Microsoft Defender for Endpoint is an enterprise endpoint security platform designed to help enterprise networks prevent, detect, investigate, and respond to advanced threats. Defender for Endpoint provides advanced threat protection that includes antivirus, antimalware, ransomware mitigation, and more, together with centralized management and reporting. Two plans are available:
- Microsoft Defender for Endpoint Plan 1; and
- Microsoft Defender for Endpoint Plan 2, formerly known as Microsoft Defender for Endpoint.
Related Posts:
- Microsoft Defender for Endpoint Configurations and Training Resources
- Enable Azure ATP (Microsoft Defender for Identity) and Install ATP Sensor
- Azure ATP vs Microsoft Defender ATP vs O365 ATP
- Microsoft 365 Defender
Microsoft Defender for Endpoint Features
Admin All guides:
Activate Microsoft Defender using Group Policy
Turn on Microsoft Defender Antivirus from group policy
Complete the following steps to turn on Microsoft Defender Antivirus on your device.
- Select the Start menu.
- In the search bar, type group policy. Then select Edit group policy from the listed results. The Local Group Policy Editor will open.
- Select Computer Configuration > Administrative Templates > Windows Components > Microsoft Defender Antivirus.
- Scroll to the middle of the list in the left column and select Turn off Microsoft Defender Antivirus.
- Select Disabled or Not configured. It might feel counter-intuitive to select these options because the names suggest that you're turning Microsoft Defender Antivirus off. Don't worry, these options actually ensure that it's turned on.
- Select Apply > OK.
Turn on real-time and cloud-delivered protection
Complete the following steps to turn on real-time and cloud-delivered protection. Together, these antivirus features protect you against spyware and can deliver fixes for malware issues via the cloud.
- Select the Start menu.
- In the search bar, type Windows Security. Select the matching result.
- Select Virus & threat protection.
- Under Virus & threat protection settings, select Manage settings.
- Flip each switch under Real-time protection and Cloud-delivered protection to turn them on.
If you don't see these options on your screen, they may be hidden. Complete the following steps to make them visible.
- Select the Start menu.
- In the search bar, type group policy. Then select Edit group policy from the listed results. The Local Group Policy Editor will open.
- Select Computer Configuration > Administrative Templates > Windows Components > Windows Security > Virus and threat protection.
- Select Hide the Virus and threat protection area.
- Select Disabled > Apply > OK.
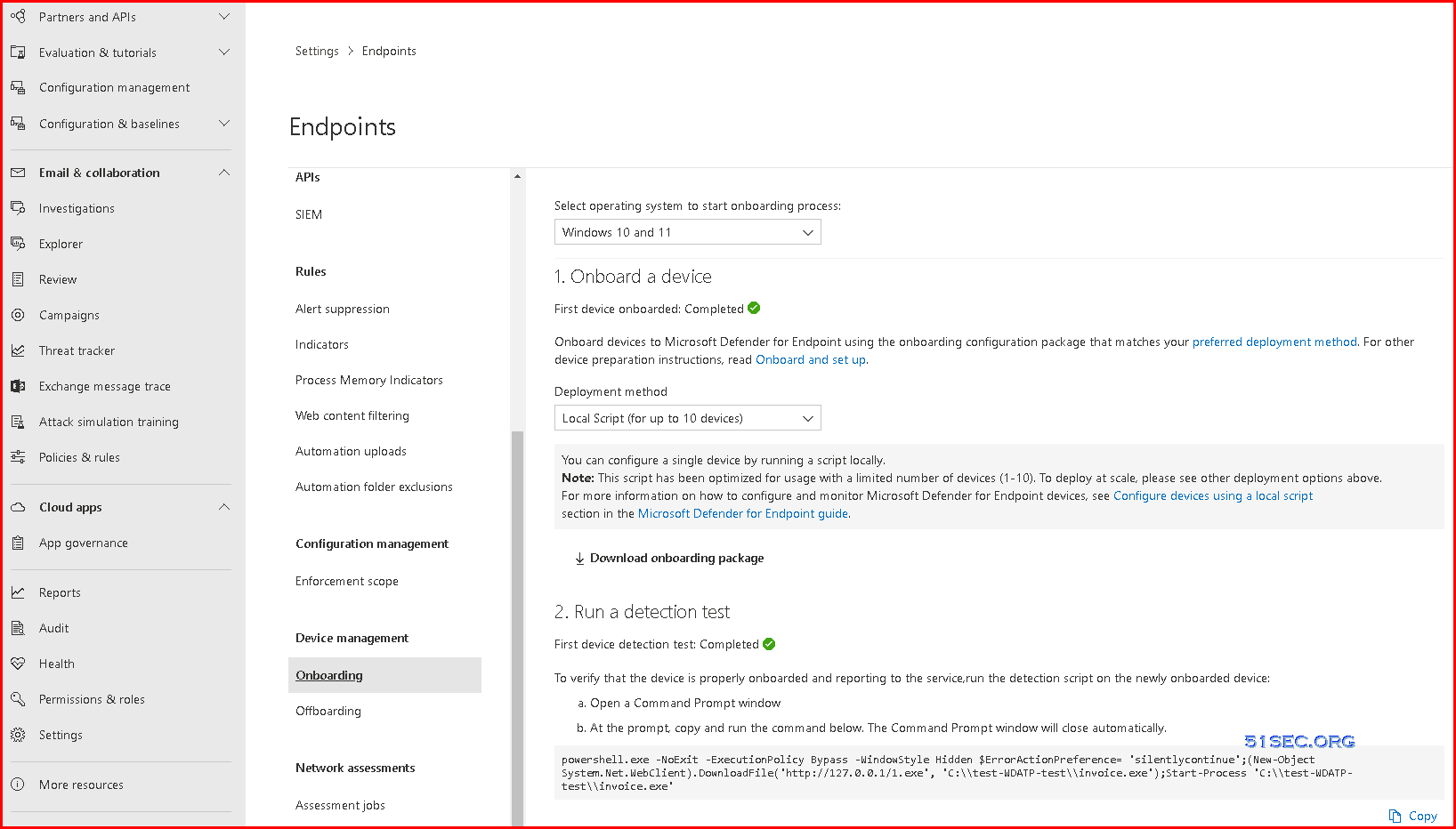
Onboarding - Device Management
1. Onboard a device
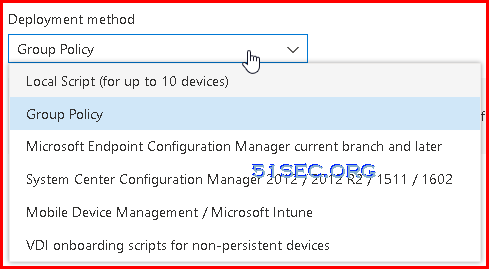
- Group Policy
You can configure your devices using Group Policy.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices see Configure devices using Group Policy section in the Microsoft Defender for Endpoint guide.
- Local Script (for up to 10 devices)
You can configure a single device by running a script locally.
Note: This script has been optimized for usage with a limited number of devices (1-10). To deploy at scale, please see other deployment options above.
For more information on how to configure and monitor Microsoft Defender for Endpoint devices, see Configure devices using a local script
section in the Microsoft Defender for Endpoint guide.
2. Run a detection test
- Open a Command Prompt window
- At the prompt, copy and run the command below. The Command Prompt window will close automatically.
powershell.exe -NoExit -ExecutionPolicy Bypass -WindowStyle Hidden $ErrorActionPreference= 'silentlycontinue';(New-Object System.Net.WebClient).DownloadFile('http://127.0.0.1/1.exe', 'C:\\test-WDATP-test\\invoice.exe');Start-Process 'C:\\test-WDATP-test\\invoice.exe'
Or you can try to download Eicar file from your windows Defender activated machines, you will get alerts on those incidents.
Onboarding tool options
The following table lists the available tools based on the endpoint that you need to onboard.
Onboarding through Azure Arc
Generate Script from Azure Arc - for multiple servers
Generated Onboarding script, and there will be some extra information you will need to put in:
$global:scriptPath = $myinvocation.mycommand.definition
function Restart-AsAdmin {
$pwshCommand = "powershell"
if ($PSVersionTable.PSVersion.Major -ge 6) {
$pwshCommand = "pwsh"
}
try {
Write-Host "This script requires administrator permissions to install the Azure Connected Machine Agent. Attempting to restart script with elevated permissions..."
$arguments = "-NoExit -Command `"& '$scriptPath'`""
Start-Process $pwshCommand -Verb runAs -ArgumentList $arguments
exit 0
} catch {
throw "Failed to elevate permissions. Please run this script as Administrator."
}
}
try {
if (-not ([Security.Principal.WindowsPrincipal] [Security.Principal.WindowsIdentity]::GetCurrent()).IsInRole([Security.Principal.WindowsBuiltInRole]::Administrator)) {
if ([System.Environment]::UserInteractive) {
Restart-AsAdmin
} else {
throw "This script requires administrator permissions to install the Azure Connected Machine Agent. Please run this script as Administrator."
}
}
# Add the service principal application ID and secret here
$ServicePrincipalId="7c7e-05-4bde-9ccc-8da9";
$ServicePrincipalClientSecret="<ENTER SECRET HERE>";
$env:SUBSCRIPTION_ID = "d9f-2d5-4ac-a0-b1";
$env:RESOURCE_GROUP = "RG-ARC-PROD-EASTUS";
$env:TENANT_ID = "79-5c47-a6-490a";
$env:LOCATION = "eastus";
$env:AUTH_TYPE = "principal";
$env:CORRELATION_ID = "226e59-6ad-4d-86-5cb24";
$env:CLOUD = "AzureCloud";
[Net.ServicePointManager]::SecurityProtocol = [Net.ServicePointManager]::SecurityProtocol -bor 3072;
# Download the installation package
Invoke-WebRequest -UseBasicParsing -Uri "https://gbl.his.arc.azure.com/azcmagent-windows" -TimeoutSec 30 -OutFile "$env:TEMP\install_windows_azcmagent.ps1";
# Install the hybrid agent
& "$env:TEMP\install_windows_azcmagent.ps1";
if ($LASTEXITCODE -ne 0) { exit 1; }
# Run connect command
& "$env:ProgramW6432\AzureConnectedMachineAgent\azcmagent.exe" connect --service-principal-id "$ServicePrincipalId" --service-principal-secret "$ServicePrincipalClientSecret" --resource-group "$env:RESOURCE_GROUP" --tenant-id "$env:TENANT_ID" --location "$env:LOCATION" --subscription-id "$env:SUBSCRIPTION_ID" --cloud "$env:CLOUD" --tags "ArcSQLServerExtensionDeployment=Disabled" --correlation-id "$env:CORRELATION_ID";
}
catch {
$logBody = @{subscriptionId="$env:SUBSCRIPTION_ID";resourceGroup="$env:RESOURCE_GROUP";tenantId="$env:TENANT_ID";location="$env:LOCATION";correlationId="$env:CORRELATION_ID";authType="$env:AUTH_TYPE";operation="onboarding";messageType=$_.FullyQualifiedErrorId;message="$_";};
Invoke-WebRequest -UseBasicParsing -Uri "https://gbl.his.arc.azure.com/log" -Method "PUT" -Body ($logBody | ConvertTo-Json) | out-null;
Write-Host -ForegroundColor red $_.Exception;
}
Running script on server after enter those necessary information:
PowerShell Command for Troubleshooting
AMEngineVersion : 1.1.18900.3
AMProductVersion : 4.18.2201.10
AMRunningMode : Normal
AMServiceEnabled : True
AMServiceVersion : 4.18.2201.10
AntispywareEnabled : True
AntispywareSignatureAge : 0
AntispywareSignatureLastUpdated : 03/04/2022 8:59:39 AM
AntispywareSignatureVersion : 1.359.1366.0
AntivirusEnabled : True
AntivirusSignatureAge : 0
AntivirusSignatureLastUpdated : 03/04/2022 8:59:38 AM
AntivirusSignatureVersion : 1.359.1366.0
BehaviorMonitorEnabled : True
ComputerID : 580F14A1-4405-EEA6-2C71-96B3EA0C42C6
ComputerState : 0
DeviceControlDefaultEnforcement : N/A
DeviceControlPoliciesLastUpdated : 03/04/2022 2:04:19 PM
DeviceControlState : N/A
FullScanAge : 0
FullScanEndTime : 03/04/2022 1:48:27 PM
FullScanStartTime : 03/04/2022 1:10:43 PM
IoavProtectionEnabled : True
IsTamperProtected : False
IsVirtualMachine : False
LastFullScanSource : 2
LastQuickScanSource : 2
NISEnabled : True
NISEngineVersion : 1.1.18900.3
NISSignatureAge : 0
NISSignatureLastUpdated : 03/04/2022 8:59:38 AM
NISSignatureVersion : 1.359.1366.0
OnAccessProtectionEnabled : True
QuickScanAge : 481
QuickScanEndTime : 11/07/2020 9:36:57 PM
QuickScanStartTime : 11/07/2020 9:35:40 PM
RealTimeProtectionEnabled : True
RealTimeScanDirection : 0
TamperProtectionSource : Service Init
TDTMode : cm
TDTStatus : Disabled
TDTTelemetry : Disabled
PSComputerName :
PS C:\Users\test1> get-mppreference
AllowDatagramProcessingOnWinServer : False
AllowNetworkProtectionDownLevel : False
AllowNetworkProtectionOnWinServer : False
AllowSwitchToAsyncInspection : False
AttackSurfaceReductionOnlyExclusions : {N/A: Must be and administrator to view exclusions}
AttackSurfaceReductionRules_Actions :
AttackSurfaceReductionRules_Ids :
CheckForSignaturesBeforeRunningScan : True
CloudBlockLevel : 0
CloudExtendedTimeout : 50
ComputerID : 580F14A1-4405-EEA6-2C71-96B3EA0C42C6
ControlledFolderAccessAllowedApplications : {N/A: Must be and administrator to view exclusions}
ControlledFolderAccessProtectedFolders :
DefinitionUpdatesChannel : 0
DisableArchiveScanning : False
DisableAutoExclusions : False
DisableBehaviorMonitoring : False
DisableBlockAtFirstSeen : False
DisableCatchupFullScan : True
DisableCatchupQuickScan : True
DisableCpuThrottleOnIdleScans : True
DisableDatagramProcessing : False
DisableDnsOverTcpParsing : False
DisableDnsParsing : False
DisableEmailScanning : True
DisableFtpParsing : False
DisableGradualRelease : False
DisableHttpParsing : False
DisableInboundConnectionFiltering : False
DisableIOAVProtection : False
DisableNetworkProtectionPerfTelemetry : False
DisablePrivacyMode : False
DisableRdpParsing : False
DisableRealtimeMonitoring : False
DisableRemovableDriveScanning : False
DisableRestorePoint : True
DisableScanningMappedNetworkDrivesForFullScan : True
DisableScanningNetworkFiles : False
DisableScriptScanning : False
DisableSshParsing : False
DisableTlsParsing : False
EnableControlledFolderAccess : 0
EnableDnsSinkhole : True
EnableFileHashComputation : False
EnableFullScanOnBatteryPower : False
EnableLowCpuPriority : False
EnableNetworkProtection : 0
EngineUpdatesChannel : 0
ExclusionExtension : {N/A: Must be and administrator to view exclusions}
ExclusionIpAddress : {N/A: Must be and administrator to view exclusions}
ExclusionPath : {N/A: Must be and administrator to view exclusions}
ExclusionProcess : {N/A: Must be and administrator to view exclusions}
ForceUseProxyOnly : False
HighThreatDefaultAction : 0
LowThreatDefaultAction : 0
MAPSReporting : 1
MeteredConnectionUpdates : False
ModerateThreatDefaultAction : 0
PlatformUpdatesChannel : 0
ProxyBypass :
ProxyPacUrl :
ProxyServer :
PUAProtection : 0
QuarantinePurgeItemsAfterDelay : 90
RandomizeScheduleTaskTimes : True
RealTimeScanDirection : 0
RemediationScheduleDay : 0
RemediationScheduleTime : 12:30:00
ReportingAdditionalActionTimeOut : 10080
ReportingCriticalFailureTimeOut : 10080
ReportingNonCriticalTimeOut : 1440
ScanAvgCPULoadFactor : 50
ScanOnlyIfIdleEnabled : True
ScanParameters : 2
ScanPurgeItemsAfterDelay : 15
ScanScheduleDay : 0
ScanScheduleOffset : 750
ScanScheduleQuickScanTime : 00:00:00
ScanScheduleTime : 12:30:00
SchedulerRandomizationTime : 4
ServiceHealthReportInterval : 60
SevereThreatDefaultAction : 0
SharedSignaturesPath :
SignatureAuGracePeriod : 0
SignatureBlobFileSharesSources :
SignatureBlobUpdateInterval : 60
SignatureDefinitionUpdateFileSharesSources :
SignatureDisableUpdateOnStartupWithoutEngine : False
SignatureFallbackOrder : MicrosoftUpdateServer
SignatureFirstAuGracePeriod : 120
SignatureScheduleDay : 0
SignatureScheduleTime : 00:15:00
SignatureUpdateCatchupInterval : 1
SignatureUpdateInterval : 1
SubmitSamplesConsent : 1
ThreatIDDefaultAction_Actions :
ThreatIDDefaultAction_Ids :
ThrottleForScheduledScanOnly : True
TrustLabelProtectionStatus : 0
UILockdown : False
UnknownThreatDefaultAction : 0
PSComputerName :
Update-MpSignature -UpdateSource InternalDefinitionUpdateServerPS C:\Program Files\Windows Defender> .\MpCmdRun.exe -SignatureUpdate
Signature update started . . .
Signature update finished.
PS C:\Program Files\Windows Defender>PS C:\Program Files\Windows Defender> .\MpCmdRun.exe -removeDefinitions
You need administrator privilege to execute this command.PS C:\windows\System32> Get-MpPreference
AllowDatagramProcessingOnWinServer : False
AllowNetworkProtectionDownLevel : False
AllowNetworkProtectionOnWinServer : False
AllowSwitchToAsyncInspection : False
AttackSurfaceReductionOnlyExclusions : {N/A: Must be and administrator to view exclusions}
AttackSurfaceReductionRules_Actions :
AttackSurfaceReductionRules_Ids :
CheckForSignaturesBeforeRunningScan : True
CloudBlockLevel : 0
CloudExtendedTimeout : 50
ComputerID : 580F14A1-4405-EEA6-2C71-96B3EA0C42C6
ControlledFolderAccessAllowedApplications : {N/A: Must be and administrator to view exclusions}
ControlledFolderAccessProtectedFolders :
DefinitionUpdatesChannel : 0
DisableArchiveScanning : False
DisableAutoExclusions : False
DisableBehaviorMonitoring : False
DisableBlockAtFirstSeen : False
DisableCatchupFullScan : True
DisableCatchupQuickScan : True
DisableCpuThrottleOnIdleScans : True
DisableDatagramProcessing : False
DisableDnsOverTcpParsing : False
DisableDnsParsing : False
DisableEmailScanning : True
DisableFtpParsing : False
DisableGradualRelease : False
DisableHttpParsing : False
DisableInboundConnectionFiltering : False
DisableIOAVProtection : False
DisableNetworkProtectionPerfTelemetry : False
DisablePrivacyMode : False
DisableRdpParsing : False
DisableRealtimeMonitoring : False
DisableRemovableDriveScanning : False
DisableRestorePoint : True
DisableScanningMappedNetworkDrivesForFullScan : True
DisableScanningNetworkFiles : False
DisableScriptScanning : False
DisableSshParsing : False
DisableTlsParsing : False
EnableControlledFolderAccess : 0
EnableDnsSinkhole : True
EnableFileHashComputation : False
EnableFullScanOnBatteryPower : False
EnableLowCpuPriority : False
EnableNetworkProtection : 0
EngineUpdatesChannel : 0
ExclusionExtension : {N/A: Must be and administrator to view exclusions}
ExclusionIpAddress : {N/A: Must be and administrator to view exclusions}
ExclusionPath : {N/A: Must be and administrator to view exclusions}
ExclusionProcess : {N/A: Must be and administrator to view exclusions}
ForceUseProxyOnly : False
HighThreatDefaultAction : 0
LowThreatDefaultAction : 0
MAPSReporting : 1
MeteredConnectionUpdates : False
ModerateThreatDefaultAction : 0
PlatformUpdatesChannel : 0
ProxyBypass :
ProxyPacUrl :
ProxyServer : 14.10.3.41:8080
PUAProtection : 0
QuarantinePurgeItemsAfterDelay : 90
RandomizeScheduleTaskTimes : True
RealTimeScanDirection : 0
RemediationScheduleDay : 0
RemediationScheduleTime : 12:30:00
ReportingAdditionalActionTimeOut : 10080
ReportingCriticalFailureTimeOut : 10080
ReportingNonCriticalTimeOut : 1440
ScanAvgCPULoadFactor : 50
ScanOnlyIfIdleEnabled : True
ScanParameters : 2
ScanPurgeItemsAfterDelay : 15
ScanScheduleDay : 0
ScanScheduleOffset : 750
ScanScheduleQuickScanTime : 00:00:00
ScanScheduleTime : 12:30:00
SchedulerRandomizationTime : 4
ServiceHealthReportInterval : 60
SevereThreatDefaultAction : 0
SharedSignaturesPath :
SignatureAuGracePeriod : 0
SignatureBlobFileSharesSources :
SignatureBlobUpdateInterval : 60
SignatureDefinitionUpdateFileSharesSources :
SignatureDisableUpdateOnStartupWithoutEngine : False
SignatureFallbackOrder : MicrosoftUpdateServer
SignatureFirstAuGracePeriod : 120
SignatureScheduleDay : 0
SignatureScheduleTime : 00:15:00
SignatureUpdateCatchupInterval : 1
SignatureUpdateInterval : 1
SubmitSamplesConsent : 1
ThreatIDDefaultAction_Actions :
ThreatIDDefaultAction_Ids :
ThrottleForScheduledScanOnly : True
TrustLabelProtectionStatus : 0
UILockdown : False
UnknownThreatDefaultAction : 0
PSComputerName :
Compare Defender plans and MS 365 E3 + MS 365 E5 Security
Defender for Endpoints P1 vs P2
The following table describes what's included in each plan at a high level.

Defender for Servers P1 vs P2
Microsoft Defender for Server Plan 2 only from Azure Monetary Commitment, Microsoft 365 E5 has Microsoft Defender for Endpoint Plan 2, subscription for users a their devices. Defender for servers is not included in Micrsoft 365 E5. You will have to pay that separately from Defender for Clouds.
License:
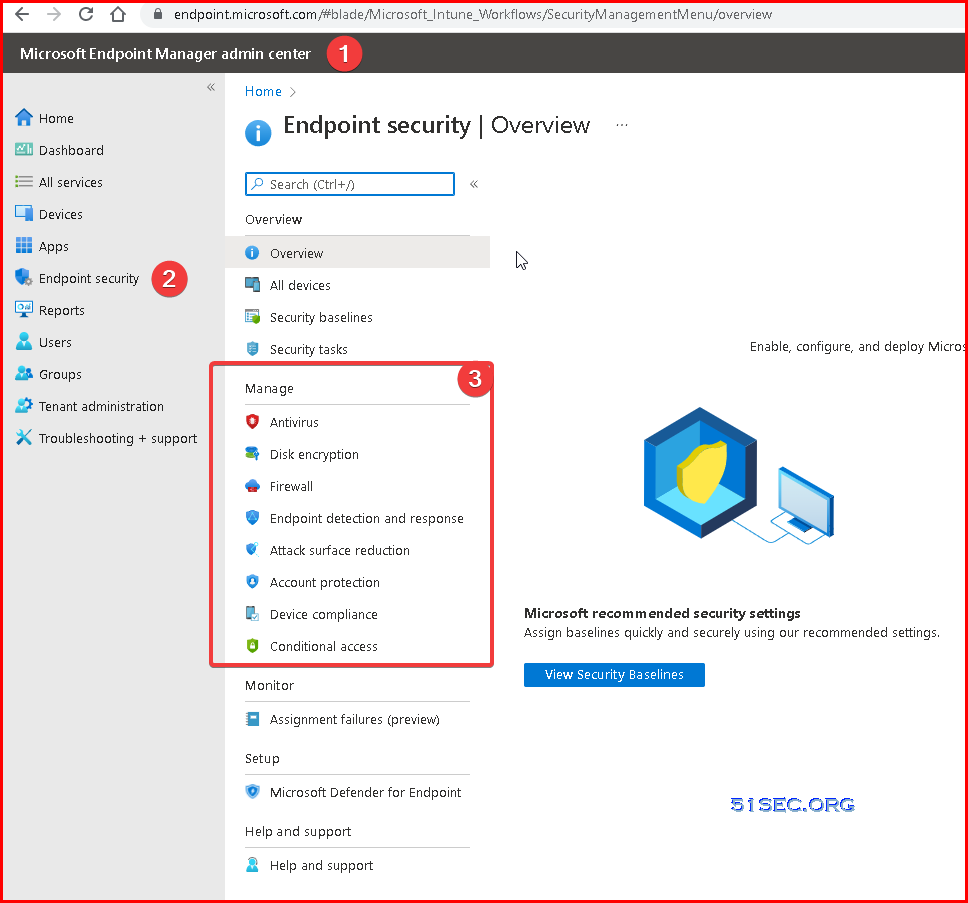
Define Defender Policies in Endpoint Manager (Intune)
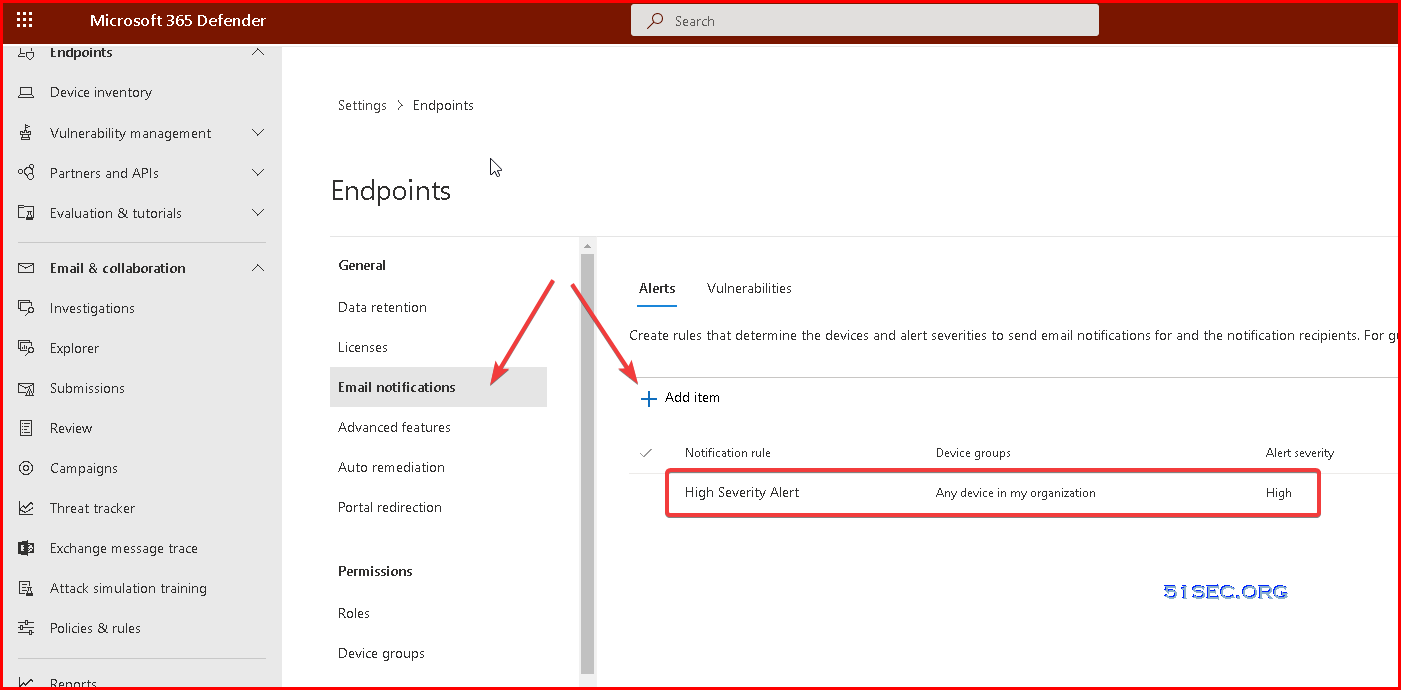
Create Notification Rules
Go to Microsoft 365 Defender - Settings - Endpoints
Click Email notifications - Alerts - Add items
Also you can create a notification rule for critical/high vulnerability event:
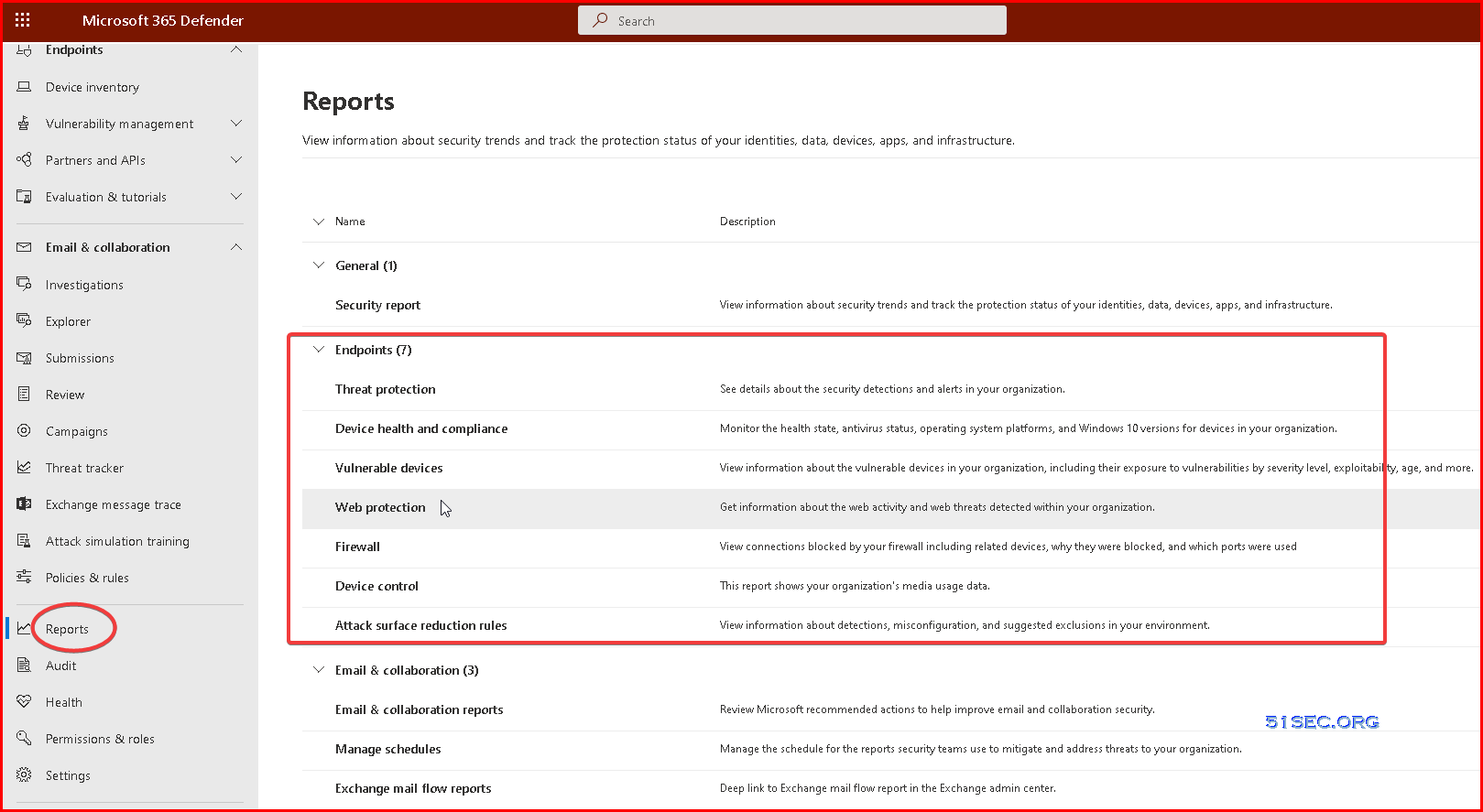
Reports
Take response actions
On a device
- Response actions on devices
- Manage tags
- Start an automated investigation
- Start a Live Response session
- Collect investigation package
- Run antivirus scan
- Restrict app execution
- Isolate devices from the network
- Consult a threat expert
- Check activity details in Action center
On a file
- Response actions on files
- Stop and quarantine files in your network
- Restore file from quarantine
- Add indicators to block or allow a file
- Consult a threat expert
- Check activity details in Action center
- Download or collect file
- Deep analysis
Training
Security Operations Fundamentals
Module 1. Technical overview
- Short overview “What is Microsoft 365 Defender"
Unified experiences across endpoint and email
- New value for Defender for Identity
- New value for Defender for Office 365
- XDR announcement blog
Module 2. Getting started
- Quick tutorial to get you started
- Starting the service
- Prepare your Azure Active Directory
- Manage access
- Provide your feedback
Module 3. Investigation – Incident
- Work with incidents
- Get email notifications on new incidents
- Improved incident queue
- Classification of incidents & alerts
- See how consolidated incidents improve SOC efficiency
- Protect your organization with Microsoft 365 Defender
- Incidents trend graph view
Responding to my first incident, a tutorial and walkthrough for new-to-role analysts
- Email Entity page
Module 4. Threat Analytics
Module 5. Advanced hunting
- Quick overview & a short tutorial that will get you started fast
- Learn the query language
- Understand the schema
Module 6. Self-healing
Module 7. Community (blogs, webinars, GitHub)
Module 8. Partner
> Ready for the Fundamentals Knowledge Check?
Security Operations Intermediate
Module 1. Architecture
Module 2. Investigation
- Correlating and consolidating attacks into incidents
- Investigate incidents
- Mapping attack chains from cloud to endpoint
- Prioritize incidents
- Manage incidents
- Investigation improvements for Microsoft Defender for Office 365
- Report false positives/negatives
Module 3. Advanced hunting
- Advanced hunting cheat sheet
- Microsoft Cloud App Security: The Hunt in a multi-stage incident
- Hunting with Microsoft Cloud App Security data
- Microsoft Cloud App Security: The Hunt for Insider Risk
- Limitless Advanced Hunting with Azure Data Explorer (ADX)
- Take action on advanced hunting query results
- Advanced Hunting in portal Schema Reference
- DeviceFromIP() function in advanced hunting
- Webinar series, episode 1: KQL fundamentals (MP4, YouTube)
- Advanced hunting query best practices
- Hunt across cloud app activities
- Use additional email data in your hunting queries
- Use Azure Active Directory audit log data in advanced hunting
- Hunt for Azure Active Directory sign-in events
- Advanced hunting queries on GitHub
Module 4. Automated investigation and remediation
Module 6. Self-healing
- Learn about the various AIR capabilities
- Self-healing explained based on an example
- Configure automated investigation and response capabilities
- Approve or reject pending actions
- Report a false positive/negative to Microsoft for analysis
- The action center
Module 5. Build your own lab
Module 7. Reporting
Module 8. Microsoft Threat Experts
> Ready for the Intermediate Knowledge Check?
Security Operations Expert
Module 1. Incidents
- Prioritize incidents
- Manage incidents
- Report false positives/negatives
- Deep-dive attack playbooks from the DART team for seasoned analysts
- Incident response overview
Module 2. Advanced hunting
- Webinar series, episode 2: Joins (MP4, YouTube)
- Webinar series, episode 3: Summarizing, pivoting, and visualizing Data (MP4, YouTube)
- Webinar series, episode 4: Let’s hunt! Applying KQL to incident tracking (MP4, YouTube)
- ⤴ Plural sight KQL training
Module 3. APIs, custom reports, SIEM & other integrations
- Microsoft 365 Defender APIs
- Best practices for leveraging API's - Episode Two
- Streaming API Announcement blog
- Overview of the Streaming API
- Stream Microsoft 365 Defender events
- Azure Sentinel and Microsoft 365 Defender incident integration
- Overview Azure Sentinel integration
- Azure Sentinel integration
Microsoft Learn learning paths
Use these Microsoft Learn learning paths and their modules to build an understanding of Microsoft 365 Defender and Microsoft Defender for Endpoint, one module and unit at a time.
- Detect and respond to cyber attacks with Microsoft 365 Defender
- Secure your organization with Microsoft Defender for Endpoint
Deployment Steps
1. Onboarding Devices
- RG-ARC-P-EASTUS
By default, Defender for Servers is enabled as a subscription-wide setting, covering all Azure VMs, Azure Arc-enabled Servers and VMSS nodes at the same time. However, there are scenarios in which it makes sense to downgrade individual machines from Defender for Servers Plan 2 to Plan 1, or only enable Defender for Servers Plan 1 on a subset of machines in a subscription.
This folder contains a PowerShell script that allows you to select machines based on Azure resource tags, or a resource group to configure them individually rather than using the same plan setting for all machines in a subscription.
Connecting terminal...
Welcome to Azure Cloud Shell
Type "az" to use Azure CLI
Type "help" to learn about Cloud Shell
Your Cloud Shell session will be ephemeral so no files or system changes will persist beyond your current session.
MOTD: SqlServer has been updated to Version 22!
VERBOSE: Auth> & './ResourceLevelPricingAtScale (1).ps1'
WARNING: Upcoming breaking changes in the cmdlet 'Get-AzAccessToken' :
The Token property of the output type will be changed from String to SecureString. Add the [-AsSecureString] switch to avoid the impact of this upcoming breaking change.
- The change is expected to take effect in Az version : '14.0.0'
- The change is expected to take effect in Az.Accounts version : '5.0.0'
Note : Go to https://aka.ms/azps-changewarnings for steps to suppress this breaking change warning, and other information on breaking changes in Azure PowerShell.
WARNING: Upcoming breaking changes in the cmdlet 'Get-AzAccessToken' :
The Token property of the output type will be changed from String to SecureString. Add the [-AsSecureString] switch to avoid the impact of this upcoming breaking change.
- The change is expected to take effect in Az version : '14.0.0'
- The change is expected to take effect in Az.Accounts version : '5.0.0'
Note : Go to https://aka.ms/azps-changRG-ARC-P-EASTUS-01o suppress this breaking change warning, and other information on breaking changes in Azure RGwerShell.
https://management.azure.com/subscriptions/d9-2-4-a-b1a/resourceGroups/RG-ARC-P-EASTUS-01/providers/Microsoft.HybridCompute/machines?api-version=2022-12-27
Found the following resources:all resourced under a given Resource Group, or 'TAG' to set pricing for all resources with a given tagName and tagValue: R
Virtual Machines:
-------------------
Virtual Machine Scale Sets:
-------------------
ARC Machines:
1 : M-S1-HQ
2 : E-B01
3 : C-C-HQ
4 : E-ANS
5 : E-AD01
6 : E-CA1
-----------------------------------------------------------------------
Press any key to proceed or press 'N' to exit:
-------------------
Enter the command set these resources - 'Free' or 'Standard' or 'Delete' or 'Read' (choosing 'Free' will remove the Defender protection; 'Standard' will enable the 'P1' subplan; 'Delete' will remove any explicitly set configuration (the resource will inherit the parent's configuration); 'Read' will read the current configuration): Standard
-------------------
Processing (setting or reading) Virtual Machines:
-------------------
Processing (setting or reading) Virtual Machine Scale Sets:
-------------------
Processing (setting or reading) ARC Machine:
Token expires on: 01/27/2025 16:02:31 - currentTime: 01/27/2025 14:43:37
Processing (setting or reading) pricing configuration for 'M-S1-HQ':
Successfully updated pricing configuration for M-S1-HQ
Token expires on: 01/27/2025 16:02:31 - currentTime: 01/27/2025 14:43:39
Processing (setting or reading) pricing configuration for 'E-B01':
Successfully updated pricing configuration for E-B01
Failed to update pricing configuration for C-CC-HQ
Response StatusCode: 503eading) pricing configuration for 'C-CC-HQ':
Response StatusDescription:
Error from response:
{
"error": {
"code": "ServerTimeout",
"message": "The request timed out. Diagnostic information: timestamp \u002720250127T144401Z\u0027, subscription id \u0027d9-2-4-a-b1a\u0027, tracking id \u0027a8fd740027, request correlation id \u0027a87202\u0027."
}
}
Token expires on: 01/27/2025 16:02:31 - currentTime: 01/27/2025 14:44:01
Processing (setting or reading) pricing configuration for 'E-A':
Successfully updated pricing configuration for E-A
Token expires on: 01/27/2025 16:02:31 - currentTime: 01/27/2025 14:44:03
Processing (setting or reading) pricing configuration for 'E-AD01':
Successfully updated pricing configuration for E-A01
Token expires on: 01/27/2025 16:02:31 - currentTime: 01/27/2025 14:44:04
Processing (setting or reading) pricing configuration for 'E-CA1':
Successfully updated pricing configuration for EC-CA1
-----------------------------------------------------------------------
-----------------------------------------------------------------------
Summary of Pricing API results:
-------------------
Found Virtual Machines count: 0
Successfully processed (set or read) Virtual Machines count: 0
Failed processing (setting or reading) Virtual Machines count: 0
Found Virtual Machine Scale Sets count: 0
Successfully processed (set or read) Virtual Machine Scale Sets result: 0
Failed processing (setting or reading) Virtual Machine Scale Sets count: 0
Found ARC machines count: 6
Successfully processed (set or read) ARC Machines count: 5
Failed processing (setting or reading) ARC Machines count: 1
-------------------
Overall
Successfully processed (set or read) resources: 5
Failures processing (setting or reading) resources: 1
PS /home/NETSEC>
- sudo bash -x MicrosoftDefenderATPOnboardingMacOs2.sh
- Deployment with a different Mobile Device Management (MDM) system for Microsoft Defender for Endpoint on Mac - Microsoft Defender for Endpoint | Microsoft Learn
- mdatp-xplat/macos/mobileconfig/profiles at master · microsoft/mdatp-xplat · GitHub
- Manual deployment for Microsoft Defender for Endpoint on macOS - Microsoft Defender for Endpoint | Microsoft Learn
2. Security Configuration Change
3. Security Policy Creation
4. Remove existing Antivirus / Enable MDE
- Path:
HKLM\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection - Name:
ForceDefenderPassiveMode - Type:
REG_DWORD - Value:
1
Or PowerShell Script:
$RegistryPath = 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection'
$Name = 'ForceDefenderPassiveMode'
$Value = '1'
New-ItemProperty -Path $RegistryPath -Name $Name -Value $Value -PropertyType DWORD -Force$RegistryPath = 'HKLM:\SOFTWARE\Policies\Microsoft\Windows Advanced Threat Protection'
$Name = 'ForceDefenderPassiveMode'
$Value = '0'
New-ItemProperty -Path $RegistryPath -Name $Name -Value $Value -PropertyType DWORD -Force
Note: New-ItemProperty only DWORD, not REG_DWORD.
Security considerations for Tier 0 assets
For a Tier 0 asset, you should use the local agent security controls to disable any unused functionality in the agent to prevent any intentional—or accidental—use of those features to make changes to the server. This includes:
- Disabling remote access capabilities
- Setting an extension allowlist for the extensions you intend to use, or disabling the extension manager if you are not using extensions
- Disabling the machine configuration agent if you don’t intend to use machine configuration policies
The following example shows how to lock down the Azure Connected Machine agent for a domain controller that needs to use the Azure Monitor Agent to collect security logs for Microsoft Sentinel and Microsoft Defender for Servers to protect against malware threats:
- azcmagent config set incomingconnections.enabled false
- azcmagent config set guestconfiguration.enabled false
- azcmagent config set extensions.allowlist “Microsoft.Azure.Monitor/AzureMonitorWindowsAgent,Microsoft.Azure.AzureDefenderForServers/MDE.Windows”
Troubleshooting
For Workstations:
Windows Defender should be active.
References
- Microsoft Defender for Endpoint Plan 1 and Plan 2
- Portal for Microsoft 365 Defender
- Microsoft Defender for Endpoint documentation
- Defender-specific functions
- Defender Proxy Settings
- Firewall settings: https://aka.ms/MDE-streamlined-urls
- Enforcement Scope Documentation (This is what we will use to
facilitate the configuration of MDE using Intune): Learn about using Intune to manage Microsoft Defender settings on
devices that aren't enrolled with Intune | Microsoft Learn
- Defender for Servers: Select a Defender for Servers plan in Microsoft Defender for Cloud
- Microsoft Defender for Cloud | Microsoft Learn
- Generating an onboarding script: Onboard Windows devices using a local script - Microsoft Defender
for Endpoint | Microsoft Learn
- Azure Arc: Quickstart - Connect hybrid machine with Azure Arc-enabled servers
- Azure Arc | Microsoft Learn
Article
What is Microsoft Defender XDR? - Microsoft Defender XDR
Article
Microsoft Defender XDR in the Microsoft Defender portal - Microsoft Defender XDR
Web page
Microsoft 365 Defender Interactive Guide
Article
Incidents and alerts in the Microsoft Defender portal - Microsoft Defender XDR
Article
Responding to your first incident in Microsoft Defender XDR - Microsoft Defender XDR
Manage incidents with automatic attack disruption in Microsoft 365 Defender
Microsoft Tech Community
Automatic disruption of Ransomware and BEC attacks with Microsoft 365 Defender
Article
Configure automatic attack disruption in Microsoft Defender XDR - Microsoft Defender XDR
Article
Automatic attack disruption in Microsoft Defender XDR - Microsoft Defender XDR
Event Session
What’s new in SIEM and XDR: Attack disruption and SOC empowerment
Microsoft Ignite 2022
2022-10-12
Mitigate threats using Microsoft Defender for Endpoint
Article Microsoft Defender for Endpoint - Microsoft Defender for Endpoint
Article Microsoft Defender Vulnerability Management - Microsoft Defender Vulnerability Management
Article Overview of endpoint detection and response capabilities - Microsoft Defender for Endpoint
Additional Resources
Certification Microsoft Certified: Security Operations Analyst Associate - Certifications
Microsoft Tech Community Microsoft 365 Defender Tech Communities



























No comments:
Post a Comment