Traffic FlowChart
1 Normal SSH Launcher Traffic
2 SSH Proxy Traffic

3 RDP Proxy
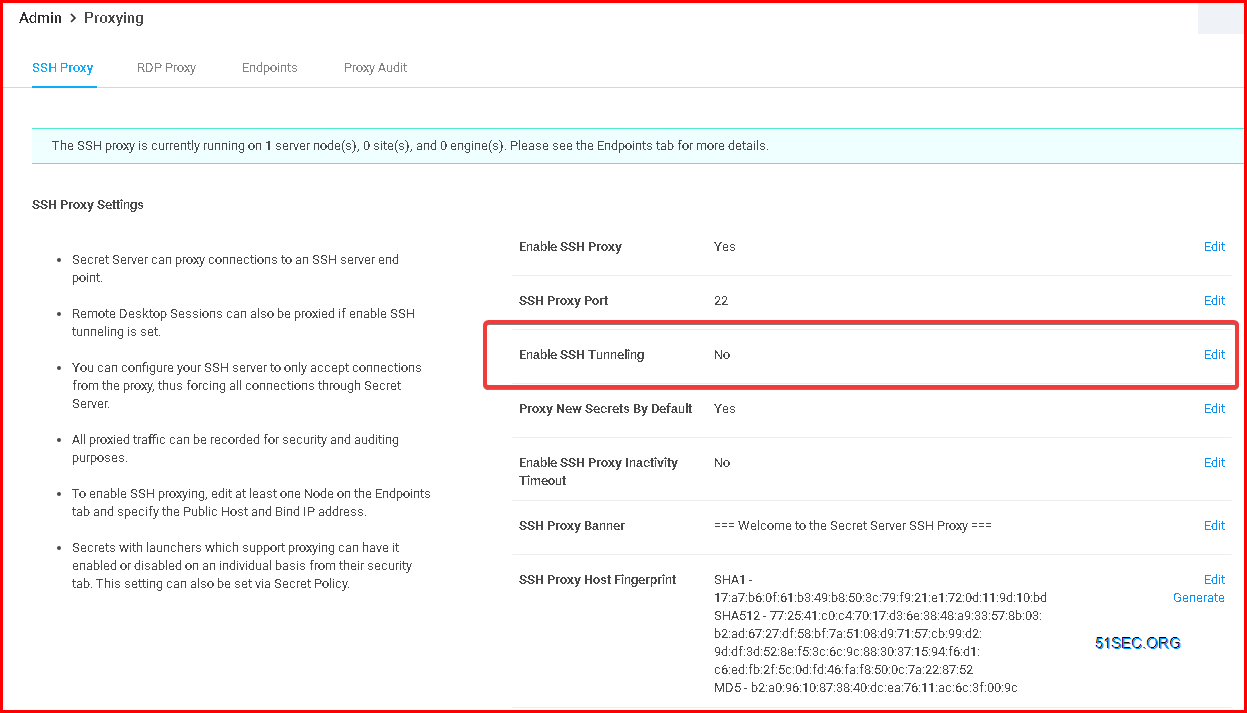
SSH Proxy
SSH Tunneling
SSH tunneling is a method of transporting arbitrary networking data over an encrypted SSH connection. It can be used to add encryption to legacy applications. It also provides a way to secure the data traffic of any given application using port forwarding, basically tunneling any TCP/IP port over SSH.
Enable SSH Tunneling for other traffic such as RDP.
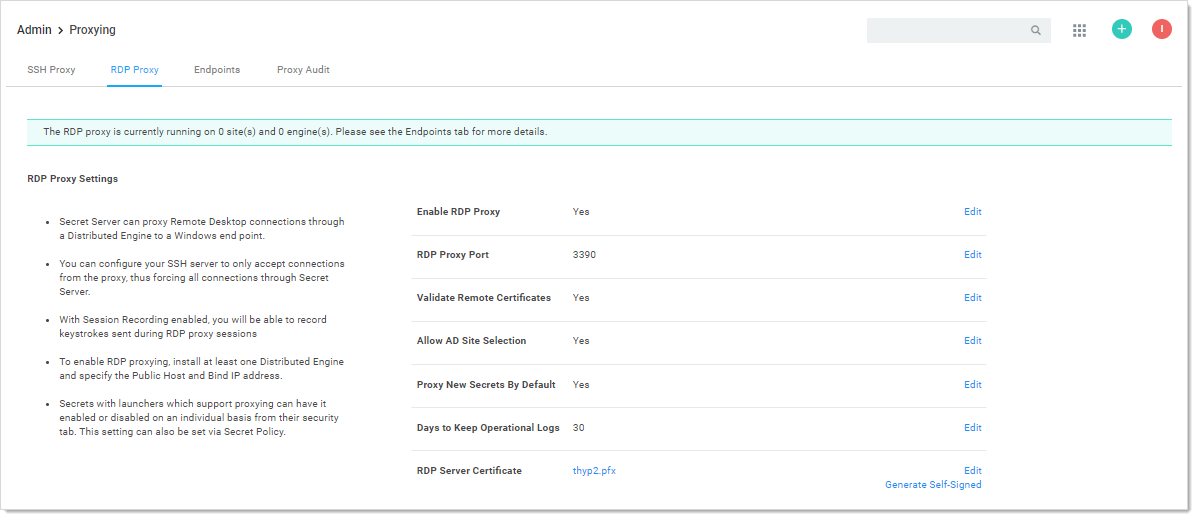
RDP Proxy
There are two methods to use RDP Proxy:
1 RDP Proxying using RDP Proxy
How It Works
- The user clicks the RDP launcher in SS.
- The launcher executes on the client's machine.
- The launcher establishes a connection to the RDP Proxy using credentials generated for the session. These credentials are short lived and can only be used once.
Once the launcher has successfully authenticated with the RDP proxy, the RDP proxy looks up the credentials and target hostname to connect to.
- Note: The secret credentials do not get served to the client machine in this flow, which improves credential security.
- The RDP proxy connects to the desired remote host with the secret credentials.
- The RDP session is established.
- RDP traffic is sent back and forth over the RDP proxy, session keystrokes are monitored if session recording is enabled.
2 RDP Proxying using SSH Proxy and SSH Tunneling
The RDP Proxying feature allows RDP connections, established using the launcher, to be routed through Secret Server. It does this using a SSH tunnel, created using SSH local client port forwarding, from the client's machine to the Secret Server SSH Proxy.
How it works
- The user clicks the RDP launcher in Secret Server.
- The launcher executes on the client's machine.
- The launcher establishes a connection to the SSH Proxy using unique credentials generated for the session. These credentials are short lived and can only be used once.
- Once the launcher has successfully authenticated with the SSH Proxy, the launcher will open a socket and listen for a connection on an available ephemeral port (the forwarding port) on the client's machine.
- RDP launches on the client machine and connects locally to the forwarding port.
- All RDP traffic for this session is now routed through the SSH tunnel to Secret Server, then forwarded to the target machine.
- The RDP session is established.
References
- SSH Proxy Configuration and Bandwidth
- Secret Server: Using Connect As Command and SSH Proxy with PuTTY launcher
- SSH Terminal Administration
- SSH Proxy Configuration
- RDP Proxy Configuration
- Configuring SSH Proxies for Launchers
- RDP Proxying - IBM
- CyberArk vs Thycotic








No comments:
Post a Comment