Security Modeling
A security model precisely describes important aspects of security and their relationship to system behavior. The primary purpose of a security model is to provide the necessary level of understanding for a successful implementation of key security requirements. The security policy plays a primary role in determining the content of the security model. Therefore, the successful development of a good security model requires a clear, well-rounded security policy. In the case of a formal model, the development of the model also must rely on appropriate mathematical techniques of description and analysis for its form.There are some security models that are most currently using for to explain the guidelines and rules that direct confidentiality, protection, and integrity of the information. The key reason and focus on the security model implementation are confidentiality over and done with access controls and Information integrity. With the help of these security models that are the main components that should be given attention to when developing information security policies and systems. These models talk about the access rules required to instantiate the defined policy and highlight the objects that are directed by the company’s policy.
Here some of the important models we are discussing below to understand the functions and importance of Information Security models in the current business world. Five popular and valuable models are as follows;
- Bell-LaPadula Model
- Biba Model
- Clark Wilson Model
- Brewer and Nash Model
- Harrison Ruzzo Ullman Model
Security Modeling Process
Step 1: Identify Requirements on the External InterfaceStep 2: Identify Internal Requirements
Step 3: Design Rules of Operation for Policy Enforcement
Step 4: Determine What is Already Known
Step 5: Demonstrate Consistency and Correctness
Step 6: Demonstrate Relevance
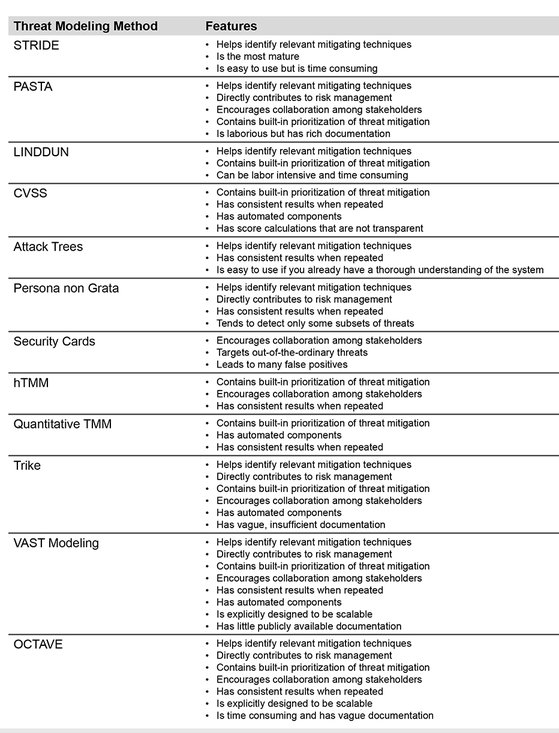
Threat Modeling Methodologies
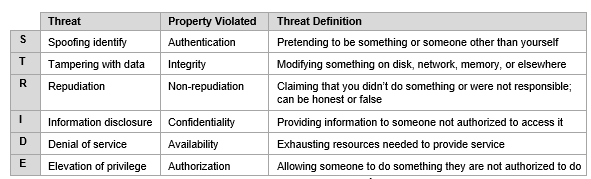
STRIDE Methodology
P.A.S.T.A.
Trike
VAST
Quantitative Threat Modeling Method: This hybrid method consists of attack trees, STRIDE, and CVSS methods applied in synergy.
| no | Model | Focus/perspective and implementation postability points |
|---|---|---|
| 1 | STRIDE | is specifically designed to focus on IT related threat |
| 2 | PASTA | is a widely used & adaptable applicable model, with threat simulation, focusing on Risks Centric methodology. Reference: Risk Centric Threat Modeling: Process for Attack Simulation and Threat Analysis |
| 3 | LINDDUN | is focused more on Data and Privacy related model |
| 4 | OCTAVE | is focused on Risk Management and organization related impact |
| 5 | VAST | scales threat modeling process across infrastructure & is focused on attacker |
| 6 | TRIKE | is a unified conceptual framework for security auditing from a risk management perspective, required a steady repeatable assessment model, is focused on Risks Measurement on calculating its stakeholders components (assets, roles, actions, risk exposure) Reference: 8) Trike v.1 Methodology Document [Draft] |
| 7 | hTMM | A hybrid type threat model which is focused on Attacker/Defender models, melds features of: Security Cards, Persona non Grata, and STRIDE |
| 8 | qTMM | A quantitative type threat model which is focused on Attacker/Defender models, melds features of Attack Trees, STRIDE, and CVSS |
| 9 | (Attack) Trees | is focused on Attacker’s scheme, works in any steady implemented production/business/process scheme, that is developed further to become the killchain nowadays |
| 10 | PnG | (Persona non Grata) has focused on attacks that represent archetypal personnels who behave in unwanted behaviors. Works perfectly to measure insider threat assessments |
Threat Modeling Process Steps
Typically, organizations conduct threat modeling during the design stage (but it can occur at other stages) of a new application to help developers find vulnerabilities and become aware of the security implications of their design, code, and configuration decisions. Generally, developers perform threat modeling in major four steps:
- Diagram. What are we building/Working on?
- Identify threats. What could go wrong?
- Mitigate. What are we doing to defend against threats?
- Validate. Have we acted on each of the previous steps?
- What are we working on? -Assess Scope
- What can go wrong? - This can be as simple as a brainstorm, or as structured as using STRIDE, Kill Chains, or Attack Trees.
- What are we going to do about it? - Decide what you’re going to do about each threat. That might be to implement a mitigation, or to apply the accept/transfer/eliminate approaches of risk management.
- Did we do a good job? - Did you do a good enough job for the system at hand?
- Pick a use case of your application
- Draw a Data Flow Diagram of this use case, which shows how data flows through your system and which applications or databases are involved.
- For each asset passing through your data flow, go through a checklist and discuss potential security risks. Rate each risk (e.g. by likelihood and impact)
- Discuss and decide what you will do about each risk
Threat Modeling Approaches
In general, there are three basic approaches to threat modeling: software centric, attacker centric, and asset centric.
Software-Centric Approach
A risk mitigation focusing on software:
- Evaluates the application being modeled
- Determines the risk
- Identifies controls to mitigate
- Requires a good understand of the application and the system it is running on
Attacker-Centric Approach
An approach that highlights the attacker:
- Puts the user into the mindset of an attacker
- Determines what is most at risk
- Needs to understand the concept of hacking
- Must have the skill set of a hacker
Asset-Centric Approach
Focusing on assets, this approach:
- Identifies assets to be protected
- Classifies assets based on data sensitivity and value potential
- Determines an “acceptable risk” level
- Takes a cyber risk–management perspective in satisfying the security auditing process
Threat Modeling Tools
There are currently five tools available for organizational threat modeling:
- Microsoft’s free threat modeling tool – the Threat Modeling Tool (formerly SDL Threat Modeling Tool). This tool also utilizes the Microsoft threat modeling methodology, is DFD-based, and identifies threats based on the STRIDE threat classification scheme. It is intended primarily for general use.
- MyAppSecurity offers the first commercially available threat modeling tool - ThreatModeler It utilizes the VAST methodology, is PFD-based, and identifies threats based on a customizable comprehensive threat library.It is intended for collaborative use across all organizational stakeholders.
- IriusRisk offers both a community and a commercial version of the tool. This tool focus on the creation and maintenance of a live Threat Model through the entire SDLC. It drives the process by using fully customizable questionnaires and Risk Pattern Libraries, and connects with other several different tools (OWASP ZAP, BDD-Security, Threadfix...) to empower automation.
- securiCAD is a threat modelling and risk management tool by the Scandinavian company foreseeti. It is intended for company cyber security management, from CISO, to security engineer, to technician. securiCAD conducts automated attack simulations to current and future IT architectures, identifies and quantifies risks holistically including structural vulnerabilities, and provides decision support based on the findings. securiCAD is offered in both commercial and community editions.
- SD Elements by Security Compass is a software security requirements management platform that includes automated threat modeling capabilities. A set of threats is generated by completing a short questionnaire about the technical details and compliance drivers of the application. Countermeasures are included in the form of actionable tasks for developers that can be tracked and managed throughout the entire SDLC.
- OWASP Application Threat Modeling - owasp.org/index.php/OWASP_Threat_Dragon
Open Source
- ADTool from University of Luxembourg
- Ent
- SeaMonster
Commercial
- AttackTree+ from Isograph
- SecurITree from Amenaza Technologies
Threat Modeling vs Others
Threat Modeling vs Risk Modeling:
Risk modeling provides a data-driven approach to understand cyber exposure and to quantify the possible outcome if a risk does indeed strike. This information is documented and disseminated in a language that makes sense to business users and decision-makers. A cyber risk model – particularly one that uses the same tools available to the cyber insurance sector – provides an efficient and repeatable way to quantify the probability of a cyberattack in financial terms.
On the other hand, a threat model helps to identify cyber threats and vulnerabilities. It also informs the company’s response and mitigation efforts.
Threat Modeling vs Threat Intelligence:
A cyber threat intelligence tool helps you collect and analyze threat information from multiple external sources to protect your enterprise from existing vulnerabilities and prepare for future ones. Next-gen cyber threat intelligence tools are essential to improve enterprise resilience and protect against external (in addition to internal) attacks.Threat intelligence enables organizations to make faster, more informed, data-backed security decisions and change their behavior from reactive to proactive in the fight against threat actors. It transforms raw data into useful interpretable intelligence for analysis.
One of the tools capable of mapping the Threat Model is Anomaly Threat Stream. A threat intelligence platform that could model any threat tailored to your specific organization.
With Anomaly Threat Stream, the analyst can build a Threat Model based on a specific adversary relevant to your organization's industry. For example, a bank would have a specific adversary of a state-sponsored attacker such as Lazarus or Cobalt Strike. By mapping all the IOCs, Tools-Technique-Procedures (TTP) along with MITRE ATT&CK Framework, an organization can have a specifically tailored cybersecurity defence that is much stronger and more impactful for its operations.
Threat Modeling vs Vulnerability Assessment
- Their primary focus: Threats vs vulnerabilities
- Proactive vs reactive processes
- Threat intelligence-driven anaysis - Both threat modeling and vulnerability assessment use threat intelligence-driven data to fuel their processes.
- Threat modeling uses CVSS and MITRE TTPs to identify vulnerabilities and threats and goes a step further to quantify threats and prioritize ways to remediate them.
Threat Modeling vs Pen Test
Differences are between Threat Modeling and penetration testing:
- Timing: Threat Modeling is preferably performed during the design phase of the system (although it is never too late to do it). Penetration testing is done during development or at least just prior to release (please don’t release first and then test on production).
- Objectives: Threat Modeling prevents or manages design flaws from a ‘white box’ perspective. Pentesting tests the actual application’s resilience – usually from a black box perspective
- Outcome: Threat Modeling leads to a list of design changes to consider, pentesting generates a list of bug fixes. Both expose risk which begs for risk management measures.
Design flaws are errors in design. They arise from a lack of security requirements (bad design), a lack of secure design knowledge (bad designer). To understand these flaws, you need contextual knowledge. That’s what you learn during a Threat Modeling workshop. Bugs are coding errors. The design might be good, but accidental errors (bad code) or a lack of secure coding practices (bad coders) can lead to vulnerabilities.
Threat Modeling won’t expose coding errors. Pentesting won’t show design flaws. We need both tools in our toolbox.
Glossary
Some Other Terms:
- Tactics, Techniques and Procedures (TTPs) : TTPs are the “patterns of activities or methods associated with a specific threat actor or group of threat actors,”
- Structured Threat Information Expression (STIX™) is a language and serialization format used to exchange cyber threat intelligence (CTI).
- Trusted Automated Exchange of Intelligence Information (TAXII™) is an application layer protocol for the communication of cyber threat information in a simple and scalable manner. TAXII is a protocol used to exchange cyber threat intelligence (CTI) over HTTPS. TAXII enables organizations to share CTI by defining an API that aligns with common sharing models.
The Glossary of the known and agreed Threat Models’ abbreviations:
| no | Model | Abbreviation Description |
|---|---|---|
| 1 | STRIDE | Spoofing, Tampering, Repudiation, Information disclosure, Denial of service, Elevation of privilege) and Associated Derivations |
| 2 | PASTA | The Process for Attack Simulation and Threat Analysis |
| 3 | LINDDUN | Linkability, Identifiability, Nonrepudiation, Detectability, Disclosure of information, Unawareness, Noncompliance) method |
| 4 | OCTAVE | Operationally Critical Threat, Asset, and Vulnerability Evaluation |
| 5 | VAST | Visual, Agile, and Simple Threat Modeling |
| 6 | hTMM | Hybrid Threat Modeling Method |
| 7 | qTMM | Quantitative Threat Modeling Method |
| 8 | TRIKE | Abbreviation is unknown, unified conceptual framework for security auditing automated concept from a risk management perspective |
| 9 | Trees | Attack Trees |
| 10 | PnG | Persona non Grata |
A Complete Guide to Effective Threat Modeling
YouTube
References
- Threat Modeling: What, Why, and How?
- Tactics, Techniques and Procedures (TTPs) Within Cyber Threat Intelligence
- A Guide to Understanding Security Modeling in Trusted Systems
- What are Information Security Models?
- Introduction To Classic Security Models
- OWASP Threat Modeling
- First Curriculum - Threat Modelling










No comments:
Post a Comment