I found this step-by-step article from CyberArk web site and quoted here for my own notes.
CyberArk Article Number: 000005387
What is AdminSDHolder?
AdminSDHolder is a container that exists in every Active Directory domain for a special purpose. The Access Control List (ACL) of the AdminSDHolder object is used as a template to copy permissions to all “protected groups” in Active Directory and their members. Protected groups include privileged groups such as Domain Admins, Administrators, Enterprise Admins, and Schema Admins. This also includes other groups that give logon rights to domain controllers, which can be enough access to perpetrate attacks to compromise the domain.
Active Directory will take the ACL of the AdminSDHolder object and apply it to all protected users and groups periodically, in an effort to make sure the access to these objects is secure. This works, in theory, because the default ACL for AdminSDHolder is very restrictive. However, if an attacker is able to manipulate the ACL for AdminSDHolder, then those permissions will automatically be applied to all protected objects. This will give an attacker a way to create persistent access to privileged accounts within the domain.
Here is an example of the AdminSDHolder ACL with a new user added to give that user account access to all protected objects:
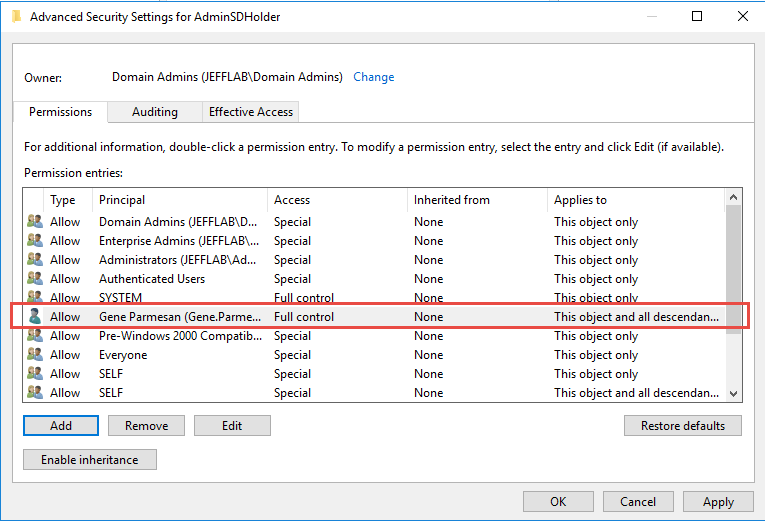
The AdminSDHolder permissions are pushed down to all protected objects by a process SDProp. This happens, by default, every 60 minutes but this interval can be changed by modifying a registry value. That means if an administrator sees an inappropriate permission on a protected object and removes it, within an hour those permissions will be put back in place by SDProp. This default setting can be frustrating and hard to track down if you don’t understand what’s happening.
How to set reconcile account
Set Reconcile account for platform
Set Least Privilege for Windows Reconcile Account
The reconcile account must be granted the necessary privileges to perform a password reset:
- Reset Password
- Read Property, pwdLastSet
- Write Property, pwdLastSet
You do so by using the dsacls.exe utility For Example:
The above grants Reset Password as well as Read and Write pwdLastSet property permissions to CA\PGPassMgrs on all accounts that will receive the AdminSDHolder template.
Domain: ca.lab
New Group for
Password Reset of Protected Groups: PGPassMgrs Reconcile account is a member of
PGPassMgrs
dsacls.exe
CN=AdminSDHolder,CN=System,DC=ca,DC=lab /G CA\PGPassMgrs:CA;"Reset
Password" CA\PGPassMgrs:RP;"pwdLastSet"
CA\PGPassMgrs:WP;"pwdLastSet"
The above grants Reset Password as well as Read and Write pwdLastSet property permissions to CA\PGPassMgrs on all accounts that will receive the AdminSDHolder template.
======================================================
Note: The topic discussed below is a feature of the Microsoft Active Directory solution and is not supported by CyberArk. It is subject to change by Microsoft. More information can be found on this topic by contacting Microsoft or visiting their online support systems.
The reconcile account must be granted the necessary privileges to perform a password reset:
Reset Password
Domain Admin accounts, along with a list of other groups, are protected. If you change the ACL on a member of the Domain Admins group, Active Directory will eventually change the ACL back based on a secure template. This template is AdminSDHolder and is always found in the System container.
In order to grant your reconcile account the ability to change the password for members of protected groups, you must add that permission to the AdminSDHolder template
You do so by using the dsacls.exe utility
For Example:
Domain: ca.lab
New Group for Password Reset of Protected Groups: PGPassMgrs
Reconcile account is a member of PGPassMgrs
dsacls.exe CN=AdminSDHolder,CN=System,DC=ca,DC=lab /G CA\PGPassMgrs:CA;"Reset Password"
The above grants Reset Password permissions to CA\PGPassMgrs on all accounts that will receive the AdminSDHolder template.
Once the command is run, you must wait for the SDPROP process to apply the template. This process is started, by default, every 60 mintues.
After the permissions have been propagated, your Reconcile account will be able to reconcile Domain Admin accounts as well as other accounts in Protected Groups. It will not, however, have all of the other privileges granted to a standard domain admin account.
If you wish to have the account unlocked on reconciliation, additional permissions are required:
**Enhancements were made as of PAS 9.10 which enable the use of a more restrictive permission set**
For PAS 9.10 and newer the following are required:
Read Property, LockoutTimeWrite Property, LockoutTime
For PAS versions prior to 9.10, the following are required:
Modify PermissionsRead Property, account restrictionsWrite Property, account restrictions
Below is an example of using dsacls.exe to grant these additional permissions
PAS 9.10 and newer
dsacls.exe CN=AdminSDHolder,CN=System,DC=ca,DC=lab /G CA\PGPassMgrs:RP;LockoutTime CA\PGPassMgrs:WP;LockoutTime
PAS versions prior to 9.10
dsacls.exe CN=AdminSDHolder,CN=System,DC=ca,DC=lab /G CA\PGPassMgrs:WD CA\PGPassMgrs:RP;"account restrictions" CA\PGPassMgrs:WP;"account restrictions"
Note: If the platform is configured for "UnlockUserOnReconcile", and these permissions are not granted, the CPM will receive the following error when reconciliation is attempted and the target account is locked out.
CACPM406E Reconciling Master Safe: <safe>, Folder: <folder>, Object: <object> failed (try #<attempt>). Code: 2101, Error: Error in reconcilepass to user <target account> on domain <domain>. Reason: The workstation driver is not installed. (winRc=2102). Reconcile account details - Safe: <safe>, Folder: <folder>, Object: <reconcile account> The CPM is trying to reconcile this password because its status matches the following search criteria: ResetImmediately.
For a list of the Protected Accounts and Groups in Active Directory by version, please see the page in Microsoft's Documentation at the URL below.
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-c--protected-accounts-and-groups-in-active-directory
https://docs.microsoft.com/en-us/windows-server/identity/ad-ds/plan/security-best-practices/appendix-c--protected-accounts-and-groups-in-active-directory







No comments:
Post a Comment