This post describes how to configure a Branch Office VPN (BOVPN) between WatchGuard Firebox on Prem and a Check Point device at my home which is behind my home router.
There are some configuration I found interesting which I mentioned in the following. Local network setting is confusing me although I got it working. It might be because of the specialty of Firebox
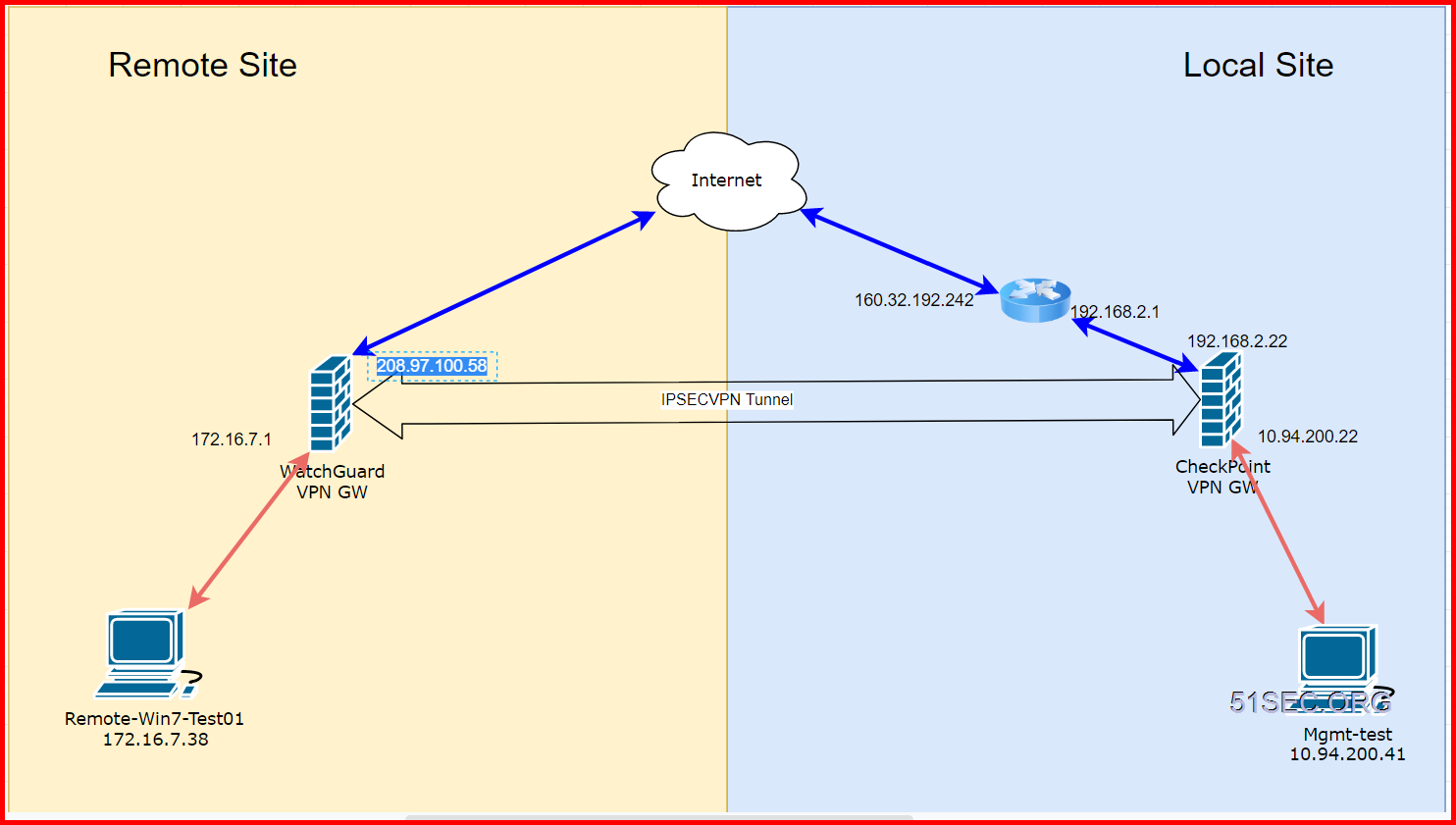
Topology
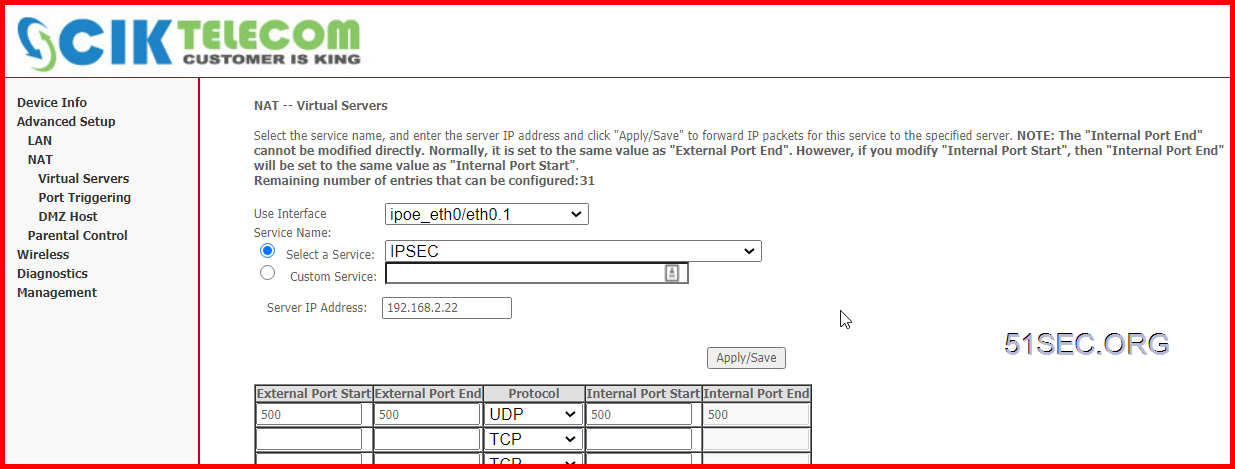
Make Sure Firewalls UDP500 Expose to Internet
UDP500 is IPSEC Protocol.
Since in local site, I am having a home router in front of Checkpoint firewall 192.168.2.22, I will have to open UDP 500 port to checkpoint firewall gateway.
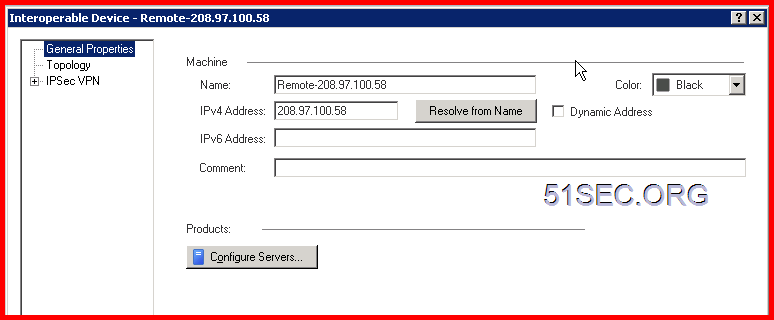
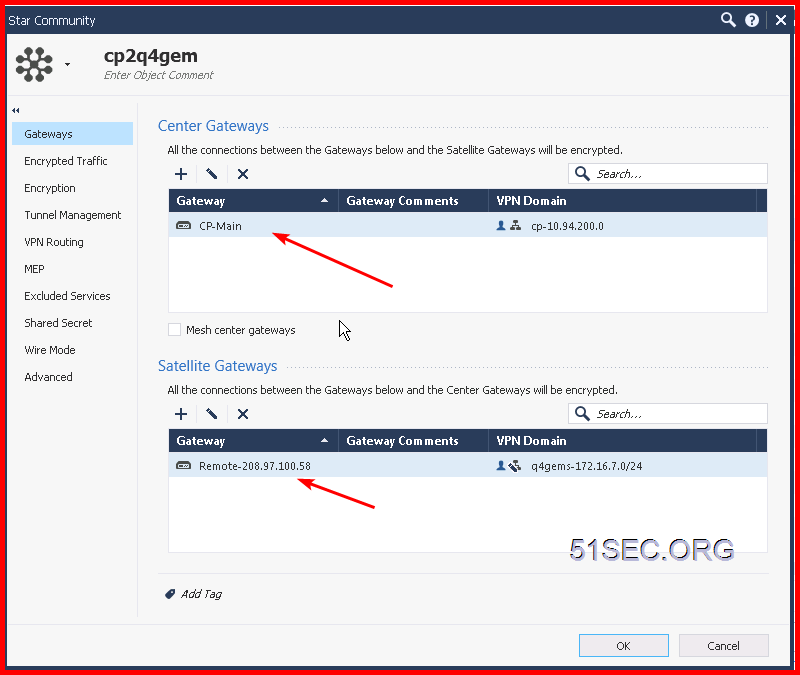
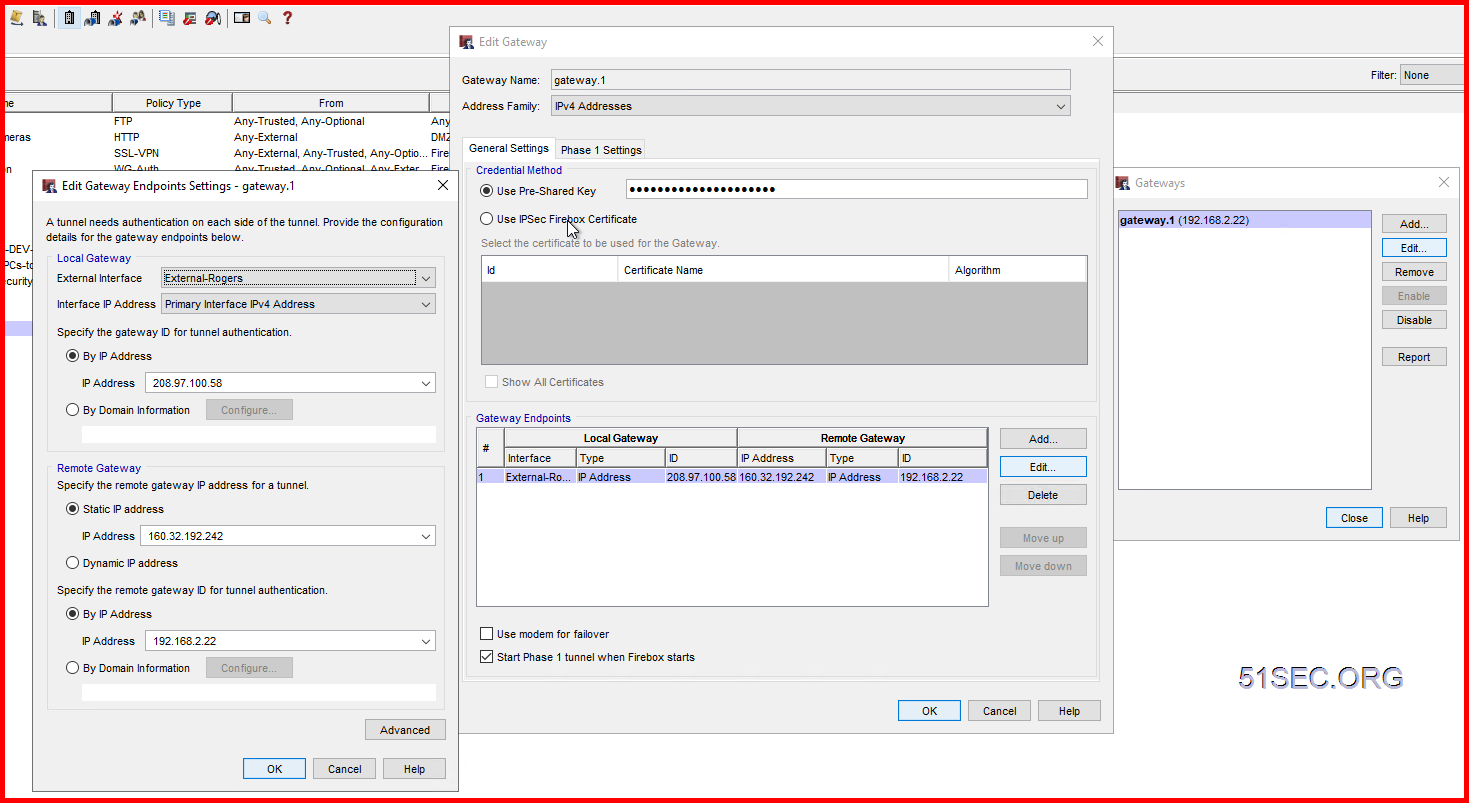
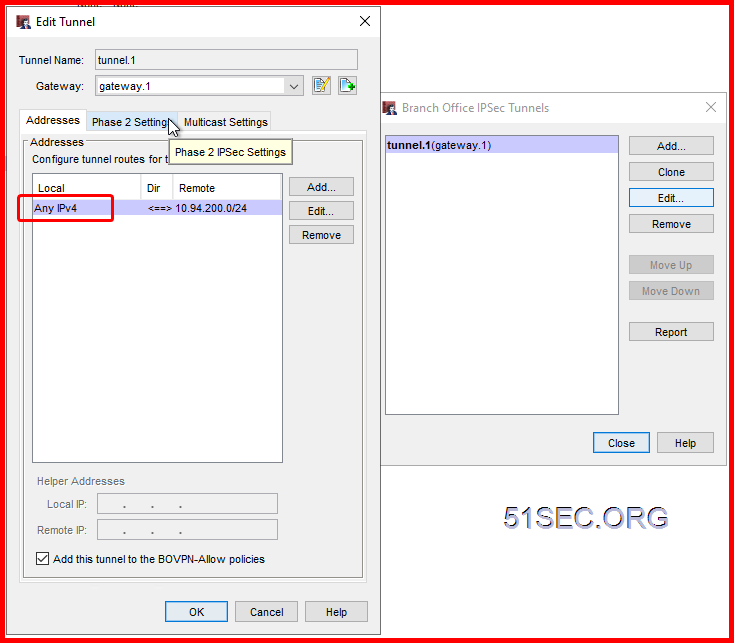
Create Gateway on each site
2 On WatchGuard, create a new Branch Office Gateway:
Under the Credential Method section, select Use Pre-Shared Key and enter a same key as you entered in the Checkpoint firewall.
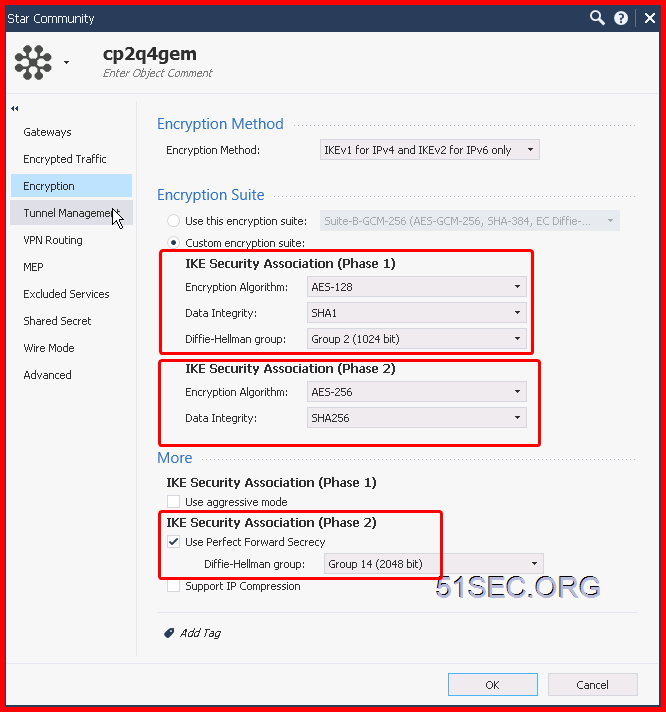
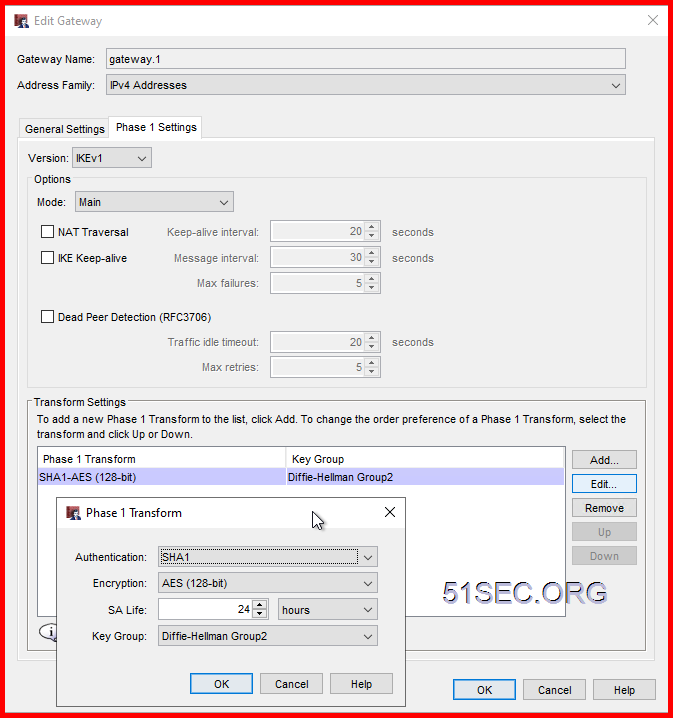
Create Phase 1 (Main) Policy
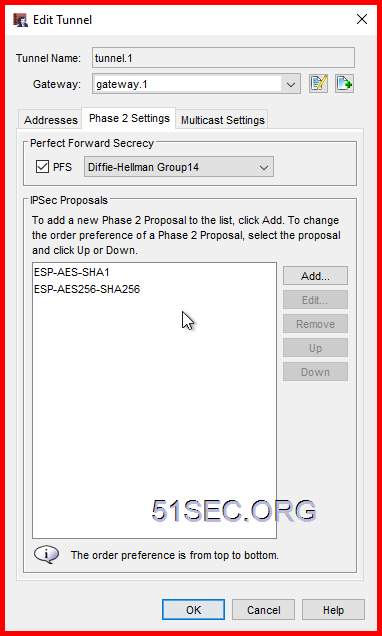
Create Phase 2 (Quick) Policy
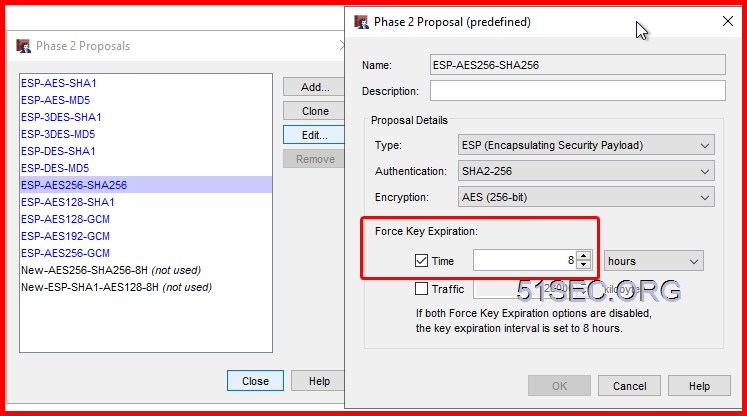
Default Phase2 Proposal can be changed at VPN menu -> Phase 2 proposals page.
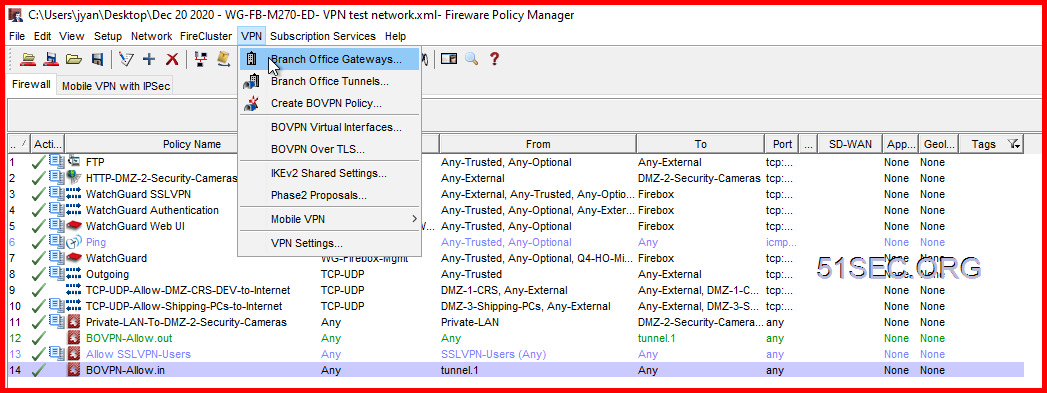
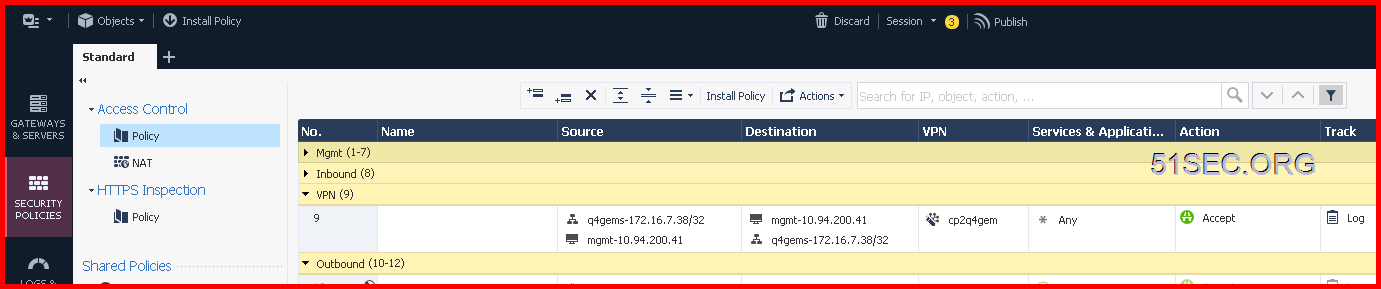
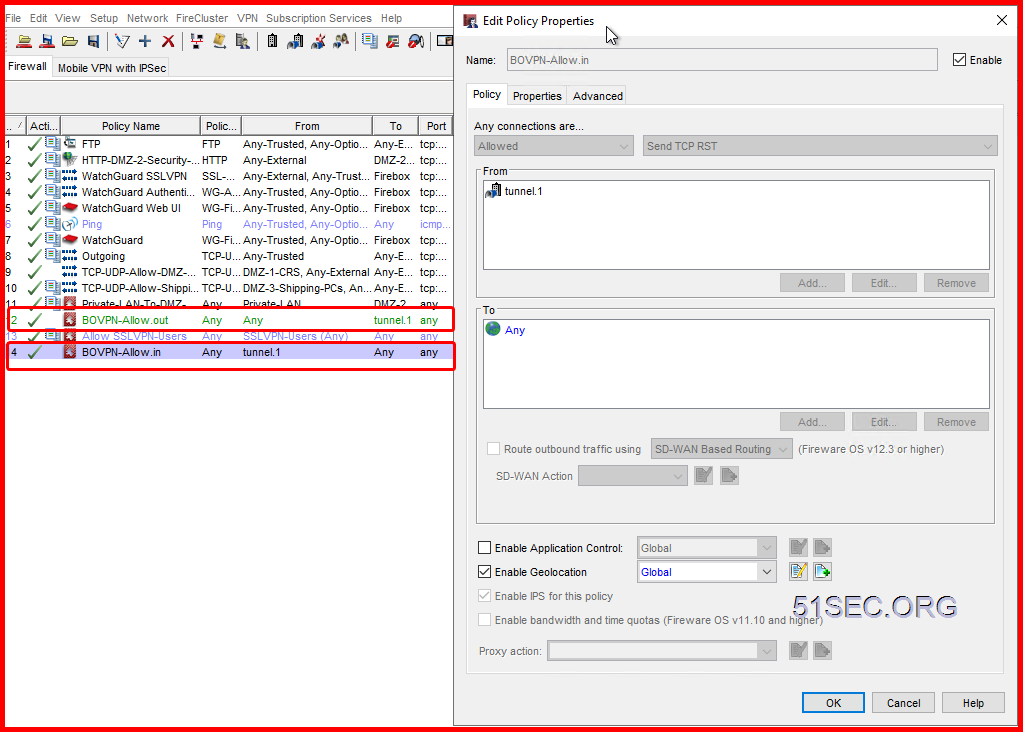
Create Firewall Policy to Allow VPN Traffic
2 On WatchGuard, it will automatically add two BOVPN rules for inbound and outbound traffic:
Test and Troubleshooting
- Ping, tracert, VPN tu, and tcpdump -nni any host <Remote VPN Gateway Public IP>
- Logs to search <Remote VPN Gateway Public IP>
2 On WatchGuard,
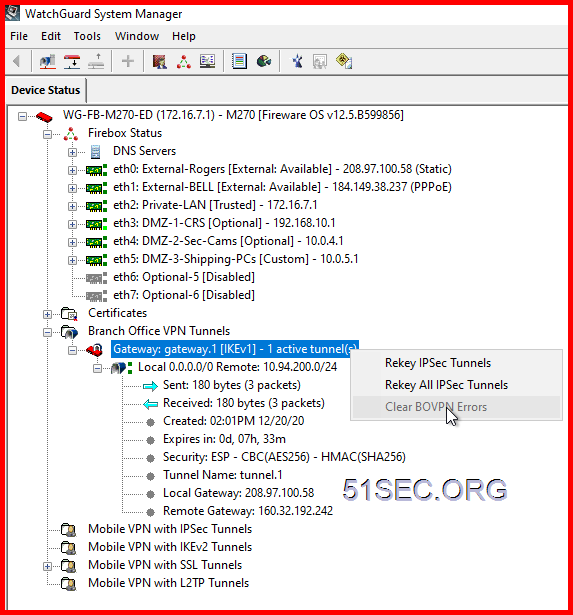
WatchGuard System Manager to reset key and clear error message
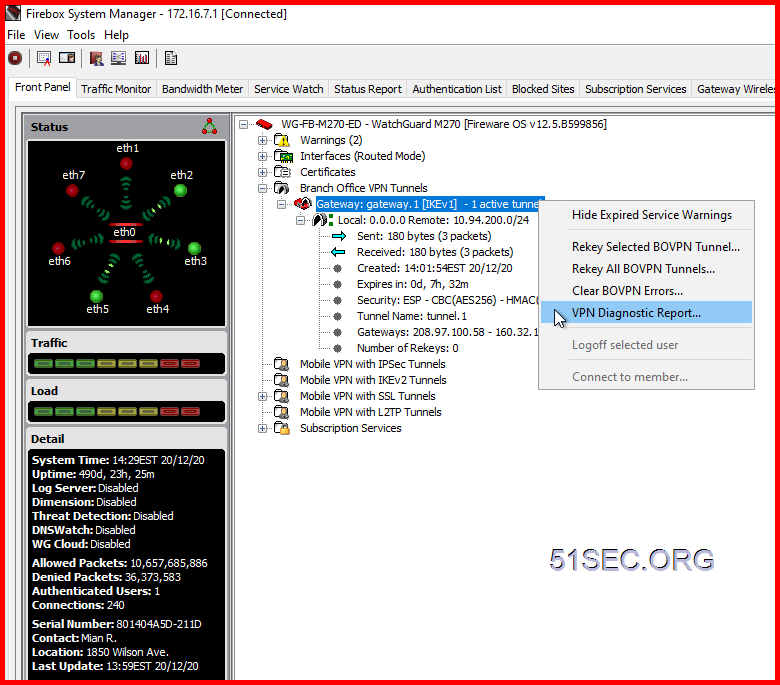
Firebox System Manager - Right Click Menu on Gateway - VPN Diagnostic Report
System Manager - Traffic Monitor
Diagnostic Report:
*** WG Diagnostic Report for Gateway "gateway.1" ***
Created On: Tue Jan 5 18:09:29 2021
[Conclusion]
Tunnel Name: tunnel.1
tunnel route#1(172.16.7.0/24<->10.11.11.0/24) - Established
Incoming traffic was NOT detected for this tunnel after the diagnostic report started.
Outgoing traffic was NOT detected for this tunnel after the diagnostic report started.
The outgoing traffic for tunnel route (172.16.7.0/24<->10.11.11.0/24) is denied by firewall policy (Inconclusive).
Recommendation: Check your firewall policy configuration.
The incoming traffic for tunnel route (10.11.11.0/24<->172.16.7.0/24) is denied by firewall policy (Inconclusive).
Recommendation: Check your firewall policy configuration.
[Gateway Summary]
Gateway "gateway.1" contains "1" gateway endpoint(s). IKE Version is IKEv1.
Gateway Endpoint #1 (name "gateway.1") Enabled
Mode: Main
PFS: Disabled AlwaysUp: Disabled
DPD: Disabled Keepalive: Disabled
Local ID<->Remote ID: {IP_ADDR(208.97.100.58) <-> IP_ADDR(109.127.221.18)}
Local GW_IP<->Remote GW_IP: {208.97.100.58 <-> 109.127.221.18}
Outgoing Interface: eth0 (ifIndex=4)
ifMark=0x10000
linkStatus=2 (0:unknown, 1:down, 2:up)
[Tunnel Summary]
"1" tunnel(s) are found using the previous gateway
Name: "tunnel.1" Enabled
PFS: "Disabled" DH-Group: "2"
Number of Proposals: "8"
Proposal "New-AES256-SHA256-1hour"
ESP:
EncryptAlgo: "AES" KeyLen: "32(bytes)"
AuthAlgo: "SHA2-256"
LifeTime: "3600(seconds)" LifeByte: "0(kbytes)"
Proposal "ESP-AES-SHA1"
ESP:
EncryptAlgo: "AES" KeyLen: "32(bytes)"
AuthAlgo: "SHA"
LifeTime: "28800(seconds)" LifeByte: "128000(kbytes)"
Proposal "ESP-AES-MD5"
ESP:
EncryptAlgo: "AES" KeyLen: "32(bytes)"
AuthAlgo: "MD5"
LifeTime: "28800(seconds)" LifeByte: "128000(kbytes)"
Proposal "ESP-3DES-SHA1"
ESP:
EncryptAlgo: "3DES"
AuthAlgo: "SHA"
LifeTime: "28800(seconds)" LifeByte: "128000(kbytes)"
Proposal "ESP-3DES-MD5"
ESP:
EncryptAlgo: "3DES"
AuthAlgo: "MD5"
LifeTime: "28800(seconds)" LifeByte: "128000(kbytes)"
Proposal "ESP-DES-SHA1"
ESP:
EncryptAlgo: "DES"
AuthAlgo: "SHA"
LifeTime: "28800(seconds)" LifeByte: "128000(kbytes)"
Proposal "ESP-DES-MD5"
ESP:
EncryptAlgo: "DES"
AuthAlgo: "MD5"
LifeTime: "28800(seconds)" LifeByte: "128000(kbytes)"
Proposal "ESP-AES128-SHA1"
ESP:
EncryptAlgo: "AES" KeyLen: "16(bytes)"
AuthAlgo: "SHA"
LifeTime: "28800(seconds)" LifeByte: "0(kbytes)"
Number of Tunnel Routes: "1"
#1
Direction: "BOTH"
"172.16.7.0/24<->10.11.11.0/24"
[Run-time Info (gateway IKE_SA)]
Name: "gateway.1" (IfStatus: 0x80000002)
IKE SAID: "0xc392edec" State: "SA Mature"
Created: Tue Jan 5 18:05:49 2021
My Address: 208.97.100.58:500 Peer Address: 109.127.221.18:500
InitCookie: "510a45b359c0b29b" RespCookie: "c6bb072f96994816"
LifeTime: "28803(seconds)" LifeByte: "0(kbtyes)" DPD: "Disabled"
Serial Number: 0
msgIdSend: 0 msgIdRecv: 0
[Run-time Info (tunnel IPSEC_SA)]
"2" IPSEC SA(s) are found under tunnel "tunnel.1"
#1 "OUTBOUND"
SPI: 0xa71f3879 ISAKMP SA ID: 0xc392edec
Created on: Tue Jan 5 18:05:49 2021
Bytes Sent: "0" Packets Sent: "0"
Errors: replay: "0" replay_win: "0" integrity: "0" hw_ctx: "0"
HwCryptoCtx: currErr: "0" ctxState: "0"
Tunnel Endpoint: "208.97.100.58->109.127.221.18"
Tunnel Selector: "172.16.7.0/24 -> 10.11.11.0/24 Proto: ANY"
AUTH: "hmac(sha1)" KeyLen: "20(bytes)"
CRYPT: "cbc(aes)" KeyLen: "32(bytes)"
Gateway Name: "gateway.1"
Tunnel Name: "tunnel.1"
Owner Id: "801404A5D211D"
IFMARK: "0x10000(4)" DPD: "Disabled"
Number of Rekeys: "4"
#2 "INBOUND"
SPI: 0xf8d6371a ISAKMP SA ID: 0xc392edec
Created on: Tue Jan 5 18:05:49 2021
Bytes Sent: "0" Packets Sent: "0"
Errors: replay: "0" replay_win: "0" integrity: "0" hw_ctx: "0"
HwCryptoCtx: currErr: "0" ctxState: "0"
Tunnel Endpoint: "109.127.221.18->208.97.100.58"
Tunnel Selector: "10.11.11.0/24 -> 172.16.7.0/24 Proto: ANY"
AUTH: "hmac(sha1)" KeyLen: "20(bytes)"
CRYPT: "cbc(aes)" KeyLen: "32(bytes)"
Gateway Name: "gateway.1"
Tunnel Name: "tunnel.1"
Owner Id: "801404A5D211D"
IFMARK: "0x10000(4)" DPD: "Disabled"
Number of Rekeys: "4"
[Run-time Info (tunnel IPSEC_SP)]
"1" IPSEC SP(s) are found under tunnel "tunnel.1"
#1
Tunnel Endpoint: "208.97.100.58->109.127.221.18"
Tunnel Selector: 172.16.7.0/24 -> 10.11.11.0/24 Proto: ANY
Created On: Tue Jan 5 17:43:07 2021
Last Used On: Tue Jan 5 18:03:26 2021
Gateway Name: "gateway.1"
Tunnel Name: "tunnel.1"
[Address Pairs in Firewalld]
Address Pairs for tunnel "tunnel.1"
Direction: BOTH
172.16.7.0/24 <-> 10.11.11.0/24
[Policy checker result]
Tunnel name: tunnel.1
#1 tunnel route 172.16.7.0/24<->10.11.11.0/24
OUTBOUND traffic (src=172.16.7.2 dst=10.11.11.1 proto=tcp)
Found policy: Inconclusive
Action: Unspecified Outif:
INBOUND traffic (src=10.11.11.1 dst=172.16.7.2 proto=tcp)
Found policy: Inconclusive
Action: Unspecified Outif:







No comments:
Post a Comment