This post is to summarize the configuration of CyberArk Privilege cloud for Azure Active Directory environment.
CyberArk Products Security Pillars (Access, Privilege, DevSecOps)
High Level Steps for Onboarding Azure Cloud Accounts
- One Azure APP Safe and Two Platforms to be created on CyberArk and be activated
- Platforms
- Microsoft Azure Application Keys Management (Name and platform properties TBD)
- Microsoft Azure Password Management (Name and platform properties TBD)
- Safe
- Azure App Safe (Name TBD)
- From Azure cloud, register one App for CyberArk CPM APP.
- This will require one Global admin to help get it done
- Following information will be generated from this app registration
- Display Name (TBD)
- Application (Client) ID
- Object ID
- Directory (Tenant) ID
- Client secret (Rotate at least once a year)
- Assign proper API permissions
- Grant User Administrator role to Step 2's new registered APP.
- Add a new account to Azure APP Safe in CyberArk PVWA with following properties
- Using Azure App Key Mgmt Platform and Azure APP Safe
- Display Name (TBD)
- Application (Client) ID
- Object ID
- Directory (Tenant) ID
- Create testing account in Azure Cloud
- This is Cloud only account. This will be required for testing.
- Create Azure Admin Safe
- Azure Admin Account Safe (Name TBD)
- Add an Azure account into CyberArk
- using Azure Password Management platform and Azure admin account safe
- Application id
- Azure Directory ID
- Link Application Account and Reconcile Account to this Azure Cloud Account
- Change, verify, reconcile account to make sure all is working as expected
- Download ChromeDriver.exe
- Download script for installing ChromeDrive.exe from CyberArk Privilege Cloud Tools package.
- install it on PSM servers using script
- Verify and modify AppLocker allow-list
- Modify Platform to get MFA supported
- Assign new connector to the platform
- Test and make sure it is working as expected.
Groups, Users, Roles in Identity
Platform
|
Length |
Description |
Sample |
Legend |
|
3 |
Account Type |
SPA |
Account type according to PAM name conventions (e.g., SPA:
Shared Privileged Account, PPA: Personal Privileged Account, WBA: Windows
Built in Account, etc.) |
|
1 |
Delimiter |
- |
Delimiter |
|
2 |
Technology Platform |
DB |
Platform or OS type (e.g., CL:Cloud, WN: Windows, NX:
Linux/Unix, DB: Database, WB: Website, AP: Application, etc.) |
|
1 |
Delimiter |
- |
Delimiter |
|
6 |
Technology type |
MSSQL |
Platform technology type, e.g. OS or DB variant (WIN, AIX,
MSSQL, MYSQL, RHEL, Azure, etc.) |
|
1 |
Delimiter |
- |
Delimiter |
|
1 |
Environment |
P |
Environment type (e.g., P: Production, D: Development
etc.) |
|
3-14 |
Workflow |
Chkout |
Workflows that are applicable to the platform (e.g., PSM,
Chkout, etc.) |
|
1 |
Delimiter |
- |
Delimiter |
|
7-10 |
Management |
Automatic |
Password management type for the account (e.g., Managed,
Unmanaged) |
|
1 |
Delimiter |
- |
Delimiter |
|
4 |
Expiry |
30 |
Password expiry duration (e.g., 12H, 1Y, 30D, 90D, 180D,
No) |
Safe
Note: Don't change safe name until you fully know the changes. The linked logon account, application account, and reconcile account in that safe will become empty.Shared Access Model:
- P-Cloud safes can be assigned to different teams
- Each team may have access to one or more safes
- Permissions to safes are assigned via AD Security groups
- The following roles are suggested for safe members:
- Safe Admins
- Safe Auditors
- Safe Approvers
- Safe Persistent Users (including nested groups)
- Safe Ad-Hoc Users
Safe Name Convention:
Naming and Capacity Restrictions & Considerations
- A safe name cannot be more than 28 characters
- Due to performance considerations, a maximum number of objects stored in a safe is 20000. This includes versions of objects, therefore the recommended number of actual accounts or files stored in a safe is 3000-5000
- Due to security considerations, it is recommended to separate objects stored in safes in groups, following the “least privilege” concept, to avoid situations where providing access for a user to a group of accounts also gives said user access to unrelated accounts. For example: “Windows Accounts” vs “Window Local Administrators for HR App” (28 character limit was not enforced in this example) Heading 2 - RGB 23-69-123
Naming Convention Creation Steps
- Define business designations that are important for your environment. For example: Line of Business, Geographical Location, Data Center, Platform, Account Type, Application Association, Environment, etc
- List them in order of importance
- Discuss and agree on the resulting layered structure. This will be your Safe Naming Convention Base. Eliminate any layers that are redundant or not needed.
- List out as many examples of each designation as possible and define 2-4 letter translations for each. For example ORA for Oracle Database or LADM for Local Administrative Account. Alternatively, define a 1-2 digit number and its place in the Safe name instead of a 2-4 letter translation. For example 06 in the 8th and 9th spot for Oracle Database or 1 in the 1st spot for Production
- Create 7-10 examples of safe names to ensure the structure is sufficiently robust to account for any future need
- Document the Safe Naming Convention
- Examples
- P-BOS-SRV-WIN-LADM – Local Administrative Accounts (LADM) for Production (P) Windows (WIN) Servers (SRV) in Boston DC (BOS)
- P-BOS-SRV-WIN-DSVC-HR – Domain Service Accounts (DSVC) for the HR Application (HR) living on Production (P) Windows (WIN) Servers (SRV) in the Boston DC (BOS)
- D-NYC-DB-ORA-LSVC-HR – Local Service Accounts (LSVC) for the HR Application (HR) living on Development (D) Oracle (ORA) Database (DB) in the NY Data Center (NYC)
Naming Convention Cheat Sheet
Category 1 - Environment:
Production (P), Development (D), Testing (T), Q/A (Q), etc
Category 2 (optional) - Geographical Location or domain:
Datacenter 1 (DC1), Datacenter 2 (DC2), California Datacenter (CA), etc
Category 3 (optional) - Business Unit/Access Groups/Application:
Security Team (SEC), Engineering Team (ENG), Support Desk (SUP), Network Team Routers (NWR), Network Team Switches (NWS), etc
Category 4 - Technology:
Server (SVR), Workstation (WKS), Network Device (NET), Database (DB), Mainframe (MF), Domain (DOM) etc
Category 5 - Technology Subtype (flavor):
Windows (WIN), UNIX (UNX), Linux (LNX), HP-UX (HP), Cisco (CSC), SQL Database (SQL), Oracle Database (ORC)
Category 6 - Account Type:
Local Account (LA), Domain Account (DA), Local Service Account (LS), Domain Service Account (DS), Root (RT), Enable Account (EN), SQL SA Account (SA)
Category 7 - Auto-Detection Enabled Safe (required only if using auto-detection for local accounts):
Auto-detection (A)
Examples:
|
Length |
Description |
Sample |
Legend |
|
1 |
Prefix
for shared safe |
S |
Reserved
for Shared Safes |
|
1 |
Delimiter |
- |
Delimiter |
|
5-8 |
Team
name |
Cyber |
Six (6)
characters abbreviation for Team name, such as EntSd |
|
1 |
Delimiter |
- |
Delimiter |
|
2-5 |
Technology |
DB |
Platform
or OS type (e.g., WN: Windows, NX: Linux/Unix, DB: Database, WB: Website, AP:
Application, AD: Active Directory, etc.) |
|
1 |
Delimiter |
- |
Delimiter |
|
3-5 |
PSM
Control |
NoPSM |
Define
if PSM should be enabled at Safe level |
|
1 |
Delimiter |
- |
Delimiter |
|
1 |
Environment |
P |
Environment
type (e.g., P: Production, D: Development, etc.) |
|
1 |
Delimiter |
- |
Delimiter |
|
2 |
Sequence
number |
01 |
Sequence
number (00-99) for teams with multiple safes |
Master Policy
Create Platforms and Safes for Azure App and CPM
Create Two Duplicated Platforms:
Create two Safes
Onboarding Azure App Key As Account
- Create a new secret
- The secret can be rotated by CyberArk CPM.
- Grant access to directory for read user in the directory
- Grant access to Application to read / write user accounts
- user administrtors
- password administrators
- Privileged Authentication administors
Onboarding Azure AD Accounts for Azure Portal
- for older version before 115: https://chromedriver.chromium.org/downloads
- for newer version after 115: https://googlechromelabs.github.io/chrome-for-testing/
Downloading and installing Chrome
Enabling web app support in PSMHardening script
Running PSM Configure AppLocker script
---
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmsshclient.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmprivatearkclientdispatcher.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmpvwadispatcher.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\mssqlmanagementstudiowindowsauthenticationdispatcher.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psm3270client.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmwebformdispatcher.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmwinscpdispatcher.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\winscp.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmrealvncdispatcher.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmxfocus.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmtokenholder.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmsessionalert.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmsuspendsession.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmpreventwindowhide.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmmessagealert.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmwindowseventslogger.exe
Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\cyberark.psm.webappdispatcher.exe Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\dllinjector.exe Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\dllinjector64.exe Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\cyberark.progressbar.exe Evaluating the dlls consumed by c:\program files (x86)\cyberark\psm\components\psmticketvalidator.exe Evaluating the dlls consumed by c:\windows\system32\conhost.exe
Evaluating the dlls consumed by c:\windows\system32\taskhostw.exe
Evaluating the dlls consumed by c:\windows\system32\wermgr.exe
Evaluating the dlls consumed by c:\program files (x86)\vcxsrv\vcxsrv.exe
Evaluating the dlls consumed by c:\program files (x86)\vcxsrv\xkbcomp.exe
Evaluating the dlls consumed by c:\program files (x86)\internet explorer\iexplore.exe
Evaluating the dlls consumed by c:\program files\internet explorer\iexplore.exe
Evaluating the dlls consumed by c:\program files (x86)\google\chrome\application\chrome.exe
CheckSensitivePrivilegesForDirectories: Current Directory: c:\programdata\microsoft\windows defender\platform\4.18.23050.9-0
CheckSensitivePrivilegesForDirectories: Current Directory: c:\windows\assembly\nativeimages_v4.0.30319_64\mscorlib\4bc5e5252873c08797895d5b6fe6ddfd
CheckSensitivePrivilegesForDirectories: Current Directory: c:\windows\assembly\nativeimages_v4.0.30319_64\system\3ac991e343330dfdb660c4b0041bfe5e
Loading new AppLocker configuration...
Configuring Application Identity service...
CyberArk AppLocker's configuration script ended successfully.
True
---
End of PSM Configure AppLocker script output
Running PSM Hardening script
---
Notice: In order to prevent unauthorized access to the PSM server, the local RemoteDesktopUsers group should contain ONLY the following users:
1) Maintenance users who login remotely to the PSM server through Remote Desktop Services.
2) Vault LDAP users who wish to connect to target systems through PSM directly from their desktop using an RDP client application such as MSTSC.
These are the current members of the local RemoteDesktopUsers group:
WinNT://IMCOINVEST/Domain Users
WinNT://IMCOINVEST/VM-NETSEC-Test-1/PSMConnect
WinNT://IMCOINVEST/VM-NETSEC-Test-1/PSMAdminConnect
Would you like to remove all members of this group? (yes/no): no
SUCCESS: The file (or folder): "C:\Windows\explorer.exe" now owned by the administrators group.
0
C:\Windows\explorer.exe
C:\Windows\explorer.exe
C:\Windows\explorer.exe
SUCCESS: The file (or folder): "C:\Windows\SysWOW64\explorer.exe" now owned by the administrators group.
1
C:\Windows\SysWOW64\explorer.exe
C:\Windows\SysWOW64\explorer.exe
C:\Windows\SysWOW64\explorer.exe
SUCCESS: The file (or folder): "C:\Windows\system32\taskmgr.exe" now owned by the administrators group.
2
C:\Windows\system32\taskmgr.exe
C:\Windows\system32\taskmgr.exe
C:\Windows\system32\taskmgr.exe
SUCCESS: The file (or folder): "C:\Windows\SysWOW64\taskmgr.exe" now owned by the administrators group.
3
C:\Windows\SysWOW64\taskmgr.exe
C:\Windows\SysWOW64\taskmgr.exe
C:\Windows\SysWOW64\taskmgr.exe
SUCCESS: The file (or folder): "C:\program files\Internet Explorer\iexplore.exe" now owned by the administrators group.
4
C:\program files\Internet Explorer\iexplore.exe
C:\program files\Internet Explorer\iexplore.exe
C:\program files\Internet Explorer\iexplore.exe
processed file: C:\program files\Internet Explorer\iexplore.exe
SUCCESS: The file (or folder): "C:\program files (x86)\Internet Explorer\iexplore.exe" now owned by the administrators group.
5
C:\program files (x86)\Internet Explorer\iexplore.exe
C:\program files (x86)\Internet Explorer\iexplore.exe
C:\program files (x86)\Internet Explorer\iexplore.exe
processed file: C:\program files (x86)\Internet Explorer\iexplore.exe
Chrome hardening completed successfully
IE hardening completed successfully
Edge hardening completed successfully
C:\Program Files (x86)\Cyberark\PSM
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM" now owned by the administrators group.
6
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM" now owned by the administrators group.
C:\Program Files (x86)\Cyberark\PSM
C:\Program Files (x86)\Cyberark\PSM
C:\Program Files (x86)\Cyberark\PSM
C:\Program Files (x86)\Cyberark\PSM\Vault
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM\Vault" now owned by the administrators group.
7
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM\Vault" now owned by the administrators group.
C:\Program Files (x86)\Cyberark\PSM\Vault
C:\Program Files (x86)\Cyberark\PSM\Vault
C:\Program Files (x86)\Cyberark\PSM\Vault
C:\Program Files (x86)\Cyberark\PSM\Recordings
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM\Recordings" now owned by the administrators group.
8
C:\Program Files (x86)\Cyberark\PSM\Recordings
C:\Program Files (x86)\Cyberark\PSM\Logs
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM\Logs" now owned by the administrators group.
9
C:\Program Files (x86)\Cyberark\PSM\Logs\Components
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM\Logs\Components" now owned by the administrators group.
10
C:\Program Files (x86)\Cyberark\PSM\Components
SUCCESS: The file (or folder): "C:\Program Files (x86)\Cyberark\PSM\Components" now owned by the administrators group.
11
processed file: C:\Program Files (x86)\Cyberark\PSM\Components
Successfully processed 1 files; Failed processing 0 files
C:\oracle
processed dir: C:\oracle
C:\oracle
True
C:
processed dir: C:\
processed file: C:\
Successfully processed 1 files; Failed processing 0 files
D:
processed dir: D:\
processed file: D:\
Successfully processed 1 files; Failed processing 0 files
SUCCESS: The file (or folder): "C:\Program Files (x86)\CyberArk\Password Manager" now owned by the administrators group.
12
C:\Program Files (x86)\CyberArk\Password Manager
C:\Program Files (x86)\CyberArk\Password Manager
C:\Program Files (x86)\CyberArk\Password Manager
SUCCESS: The file (or folder): "C:\WindowsAzure" now owned by the administrators group.
13
C:\WindowsAzure
C:\WindowsAzure
C:\WindowsAzure
SUCCESS: The file (or folder): "C:\Packages" now owned by the administrators group.
14
C:\Packages
C:\Packages
C:\Packages
Executing (\\VM-NETSEC-Test-1\root\CIMV2\TerminalServices:Win32_TSPermissionsSetting.TerminalName="RDP-Tcp")->AddAccount()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\CIMV2\TerminalServices:Win32_TSPermissionsSetting.TerminalName="RDP-Tcp")->AddAccount()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
Executing (\\VM-NETSEC-Test-1\root\cimv2\TerminalServices:Win32_TSAccount.AccountName="VM-NETSEC-Test-1\\PSMAdminConnect",TerminalName="RDP-Tcp")->ModifyPermissions()
Method execution successful.
Out Parameters:
instance of __PARAMETERS
{
ReturnValue = 0;
};
[SC] ChangeServiceConfig SUCCESS
[SC] OpenService FAILED 1060:
The specified service does not exist as an installed service.
WinSCP password storing has been disabled
CyberArk Hardening script ended successfully.
---
End of PSM Hardening script output
All tasks completed.
Onboarding Azure AD Accounts with MFA
RDS License - Remote Desktop Service
Step 1: Win key + R
Step 2: Type in regedit and click ok
Step 3: Navigate to this folder path
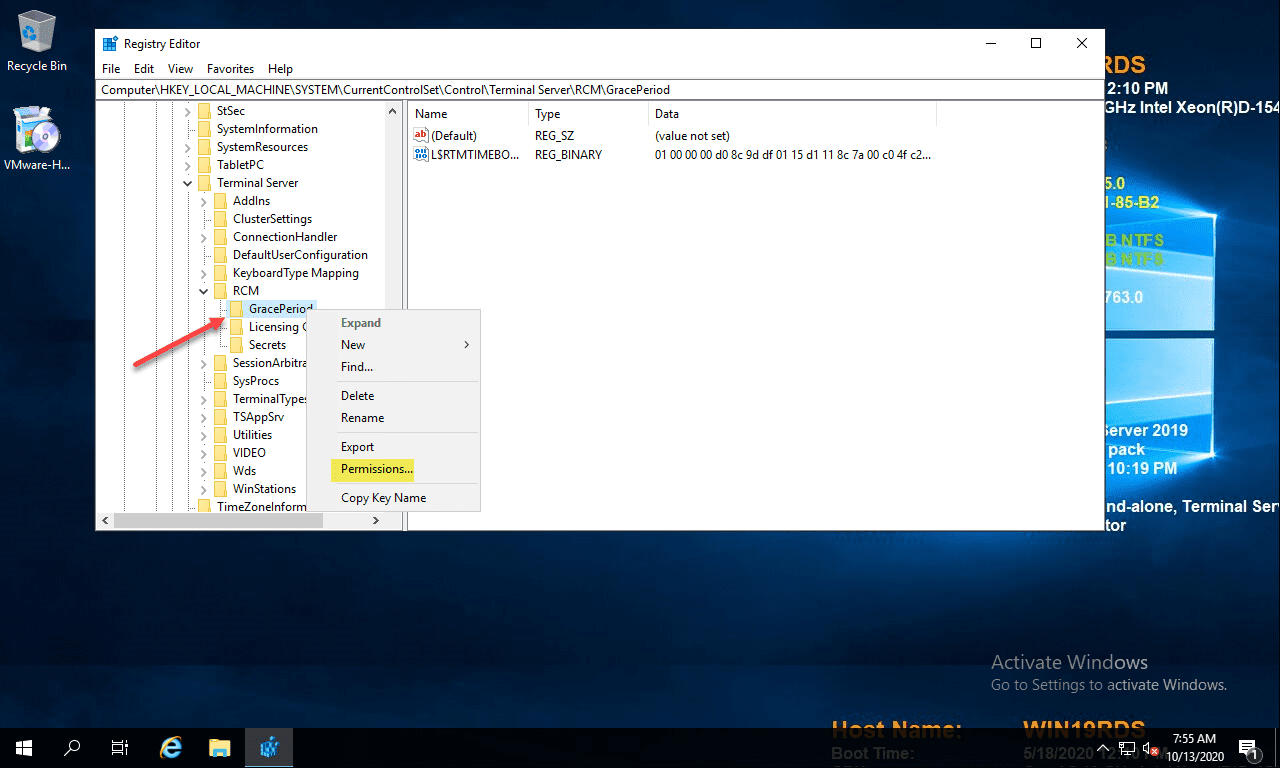
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Terminal Server\RCM\GracePeriod
Step 4: Delete the REG_BINARY
Change Permissions on the RDS GracePeriod key and delete the key
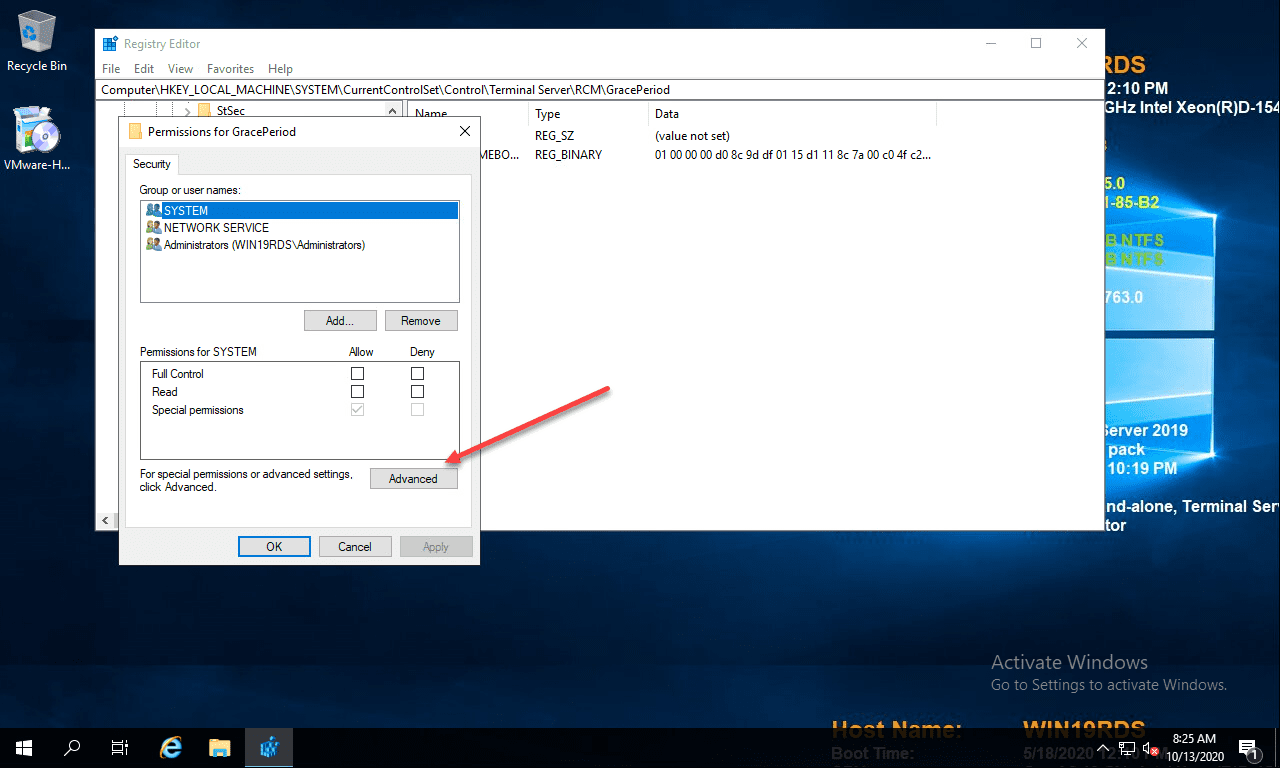
Open a command prompt, and type regedit. After you have navigated to the key documented above, right-click GracePeriod and select Permissions.
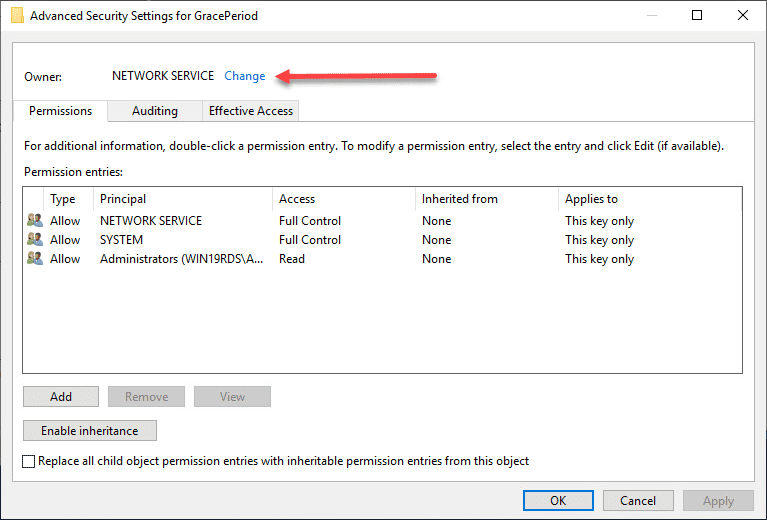
For obvious reasons, there are no default permissions on this key for even Administrators. So you have to first take ownership of the key before you can delete the timebomb value. Click the Advanced button on the permissions dialog box.
Click the Change button next to the Owner.
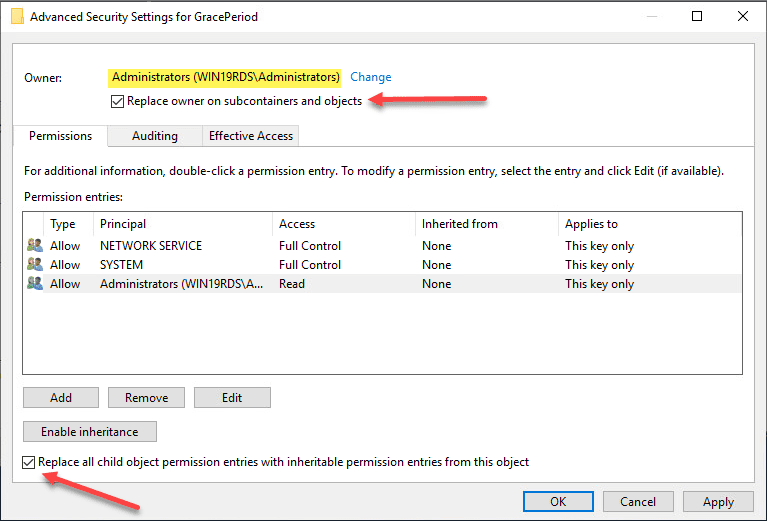
Here I have selected local administrators group as the owner of the key. However, you will want to choose whichever user/group you want to use to delete the registry key. Select the options to replace owners and replace all child object permissions.
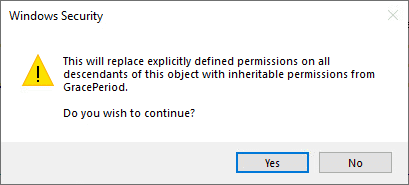
Confirm the replacement of permissions on the registry key.
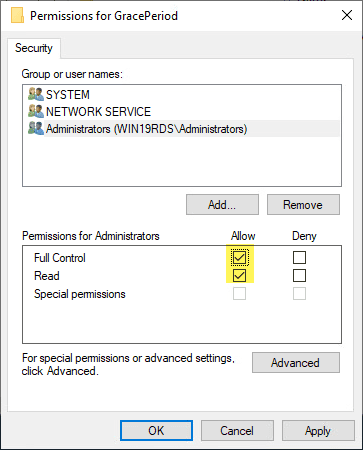
Now that we have changed ownership on the key, we can actually set permissions without getting permissions errors. Here I am granting administrators full control on the key.
Troubleshooting
PS C:\Installation\Add-PSMApps> Get-WinEvent -LogName "Microsoft-Windows-AppLocker/EXE and DLL" |Where-Object {$_.LevelDisplayName -ne "Information"} |Format-Table -AutoSize| Out-File C:\AppLocker.txt -Width 1000
PS C:\Installation\Add-PSMApps> type c:\AppLocker.txt
ProviderName: Microsoft-Windows-AppLocker
TimeCreated Id LevelDisplayName Message
----------- -- ---------------- -------
9/7/2023 7:15:16 PM 8004 Error %WINDIR%\SHELLCOMPONENTS\TASKFLOWUI.DLL was prevented from running.
9/7/2023 7:15:16 PM 8004 Error %WINDIR%\SHELLEXPERIENCES\TILECONTROL.DLL was prevented from running.
9/7/2023 7:15:16 PM 8004 Error %WINDIR%\SHELLCOMPONENTS\WINDOWSINTERNAL.COMPOSABLESHELL.EXPERIENCES.SWITCHER.DLL was prevented from running.
9/7/2023 7:15:16 PM 8004 Error %SYSTEM32%\WLRMDR.EXE was prevented from running.
9/7/2023 7:15:12 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:15:12 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:54 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:54 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:54 PM 8004 Error %PROGRAMFILES%\CYBERARK\PSM\COMPONENTS\CHROMEDRIVER.EXE was prevented from running.
9/7/2023 7:14:53 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:53 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:52 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:52 PM 8004 Error %WINDIR%\ASSEMBLY\NATIVEIMAGES_V4.0.30319_32\MSCORLIB\FAF93F57AA8C4C5DDDD9CD0DE441D5A1\MSCORLIB.NI.DLL was prevented from running.
9/7/2023 7:14:47 PM 8004 Error %SYSTEM32%\SETHC.EXE was prevented from running.
9/7/2023 7:14:47 PM 8004 Error %SYSTEM32%\SVCHOST.EXE was prevented from running.
9/7/2023 7:14:47 PM 8004 Error %SYSTEM32%\SVCHOST.EXE was prevented from running.
9/7/2023 7:14:46 PM 8004 Error %SYSTEM32%\SVCHOST.EXE was prevented from running.
9/7/2023 7:14:46 PM 8004 Error %SYSTEM32%\CTFMON.EXE was prevented from running.
9/7/2023 7:14:46 PM 8004 Error %SYSTEM32%\CMD.EXE was prevented from running.
PS C:\Installation\Add-PSMApps>
Manual change:
C:\Program Files (x86)\Cyberark\PSM\Hardening\PSMConfigureAppLocker.xml
<?xml version="1.0" encoding="utf-8"?>
<PSMAppLockerConfiguration>
<GeneralConfiguration>
<!-- SetAutoAndStart: To start the Application Identity service and set it to automatic startup -->
<!-- mode, set this attribute's value to 'true'. Valid values: true/false. -->
<ServiceConfiguration SetAutoAndStart="true" />
<RuleCollections>
<!-- For each rule collection, you can define the following parameters: -->
<!-- Enforce: To block applications of the relevant collection, set this attribute's value to -->
<!-- 'true'. To prevent AppLocker from blocking applications of the relevant type, set this -->
<!-- attribute's value to 'false'. -->
<!-- Action: To apply new AppLocker configurations and lose any existing settings, set this -->
<!-- attribute's value to 'override'. To merge new configurations with the existing -->
<!-- settings, set this attribute's value to 'merge'. -->
<Executable Enforce="true" Action="Override" />
<WindowsInstaller Enforce="true" Action="Override" />
<Script Enforce="true" Action="Override" />
<PackagedApp Enforce="true" Action="Override" />
<DLL Enforce="true" Action="Override" />
</RuleCollections>
</GeneralConfiguration>
<!-- This part is internal and should not be modified unless instructed to by CyberArk professional -->
<!-- services. -->
<!-- InternalApplications section is directed for PSMConnect and PSMAdminConnect. -->
<!-- SessionType index: "Admin" for PSMAdminConnect, "Regular" for PSMConnect, "*" for both. -->
<InternalApplications>
<Application Name="PSMInitSession" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMInitSession.exe" Method="Hash" />
<Application Name="PSMRDPClient" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMRDPClient.exe" Method="Hash" />
<Application Name="PSMSessionAlert" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSessionAlert.exe" Method="Hash" />
<Application Name="PSMSuspendSession" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSuspendSession.exe" Method="Hash" />
<Application Name="PSMMessageAlert" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMMessageAlert.exe" Method="Hash" />
<Application Name="PSMLauncher" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMLauncher.exe" Method="Hash" />
<Application Name="PSMLiveMonitoringClient" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMLiveMonitoringClient.exe" Method="Hash" />
<Application Name="PSMSessionSignalStatusNotification" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSessionSignalStatusNotification.exe" Method="Hash" />
<Application Name="PSMWindowsEventsLogger" Type="Exe" SessionType="*" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMWindowsEventsLogger.exe" Method="Hash" />
<Application Name="UserInit" Type="Exe" SessionType="*" Path="c:\windows\system32\userinit.exe" Method="Publisher" />
<Application Name="SplWOW64" Type="Exe" SessionType="*" Path="c:\windows\splwow64.exe" Method="Publisher" />
<Application Name="RDPClip" Type="Exe" SessionType="*" Path="c:\windows\system32\rdpclip.exe" Method="Publisher" />
<Application Name="TSTheme" Type="Exe" SessionType="*" Path="c:\windows\system32\tstheme.exe" Method="Publisher" />
<Application Name="ConsoleHost" Type="Exe" SessionType="*" Path="c:\windows\system32\conhost.exe" Method="Publisher" />
<Application Name="TaskHost" Type="Exe" SessionType="*" Path="c:\windows\system32\taskhostw.exe" Method="Publisher" />
<Application Name="ErrorReporting" Type="Exe" SessionType="*" Path="c:\windows\system32\WERMGR.EXE" Method="Publisher" />
<Application Name="TSShadow" Type="Exe" SessionType="Admin" Path="c:\windows\system32\mstsc.exe" Method="Publisher" />
<Application Name="RDPSA" Type="Exe" SessionType="Regular" Path="c:\windows\system32\RDPSA.EXE" Method="Publisher" />
<Application Name="RDPSAPROXY" Type="Exe" SessionType="Regular" Path="c:\windows\system32\RDPSAPROXY.exe" Method="Publisher" />
<Application Name="RDPInit" Type="Exe" SessionType="*" Path="c:\windows\system32\rdpinit.exe" Method="Publisher" />
<Application Name="RDPShell" Type="Exe" SessionType="*" Path="c:\windows\system32\rdpshell.exe" Method="Publisher" />
<Application Name="Sihost" Type="Exe" SessionType="*" Path="c:\windows\system32\sihost.exe" Method="Publisher" />
<!-- Added to support win 2016 -->
<Application Name="RunOnce" Type="Exe" SessionType="*" Path="c:\windows\system32\runonce.exe" Method="Publisher" />
<!-- Added to support RemoteApp on first login -->
<Application Name="PSMTicketingValidationPage" SessionType="*" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMTicketValidator.exe" Method="Hash" />
<!-- Allowed DLLs -->
<!-- If Dll Whitelist is deployed, the following dlls will be allowed -->
<Libraries Name="ComponentsFolder" Type="Dll" Path="C:\Program Files (x86)\CyberArk\PSM\Components\*" Method="Path" SessionType="*" />
<Libraries Name="System32" Type="Dll" Path="%SYSTEM32%\*" Method="Path" SessionType="*" />
<Libraries Name="WinSxS" Type="Dll" Path="%WINDIR%\WINSXS\*" Method="Path" SessionType="*" />
<Libraries Name="DotNetFramework32Bit" Type="Dll" Path="%WINDIR%\Microsoft.NET\Framework\v4.0.30319\*" Method="Path" SessionType="*" />
<Libraries Name="DotNetFramework64Bit" Type="Dll" Path="%WINDIR%\Microsoft.NET\Framework64\v4.0.30319\*" Method="Path" SessionType="*" />
</InternalApplications>
<!-- AllowedApplications section is directed for PSMShadowUsers -->
<AllowedApplications>
<!-- For each allowed application, specify the following attributes: -->
<!-- Name: Name of the application for log proposes. Valid values: Any string value. -->
<!-- Type: Type of application to allow. Valid values: Exe/Script. -->
<!-- Path: Path of the application executable. Valid values: exact application path, -->
<!-- wildcards are allowed only if the chosen method is "Path". -->
<!-- Method: The chosen identification method for the application. -->
<!-- Valid values: Path/Hash/Publisher -->
<!-- PSM Components -->
<Application Name="PSMSSHClient" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSSHClient.exe" Method="Hash" />
<Application Name="PSMPrivateArkClientDispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMPrivateArkClientDispatcher.exe" Method="Hash" />
<Application Name="PSMPVWADispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMPVWADispatcher.exe" Method="Hash" />
<Application Name="MSSQLManagementStudioWindowsAuthenticationDispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\MSSQLManagementStudioWindowsAuthenticationDispatcher.exe" Method="Hash" />
<Application Name="PSM3270Client" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSM3270Client.exe" Method="Hash" />
<Application Name="PSMWebFormDispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMWebFormDispatcher.exe" Method="Hash" />
<Application Name="PSMWinSCPDispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMWinSCPDispatcher.exe" Method="Hash" />
<Application Name="WinSCP" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\WinSCP.exe" Method="Hash" />
<Application Name="PSMRealVNCDispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMRealVNCDispatcher.exe" Method="Hash" />
<Application Name="PSMXFocus" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMXFocus.exe" Method="Hash" />
<Application Name="PSMTokenHolder" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMTokenHolder.exe" Method="Hash" />
<Application Name="PSMSessionAlert" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSessionAlert.exe" Method="Hash" />
<Application Name="PSMSuspendSession" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSuspendSession.exe" Method="Hash" />
<Application Name="PSMPreventWindowHide" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMPreventWindowHide.exe" Method="Hash" />
<Application Name="PSMMessageAlert" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMMessageAlert.exe" Method="Hash" />
<Application Name="PSMWindowsEventsLogger" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMWindowsEventsLogger.exe" Method="Hash" />
<Application Name="PSM-WebAppDispatcher" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\CyberArk.PSM.WebAppDispatcher.exe" Method="Hash" />
<Application Name="DLLInjector" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\DLLInjector.exe" Method="Hash" />
<Application Name="DLLInjector64" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\DLLInjector64.exe" Method="Hash" />
<Application Name="PSM-ProgressBar" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\CyberArk.ProgressBar.exe" Method="Hash" />
<Application Name="PSMTicketingValidationPage" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMTicketValidator.exe" Method="Hash" />
<!-- Microsoft session processes -->
<Application Name="ConsoleHost" Type="Exe" Path="c:\windows\system32\conhost.exe" Method="Publisher" />
<Application Name="TaskHost" Type="Exe" Path="c:\windows\system32\taskhostw.exe" Method="Publisher" />
<Application Name="ErrorReporting" Type="Exe" Path="c:\windows\system32\WERMGR.EXE" Method="Publisher" />
<!-- Oracle connection clients -->
<!-- If relevant, uncomment this part after installing Oracle client and Toad.
<Application Name="Toad" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\toad.exe" Method="Publisher,Hash" />
<Application Name="SQLPlus" Type="Exe" Path="c:\oracle\instantclient\sqlplus.exe" Method="Hash" />
<Application Name="Notepad" Type="Exe" Path="c:\windows\system32\notepad.exe" Method="Publisher"/>
<Application Name="SDFConverter" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\ClientFiles\ScriptMgr\SDFConverter.exe" Method="Hash" />
<Application Name="QuestScriptRunner" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\qsr.exe" Method="Hash" />
<Application Name="OptimizerEngine" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\OptimizerEngine.exe" Method="Hash" />
<Application Name="FormatOptions" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\FmtOptions.exe" Method="Hash" />
<Application Name="ToadScriptRuntime" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\tsr.exe" Method="Hash" />
<Application Name="UninstallClientFiles" Type="Exe" Path="C:\Program Files (x86)\Quest Software\Toad for Oracle 10.6\UninstallClientFiles.exe" Method="Hash" />
End of oracle connections comment -->
<!-- vSphere client processes -->
<!-- If relevant, uncomment this part after installing vSphere client (including .Net framework 2 and 3.5).
<Application Name="VpxClient" Type="Exe" Path="C:\Program Files (x86)\VMware\Infrastructure\Virtual Infrastructure Client\Launcher\VpxClient.exe" Method="Hash" />
<Application Name="VMWare-VMRC" Type="Exe" Path="C:\Program Files (x86)\VMWARE\INFRASTRUCTURE\VIRTUAL INFRASTRUCTURE CLIENT\4.0\VMWARE-VMRC.EXE" Method="Publisher" />
<Application Name="VMWare-RemoteMKS.EXE" Type="Exe" Path="C:\Program Files (x86)\VMWARE\INFRASTRUCTURE\VIRTUAL INFRASTRUCTURE CLIENT\4.0\VMWARE-REMOTEMKS.EXE" Method="Publisher" />
<Application Name="CSC" Type="Exe" Path="c:\windows\MICROSOFT.NET\FRAMEWORK\V2.0.50727\CSC.EXE" Method="Publisher" />
<Application Name="CVTRES" Type="Exe" Path="c:\windows\MICROSOFT.NET\FRAMEWORK\V2.0.50727\CVTRES.EXE" Method="Publisher" />
End of vSphere client comment -->
<!-- SQL Server Management Studio 2012 processes -->
<!-- If relevant, uncomment this part after installing SQL Server Management Studio 2012 processes
<Application Name="SSMS2012" Type="Exe" Path="C:\Program Files (x86)\Microsoft SQL Server\110\Tools\Binn\ManagementStudio\Ssms.exe" Method="Publisher" />
End of SQL Server Management Studio 2012 processes comment -->
<!-- SAP GUI processes -->
<!-- If relevant, uncomment this part after installing SAP GUI processes and downloading the CyberArk PSMSAPGUI connection component from the Marketplace
<Application Name="PSMSAPGUI" Type="Exe" Path="C:\Program Files (x86)\CyberArk\PSM\Components\PSMSAPGUI.exe" Method="Hash" />
<Application Name="saplogon" Type="Exe" Path="C:\Program Files (x86)\SAP\FrontEnd\SAPgui\saplogon.exe" Method="Hash" />
<Application Name="SAPgui" Type="Exe" Path="C:\Program Files (x86)\SAP\FrontEnd\SAPgui\SAPgui.exe" Method="Hash" />
End of SAP GUI processes comment -->
<!-- X Forwarding X Server processes -->
<Application Name="VcXsrv" Type="Exe" Path="C:\Program Files (x86)\VcXsrv\vcxsrv.exe" Method="Hash" />
<Application Name="xkbcomp" Type="Exe" Path="C:\Program Files (x86)\VcXsrv\xkbcomp.exe" Method="Hash" />
<!-- Microsoft IExplore processes -->
<!-- If relevant, uncomment this part to allow webform based connection clients -->
<Application Name="IExplore32" Type="Exe" Path="c:\Program Files (x86)\Internet Explorer\iexplore.exe" Method="Publisher" />
<Application Name="IExplore64" Type="Exe" Path="c:\Program Files\Internet Explorer\iexplore.exe" Method="Publisher" />
<!-- End of Microsoft IExplore processes comment -->
<!-- Google Chrome process -->
<!-- If relevant, uncomment this part to allow Google Chrome webform based connection clients
<Application Name="GoogleChrome" Type="Exe" Path="C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" Method="Publisher" />
End of Google Chrome process comment -->
<!-- Microsoft Edge process -->
<!-- If relevant, uncomment this part to allow Edge webform based connection clients
<Application Name="Edge" Type="Exe" Path="C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" Method="Publisher" />
End of Microsoft Edge process comment -->
<!-- Generic client support -->
<!-- If relevant, uncomment this part to allow generic clients support and add a rule for each generic connection client
<Application Name="GenericClient-Sample" Type="Exe" Path="C:\VNC-Viewer-5.0.5-Windows-64bit.exe" Method="Hash" />
End of Generic client support comment -->
<!-- Google Chrome section -->
<Application Name="Chrome" Type="Exe" Path="C:\Program Files (x86)\Google\Chrome\Application\chrome.exe" Method="Publisher" />
<Application Name="ChromeDriver" Type="Exe" Path="C:\Program Files (x86)\Cyberark\PSM\Components\chromedriver.exe" Method="Path" />
<!-- End of Google Chrome section -->
<!-- Allowed DLLs -->
<!-- If Dll Whitelist is deployed, the following dlls will be allowed -->
<Libraries Name="ComponentsFolder" Type="Dll" Path="C:\Program Files (x86)\CyberArk\PSM\Components\*" Method="Path" />
<Libraries Name="System32" Type="Dll" Path="%SYSTEM32%\*" Method="Path" />
<Libraries Name="WinSxS" Type="Dll" Path="%WINDIR%\WINSXS\*" Method="Path" />
<Libraries Name="DotNetFramework32Bit" Type="Dll" Path="%WINDIR%\Microsoft.NET\Framework\v4.0.30319\*" Method="Path" />
<Libraries Name="DotNetFramework64Bit" Type="Dll" Path="%WINDIR%\Microsoft.NET\Framework64\v4.0.30319\*" Method="Path" />
<Libraries Name="DotNetFrameworkGAC" Type="Dll" Path="%WINDIR%\Microsoft.NET\assembly\*" Method="Path" />
<Libraries Name="VcXsrv" Type="Dll" Path="%PROGRAMFILES%\VcXsrv\*" Method="Path" />
</AllowedApplications>
</PSMAppLockerConfiguration>
Open PowerShell in C:\Program Files (x86)\CyberArk\PSM\Hardening and run the following command to start the script:
“.\PSMConfigureAppLocker.ps1” |
Note: https://docs.cyberark.com/PAS/Latest/en/Content/PAS%20INST/Install_ConfigurePSMServerMachineForWebApps.htm#Configur
2. Add user into Safe Member
Got an error : Object reference not set to an instance of an object.
Videos
CyberArk Useful Links
References
- Microsoft Azure Password Management
- Microsoft Azure Application Keys
- Microsoft Azure Application Keys Online Help
- Add Azure Active Directory as a directory service
- How to remove "automated test software" prompt in PSM webconnectors: https://cyberark-customers.force.com/s/article/PSM-web-application-shows-Chrome-is-being-controlled-by-automated-test-software-with-Chrome-98
- Set Edge to be browser for PSM: https://cyberark-customers.force.com/s/article/How-to-change-PSM-WebApp-to-use-Edge
- Plugin Generator Utility for mapping web sites to PSM connectors: https://cyberark-customers.force.com/mplace/s/#a3550000000EiC4AAK-a3950000000jjUeAAI
- Add additional apps with add-psmapps: https://cyberark-customers.force.com/s/article/How-to-use-Add-PSMApplication
- Configure WebDriverUpdate tool on each connector server: https://cyberark-customers.force.com/mplace/s/#a35Ht000000rjXlIAI-a39Ht000001kceVIAQ
- https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/MSAzurePasswordManagement.htm?tocpath=Administrator%7CComponents%7CCentral%20Policy%20Manager%7CCPM%20plugins%7CTarget%20account%20plugins%7CCloud%20services%7C_____3#Logon
- https://docs.cyberark.com/Product-Doc/OnlineHelp/PAS/Latest/en/Content/PASIMP/MicrosoftAzureApplicationKeys.htm?tocpath=Administrator%7CComponents%7CCentral%20Policy%20Manager%7CCPM%20plugins%7CTarget%20account%20plugins%7CCloud%20services%7C_____4
























No comments:
Post a Comment