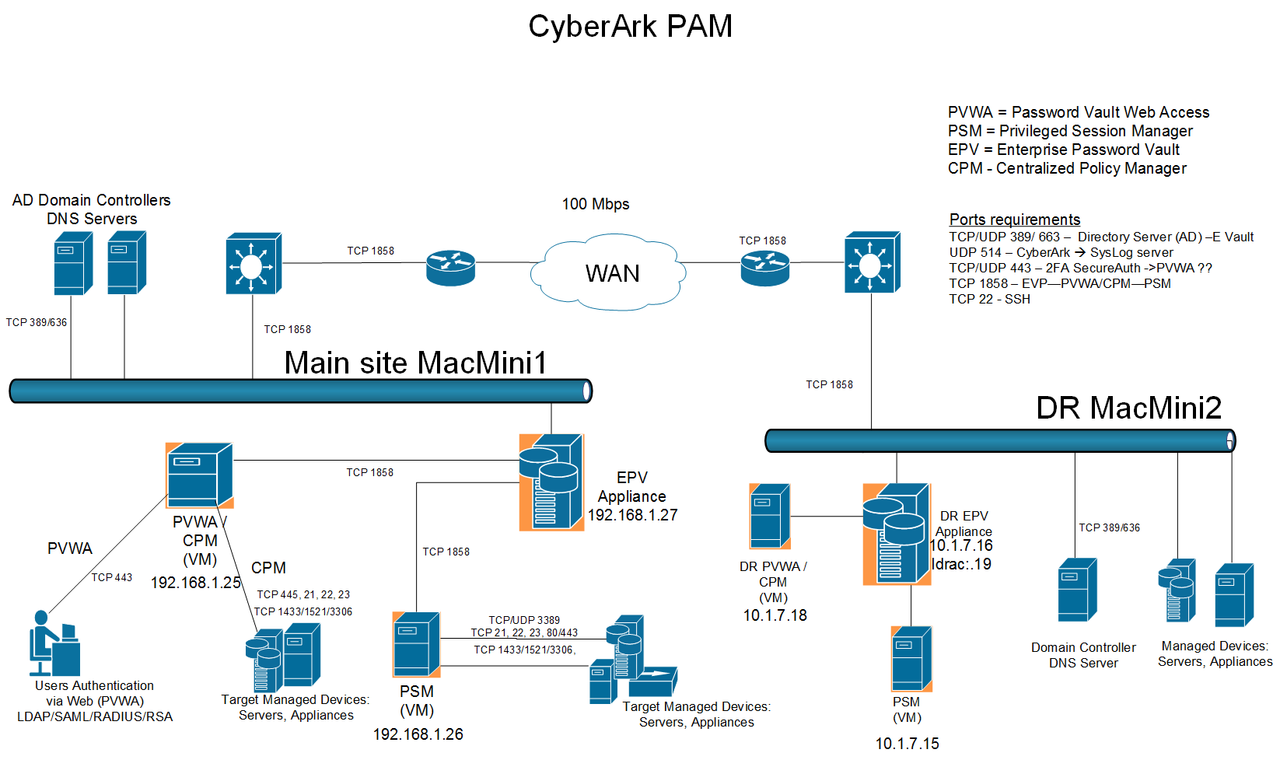 |
| PAM Solution High Availability Design |
PAS architecture design with PSM.
Connect through the web portal (PVWA):
1. create a CyberArk Bind User - ex. [email protected]. Usually it is domain admin account
2. Define follow LDAP CyberArk groups - Cyberark mapping roles:
CyberArk Vault Admins - Vault Admins
CyberArk Safe Managers - Safe Managers
CyberArk Auditors - Auditors
CyberArk Users - Users
From PVWA Web GUI:
1. Activate PSM
2. Deactivate 'Require users to specify reason for access'
3. Integrate LDAP
On the Vault
1. Manual restart the vault service, will not start Event Notification Engine service.
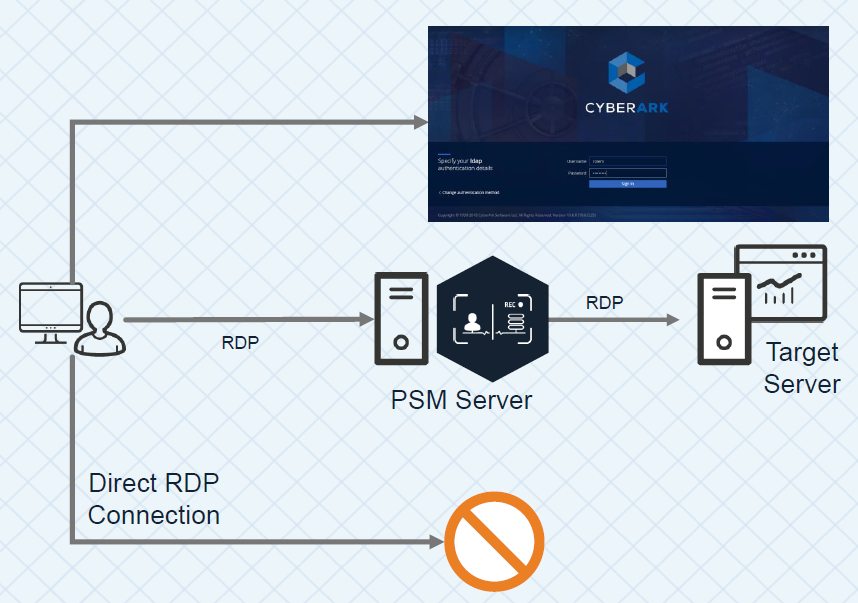
Connect through PSM for Windows:
PAS Configuration Steps
On the Domain Controller:1. create a CyberArk Bind User - ex. [email protected]. Usually it is domain admin account
2. Define follow LDAP CyberArk groups - Cyberark mapping roles:
CyberArk Vault Admins - Vault Admins
CyberArk Safe Managers - Safe Managers
CyberArk Auditors - Auditors
CyberArk Users - Users
From PVWA Web GUI:
1. Activate PSM
2. Deactivate 'Require users to specify reason for access'
3. Integrate LDAP
On the Vault
1. Manual restart the vault service, will not start Event Notification Engine service.
PSM "connect" explaination
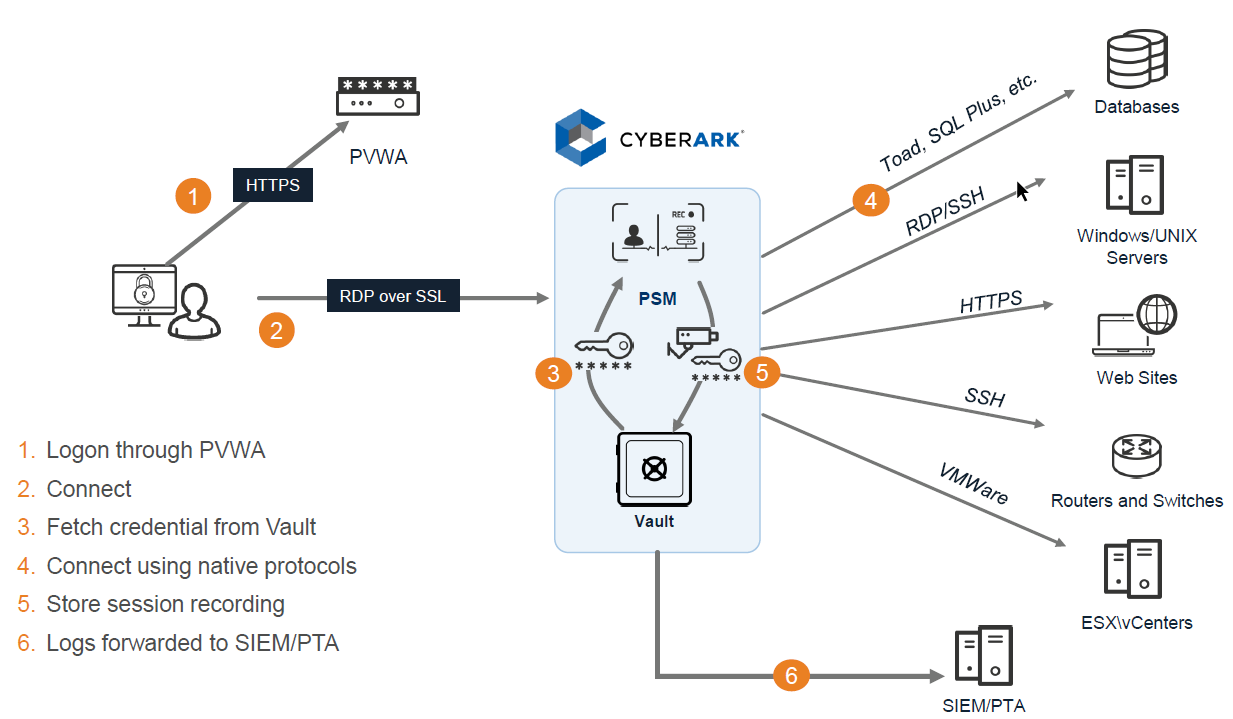
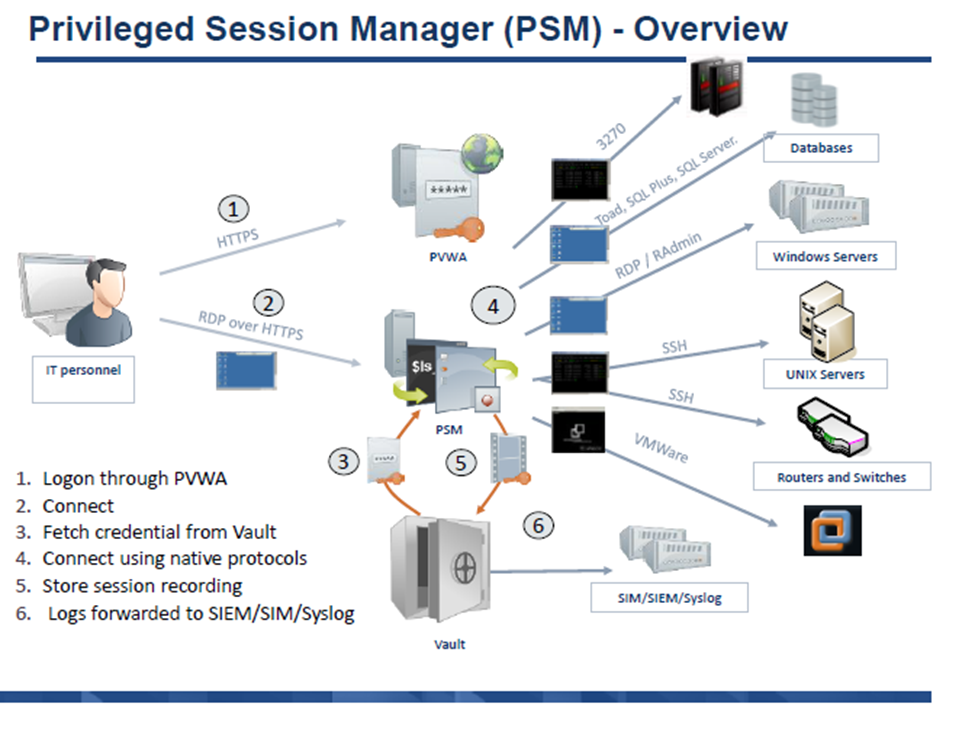 A user clicks "connect" in PVWA, an initial RDP session is established between the user and the PSM server. Since the user shouldn't be able to connect to the PSM server directly, the PSMConnect account is used. Once the session connects, PSM checks the session variables of the connecting user, including CyberArk username. Then the PSMConnect session creates a temporary profile for the user on the PSM server, called a Shadow user (if one doesn't exist), and switches the user's RDP session to that "isolated" shadow session/profile. Now that the user is in their own shadow session, PSM tries to execute the Connection Component specified. For example if it's SSH, it needs to pull the target address, managed account and password from the Vault. It will check if the user is authorized to use that account, pull the information, and launch an ssh session using command line switches for putty. Finally it will start recording, and give control to the RDS session back to the user.
A user clicks "connect" in PVWA, an initial RDP session is established between the user and the PSM server. Since the user shouldn't be able to connect to the PSM server directly, the PSMConnect account is used. Once the session connects, PSM checks the session variables of the connecting user, including CyberArk username. Then the PSMConnect session creates a temporary profile for the user on the PSM server, called a Shadow user (if one doesn't exist), and switches the user's RDP session to that "isolated" shadow session/profile. Now that the user is in their own shadow session, PSM tries to execute the Connection Component specified. For example if it's SSH, it needs to pull the target address, managed account and password from the Vault. It will check if the user is authorized to use that account, pull the information, and launch an ssh session using command line switches for putty. Finally it will start recording, and give control to the RDS session back to the user.
CPM "verify" explaination
For most platforms, to "verify" the password, CyberArk tries to log into the target with the stored account. If it's able to log in, it calls the password verify. In Unix machines that concept is fairly straightforward - it does an SSH connection, and if it's able to get to the regular prompt, it calls it a success. In Windows, for the regular (non-WMI platform), it tries to issue a "net use \servername\IPC$ /user:<manageduser>" command. If successful, the password is verified. For databases it might try to establish an ODBC connection, etc.Key Features of Core PAS
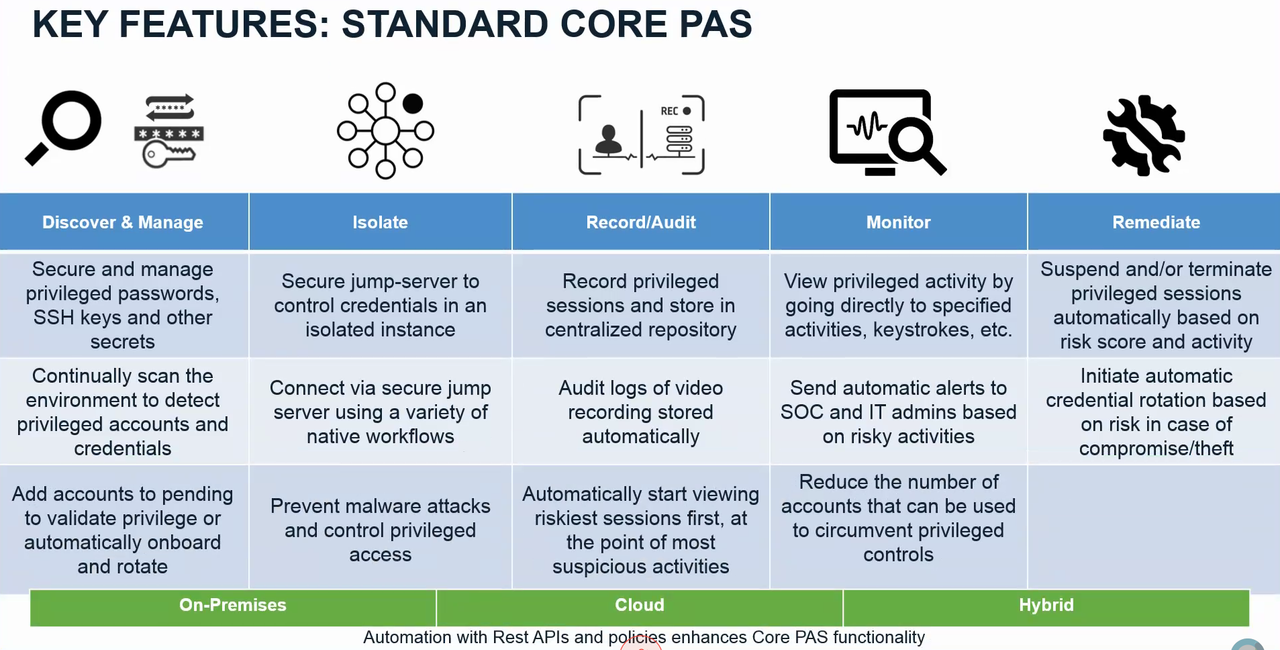
Standard Core PAS Componets
RDP Traffic Flow
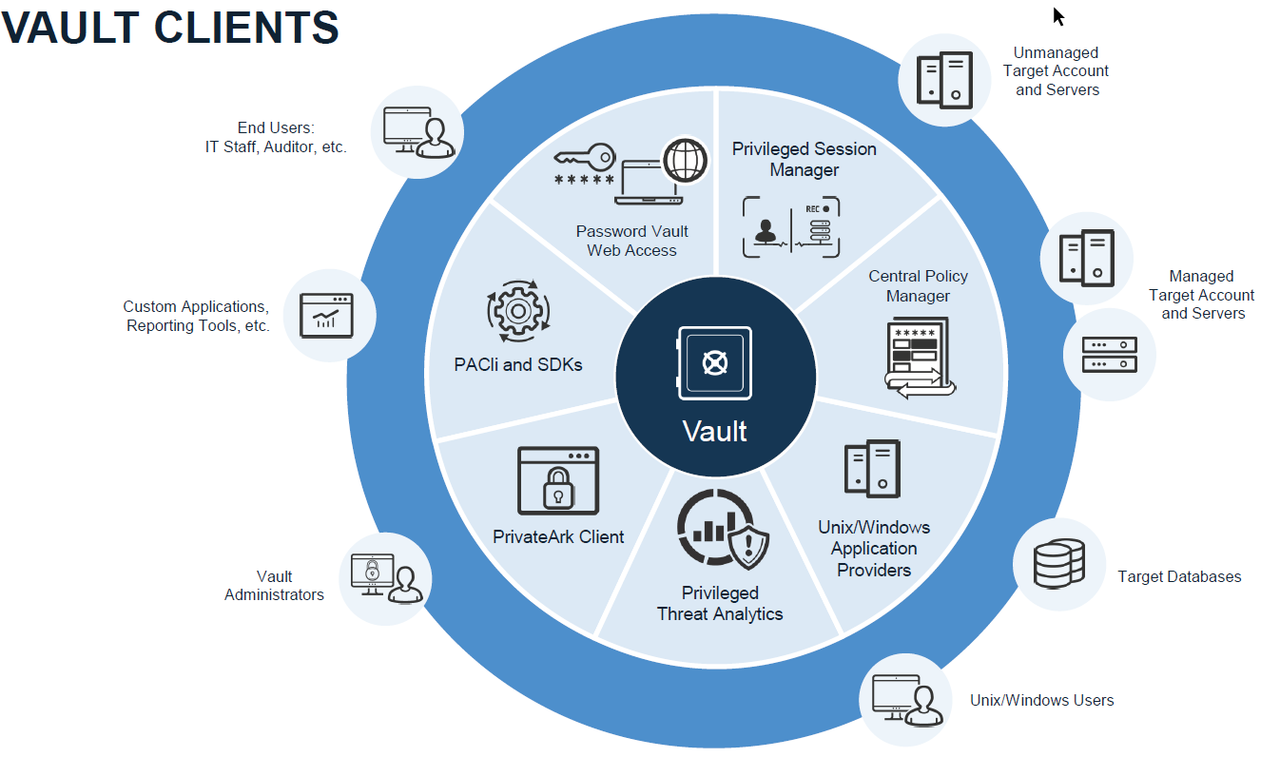
Vault, Components and Clients
References
- Install the Vault Backup Utility
- https://cyberark-customers.force.com/login
- CyberArk Secure File Exchange to download your software
- Official Visio and PowerPoint CyberArk icons











Thank you! Cyberark doesn't look unpolished. However, it still has some issues.
ReplyDeleteHello Team, Can I get the below details:
ReplyDelete- Conceptual Design for CyberArk PIAM
- Logical design
- Or any standard document with all high level information/document to implement the CyberArk Infrastructure.
Thanks!!