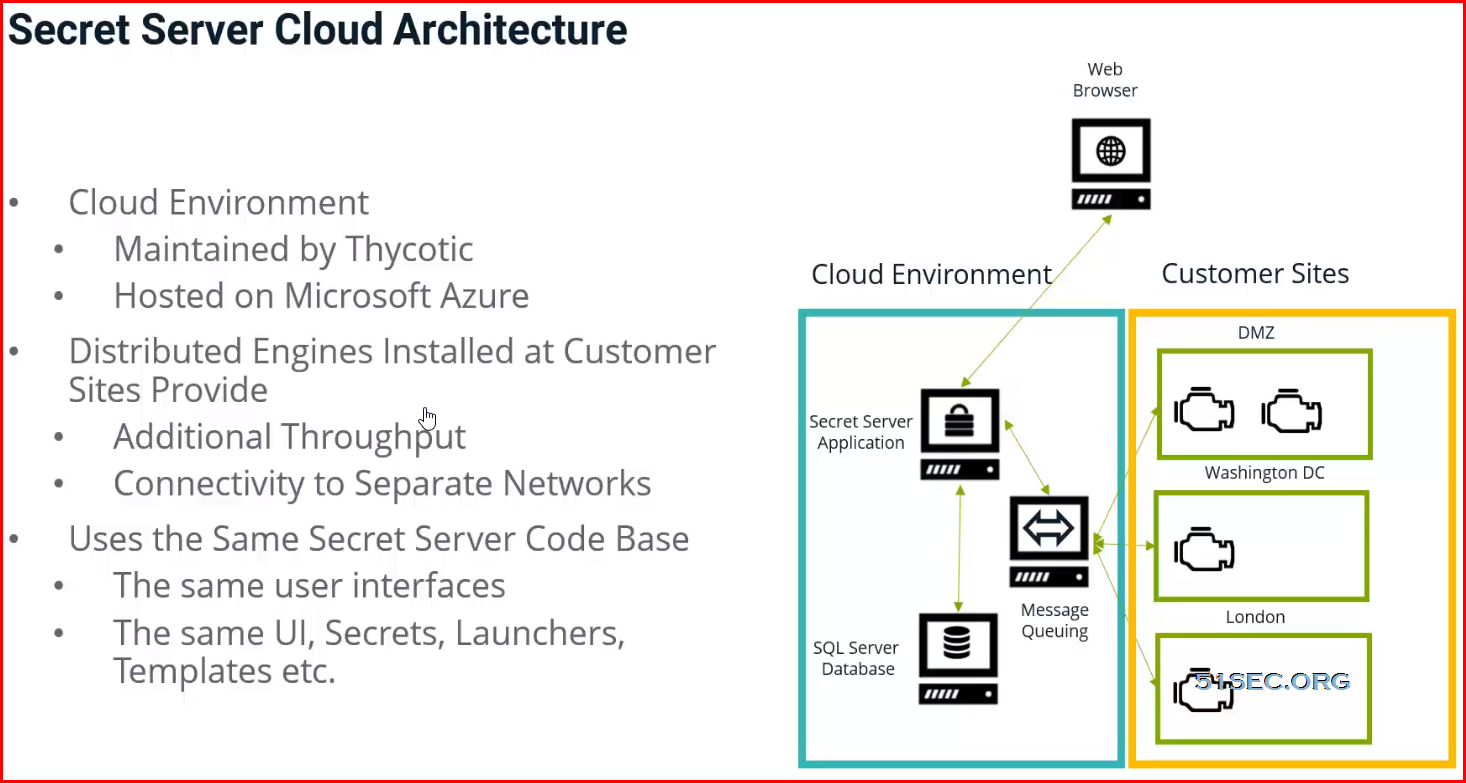
You can install a DE in a remote site and allow it to operate many functions. Communication with Secret Server Cloud also requires the distributed engine to be installed.
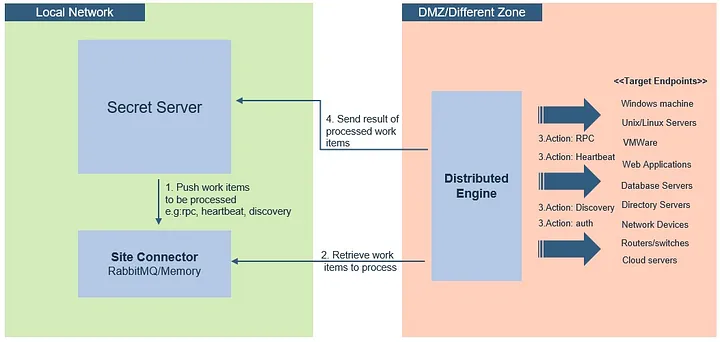
Distributed Engines allow RPC, heartbeat and discovery to occur on networks that are not directly connected to the network that SS is installed on.
Distributed Engine supports Active Directory Synchronization, Authentication, Heartbeat, Password Changing, Discovery, and SSH Proxying. Distributed Engine has three components – Engines, Sites, and Site Connectors:
- An engine is a Windows service that does the actual work, such as password changing, heartbeat, Discovery, and more. Each engine belongs to a site.
- A site can be thought of as a bucket of work items for a particular network area. Each engine is assigned to a single site, but each site can include multiple engines, significantly increasing throughput.
- A site connector is a Windows service that holds the work items for a number of sites. The site connector can be either RabbitMQ or MemoryMQ (a built-in service developed by Thycotic). Each site can only be assigned to a single site connector, but you can have multiple site connectors running on separate machines, each storing work items for multiple sites. Those sites, in turn, distribute the work items among multiple engines. The ability to add new Site Connectors, Sites, and Engines as needed makes Distributed Engine a highly-scalable solution.
Distributed Engine Major Components
Ports
Default Ports for DE
Default ports:
RabbitMQ: 5672 (non-SSL), 5671 (SSL)
MemoryMQ: 8672 (non-SSL), 8671 (SSL)
Secret Server: existing IP address bindings or custom port over TCP. We reserve one port for legacy upgrades, usually port 9999.
Secret Server Cloud:
443 (Web sockets—the default)
5671 and 5672 (AMQP)
| Process | Type of Traffic | Port Number |
|---|---|---|
| Active Directory Sync | LDAPS LDAP Kerberos NTLM | 636 389 88 445 |
| Discovery | RPC Dynamic Port Range* Microsoft DS Epmap SSH | 49152-65535 445 135 22 |
| Remote Password Changing | RPC Dynamic Port Range* SSH Telnet MS SQL NTLM LDAP LDAPS Sybase Oracle Kerberos | 49152-65535 22 23 1433 445 389 636 5000 1521 464 |
| Ports Incoming to Web Server | HTTP HTTPS | 80 443 |
| Ports Incoming to Database Server | SQL Connection TCP and UDP | 1433 |
| SMTP | 25 | |
| Radius Server | RADIUS | 1812 |
The major components diagram above shows the ports that are used for connecting to the site connector for both retrieval of new work and placement of task results (site connector port). There is an additional port the engine uses during initial configuration and at a regular interval to retrieve the most up-to-date configuration information (callback port) this port is on the Secret Server instance rather than on the site connector.
Engine Workflow
2 Connect to Secret Server using the engine callback port.
- Secret Server verifies that the engine is authorized.
- Engine requests configuration & site information from Secret Server in regular intervals.
4 The engine picks up as many work items as it can at one time and works on them.
5 When a work item is complete, the engine sends the result of the work item back to Secret Server byway of the Site Connector.
More detail can be found from: https://updates.thycotic.net/secretserver/documents/SS_Sec_DistributedEngine.pdf
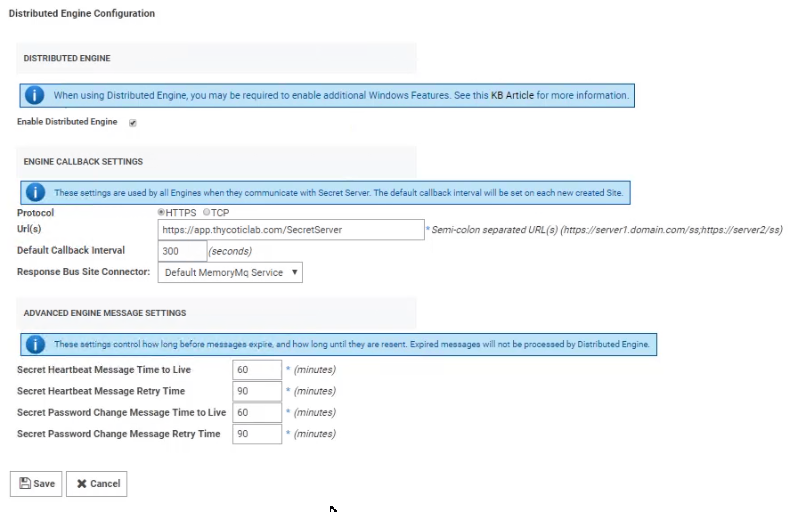
Distributed Engine Configuraiton
Below is a summary of the steps required to configure DEs:
Enable the DE and specify the engine callback settings.
Configure and Install the site connector.
If you plan to use RabbitMQ (recommended), follow the instructions here. You can find general information on using RabbitMQ Helper to install RabbitMQ can be found in Thycotic’s GitHub Repository
If you plan to use MemoryMQ, create the site connector record within SS then click the Download Site Connector Installer button to get the MSI. Run the MSI on the desired host.
Setup sites.
Install engines.
Assign secrets to sites. Secrets can be assigned to a site through their Remote Password Changing tab or via a bulk operation on the SS dashboard. Once assigned to a site, all heartbeat or password changing operations take place through that site.
Assign discovery sources to sites. To run discovery through a site, edit the discovery source and assign the site. Once assigned, all discovery operations for that discovery source take place through that site.
Faq
What happens if SS sends work items to the site connector, but no engines are running to consume them?
Work items continue to build up in the site connector until a limit is reached. Heartbeat work items have a Time To Live (TTL) of 5 minutes, Password Changing work items have a TTL of 20 minutes. Expired work items are thrown away and will not be processed. Once a heartbeat or password changing work item is sent to the site connector, SS will not send the same work item to the queue until 5 minutes after the TTL is up (10 and 25 minutes for heartbeat and password changing, respectively). This prevents multiple pending heartbeat or password changing work items for the same secret at the same time.
How many Sites can a Site Connector hold?
MemoryMQ supports up to 100. RabbitMQ supports up to 200.
Can I cluster Site Connectors?
RabbitMQ supports clustering, MemoryMQ does not.
Can I use both RabbitMQ and MemoryMQ?
Yes. You can have as many site connectors, of either type, installed as needed. Note that while you can have both RabbitMQ and MemoryMQ installed on a single machine, you cannot have two RabbitMQ instances or two MemoryMQ instances on the same machine.
Can I convert a site connector from MemoryMQ to RabbitMQ or vice versa?
Yes. You can install the new site connector, swap the sites over to the new service, and then decommission the old site connector.
DE Security
- Engines must be approved within Secret Server before they will be given access to a Site.
- Work items are encrypted with a Site-specific symmetric key prior to sending them to the Site Connector.
- Communication to the Site Connector supports SSL & TLS.
- Direct communication from Engine to Secret Server uses a public-private key exchange.
- The Engine configuration file is DPAPI encrypted.
For more information about Distributed Engine security, see the Distributed Engine Security guide downloadable PDF below:
DOWNLOAD
Encryption & Sites
Each site has its own AES 256 Symmetric Key (Site Symmetric Key) that is used to encrypt & decrypt messages for that particular site. As a result, each Engine has access to at most one Site Symmetric Key. An example flow for a Secret Heartbeat is below.
- 1. Secret Server loads the encrypted Secret from the database.
- 2. Secret Server decrypts the Secret using the Secret’s AES 256-bit key.
- 3. Secret Server creates a Secret Heartbeat message for the decrypted Secret.
- 4. Secret Server encrypts the message with the Site Symmetric Key.
- 5. Secret Server sends the message to the Site Connector.
- 6. An Engine assigned to the specific site connects to the Site Connector and retrieves the message.
- 7. The Engine decrypts the Secret Heartbeat message using the Site Symmetric Key.
- 8. The Engine processes the Secret Heartbeat message and creates a response object.
- 9. The response object is encrypted using the Engine Symmetric Key and submitted to Secret Server
DE Hardening: https://docs.delinea.com/secrets/current/security-hardening/distributed-engine-hardening/index.md
Thycotic VS CyberArk - Comparison
| Thycotic | CyberArk |
| Footprints with a long history or a large footprint | Designed to make things easier. |
| It's difficult to assess. | It's simple to compare and contrast |
| Installing it is difficult. | simple to set up in a matter of minutes |
| Getting up to speed can take weeks or months. | Day one's findings |
| It is frequently necessary to hire an expensive consultant. | There's no need to consult anyone. |
| To handle properly, you'll need to do certain measures. | In only a few clicks, you'll be able to handle anything. |
| To function, employees must undergo intensive training. | There is no need for training. |
| The user manual is 1000 pages long. | A simple guidebook that is normally used as a reference just once in a while |
| Slow, multi-tiered support | Experts respond quickly. |
| Initially, there is a significant investment. | Cloud-based, cost-effective solution |
Platforms Supported
| Thycotic | CyberArk |
|
|
Pricing
Free trial is available for both Thycotic ad Cyberark
Privileged Access Management Features
| Thycotic | CyberArk |
|
|
Integrations
| Thycotic | CyberArk |
|
|
Conclusion
Reviewers found Thycotic Secret Server to be easier to use, set up, and administer when comparing the two systems. CyberArk will be a more comprehensive solution, with more professional support services, broader adoption, more alliance relationships and integrations with third parties, a more mature offering across many corporate requirements, and a higher likelihood of being around in ten years.
From: https://mindmajix.com/thycotic-vs-cyberark








No comments:
Post a Comment