This post is to summarize the steps and notes regarding FortiClient's advanced features
SSL VPN Types
There are two major types of SSL VPNs:SSL Portal VPN
In this type of SSL VPN, a user visits a website and enters credentials to initiate a secure connection. The SSL portal VPN allows for a single SSL connection to a website. Additionally, the user can access a variety of specific applications or private network services as defined by the organization.Users can typically enter the gateway, or the hardware on a network that allows data to flow from one network to another, using any modern web browser, by entering the username and password provided by the VPN gateway service.
SSL Tunnel VPN
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet. This VPN tunneling technology may require a browser with additional applications, such as JavaScript or Flash, installed to display active content.SSL-VPN Web and Tunnel Mode
Notes: https://video.fortinet.com/products/fortigate/5.4/cookbook-ssl-vpn-web-and-tunnel-mode-5-4#:~:text=Web%20Mode%20allows%20users%20to,FortiGate's%20security%20policies%20and%20profiles.
Basically, Web Mode is the mode your vpn user can use browser to access those internal or internet resources.
Tunnel mode, is the mode your vpn users use FortiClient to access internal or internet resources.
FGT # get vpn ssl monitor
SSL-VPN Login Users:
|Index|User|Group|Auth Type|Idle-Timeout|Auth-Timeout|From|HTTP in/out|HTTPS in/out|Two-factor Auth|
|0|Vla|Remote Users|1(1)|272|20884|5.17.102.10|0/0|0/0|0|
|1|And|Remote Users|1(1)|296|24733|5.17.102.10|0/0|0/0|0|
|2|Jos|Remote Users|1(1)|296|25470|5.17.102.10|0/0|0/0|0|
SSL-VPN sessions:
|Index|User|Group|Source IP|Duration|I/O Bytes|Tunnel/Dest IP|
|0|VldKioSoft|Remote Users|5.17.102.10|7917|867941/2664146|10.212.134.200|
|1|And|Remote Users|5.17.102.10|4067|418632/1082959|10.212.134.201|
|2|Jos|Remote Users|5.17.102.10|3331|143730/11424|10.212.134.202|
SSL-VPN Web Mode and Bookmarks
Bookmark is the shortcut for internal resources.
Edit full-access portal.
The legacy SSL-VPN web mode feature is disabled globally. Web mode will not be accessible in portals.
SSL VPN connection logout after 8 hours : auth-timeout, idle-timeout
The default value is 28800 seconds (8 hours). The value can be between <0> to <259200>
A value of 0 indicates no timeout.
Note:
- https://community.fortinet.com/t5/FortiGate/Technical-Tip-SSL-VPN-connection-logout-after-8-hours/ta-p/191322
- https://community.fortinet.com/t5/FortiGate/Technical-Tip-SSL-VPN-timers-explanation-and-SSL-VPN-Login/ta-p/203615
Advanced Features: Auto Connect, Always Up
Feature | Description |
|---|---|
Save Password | Allows the user to save the VPN connection password in FortiClient |
Auto Connect | When FortiClient launches, the VPN connection automatically connects. Automatic connection to the VPN tunnel may fail if the endpoint boots up with a user profile set to automatic logon. See Appendix E - VPN autoconnect for configuration examples. |
Always Up (Keep Alive) | When selected, the VPN connection is always up. If the connection fails, possibly due to network errors, FortiClient attempts to reconnect. If credentials (username and password) are saved, FortiClient attempts to reconnect silently. If credentials are insufficient (for instance, multifactor authentication is required or password is not saved), FortiClient prompts for credentials. |
Note:
The following features are not supported in the FortiClient v6.2.X - v7.0.12, v7.2.X and v7.4.X free versions:
- VPN auto-connect/always-up.
- VPN before logon.
- On-net/off-net.
- Host check features.
- Central management
- No feedback option & no diagnostic tool under help/info page.
- IKEv2 is not supported on FortiClient 6.2.x free version.
- TAC support.
SSL VPN user connectivity logs
https://community.fortinet.com/t5/FortiGate/Technical-Tip-View-historic-SSL-VPN-user-connectivity-logs/ta-p/192081The historic logs for users connected through SSL VPN can be viewed under a different location depending on the FortiGate version:
- Log & Report -> VPN Events in v6.0.x.
- Log & Report -> Events and select 'VPN Events' in 6.2.x and 7.0.x
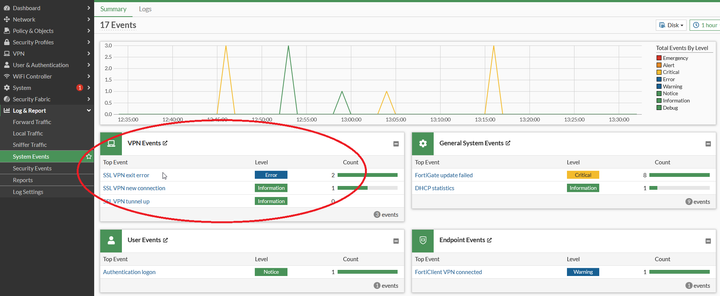
- Log & Report -> System Events and select 'VPN Events' in 7.2.x and 7.4.x.
- FortiOS v7.2.x and v7.4.x:
Note:
Make sure that the VPN activity event is enabled.
To log VPN events from the GUI:
- Go to Log & Report -> Log Settings.
- Verify that the VPN activity event option is selected.
- Select Apply.

Monitor SSL VPN User
https://www.reddit.com/r/fortinet/comments/10jlcmo/how_to_monitor_sslvpn_login_activity_or_get/security fabric -> automation
create trigger:
1.) "FortiOS Event Log" type
2.) "SSL VPN tunnel up"
create ation:
1.) configure "from", "to" and "Subject" as desired, leave everything else
create stitch:
choose the new trigger and action we created
you can do the same with ANY fortios event log event
References
- https://www.fortinet.com/resources/cyberglossary/ssl-vpn


















No comments:
Post a Comment