I had a old post regarding how to install OpenWRT into VMWare.
For me, OpenWRT is a perfect solution to run in my virtual environment. It can be ran as a light weight router to connect two different networks simulating two offices.
It also can act as an Firewall to filter the traffic crossing OpenWRT. It took a little resources fro your CPU, Memory and Hard Drive.
There are lots of situations when I created my lab, I will need only a small device acting as an router. All traffic has to be passed but two networks are having completely two different network addresses.
Here is an example topology:
192.168.196.0/24 -------- (192.168.196.2/24 OpenWRT 192.168.2.39/24) --------- 192.168.2.0/24
I do not need NAT since both network should see each other's real IP.
Firewall can be disabled, but I am not sure how to do it from OpenWRT. So here are some of my steps I did to allow all traffic passing through OpenWRT.
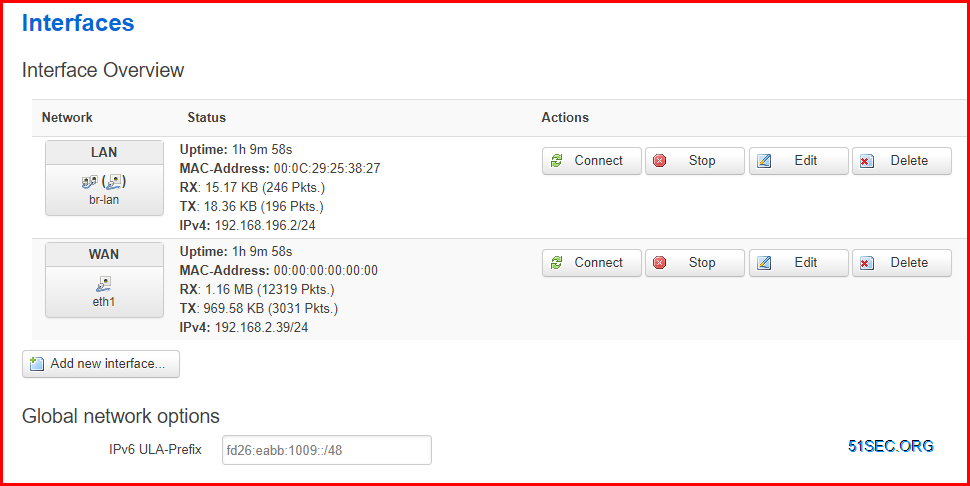
1 Interfaces configuration
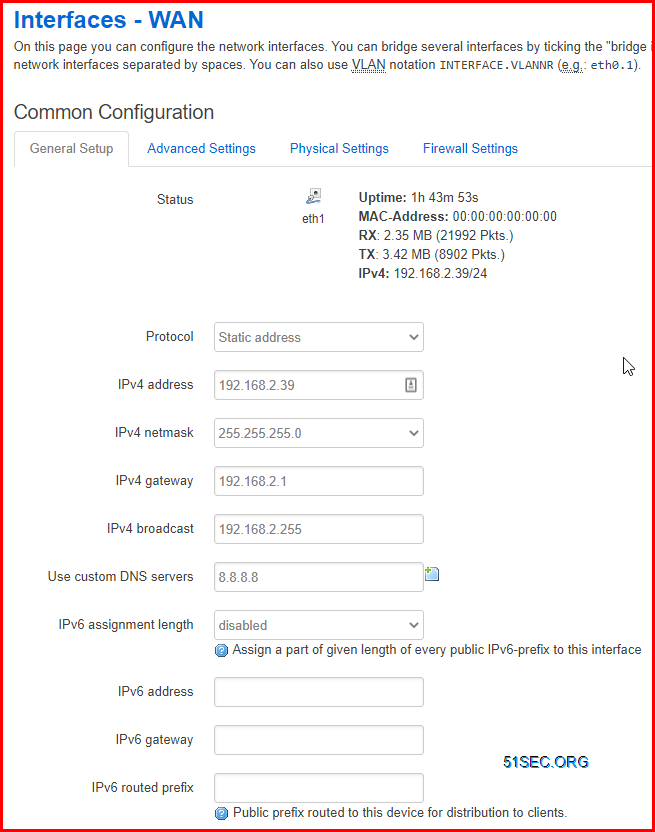
In OpenWrt, the first interface (eth0) is setup as LAN by default. The second (eth1) is setup as WAN. You might need to edit your interface to change network, or re-assign interface to right network.For example, you might need to delete your LAN, re-create your WAN or DMZ. For WAN interface, you might need to re-assign eth0 to bridge network, and assign static ip to it.
In this lab:
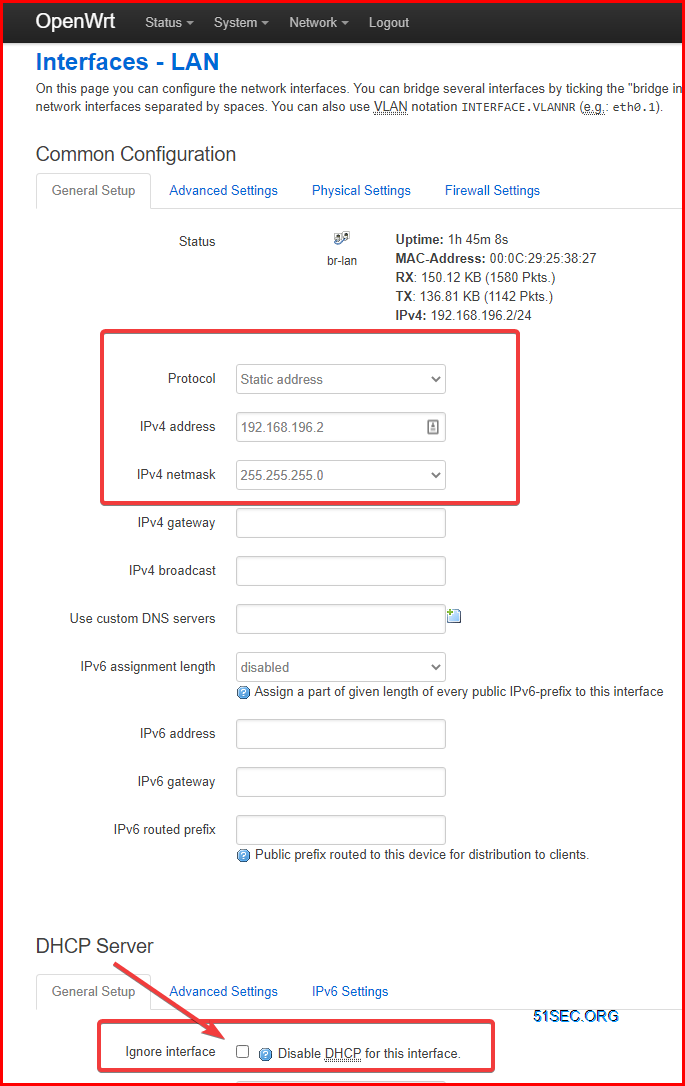
LAN interface has an ip : 192.168.196.2/24.
LAN interface has an ip : 192.168.196.2/24.
WAN interface has an ip: 192.168.2.39/24 with gateway 192.168.2.1 and DNS: 8.8.8.8
For LAN interface, I also disabled DHCP to simplify configuration.
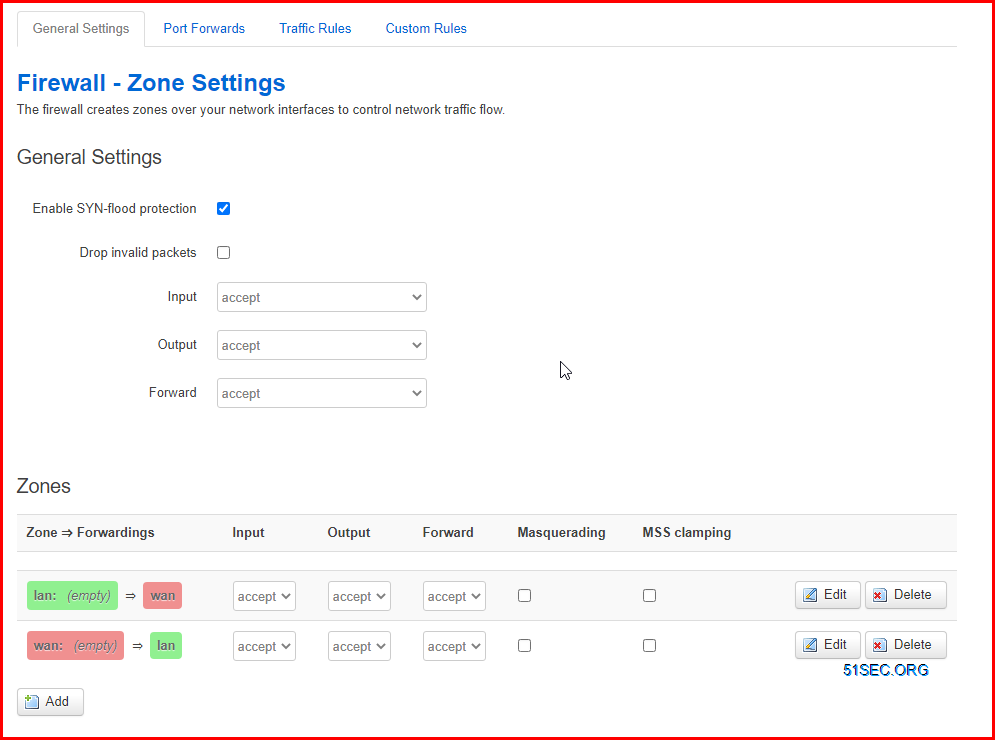
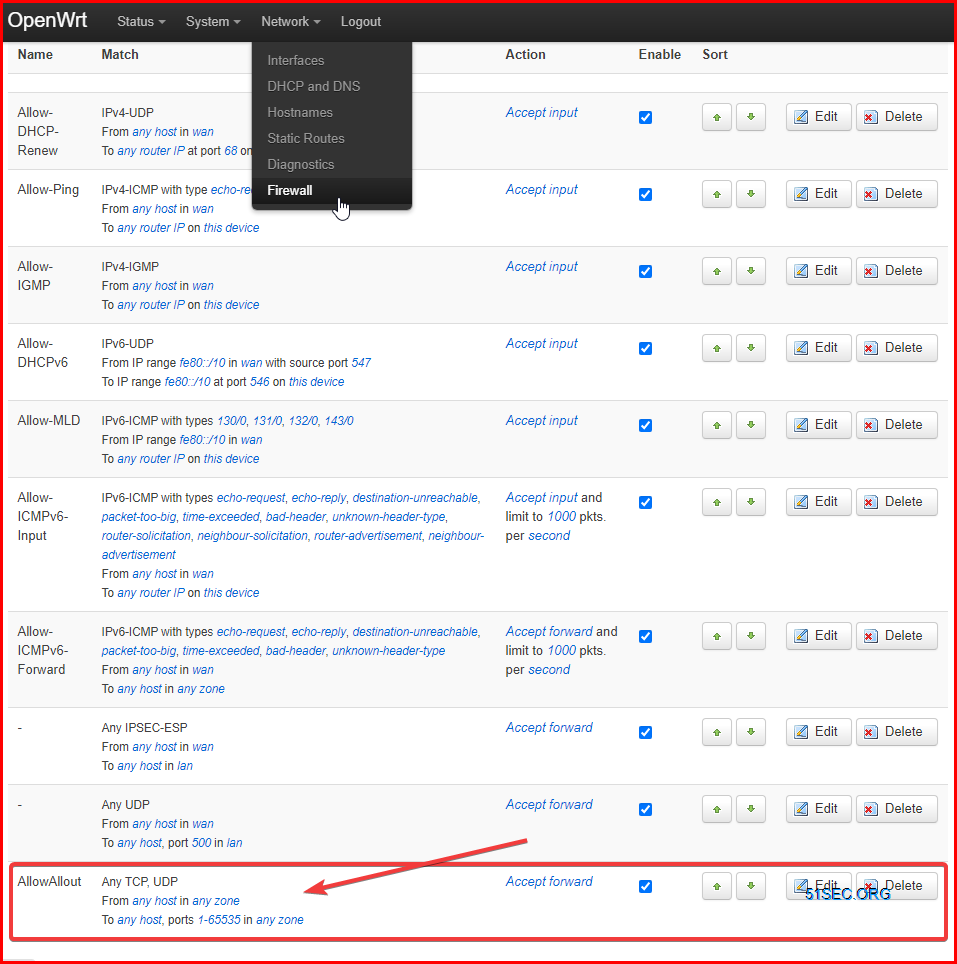
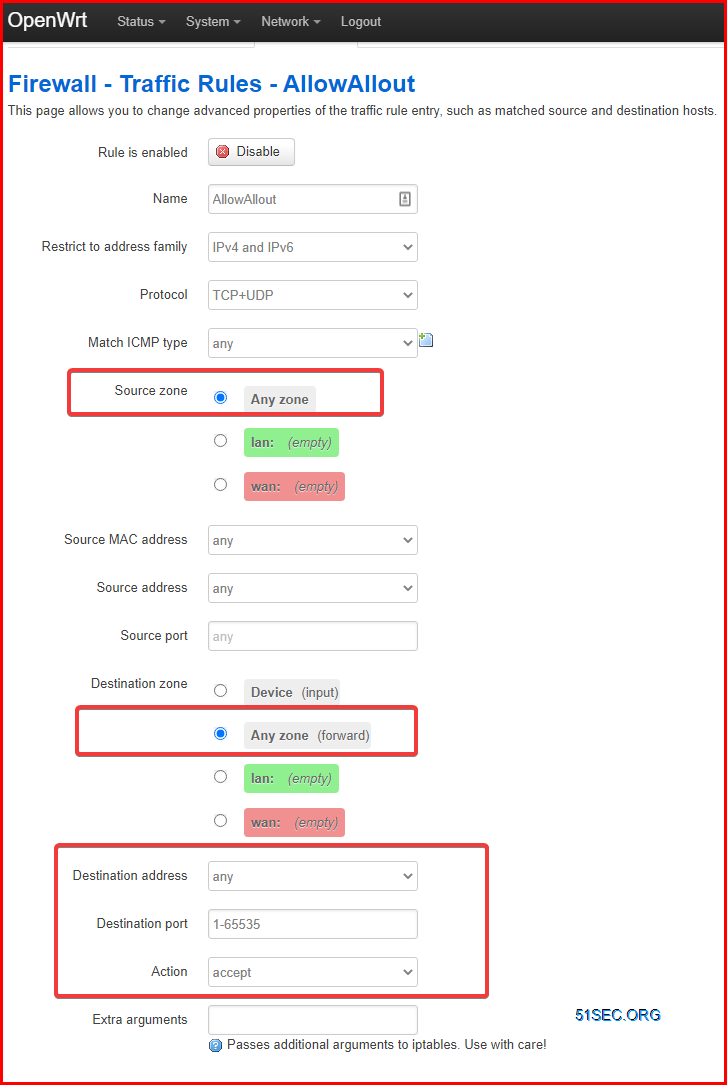
2 Firewall Configuration
Zone to Zone firewall configuration has been changed to accept for all, no masquerading and MSS Clamping.
The firewall rule details show in the following screenshot:







Thanks for sharing.
ReplyDelete