 V2Ray, short for "V2-Project Ray," is an open-source network protocol that aims to provide users with enhanced privacy, security, and anonymity while navigating the digital realm. Essentially, V2Ray serves as a versatile tool for bypassing censorship, encrypting internet traffic, and accessing geo-restricted content. Unlike traditional VPNs and proxies, V2Ray operates on a more sophisticated level, offering a broader range of features and customization options.
V2Ray, short for "V2-Project Ray," is an open-source network protocol that aims to provide users with enhanced privacy, security, and anonymity while navigating the digital realm. Essentially, V2Ray serves as a versatile tool for bypassing censorship, encrypting internet traffic, and accessing geo-restricted content. Unlike traditional VPNs and proxies, V2Ray operates on a more sophisticated level, offering a broader range of features and customization options.V2rayN provides a few features that make it easier to use V2Ray. It allows users to quickly switch between different servers, set up custom routing rules, and monitor their connection status. It also provides a few additional features such as automatic connection and the ability to export and import configuration files.
- https://github.com/vfarid/v2ray-worker
- https://github.com/Vauth/vless-cf
- https://github.com/51sec/ss_generator
V2rayN Features
Supports V2Ray, Shadowsocks, Trojan and VMess protocols. Offers support for multiple servers and custom routing rules. Configuration file import and export support. Supports many different obfuscation methods like HTTP/2, QUIC and WebSocket.Vless protocol:
如上图所示,展示四种不同配置的封装原理,每个协议从左到右是逐级解包过程,最后还原出原始的数据请求包,通常解包过程发生在数据接收端;而从右到左打包过程,最后打包成Tcp数据包,通常打包过程发生在数据发送端。计算机网络通信端到端通常发送的数据包是TCP数据包或UDP数据包。
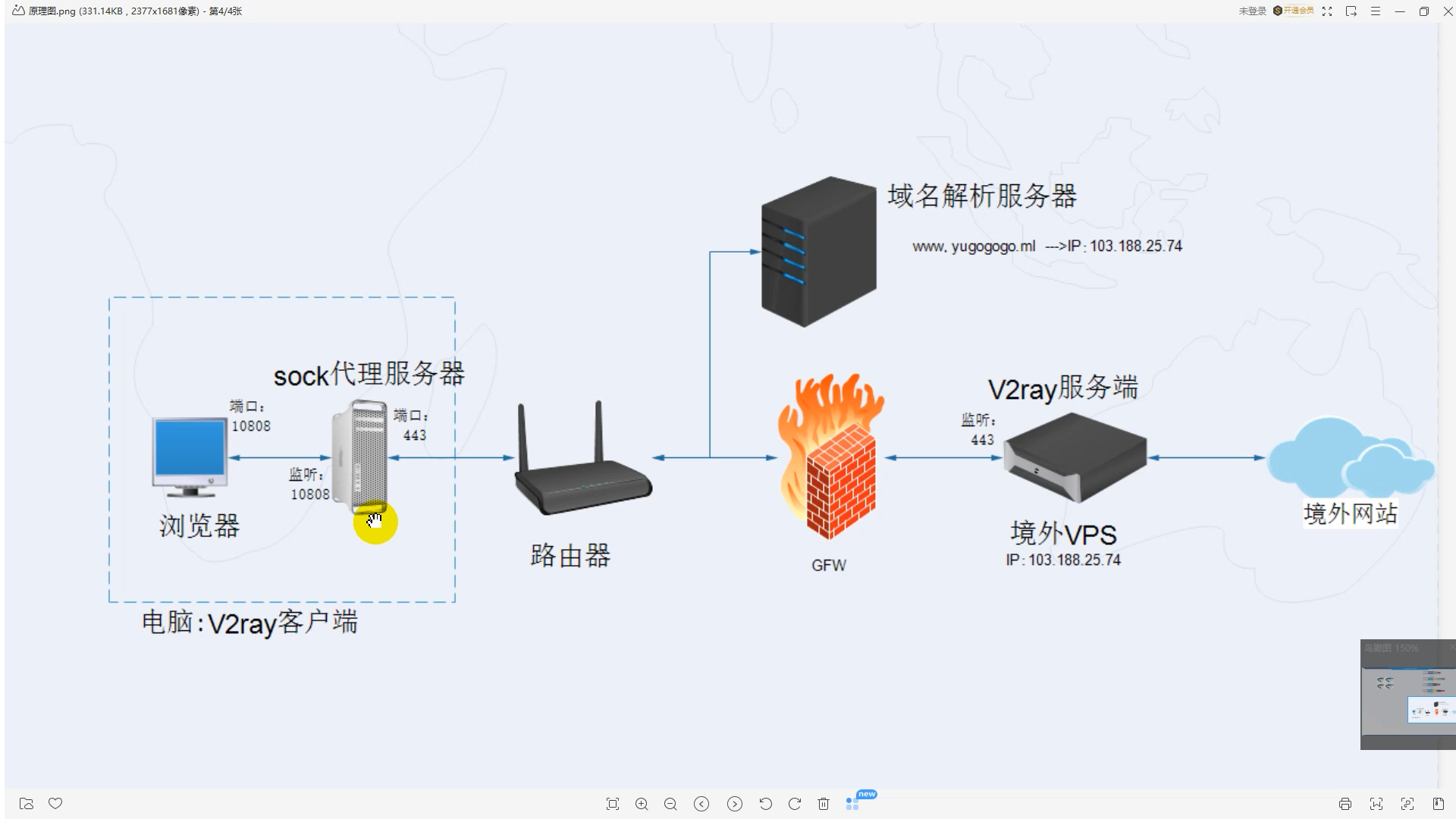
{浏览器} <--(socks)--> {V2Ray 客户端 inbound <-> V2Ray 客户端 outbound} <--(Vless)--> {V2Ray 服务器 inbound <-> V2Ray 服务器 outbound} <--(Freedom)--> {目标网站}
这就是整个通信的原理,只不过联网的电脑需要通过互联网的域名解析服务器帮助解析通信的目标域名,即www.yugogogo.ml绑定的IP是多少。域名好比通信录的姓名,而电话号码好比ip地址。
How to Download and Which one to Download
1 Go to release page
Release Page: Github release page V2rayN
Or other download page:
v2fly/xray Clients
v2fly/xray Windows Client v2rayN
xray Android App v2rayNG
v2fly Android App v2flyNG
clash 客户端
clash Windows客户端 clashN
2 You can choose pre-release version or latest release version
Click version number, here we are using version 7.0.6 as an example
3 Select the right file to download.
I am using Windows OS, and usually go with
4 Download and extract the file. Double click v2rayN.exe file to start this V2ray client.
Get free web service from sshOcean
Creae a server in V2rayN
Since we have copied our v2ray VLESS link, we can choose import shared links from Clipboard this option:Configuration successful
[VLESS] sshocean-netsec.cagmail.com-ws(hu2***site:443)
Microsoft Windows NT 10.0.19045.0 - 64
Start service (2024/11/03 14:15:06)...
Xray 24.10.31 (Xray, Penetrates Everything.) 4ec5c78 (go1.23.2 windows/amd64)
A unified platform for anti-censorship.
2024/11/03 14:15:06 Using default config: C:\Users\User\Downloads\v2rayN-windows-64-SelfContained-With-Core\v2rayN-windows-64-SelfContained-With-Core\guiConfigs\config.json
2024/11/03 14:15:06 [Info] infra/conf/serial: Reading config: &{Name:C:\Users\User\Downloads\v2rayN-windows-64-SelfContained-With-Core\v2rayN-windows-64-SelfContained-With-Core\guiConfigs\config.json Format:json}
2024/11/03 14:15:07 [Warning] core: Xray 24.10.31 started
2024/11/03 14:15:07 from 127.0.0.1:4018 accepted //www.google.com:443 [http -> proxy]
2024/11/03 14:15:09 The ping of current service: 112 ms
Configuration successful
[VLESS] sshocean-netsec.cagmail.com-ws(hu2***site:443)
Microsoft Windows NT 10.0.19045.0 - 64
Start service (2024/11/03 14:15:15)...
Xray 24.10.31 (Xray, Penetrates Everything.) 4ec5c78 (go1.23.2 windows/amd64)
A unified platform for anti-censorship.
2024/11/03 14:15:15 Using default config: C:\Users\User\Downloads\v2rayN-windows-64-SelfContained-With-Core\v2rayN-windows-64-SelfContained-With-Core\guiConfigs\config.json
2024/11/03 14:15:15 [Info] infra/conf/serial: Reading config: &{Name:C:\Users\User\Downloads\v2rayN-windows-64-SelfContained-With-Core\v2rayN-windows-64-SelfContained-With-Core\guiConfigs\config.json Format:json}
2024/11/03 14:15:16 [Warning] core: Xray 24.10.31 started
2024/11/03 14:15:17 from 127.0.0.1:4037 accepted //www.google.com:443 [http -> proxy]
2024/11/03 14:15:18 from udp:127.0.0.1:54581 accepted udp:8.8.8.8:53 [socks -> proxy]
2024/11/03 14:15:19 The ping of current service: 245 ms
2024/11/03 14:15:19 System proxy setting is changed - ForcedChange
2024/11/03 14:15:19 from 127.0.0.1:9615 accepted //mtalk.google.com:5228 [http -> proxy]
2024/11/03 14:15:20 from 127.0.0.1:9634 accepted //teams.events.data.microsoft.com:443 [http -> proxy]
After done, you can set back the settings of "System Proxy" to Clear system proxy.
Use Google Colab to Generate SS Nodes
sshocean can generate multiple types of secure proxy / vpn servers. But each time you only can get one server. Here is a way you can generate 12 different SS (Shadowsocks) servers at one time.- Github: https://github.com/51sec/ss_generator
import base64
import json
import pyaes
import binascii
from datetime import datetime
a = 'http://api.skrapp.net/api/serverlist'
b = {
'accept': '/',
'accept-language': 'zh-Hans-CN;q=1, en-CN;q=0.9',
'appversion': '1.3.1',
'user-agent': 'SkrKK/1.3.1 (iPhone; iOS 13.5; Scale/2.00)',
'content-type': 'application/x-www-form-urlencoded',
'Cookie': 'PHPSESSID=fnffo1ivhvt0ouo6ebqn86a0d4'
}
c = {'data': '4265a9c353cd8624fd2bc7b5d75d2f18b1b5e66ccd37e2dfa628bcb8f73db2f14ba98bc6a1d8d0d1c7ff1ef0823b11264d0addaba2bd6a30bdefe06f4ba994ed'}
d = b'65151f8d966bf596'
e = b'88ca0f0ea1ecf975'
def f(g, d, e):
h = pyaes.AESModeOfOperationCBC(d, iv=e)
i = b''.join(h.decrypt(g[j:j+16]) for j in range(0, len(g), 16))
return i[:-i[-1]]
j = requests.post(a, headers=b, data=c)
if j.status_code == 200:
k = j.text.strip()
l = binascii.unhexlify(k)
m = f(l, d, e)
n = json.loads(m)
print("youtube.com/netsec")
for o in n['data']:
p = f"aes-256-cfb:{o['password']}@{o['ip']}:{o['port']}"
q = base64.b64encode(p.encode('utf-8')).decode('utf-8')
r = f"ss://{q}#{o['title']}"
print(r)
Use Replit.com to Generate Server List
Log into Replit.com- Github: https://github.com/51sec/ss_generator
import base64
import json
import pyaes
import binascii
from datetime import datetime
a = 'http://api.skrapp.net/api/serverlist'
b = {
'accept': '/',
'accept-language': 'zh-Hans-CN;q=1, en-CN;q=0.9',
'appversion': '1.3.1',
'user-agent': 'SkrKK/1.3.1 (iPhone; iOS 13.5; Scale/2.00)',
'content-type': 'application/x-www-form-urlencoded',
'Cookie': 'PHPSESSID=fnffo1ivhvt0ouo6ebqn86a0d4'
}
c = {'data': '4265a9c353cd8624fd2bc7b5d75d2f18b1b5e66ccd37e2dfa628bcb8f73db2f14ba98bc6a1d8d0d1c7ff1ef0823b11264d0addaba2bd6a30bdefe06f4ba994ed'}
d = b'65151f8d966bf596'
e = b'88ca0f0ea1ecf975'
def f(g, d, e):
h = pyaes.AESModeOfOperationCBC(d, iv=e)
i = b''.join(h.decrypt(g[j:j+16]) for j in range(0, len(g), 16))
return i[:-i[-1]]
j = requests.post(a, headers=b, data=c)
if j.status_code == 200:
k = j.text.strip()
l = binascii.unhexlify(k)
m = f(l, d, e)
n = json.loads(m)
print("youtube.com/netsec")
for o in n['data']:
p = f"aes-256-cfb:{o['password']}@{o['ip']}:{o['port']}"
q = base64.b64encode(p.encode('utf-8')).decode('utf-8')
r = f"ss://{q}#{o['title']}"
print(r)
Use Cloudflare to Generate vless nodes
Github project:- https://github.com/51sec/ss_generator/blob/main/worker2vless.js
- Code has to be obfuscated before deploied to Clouflare workers
- Original one: https://github.com/zizifn/edgetunnel/tree/main/src
- Same, code has to be obfuscated.
- const proxyIPs = ['cdn.xn--b6gac.eu.org', 'cdn-all.xn--b6gac.eu.org', 'workers.cloudflare.cyou'];
-
- // if you want to use ipv6 or single proxyIP, please add comment at this line and remove comment at the next line
- let proxyIP = proxyIPs[Math.floor(Math.random() * proxyIPs.length)];
- // use single proxyIP instead of random
- // let proxyIP = 'cdn.xn--b6gac.eu.org';
- // ipv6 proxyIP example remove comment to use
- // let proxyIP = "[2a01:4f8:c2c:123f:64:5:6810:c55a]"
Two things you might want to change:
1. UUID
2. Proxyip
- aliyun.classelivre.eu.org 天城大佬
- cm.godns.onflashdrive.app 天城大佬
- 3k.fxxk.dedyn.io 3K大佬
- vmess.fxxk.dedyn.io CM大佬
- vless.fxxk.dedyn.io CM大佬
- Can be those popular site, but might cause issue with cloudflare.
- in my example, it is same as 优选IP (Address)
- or it can be your workers domain or your own domain
- 自定义的域名 或者 优选域名 或者 优选IP 或者 反代IP
- it can be changed to any other better ones, such as:
- icook.hk
- default one as show in screenshot: www.visa.com.sg
- in my example, it is same as 伪装域名 (host)
- But it can be different.
- such as www.visa.com:8880 to replace my v.51sec.workers.dev:443
将复制的 V2ray 配置链接粘贴到 V2rayN 客户端,地址填入优选 IP ,即可成功科学上网。优选 IP 可通过 https://stock.hostmonit.com/CloudFlareYes.
- decade00-0000-4000-a000-000000000000
v2ray
---------------------------------------------------------------
vless://[email protected]:443?encryption=none&security=tls&sni=v.51sec.workers.dev&fp=randomized&type=ws&host=v.51sec.workers.dev&path=%2F%3Fed%3D2048#v.51sec.workers.dev
---------------------------------------------------------------
################################################################
clash-meta
---------------------------------------------------------------
- type: vless
name: v.51sec.workers.dev
server: v.51sec.workers.dev
port: 443
uuid: decade00-0000-4000-a000-000000000000
network: ws
tls: true
udp: false
sni: v.51sec.workers.dev
client-fingerprint: chrome
ws-opts:
path: "/?ed=2048"
headers:
host: v.51sec.workers.dev
---------------------------------------------------------------
################################################################yonggekkk/Cloudflare_vless_trojan
In the screenshot, 客户端参数如下:
- 客户端地址(address):自定义的域名 或者 优选域名 或者 优选IP 或者 反代IP
- it can be changed to any other better ones, such as:
- icook.hk
- default one as show in screenshot: www.visa.com.sg
- 端口(port):6个https端口可任意选择(443、8443、2053、2083、2087、2096),或反代IP对应端口
- 用户ID(uuid):786e8ca7-5bc2-48f3-8659-612e0789443a (cusotmized, not default)
- default: 86c50e3a-5b87-49dd-bd20-03c7f2735e40
- 传输协议(network):ws 或者 websocket
- 伪装域名(host):v.51sec1.eu.org
- your own domain, or your workers domain for your this project.
- 路径(path):/?ed=2560
- 传输安全(TLS):开启
- 跳过证书验证(allowlnsecure):false
- Which is built in the code, and will not show in the screenshot.
- You will be able to use variable to control it.
| 变量作用 | 变量名称 | 变量值要求 | 变量默认值 | 变量要求 |
|---|---|---|---|---|
| 1、必要的uuid | uuid (小写字母) | 符合uuid规定格式 | 万人骑uuid:86c50e3a-5b87-49dd-bd20-03c7f2735e40 | 建议 |
| 2、全局节点能上CF类网站 | proxyip (小写字母) | 443端口:ipv4地址、[ipv6地址]、域名。非443端口:IPV4地址:端口、[IPV6地址]:端口、域名:端口 | proxyip域名:ts.hpc.tw公用域名 | 可选 |
| 3、订阅节点:优选IP | ip1到ip13,共13个 | CF官方IP、CF反代IP、CF优选域名 | CF官方不同地区的visa域名 | 可选 |
| 4、订阅节点:优选IP对应端口 | pt1到pt13,共13个 | CF13个标准端口、反代IP对应任意端口 | CF13个标准端口 | 可选 |
Cloudflare Worker Error 1101 / 1103 Issue
Obfuscated Code For workers:
- https://github.com/yonggekkk/Cloudflare_vless_trojan/blob/main/Vless_workers_pages/_worker.js
- uuid
- default: 86c50e3a-5b87-49dd-bd20-03c7f2735e40
- decade00-0000-4000-a000-000000000000
- proxyip
- ts.hpc.tw
- more others you can find from previous sections
Performance Check
Alternatively, you can check the latency via HTTPS request from your browser (different than ping) and verify if your ISP is not blocked or if you will be bypassing the firewall following the URL:
ping falkenstein-lb-1.vs.secologist.comTroubleshooting
Got an error "Failed to start: app/proxyman/inbound: failed to listen TCP on 10808"
Start service (2024/12/18 15:59:18)...
Xray 24.10.31 (Xray, Penetrates Everything.) 4ec5c78 (go1.23.2 windows/amd64)
A unified platform for anti-censorship.
2024/12/18 15:59:18 Using default config: C:\Tools\v2rayN-windows-64-SelfContained-With-Core\guiConfigs\config.json
2024/12/18 15:59:18 [Info] infra/conf/serial: Reading config: &{Name:C:\Tools\v2rayN-windows-64-SelfContained-With-Core\guiConfigs\config.json Format:json}
Failed to start: app/proxyman/inbound: failed to listen TCP on 10808The reason is most likely due to a Windows Update that restricted access to certain ports on Windows machines. The details are here.
You can view a list of which ports are excluded from your user by running this command:
C:\Users\User>netsh interface ipv4 show excludedportrange protocol=tcp
Protocol tcp Port Exclusion Ranges
Start Port End Port
---------- --------
5357 5357
8684 8783
8784 8883
8884 8983
8984 9083
9084 9183
9184 9283
9284 9383
9384 9483
9609 9708
9709 9808
9809 9908
9909 10008
10009 10108
10109 10208
10209 10308
10309 10408
10654 10753
10754 10853
10854 10953
10954 11053
11054 11153
11154 11253
11254 11353
11354 11453
11764 11863
11864 11963
11964 12063
12064 12163
12164 12263
12264 12363
12364 12463
12464 12563
12974 13073
13074 13173
13214 13313
13314 13413
13414 13513
13514 13613
13614 13713
13714 13813
14082 14181
14182 14281
14282 14381
14382 14481
14482 14581
50000 50059 *
* - Administered port exclusions.
Changed from default port 10808 to port 20000 then it works again.
Videos
References
- How to Set up V2rayN on Windows
- 免费vpn 最新技术 简单部署 轻松秒开油管4K 只要复制粘贴 谷歌colab
- 神秘代码一键生成免费上网节点,速度惊人! 解锁流媒体 4K秒开|支持sing-box,nekobox,v2rayN等
- https://replit.com/
- https://colab.research.google.com/
- v2ray-worker - https://github.com/vfarid/v2ray-worker
- https://github.com/zizifn/edgetunnel
- Built-in trojan config generator is based on ca110us/epeius
- Proxy IPs source: https://rentry.co/CF-proxyIP
- https://ygkkk.blogspot.com/2023/07/cfworkers-vless.html
- https://github.com/yonggekkk/Cloudflare_vless_trojan/tree/main
- https://www.youtube.com/watch?v=QSFaP5EVI04































No comments:
Post a Comment