All Secret Server Cloud customers benefit from an infrastructure and platform built to meet the requirements of the most security-sensitive organizations. Here is the list for the features of Thycotic Secret Server Cloud :
- 100% isolation and encryption of all customer data both in-transit and at rest, using the AES-256 standard encryption algorithm and PBKDF2-HMAC-SHA256 hashing algorithm.
- Private encryption keys for each customer, with third-party key management support (AWS KMS).
- All Secrets are systematically “salted” before being hashed, and encrypted with their own unique Initialization Vector and Key.
- All connections to Secret Server Cloud are protected via Transport Layer Security (TLS). Distributed Engine communications are also secured with an additional encryption key unique to the tenant.
- All customer databases are continuously backed up every hour, with a transaction log backup performed every five minutes.
- Thycotic undergoes an annual, comprehensive SOC 2 audit and adheres to NIST-based security response policies to score, resolve, and communicate any necessary security advisories in response to reported vulnerabilities or bugs.
- Secret Server Cloud is delivered from the hardened Microsoft Azure US-EAST, Canada, SEA (Singapore), Germany-Central and Australia datacenters.
- Secret Server Cloud takes advantage of Microsoft Azure’s auto-scaling and built-in geo-redundancy, which generates three copies of each customer’s database, maintained across fault tolerant nodes to ensure continuous availability and facilitate swift disaster failover and recovery.
- Secret Server Cloud leverages Microsoft’s latest threat management and mitigation protocols, including intrusion detection, denial-of-service (DDoS) attack prevention, anti-malware, penetration testing, and analytics and machine learning tools to help mitigate threats.
- Azure architecture meets a broad set of international and industry-specific compliance standards, including General Data Protection Regulation (GDPR), ISO 27001, HIPAA, FedRAMP, SOC 1 and SOC 2.
For documentation purposes, SSC is the same as the corresponding on-premise edition. However, there are some feature differences:
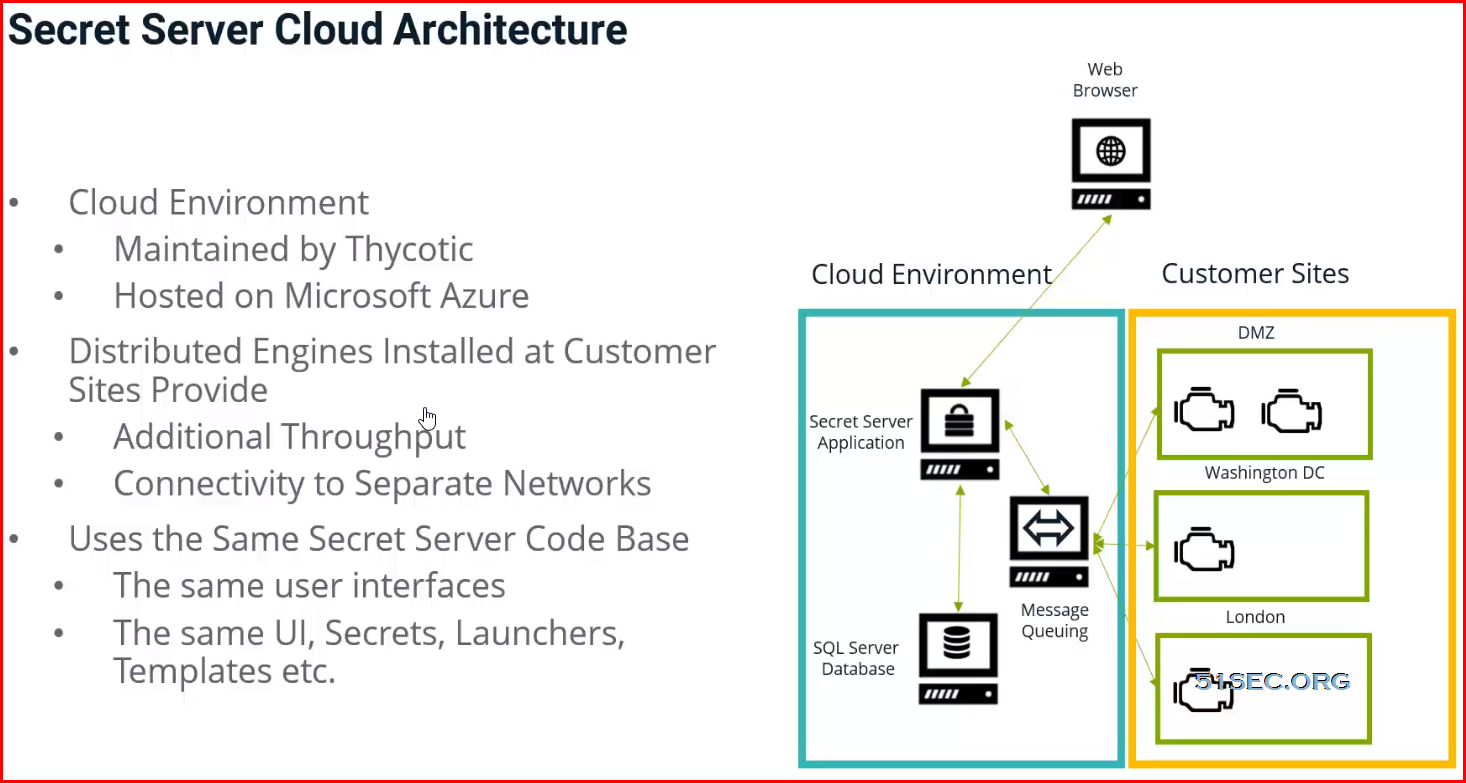
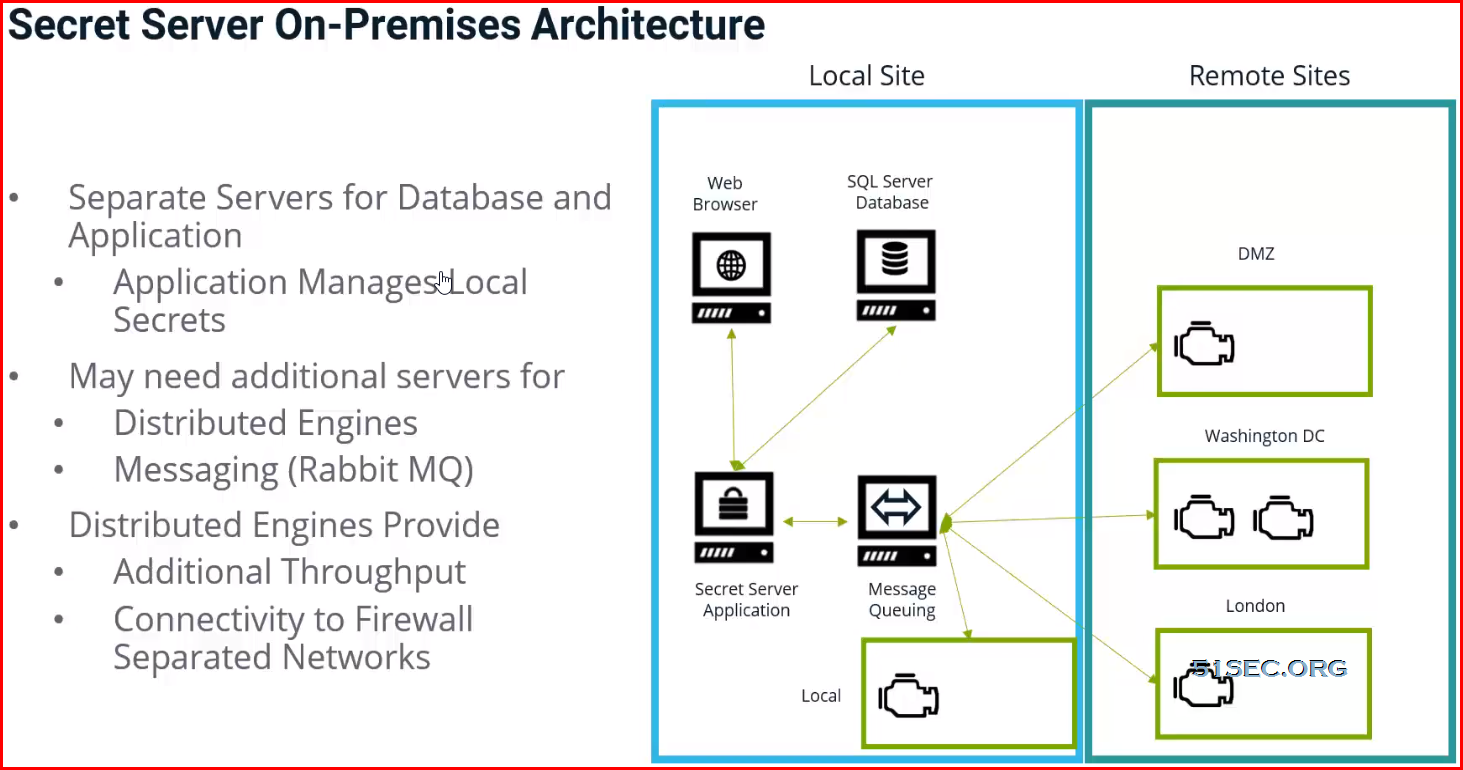
- Site Connectors: On-premise versions can use multiple site connectors to manage engine connections, such as RabbitMQ or MemoryMQ. The cloud version manages this for you as an Azure service and is not configurable.
- CRM Integration: On-premise versions can integrate with CRMs via direct database connections or the ConnectWise API. This is not currently available in SSC.
Architecture
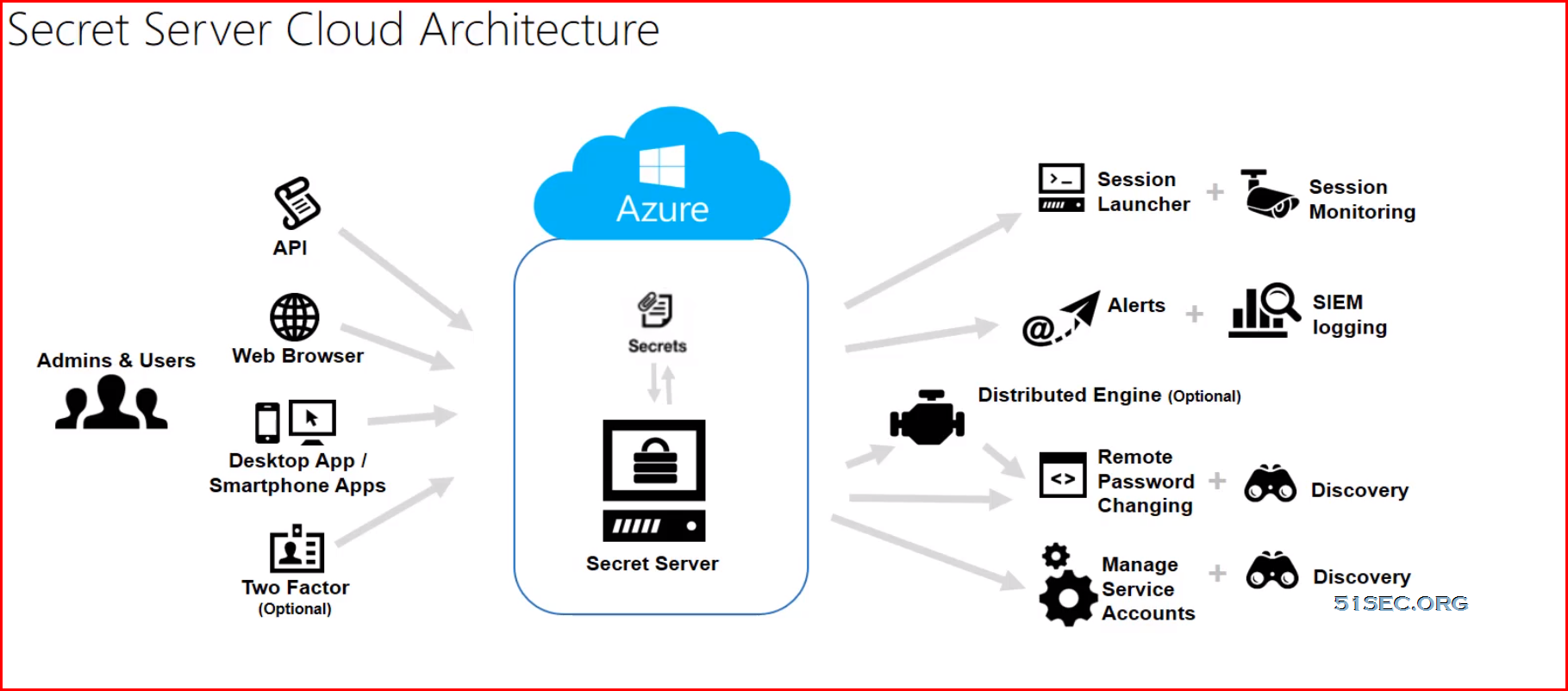
SS Cloud:
SS On-Premise:
Ports: 5671 and 5672 for RabiitMQ
Get an Trial for Thycotic Secret Server in the Cloud
Three DCs Available:
- Germany Central
- East US
- Australia Central
Why PAM in the cloud
- Deploy instantly. PAM should not be complex.
- Configure rapidly
- Stop wasting infosec resources spending time on software upgrades and configuration hardware
- Avoid financial and logistical nightmare of relying upon expensive professional service and consulting engagement.
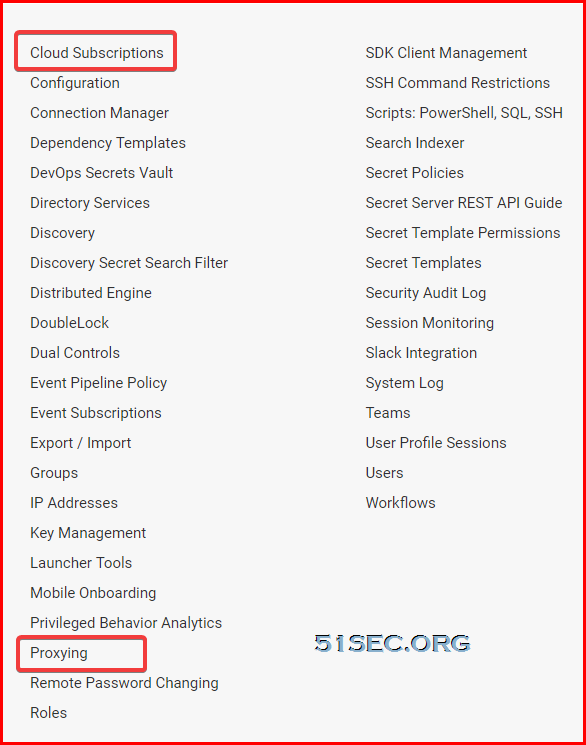
TSS Cloud Admin Menu - See All
TSS Cloud:
- Cloud Subscriptions
- Proxying
Comparing to On-Prem version:
From: https://docs.thycotic.com/ss/10.9.0/networking/secret-server-clustering/index.md
Thycotic and Azure Best Practice Industry Standards
Thycotic Certification Secret Server Cloud Tutorials
Distributed Engine
System Requirements
A distributed Engine server is required to communicate with SSC. Distributed engine server recommended specifications:
- Windows Server 2012 or Above
- CPU: 4-core 2 GHz (minimum)
- Memory: 4 GB of RAM (minimum)









No comments:
Post a Comment