Why PAM: ROI Example
Key Economic Benefits (from Delinea ROI Calculations report)Anytown Manufacturing Corporation:
Industry: Manufacturing
Annual revenue: $1.4 b
Total employees: 1376
IT security personnel: 18
Four key areas of cost reductions:
- Cyber insurance compliance
- Regulatory compliance
- Data breach damages
- Privileged account managment support
Cells in grey depict average statistics provided by all interviewed customers. cells in blue depict annual cost reductions.
AMC (Anytown Manufacturing Corporation) achieves ROI of 1,322% or 12.22x its PAM first-year investment. In other words, for every $1 AMC spends with PAM, it achieves $12.22 in return.
Another cost reduction is using PAM can reduce cost associated with investigating false alarms.
Design for Small/Medium Environment
System Requirements
- Server sizing for each component, especially vault storage for PSM recording, RDP License/CPU/Memory for PSM
- Break-glass process
- In / Out of the project scope
- Integration with LDAP, MFA, SIEM, HSM, Ticket System, NTP, SMTP, PKI
- Security and Hardening
- Cloud / On-Prem
Vault Design
- Server sizing for each component, especially vault storage for PSM recording, RDP License/CPU/Memory for PSM
- Break-glass process
- In / Out of the project scope
- Integration with LDAP, MFA, SIEM, HSM, Ticket System, NTP, SMTP, PKI
- Security and Hardening
- Cloud / On-Prem
- Cluster HA / DR
- Appliance / Virtual Machine
- Server IP, FQDN, Specification
PVWA Design
- Multiple PVWA
- HA / Load balance, DNS rotation or using Load Balancer.
- Server IP, FQDN, Specification
CPM Design
- Multiple CPM
- Load balance on different types of Safe, such as one for Windows, one for *nux/Cloud.
- Server IP, FQDN, Specification
PSM Design
- Server Sizing and Recording Hard Drive Requirement on Vault Storage.
- RDP License
- Multiple PSM, Load balance, monitoring method
- PSMP, PSM HTML5 GW,
- Server IP, FQDN, Specification
- PSMConnect & PSMAdminconnect - Move to domain level - Onboard into Vault to Rotate Password.
Design Access Control List for User Management
- Applications Roles: access to the CyberArk application, but do not provide direct access to safes. For Examples:
- Vault Administrators - Native CyberArk Accounts
- Auditors - LDAP or AD
- End Users - LDAP or AD
- Safe Roles - specific to Safes, For Examples:
- Using a credential file (CRED)
- End Users (Permanent)
- End Users (Ad Hoc)
- Safe Master - Breakglass
- No Credential file (NO CRED)
- Vault Admins
- Approvers
- Account Provisioning
- API Automation User
- Built-In Administrator
- Line of Business Auditor
- Mapping CyberArk Baseline Safe Access Roles to Access
Safe Design
- Safe Structure
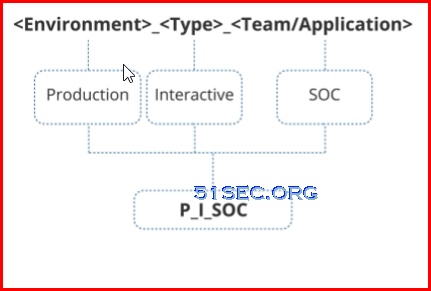
- Safe Name Convention
- 28 Character limit
- No Best standard
- Documented
- Examples: P=Production, WND= Windows Domain, Interactive =I, ORA=Oracle,
- Safe Access Mapping from Roles to Access Rights
- Rule-based access control (Clear) or Role-based access control (Flexible)
- Safe Access Model : Share , Personal, Mix
Example:
WSL = Windows Server Local
Rule-Based Access control
Design your Master Policy
- Design Master Policy, which should reflect your organization’s IT Security and password policy
Platform Design
- Name Convention (44 Characters recommended, 100+ Characters will cause problem when viewing from PVWA)
- Settings
- Exceptions
Workflow Design
- Approval
- Just in time access
- Dual Control
- Ticket system integration
- Email Alerts
- Audit workflows
- Export Vault data : export Vault reporting data into an MSSQL database
- PSM and PTA integration
Account Design
- Account name length restriction
- Account name convention
- Personalized accounts, Shared accounts for different technologies (DB, Windows, *Nix, Networking, Cloud)
- Accounts On-boarding Process
- Automate account creation, onboarding, and more :To accomplish this goal, most customers leverage the CyberArk REST API, however PACLI can still be used in the rare situations where it’s truly necessary.
- Accounts Feed
- Windows local accounts
- Domain accounts
- Windows services and scheduled tasks
- UNIX local accounts
- SSH keys and their trusts
- Bulk upload: The Password Upload Utility takes a .csv file of accounts and places them into Safes as defined within the .csv file. This is the most common approach when the CyberArk PAS solution is displacing another password vaulting solution.
- Auto-detection
- Windows local accounts
- VMWare Unix/Linux guest machines
- VMWare ESX host root accounts
- Local and domain service account usages
- Application accounts based on directory queries
Note: https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/IMP-Program/Imp-Program-DesignANDImp.htm?tocpath=Get%20Started%7CImplementation%20Program%7C_____3
Network Traffic Flow Diagram
- Firewall Ports
- Traffic direction : one way or two way
- All components including integration with NTP, AD, DC, Target Servers, DBs, Cloud , SIEM, Ticket system, etc
Authentication
- MFA, 2FA
- First Factor
- Second Factor
- Non Web Client Authentication - All kinds of Native Clients
Other Advanced Feature Consideration:
- PTA Design
- Licensing
- Integration
- Planning for application (non-human) account security
- Planning for endpoint security
- Endpoint Privilege Manager (EPM)
- On-Demand Privileges Manager (OPM)
Uses Cases Design
- Use Cases
- Test Cases
A phased approach for implementing PAS
CyberArk Brief: A phased approach for implementing a Privileged Access Security Program1. Phase 0 - Identify
1.1 Crown of jewels - Most critical assets
PII
Credit Cards
etc
1.2 Accounts who can access those assets
OS accounts
DB accounts
applications accounts
1.3 Accounts
shared / role based privilege accounts - built-in administrator account and root account
personal privilege accounts : accounts with -adm, or $ at the end
Focus on shared / role based privilege accounts first will get you least push back from admins.
2. Phase 1
2.1 Load --> Rotate
Load credentials into actual vaultsSet up automatic verification process to confirm those credentials are accurate
End user should be able to use connect to reach their targets to do their administration work
Choose selective subset accounts to change password. Start with change button to confirm the CPM process is working.
Automated changes to rotate credentials' passwords.
2.2 Isolate --> Monitor --> Analyze
Remove show/copy buttons to require end users to connect to target.
PSM will provide connectivity and monitor/record the session without exposing credentials.
PTA component will detect / alert threat detected from multiple sources
3. Phase 2
Repeat - going wider and deeper
Going wider: - expand the process to other end points we identified (Networking devices, databases, web applications, iol devices)Going deeper: - non human id ( application accounts, iis app pool, registry keys )
Timeline for basic installation of PAS
This is basic sample implementation schedule to roll out a non-ha basic design PAS solutionPre-implementation to collect following information;
1. network design diagram including firewall, domain controller, VM ip, dns, smtp, snmp , ntp, etc.
2. hardware / virtual machine information based on size evaluation
3. traffic flow diagram
4. firewall rule sets based on traffic flow diagram
5. Details of SMTP, DC, SNMP, NTP,
6. CA certificate
7. Download software copy and licenses.
8. Make sure hard copy of Master CD, Operator CD in safe hand.
• Onsite Implementation Day 1: Install and perform initial configuration of the Production including advanced Vault integration such as SNMP, SMTP, SYSLOG and any others the were agreed upon.
• Onsite Implementation Day 2: Install and perform initial configuration of the Central Policy Manager, Password Vault Web Access 1 and 2, Privileged Session Manager, Secure Replication Utility and the PrivateArk Client.
•Onsite Implementation Day 3 Perform advanced configuration for the CPM, PVWAs and PSM. Test CPM management on 3 5 types of the out of the box plug ins. Test PSM workflows on 3 5 types of the out of the box connectors.
• Onsite Implementation Day 4 Troubleshoot any issues discovered during the CPM testing and PSM workflows. Perform overview session with administrators. Go over and assist in documenting the Master Policy, Access Control Model data and permission structures. Set up and go over support access and procedures.
References
- Docs > Administration > Components > Privileged Session Manager > Architecture
- Official Visio and PowerPoint CyberArk icons











No comments:
Post a Comment