The following steps is only used for a selected environment to have a simplified deployments which is to target bringing MDE to all devices as fast as we can (in a week for 1k devices including windows, macOS, linux, servers, workstations, etc), also remove existing expired antimalware software, at the same time, has maximum possible security on the end point devices.
Background
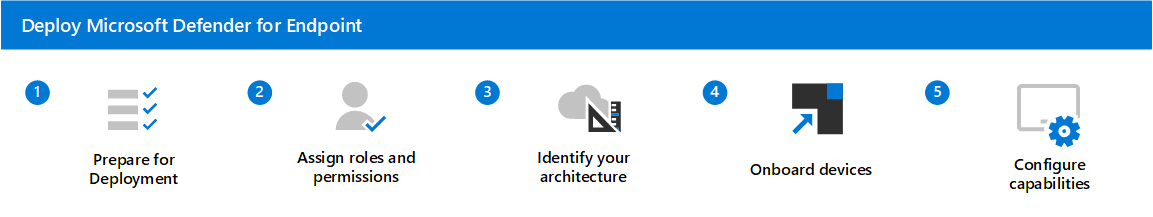
From Microsoft learn, https://learn.microsoft.com/en-us/defender-endpoint/mde-planning-guide, the steps to deploy Defender for Endpoint are:
- Step 1 - Set up Microsoft Defender for Endpoint deployment: This step focuses on getting your environment ready for deployment.
- Step 2 - Assign roles and permissions: Identify and assign roles and permissions to view and manage Defender for Endpoint.
- Step 3 - Identify your architecture and choose your deployment method: Identify your architecture and the deployment method that best suits your organization.
- Step 4 - Onboard devices: Assess and onboard your devices to Defender for Endpoint.
- Step 5 - Configure capabilities: You're now ready to configure Defender for Endpoint security capabilities to protect your devices.
Process related to MDE
High Level Deployment Steps for Workstation
1 Generating onboarding code
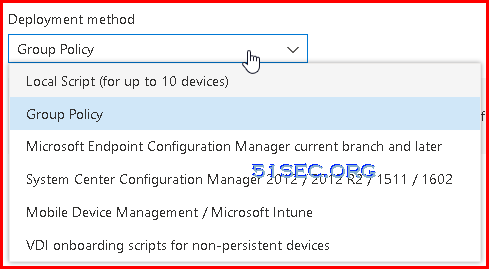
- Group Policy
You can configure your devices using Group Policy.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices see Configure devices using Group Policy section in the Microsoft Defender for Endpoint guide.
- Local Script (for up to 10 devices)
You can configure a single device by running a script locally.
Note: This script has been optimized for usage with a limited number of devices (1-10). To deploy at scale, please see other deployment options above.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices, see Configure devices using a local script
section in the Microsoft Defender for Endpoint guide.
2 Deploy onboarding package (script) to all workstations
Get-MpComputerStatus : Gets the status of antimalware software on the computer
PS C:\Users\User> get-mpcomputerstatus
AMEngineVersion : 1.1.25010.7
AMProductVersion : 4.18.24090.11
AMRunningMode : Normal
AMServiceEnabled : True
AMServiceVersion : 4.18.24090.11
AntispywareEnabled : True
AntispywareSignatureAge : 0
AntispywareSignatureLastUpdated : 2/21/2025 11:24:41 AM
AntispywareSignatureVersion : 1.423.36.0
AntivirusEnabled : True
AntivirusSignatureAge : 0
AntivirusSignatureLastUpdated : 2/21/2025 11:24:41 AM
AntivirusSignatureVersion : 1.423.36.0
BehaviorMonitorEnabled : True
ComputerID : C223A6B9-EE37-4983-B88D-09CC8C8BFA9F
ComputerState : 0
DefenderSignaturesOutOfDate : False
DeviceControlDefaultEnforcement :
DeviceControlPoliciesLastUpdated : 3/27/2023 10:12:31 AM
DeviceControlState : Disabledhttps://learn.microsoft.com/en-us/powershell/module/defender/get-mpcomputerstatus?view=windowsserver2025-ps
Get-MpComputerStatus gets the antimalware status of Defender AV. Use the command for validating the running mode. Check the following items:
- AMRunningMode: Must be in normal mode for active Defender protection
- AMProductVersion: Must be one of the latest released versions
- AMServiceEnabled: Must be True
- AntiSpywareEnabled: Must be True
- BehaviorMonitorEnabled: Must be True
- RealTimeProtectionEnabled: Must be True
- IoavProtectionEnabled: Must be Tru
If the client is running MDE it will have processes like sensendr running
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows Advanced Threat Protection\Status
+ I guess you could check for mssense.exe
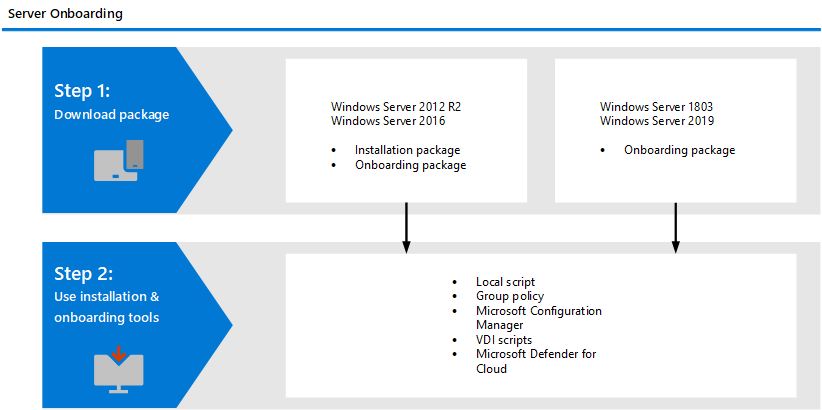
High Level Deployment Steps for Servers
You need to complete the following general steps to successfully onboard servers.
Applies to:
- Microsoft Defender for Endpoint Server
- Microsoft Defender for Servers
2. Connect your non-azure machines to Microsoft Defender for Cloud with Defender for Endpoint
- Go to Defender for Cloud > Environment Settings > Direct onboarding.
- Switch the Direct onboarding toggle to On.
- Select the subscription you would like to use for servers onboarded directly with Defender for Endpoint.
- Select Save.
Connect your non-azure machines to Microsoft defender for cloud
- Servers will not be onboarded if the windows defender AV component is not installed on the machine
- Defender AV is not disabled by GPO
- Make sure your server is having latest security updates
- Required URLs are whitelisted - https://download.microsoft.com/download/6/b/f/6bfff670-47c3-4e45-b01b-64a2610eaefa/mde-urls-commercial.xlsx
1 Generate Azure Arc Script
2 Run Special PowerShell Script to Enable MDE
3 Upload ResourceLevelPricingAtScale.ps1 into your cloud shell
Make sure use proper resource group or tag to enable MDE.
4 Put MDE in passive mode if you are using a third-party anti-malware solution.
You need to apply the following Microsoft Defender Antivirus passive mode setting. Verify that it was configured correctly: Set the following registry entry:
- Path:
HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection - Name:
ForceDefenderPassiveMode - Type:
REG_DWORD - Value:
1

5 Configure Defender Portal connect to Intune
Defender Settings
6 Configure Intune to Connect Windows Devices to Microsoft Defender for Endpoint
7 Configure Antivirus and Expose Management Policy / Profiles in Intune
Defender for Servers Activation on Resource Level
By default, Defender for Servers is enabled as a subscription-wide setting, covering all Azure VMs, Azure Arc-enabled Servers and VMSS nodes at the same time. However, there are scenarios in which it makes sense to downgrade individual machines from Defender for Servers Plan 2 to Plan 1, or only enable Defender for Servers Plan 1 on a subset of machines in a subscription.
This folder contains a PowerShell script that allows you to select machines based on Azure resource tags, or a resource group to configure them individually rather than using the same plan setting for all machines in a subscription.
ResourceLevelPricingAtScale.ps1
Workflow of Onboarding Servers
- sc query windefend
- sc qc windefend
- hostname
3. Check the event logs in the sense related folders
- sc qc sense
- sc query sense
4. Run onboarding script
5. verify sense service is running
Offboard Windows Servers
You can offboard Windows Server 2012 R2, Windows Server 2016, Windows Server (SAC), Windows Server 2019, Windows Server 2019 Core edition, Windows Server 2022, and Windows Server 2025 (beginning in February 2025 and rolling out over the next several weeks) using the same method available for Windows 10 client devices.
- Offboard devices using Group Policy
- Offboard devices using Configuration Manager
- Offboard devices using Mobile Device Management tools
- Offboard devices using a local script
After offboarding, you can proceed to uninstall the unified solution package on Windows Server 2016 and Windows Server 2012 R2.
For other Windows server versions, you have two options to offboard Windows servers from the service:
- Uninstall the MMA agent
- Remove the Defender for Endpoint workspace configuration
- Locally, by running an offboarding script on a device (supported for macOS, Linux, and Windows (Server)).
- Through the offboarding API (supported for Windows 10 and Windows Server 2019).
It is important to understand that offboarding a device does not remove a device from the inventory. Instead, the device switches to an ‘inactive’ state 7 days after offboarding. This means that offboarding is not an efficient way to manage reimaged/repurposed devices.
The main goal of offboarding is to sever the connection between Microsoft Defender and the device. This is useful in several scenarios, including:
- A device encounters compatibility issues because the scanning process impacts performance and the standard operation of the server or legitimate processes are being blocked
- You are moving away from Microsoft Defender to a different EDR solution.
- The device is no longer in scope.
The last scenario is something I regularly encounter with customers: by accident, the customer onboarded personal devices into Microsoft Defender for Endpoint due to a misconfiguration. By using the offboarding API, I could block the device from sending data to Microsoft 365 Defender by moving it out of scope for the company. So offboarding devices do have a use case, but it is not a solution for managing inactive devices
Security Policies for Windows Workstation
Security Policies for Windows Servers
Intune - Endpoint Security - Manage - Attack surface reduction
Security Policies for Mac
Security Policies for Linux
- Linux servers onboarded through Microsoft Defender for Cloud have their initial configuration set to run Defender Antivirus in passive mode.
Microsoft Defender for Endpoint client analyzer
- The latest stable edition is available for download from following URL: https://aka.ms/MDEAnalyzer
- The latest preview edition is available for download from following URL: https://aka.ms/MDEClientAnalyzerPreview
The latest stable edition will be integrated into the MDE for Endpoint agent. Ensure that you are running the latest edition for either macOS or Linux.
The latest preview edition is available for direct download from following URL: https://aka.ms/XMDEClientAnalyzer
MDE VDI Deployments
https://learn.microsoft.com/en-us/defender-endpoint/configure-endpoints-vdiOpen the VDI configuration package file (
WindowsDefenderATPOnboardingPackage.zip) that you downloaded from the service onboarding wizard. You can also get the package from the Microsoft Defender portal.In the navigation pane, select Settings > Endpoints > Device management > Onboarding.
Select the operating system.
In the Deployment method field, select VDI onboarding scripts for non-persistent endpoints.
Select Download package and save the file.
Copy the files from the
WindowsDefenderATPOnboardingPackagefolder extracted from the zipped folder into the golden/primary image under the pathC:\WINDOWS\System32\GroupPolicy\Machine\Scripts\Startup. (The folder will be generated by local group policy from next step, if the folder is not presented in the system)If you're implementing multiple entries for each device - one for each session, copy
WindowsDefenderATPOnboardingScript.cmd.If you're implementing a single entry for each device, copy both
Onboard-NonPersistentMachine.ps1andWindowsDefenderATPOnboardingScript.cmd.
Open a Local Group Policy Editor window and navigate to Computer Configuration > Windows Settings > Scripts > Startup.
Note
Domain Group Policy may also be used for onboarding non-persistent VDI devices.
Depending on the method you'd like to implement, follow the appropriate steps:
Method Steps Single entry for each device 1. Select the PowerShell Scripts tab, then select Add (Windows Explorer opens directly in the path where you copied the onboarding script earlier).
2. Navigate to onboarding PowerShell scriptOnboard-NonPersistentMachine.ps1. There's no need to specify the other file, as it's triggered automatically.Multiple entries for each device 1. Select the Scripts tab, then select Add (Windows Explorer opens directly in the path where you copied the onboarding script earlier).
2. Navigate to the onboarding bash scriptWindowsDefenderATPOnboardingScript.cmd.Test your solution
Write-Host "INFO: Checking hostname against a list of known master images... Please wait..."
# Get the current hostname
$CURRENT_HOSTNAME = (hostname)
# Define the target hostnames
$TARGET_HOSTNAMES = @("example1", "example2", "example3", "example4", "MDLT2")
Write-Host "INFO: Current hostname is $CURRENT_HOSTNAME"
Write-Host "INFO: Target hostnames are $($TARGET_HOSTNAMES -join ', ')"
# Initialize a flag to indicate if a match is found
$MATCH_FOUND = $false
# Check if the current hostname matches any of the target hostnames
foreach ($TARGET_HOSTNAME in $TARGET_HOSTNAMES) {
if ($CURRENT_HOSTNAME -eq $TARGET_HOSTNAME) {
$MATCH_FOUND = $true
Write-Host "INFO: Hostname matches one of the target hostnames"
Write-Host "WARNING: This machine is a master image... Exiting..."
exit
}
}
if (-not $MATCH_FOUND) {
Write-Host "INFO: Hostname does not match any of the target hostnames"
$script = $PSScriptRoot+"\Onboard-NonPersistentMachine.ps1"
& $script
}
For @echo off
echo INFO: Checking hostname against a list of known master images... Please wait...
for /f "tokens=*" %%i in ('hostname') do set CURRENT_HOSTNAME=%%i
set TARGET_HOSTNAMES=example1 exampl2 example3 exampel4
echo INFO: Current hostname is %CURRENT_HOSTNAME%
echo INFO: Target hostnames are %TARGET_HOSTNAMES%
set MATCH_FOUND=false
for %%h in (%TARGET_HOSTNAMES%) do (
if "%CURRENT_HOSTNAME%"=="%%h" (
set MATCH_FOUND=true
echo INFO: Hostname matches one of the target hostnames
echo WARNING: This machine is a master image... Exiting...
exit
)
)
Offboarding
Steps:
1 Get offboarding code2 Run offboarding code from local machine
No need to reboot
3 Verify
- Open Registry Editor (regedit).
- Navigate to the following key:
HKLM:\Software\Microsoft\Windows Advanced Threat Protection\Status. - Find the
OnboardingStatevalue. If it's set to0, the device is offboarded.
- Go to the Microsoft Defender portal (https://security.microsoft.com).
- Navigate to Assets > Devices.
- Locate the device in the device inventory.
- Check the device's status in the flyout panel, which may show "Inactive" or "No sensor data".
- Go to the Microsoft Defender portal (https://security.microsoft.com).
- If you used a local script to offboard the device, ensure that the offboarding package was successfully executed on the device.
- You can verify that the MDE agent has been removed by checking if the SENSE service is running (if the service is not running, the agent is gone).
- If you used a local script to offboard the device, ensure that the offboarding package was successfully executed on the device.
- Keep in mind that data from an offboarded device, including alerts and vulnerabilities, is retained in the portal for up to 6 months, says Microsoft.
- The device profile will also remain in the device inventory for up to 180 days, says Microsoft.
- Keep in mind that data from an offboarded device, including alerts and vulnerabilities, is retained in the portal for up to 6 months, says Microsoft.
- While not always mandatory, rebooting the device or restarting the MDE service can help ensure all changes are fully applied and the device transitions to an inactive state. This is particularly important if you are migrating to a streamlined connectivity method or using a local script for offboarding.
- If you encounter issues after offboarding, such as the device not fully transitioning to an inactive state, a reboot or service restart might be helpful.
RBAC
4 Steps:Device Groups / User Groups
Many users ask when to use user groups and when to use device groups. The answer depends on your goal. Here's some guidance to get you started.
Device groups
If you want to apply settings on a device, regardless of who's signed in, then assign your policies to a devices group. Settings applied to device groups always go with the device, not the user.
For example:
Device groups are useful for managing devices that don't have a dedicated user. For example, you have devices that print tickets, scan inventory, are shared by shift workers, are assigned to a specific warehouse, and so on. Put these devices in a devices group, and assign your policies to this devices group.
You create a Device Firmware Configuration Interface (DFCI) Intune profile that updates settings in the BIOS. For example, you configure this policy to disable the device camera, or lock down the boot options to prevent users from booting up another OS. This policy is a good scenario to assign to a devices group.
On some specific Windows devices, you always want to control some Microsoft Edge settings, regardless of who's using the device. For example, you want to block all downloads, limit all cookies to the current browsing session, and delete the browsing history. For this scenario, put these specific Windows devices in a devices group. Then, create an Administrative Template in Intune, add these device settings, and then assign this policy to the devices group.
To summarize, use device groups when you don't care who's signed in on the device, or if anyone signs in. You want your settings to always be on the device.
User groups
Policy settings applied to user groups always go with the user, and go with the user when signed in to their many devices. It's normal for users to have many devices, such as a Surface Pro for work, and a personal iOS/iPadOS device. And, it's normal for a person to access email and other organization resources from these devices.
If a user has multiple devices on the same platform, then you can use filters on the group assignment. For example, a user has a personal iOS/iPadOS device, and an organization-owned iOS/iPadOS. When you assign a policy for that user, you can use filters to target only the organization-owned device.
Follow this general rule: If a feature belongs to a user, such as email or user certificates, then assign to user groups.
For example:
You want to put a Help Desk icon for all users on all their devices. In this scenario, put these users in a users group, and assign your Help Desk icon policy to this users group.
A user receives a new organization-owned device. The user signs in to the device with their domain account. The device is automatically registered in Microsoft Entra ID, and automatically managed by Intune. This policy is a good scenario to assign to a users group.
Whenever a user signs in to a device, you want to control features in apps, such as OneDrive or Office. In this scenario, assign your OneDrive or Office policy settings to a users group.
For example, you want to block untrusted ActiveX controls in your Office apps. You can create an Administrative Template in Intune, configure this setting, and then assign this policy to a users group.
To summarize, use user groups when you want your settings and rules to always go with the user, whatever device they use.
Sample Device Groups:
Create Custom Role:
Permissions:
Roles for Endpoints, Defender XDR, and Cloud Apps
Tags
Here's an example of how to add a TAG to devices using the onboarding script:
Open the onboarding script file in a text editor
Locate the :SCRIPT_START section
Add a command to assign a TAG to the device. For instance, if we want to assign a TAG "Workgroup", we can use the following command:
REG add "HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection\DeviceTagging" /v Group /t REG_SZ /f /d "Workgroup" >NUL 2>&1By incorporating a command to assign TAGs within the onboarding script, we can streamline the process and automatically categorize the devices during onboarding.
Device Group and Device Tag Check List Sample:
Tagging through Group Policy
Tagging through Defender Portal - Settings - XDR - Rules - Asset Rule Mgmt
Web Content Filtering
References
- Firewall settings: https://aka.ms/MDE-streamlined-urls
- Enforcement Scope Documentation (This is what we will use to
facilitate the configuration of MDE using Intune): Learn about using Intune to manage Microsoft Defender settings on
devices that aren't enrolled with Intune | Microsoft Learn
- Defender for Servers: Select a Defender for Servers plan in Microsoft Defender for Cloud
- Microsoft Defender for Cloud | Microsoft Learn
- Generating an onboarding script: Onboard Windows devices using a local script - Microsoft Defender
for Endpoint | Microsoft Learn
- Azure Arc: Quickstart - Connect hybrid machine with Azure Arc-enabled servers
- Azure Arc | Microsoft Learn





































No comments:
Post a Comment