There are some configuration on Azure network to get your Palo Alto firewall working well for the passing through traffic. Especially for ping traffic, by default, you wont be able to ping Internet ip through Palo Alto firewall.
In this post, it will give you some small tricks to get ping working for local interfaces and internet.For other basic configuration, please check this post: https://blog.51sec.org/2021/12/deploy-palo-alto-vm-series-firewall.html
Topology
Details about Palo Alto Azur VM-Series
Test Drive:
- https://azuremarketplace.microsoft.com/en-us/marketplace/apps/paloaltonetworks.vmseries-ngfw?tab=Overview
VM-Series Virtual Next-Generation Firewall with Threat Prevention - (Bundle1 PAYG Azure)
- Threat Prevention: Safeguard your network from known threats, such as exploits, malware, spyware, and command and control attacks, with market-leading, researcher-grade signatures that do not compromise performance.
D3_v2, DS3_v2, D4_v3, E4a_v4 (4 vCPU). - $0.87 (Hourly) $3,060.00 (Annual)
D4_v2, DS4_v2, D8_v3, D8s_v3, D8_v4, D8s_v4, E8a_v4, F8s_v2 (8 vCPU) - $1.42 (Hourly) $8,700.00 (Annual)
D5_v2, DS5_v2, D16_v3, D16s_v3, D16_v4, E16a_v4 (16 vCPU) - $ 2.82 (Hourly) $18,500.00 (Annual)
F32s_v2 (32 vCPU) - $2.82(Hourly) $18,500.00 (Annual)
Threat Prevention: Safeguard your network from known threats, such as exploits, malware, spyware, and command and control attacks, with market-leading, researcher-grade signatures that do not compromise performance.
URL Filtering: Defend your network from web-based threats by limiting your cloud workloads, VDI, and users safe access to the web while delivering granular policy controls to precisely define how they interact and access online content.
DNS Security: Detecting and preventing sophisticated DNS-layer network attacks and data exfiltration
GlobalProtectTM: Secure your infrastructure from malware and threats that can piggyback on traffic from mobile users.
WildFire®: Identify files with potential malicious behaviors and then deliver verdicts based on their actions by applying threat intelligence, analytics, and correlation.
D3_v2, DS3_v2, D4_v3, E4a_v4 (4 vCPU). - $1.38(Hourly) $4,840.00(Annual)
D4_v2, DS4_v2, D8_v3, D8s_v3, D8_v4, D8s_v4, E8a_v4, F8s_v2 (8 vCPU) - $1.84(Hourly) $13,700.00(Annual)
D5_v2, DS5_v2, D16_v3, D16s_v3, D16_v4, E16a_v4 (16 vCPU) - $3.45(Hourly) $29,300.00(Annual)
F32s_v2 (32 vCPU) - $3.45(Hourly) $29,300.00(Annual)
VM-Series Virtual Next-Generation Firewall with five Advanced Security Services and 24/7 Premium TAC Support. (Bundle 3 PAYG Azure)
Advanced Threat Prevention: protects your network by providing multiple layers of prevention during each phase of an attack while applying deep learning and machine learning models to block evasive and unknown C2 and stop zero-day exploit attempts inline.
Advanced URL Filtering: protects your organization from advanced and highly evasive phishing attacks, all in real-time.
DNS Security: Detecting and preventing sophisticated DNS-layer network attacks and data exfiltration
WildFire®: Identify files with potential malicious behaviors and deliver verdicts based on their actions by applying threat intelligence, analytics, and correlation.
GlobalProtectTM: Secure your infrastructure from malware and threats that can piggyback on traffic from mobile users.
D3_v2, DS3_v2, D4_v3, E4a_v4 (4 vCPU). - $1.50 (Hourly) $5,274.00 (Annual)
D4_v2, DS4_v2, D8_v3, D8s_v3, D8_v4, D8s_v4, E8a_v4, F8s_v2 (8 vCPU) - $2.01 (Hourly) $14,929.00 (Annual)
D5_v2, DS5_v2, D16_v3, D16s_v3, D16_v4, E16a_v4 (16 vCPU) - $3.76 (Hourly) $31,928.00 (Annual)
F32s_v2 (32 vCPU) - $3.76 (Hourly) $31,928.00 (Annual)
VM-Series Virtual Next Generation Firewall (BYOL)
Web Gui Overview
ACC Tab: The default ACC view will show you the network, threat, blocked and tunnel activity in four separate tabs for the past hour. The time frame and each tab can be customized to display the relevant application, threat, and user activity depending upon the user role.- The Objects tab allows you to manage the building blocks for creating policies such as address objects, custom applications, and security profiles.
- The Network tab allows you to create and manage interfaces, security zones, VLANs and other elements that enable connectivity.
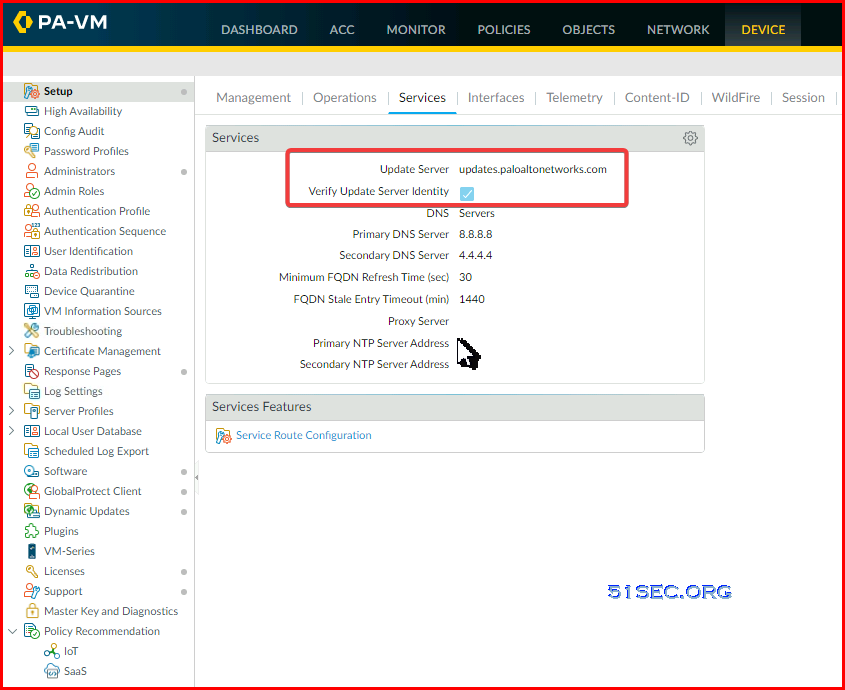
- The Device tab is where configuration items like DNS, service routes, etc. are managed. The device tab also allows you to manage high availability, users, software and content updates.
Enable Ping on Interfaces
Steps
- Go to Network > Network Profiles > Interface Mgmt
- Create a profile allowing ping:
- Go to Network > Interfaces and assign the profile, created above, to the interface under the Advanced tab:
- Commit the changes
From CLI:> configure # set network profiles interface-management-profile mgmt ping yes # set network interface ethernet ethernet1/3 layer3 interface-management-profile mgmt
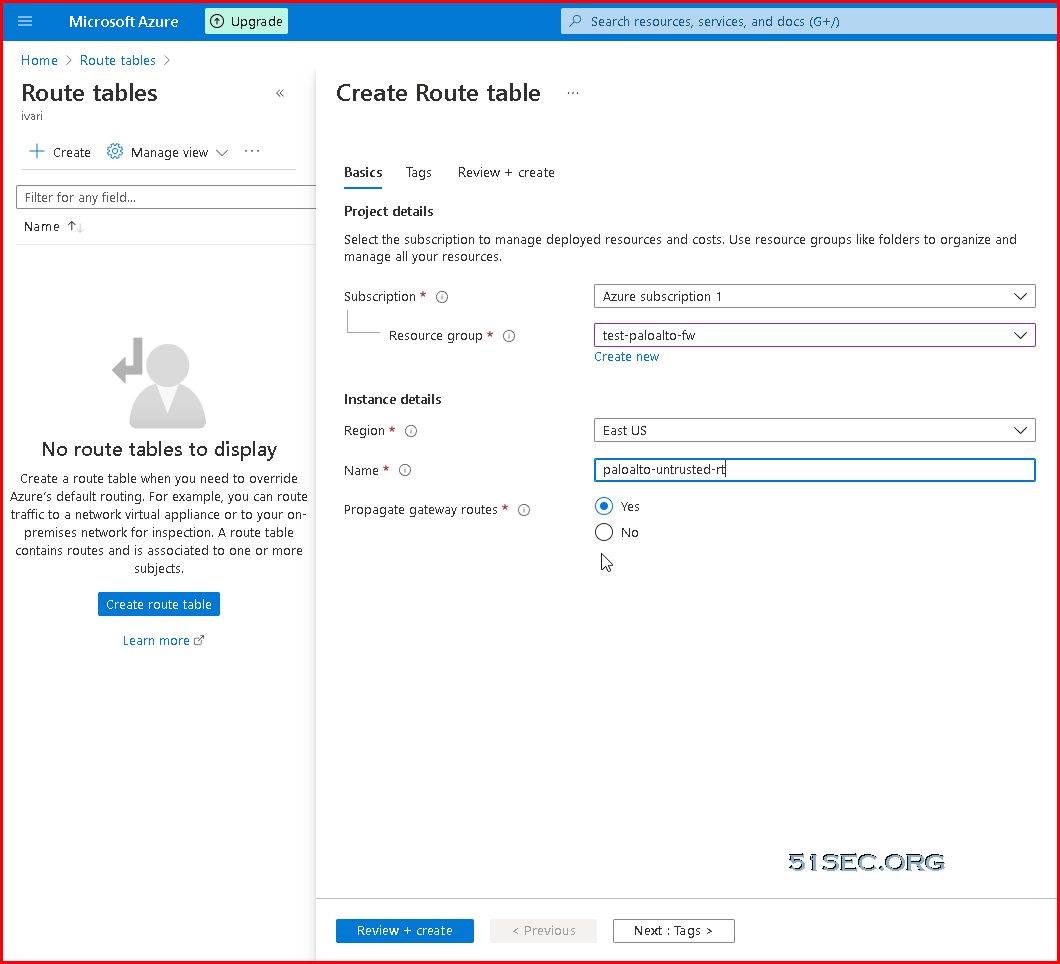
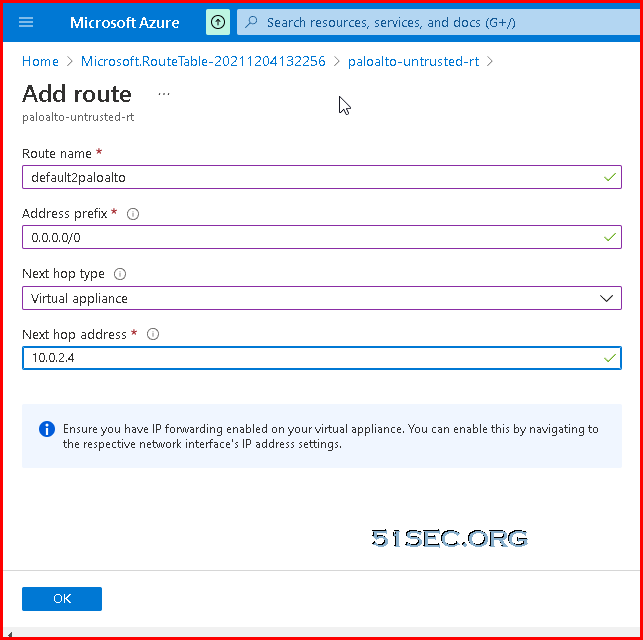
Add a Route Table and Route
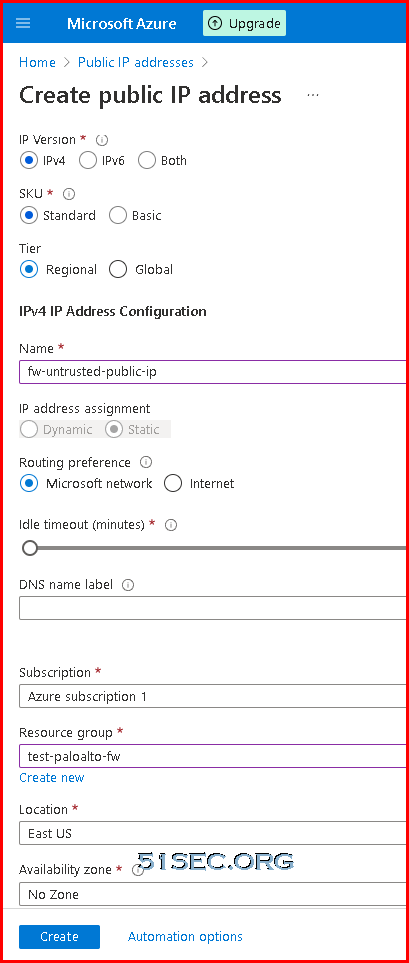
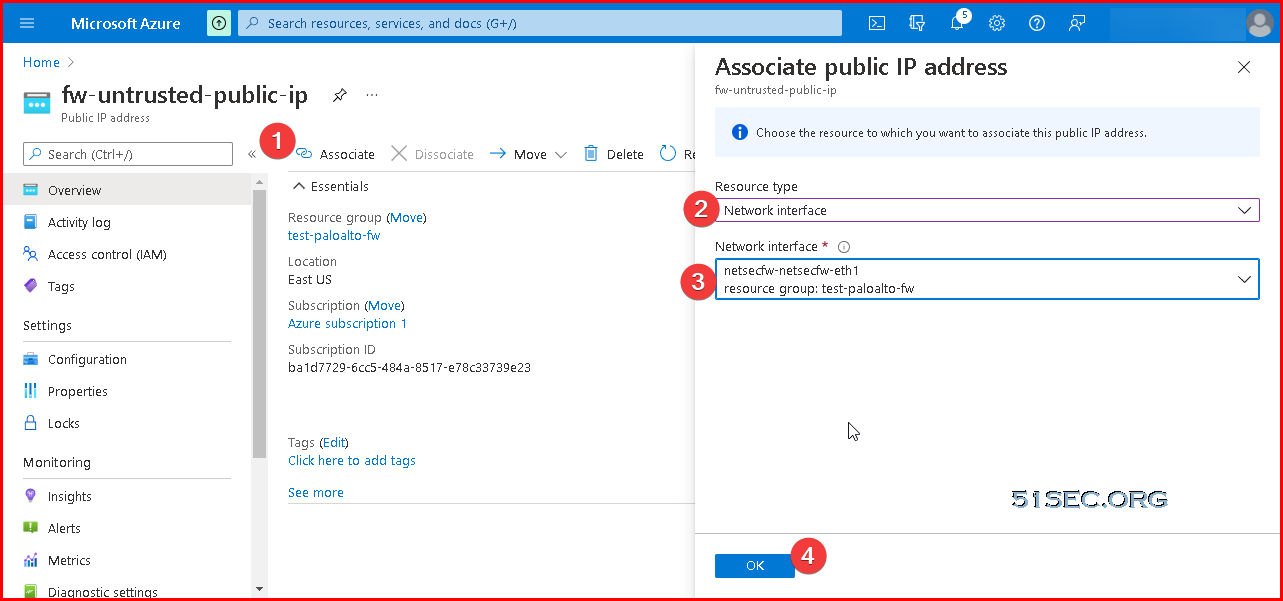
A subnet is a range of IP addresses in the virtual network. You can divide a virtual network into multiple subnets for organization and security. Each NIC in a VM is connected to one subnet in one virtual network. NICs connected to subnets (same or different) within a virtual network can communicate with each other without any extra configuration. By default all Azure subnet traffic will go to Azure default gateway for that subnet, which is .1 ip address.Add Public IP Address To Untrusted Interface
By default Azure vnet will not allow ping or tracert packet going through well.Updates
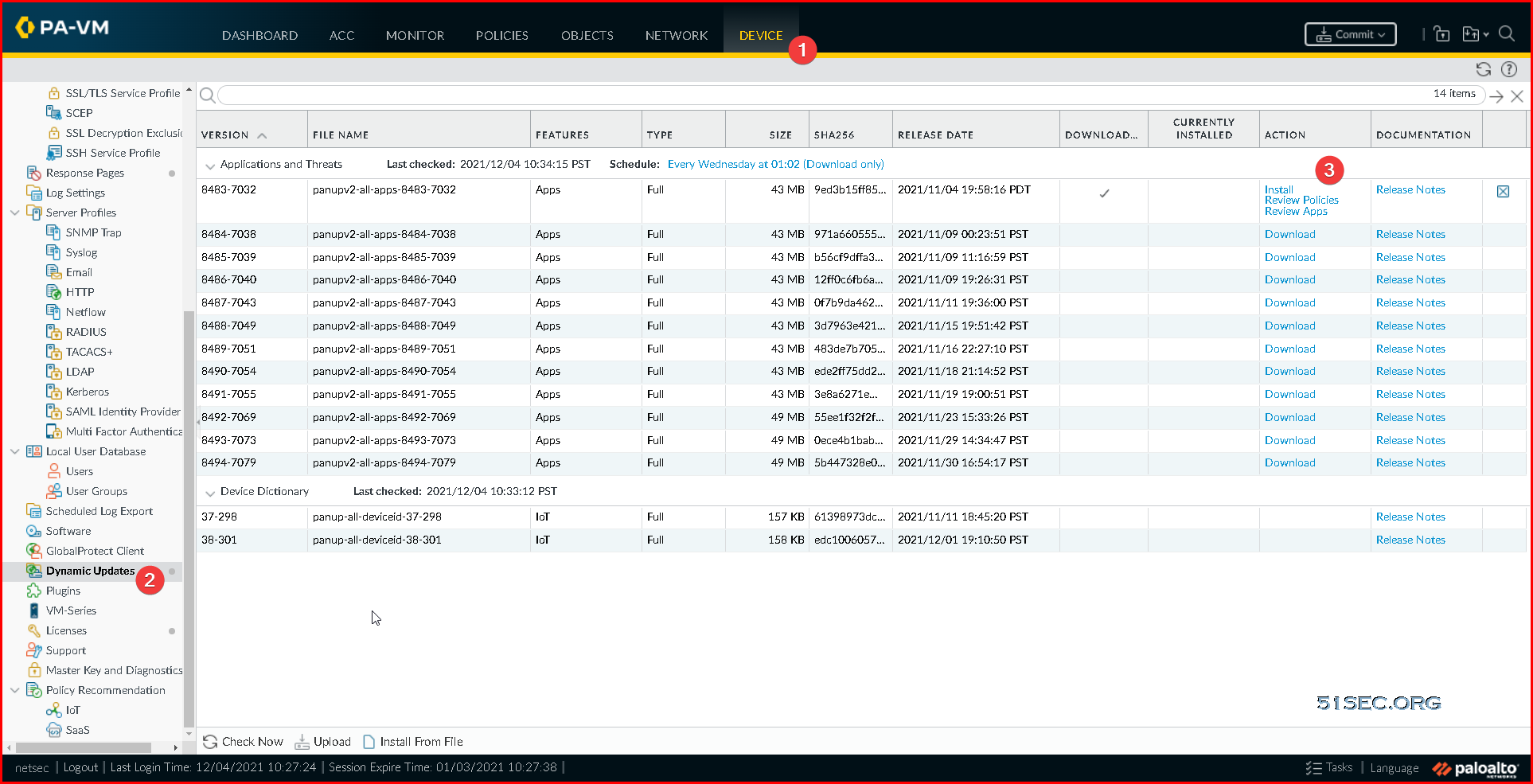
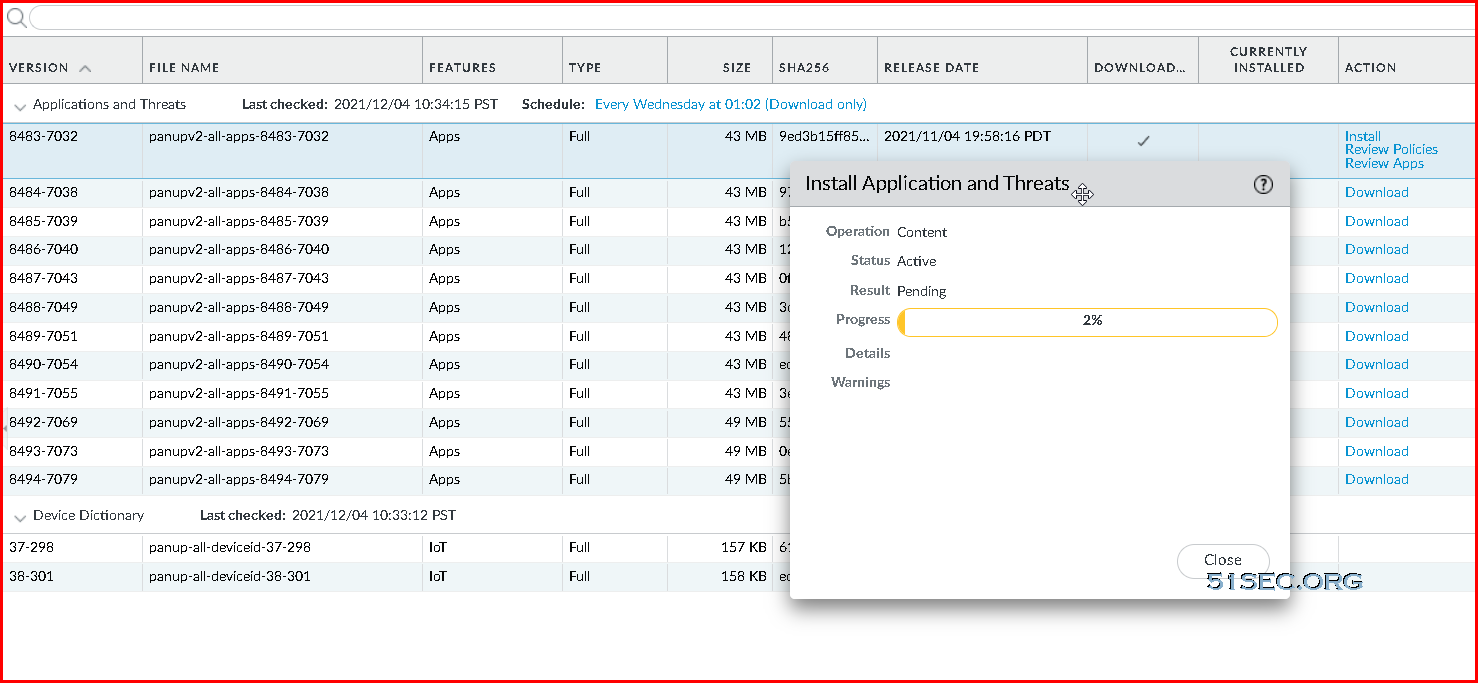
After did Check Now from Device -> Dynamic Updates page, you will be able to see some updates available for downloading. You can install them after downloaded.Basic Steps to Setup VM-Series Firewall and Register it with Credits
Steps:
https://docs.paloaltonetworks.com/vm-series/9-1/vm-series-deployment/set-up-the-vm-series-firewall-on-azure
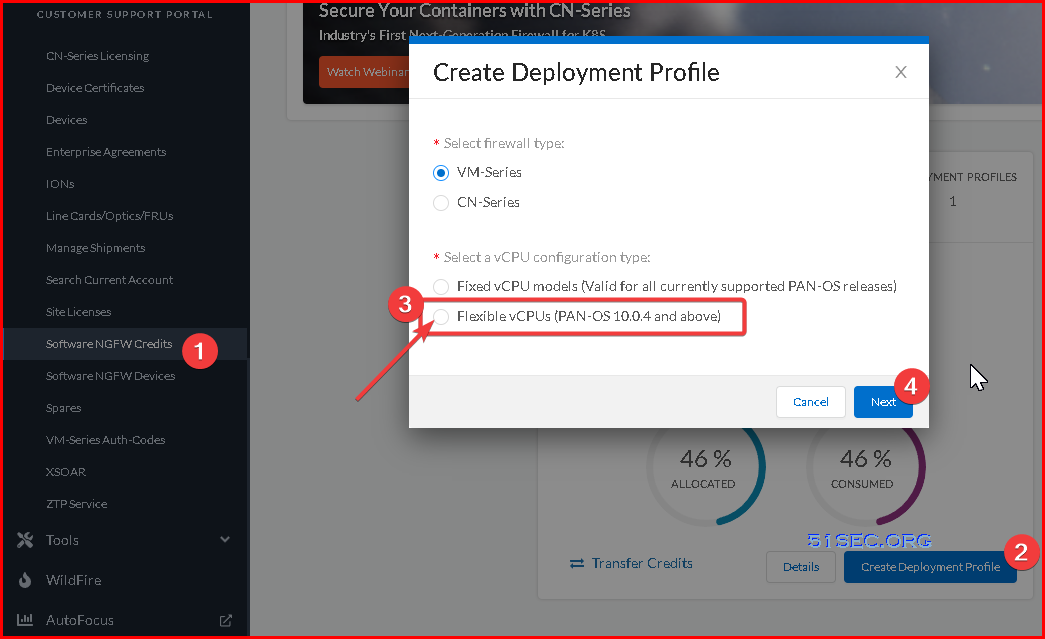
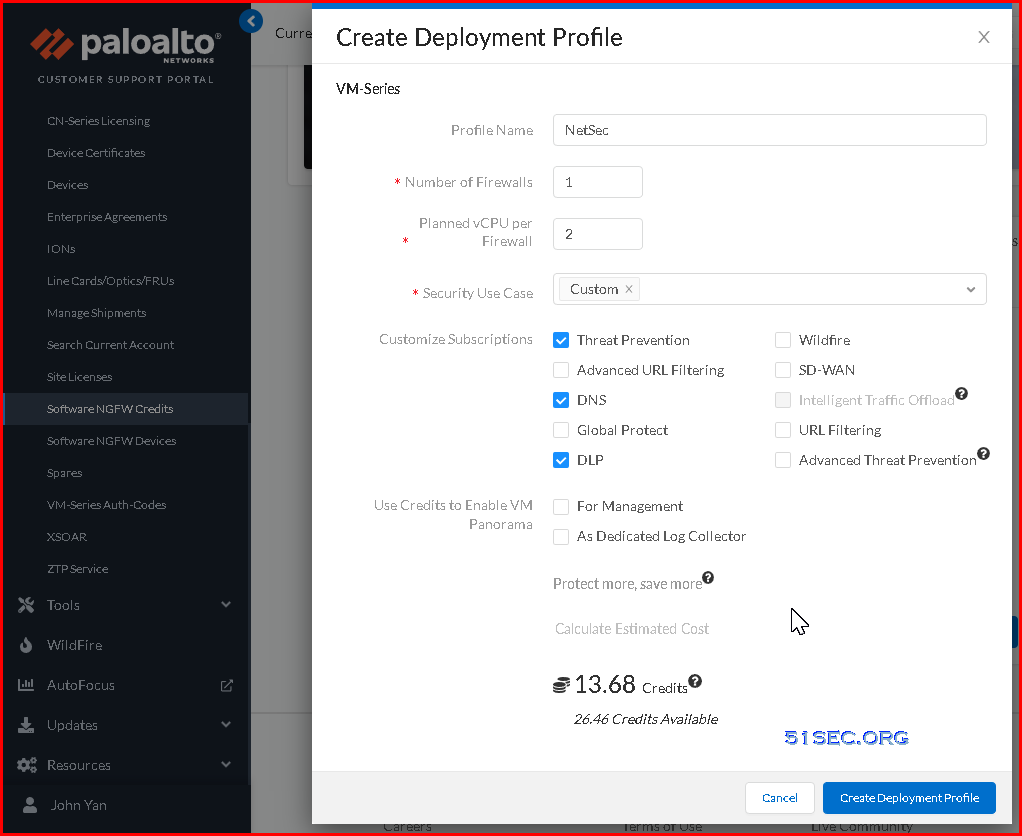
2 Create a Deployment Profile:
https://docs.paloaltonetworks.com/vm-series/9-1/vm-series-deployment/license-the-vm-series-firewall/software-ngfw/create-a-deployment-profile-vm-series
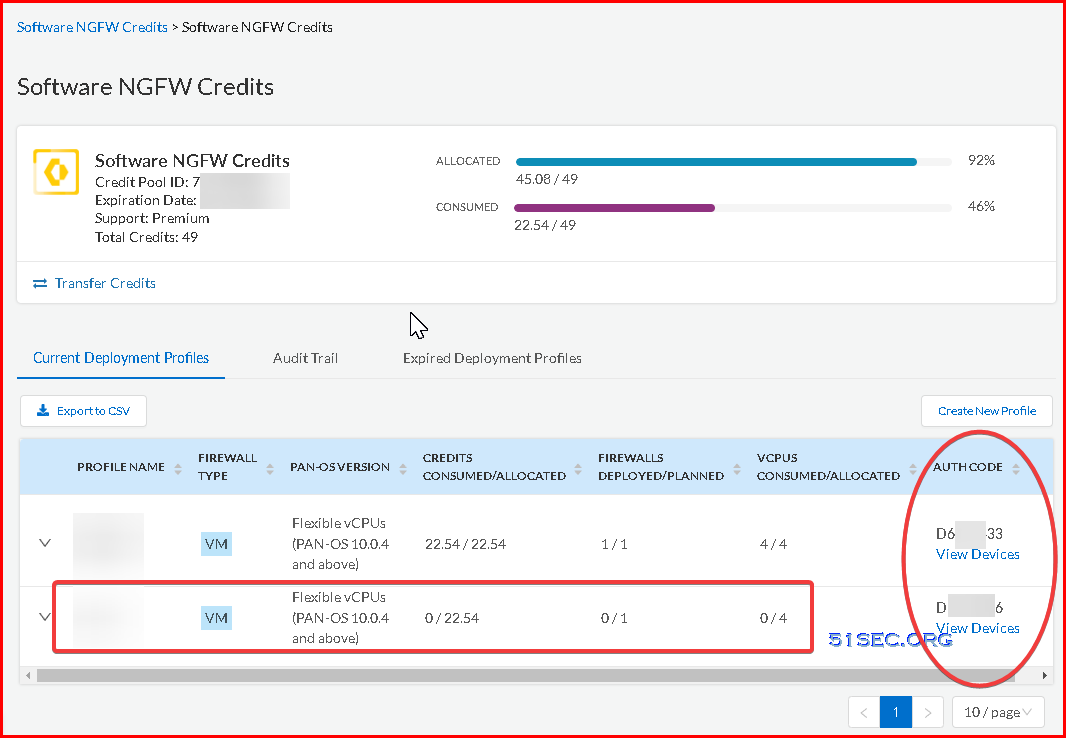
3 Manage a Deployment Profile:
https://docs.paloaltonetworks.com/vm-series/9-1/vm-series-deployment/license-the-vm-series-firewall/software-ngfw/manage-a-deployment-profile
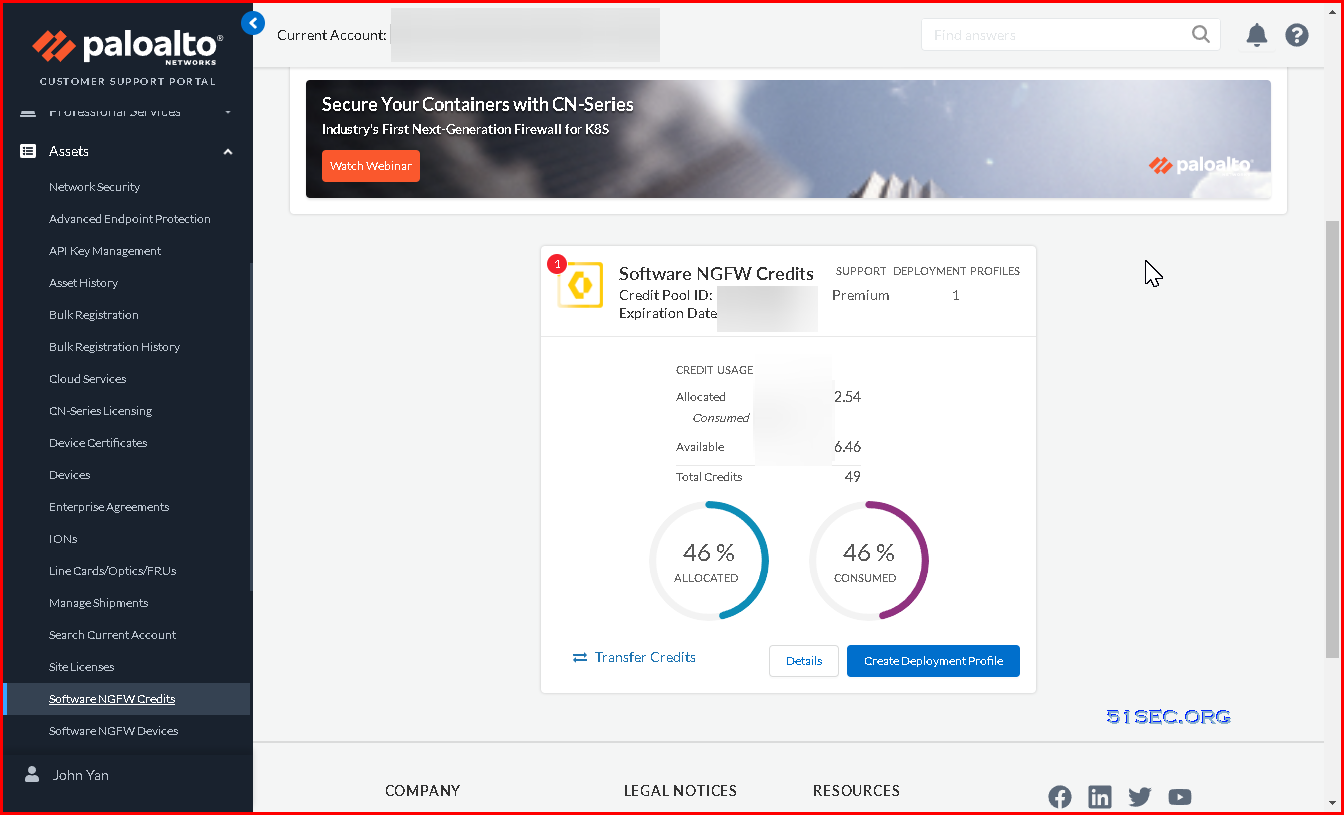
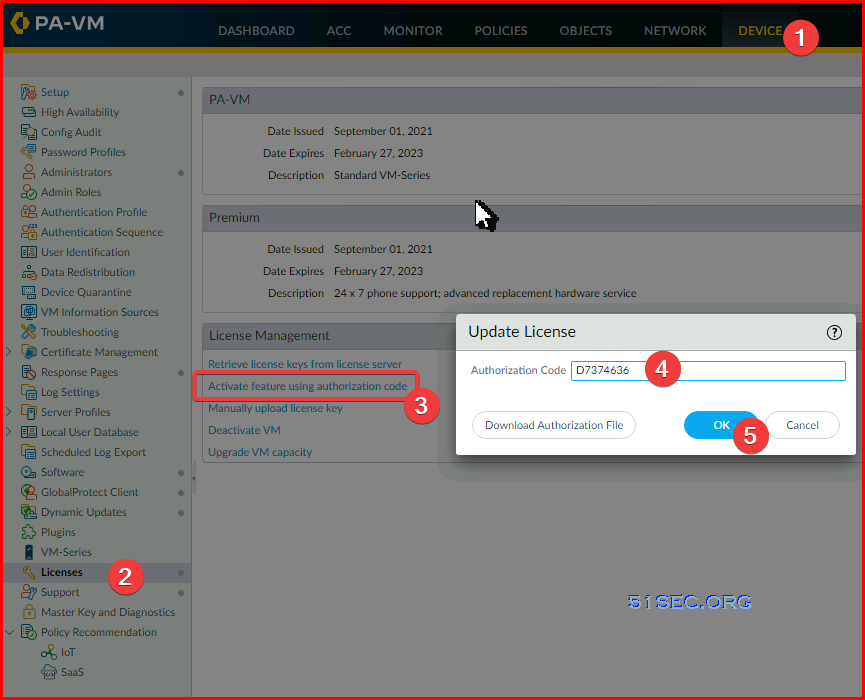
4 Register the VM-Series Firewall (Software NGFW Credits):
https://docs.paloaltonetworks.com/vm-series/10-2/vm-series-deployment/license-the-vm-series-firewall/software-ngfw/register-the-vm-series-firewall-software-ngfw-credits
Click OK to confirm the license upgrade.The firewall contacts the Palo Alto Networks update server and consumes the tokens required for your firewall based on the VM-Series model.
Videos
References
- DOES AZURE CLOUD SUPPORT PING AND TRACEROUTE
- Azure Virtual Network frequently asked questions (FAQ)
- New VM-100 deployment, cannot ping or tracert to external websites
- Palo Alto Firewall Lab Setup-Allow Inside Users To The Internet
- https://blog.51sec.org/2021/12/deploy-palo-alto-vm-series-firewall.html








No comments:
Post a Comment