Microsoft 365 Defender is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
 |
| MS Defender |
Here's a list of the different Microsoft 365 Defender products and solutions that Microsoft 365 Defender coordinates with:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender Vulnerability Management
- Azure Active Directory Identity Protection
- Microsoft Data Loss Prevention
- App Governance
Related Posts:
Microsoft 365 Defender is an XDR solution that automatically collects, correlates, and analyzes signal, threat, and alert data from across your Microsoft 365 environment, including endpoint, email, applications, and identities.
Microsoft Defender XDR is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation, and response across endpoints, identities, email, and applications to provide integrated protection against sophisticated attacks.
Microsoft Defender XDR helps security teams protect and detect their organizations by using information from other Microsoft security products, including:
- Microsoft Defender for Endpoint
- Microsoft Defender for Office 365
- Microsoft Defender for Identity
- Microsoft Defender for Cloud Apps
- Microsoft Defender Vulnerability Management
- Microsoft Defender for Cloud
- Microsoft Entra ID Protection
- Microsoft Data Loss Prevention
- App Governance
- Microsoft Purview Insider Risk Management
Exclude Devices & Transient Devices
Excluded devices are removed from vulnerability management, meaning that you won’t see any of the installed software and affecting vulnerabilities in the overview, nor will it count towards your exposure score.
You can exclude both active and inactive devices. If you try to exclude an active device, Defender displays a pop-up warning that this is unsupported.
It’s easy to create a view of excluded devices by applying a filter to the device inventory. By default, the filter ‘not excluded’ is enabled.
I see some organizations using this feature to ‘hide’ their legacy environment and artificially increase their exposure score. These organizations are lying to themselves. Just because a major vulnerability is excluded doesn’t mean it doesn’t exist. An attacker will always try to find the weakest link and it is important to identify any weak links.
I typically don’t recommend excluding a device that is active because the vulnerabilities on it are still accurate. Of course, scenarios exist where it is impossible to update a certain machine due to organizational restrictions. In that case, I recommend that you create an exception for a specific recommendation. Adding an exception means the recommendation is removed from the list; it enables you to focus on what is important. The main added value is that an exception can be scoped to a specific piece of software or vulnerability and doesn’t exclude the entire device.
The only time to exclude a device is if you remove a device from your network and want to immediately remove all associated software and vulnerabilities, instead of waiting for the device to become inactive.
Defender’s device discovery feature automatically looks for non-onboarded devices on a corporate network and adds them to the device inventory.
Microsoft released the transient devices feature in May 2024. This is an automated process to tag devices that have not appeared on the network for a long time, meaning there was not enough time to do an adequate scan. The intention is to avoid inventory clutter if a device hasn’t been seen long enough to execute an adequate discovery that would gather all required details of a device.
The transient devices feature is enabled by default and there is no way to turn it off. If you visit the device inventory page in the Microsoft Defender XDR portal, you will see that a filter is enabled automatically to filter out transient devices.
It is important to note that the transient devices feature doesn’t take any action on servers. I have seen cases where Defender tags a device as transient when it was a corporate asset.
The transient device feature helps administrators maintain a cleaner device overview by removing some clutter. However, I advise you to tread carefully and validate all transient devices to ensure you don’t filter out any useful devices. This can be done by checking all transient devices and verifying that there are no company assets included.
Inactive Devices
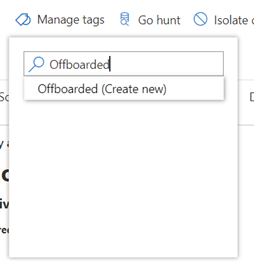
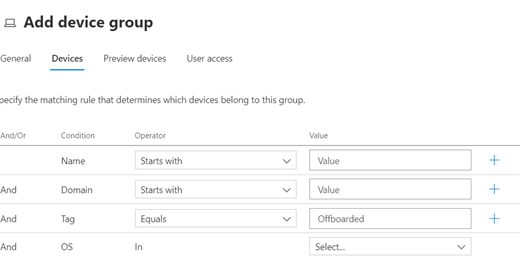
While no ideal solution exists for managing inactive devices within Microsoft Defender for Endpoint, I recommend using a combination of tags and device groups. Do this by adding the tag ‘Offboarded’ to inactive devices and creating a device group based on the tag value.
Throughout the portal and different reports, you can filter the data based on the group a device is in. By excluding devices tagged as inactive, these devices won’t skew your reports or interfere with other maintenance work.
The first step is to add the tag. This can be done manually on the device page or through the API. The most interesting case is where you can automate this process through an API. Some organizations have achieved this by connecting their asset lifecycle workflow with Defender to automatically execute the API call when the state of the device changes. (Developing)
Microsoft Defender Antivirus Performance Analyzer
Some options to analyze include:
- Top paths that impact scan time
- Top files that impact scan time
- Top processes that impact scan time
- Top file extensions that impact scan time
- Combinations – for example:
- top files per extension
- top paths per extension
- top processes per path
- top scans per file
- top scans per file per process
Using performance analyzer
To start recording system events, open PowerShell in administrator mode and perform the following steps:
Run the following command to start the recording:
New-MpPerformanceRecording -RecordTo <recording.etl>where
-RecordToparameter specifies full path location in which the trace file is saved. For more cmdlet information, see Microsoft Defender Antivirus cmdlets.If there are processes or services thought to be affecting performance, reproduce the situation by carrying out the relevant tasks.
Press ENTER to stop and save recording, or Ctrl+C to cancel recording.
Analyze the results using the performance analyzer's
Get-MpPerformanceReportparameter. For example, on executing the commandGet-MpPerformanceReport -Path <recording.etl> -TopFiles 3 -TopScansPerFile 10, the user is provided with a list of top-ten scans for the top three files affecting performance.For more information on command-line parameters and options, see the New-MpPerformanceRecording and Get-MpPerformanceReport.
Protect your c-suite with priority account protection
- Sign to the Microsoft Defender portal.
- In the navigation bar, select Settings.
- Select Priority account protection.
- Make sure protection is set to On.
Role & Permissions
- Global reader
- Security reader
Microsoft 365 Defender Protection
Zero Trust
In the illustration: Microsoft 365 Defender provides XDR capabilities for protecting:
- Endpoints, including laptops and mobile devices
- Data in Office 365, including email
- Cloud apps, including other SaaS apps that your organization uses
- On-premises Active Directory Domain Services (AD DS) and Active Directory Federated Services (AD FS) servers
Microsoft 365 Defender helps you apply the principles of Zero Trust in the following ways:
| Zero Trust principle | Met by |
|---|---|
| Verify explicitly | Microsoft 365 Defender provides XDR across users, identities, devices, apps, and emails. |
| Use least privileged access | If used with Azure Active Directory (Azure AD) Identity Protection, Microsoft 365 Defender blocks users based on the level of risk posed by an identity. Azure AD Identity Protection is licensed separately from Microsoft 365 Defender and is included with Azure AD Premium P2. |
| Assume breach | Microsoft 365 Defender continuously scans the environment for threats and vulnerabilities. It can implement automated remediation tasks, including automated investigations and isolating endpoints. |
Microsoft 365 Defender services protect:
- Endpoints with Defender for Endpoint - Defender for Endpoint is a unified endpoint platform for preventative protection, post-breach detection, automated investigation, and response.
- Assets with Defender Vulnerability Management - Microsoft Defender Vulnerability Management delivers continuous asset visibility, intelligent risk-based assessments, and built-in remediation tools to help your security and IT teams prioritize and address critical vulnerabilities and misconfigurations across your organization.
- Email and collaboration with Defender for Office 365 - Defender for Office 365 safeguards your organization against malicious threats posed by email messages, links (URLs) and collaboration tools.
- Identities with Defender for Identity and Azure Active Directory (Azure AD) Identity Protection - Microsoft Defender for Identity is a cloud-based security solution that leverages your on-premises Active Directory signals to identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions directed at your organization. Azure AD Identity Protection uses the learnings Microsoft has acquired from their position in organizations with Azure AD, the consumer space with Microsoft Accounts, and in gaming with Xbox to protect your users.
- Applications with Microsoft Defender for Cloud Apps - Microsoft Defender for Cloud Apps is a comprehensive cross-SaaS solution bringing deep visibility, strong data controls, and enhanced threat protection to your cloud apps.
Microsoft 365 Defender Services
- Defender for Endpoint in Microsoft 365 Defender
- Defender for Office 365 in Microsoft 365 Defender
- Defender for Identity in Microsoft 365 Defender
- Defender for Cloud Apps in Microsoft 365 Defender
- Redirecting Defender for Endpoint to Microsoft 365 Defender
- Redirecting Defender for Cloud Apps to Microsoft 365 Defender
Security portals
Security operators and admins can go to the following portals to manage security-specific settings, investigate possible threat activities, respond to active threats, and collaborate with IT admins to remediate issues.
| Portal name | Description | Link |
|---|---|---|
| Microsoft 365 Defender portal | Monitor and respond to threat activity and strengthen security posture across your identities, email, data, endpoints, and apps with Microsoft 365 Defender | security.microsoft.com |
| Microsoft Defender Security Center | Monitor and respond to threat activity on your endpoints using capabilities provided with Microsoft Defender for Endpoint. NOTE: Most tenants should now be redirected to the Microsoft 365 Defender portal at security.microsoft.com. | securitycenter.windows.com |
| Office 365 Security & Compliance Center | Manage Exchange Online Protection and Microsoft Defender for Office 365 to protect your email and collaboration services, and ensure compliance to various data-handling regulations. NOTE: Most tenants using the security sections of the Office 365 Security & Compliance Center should now be redirected to the Microsoft 365 Defender portal at security.microsoft.com. | protection.office.com |
| Defender for Cloud portal | Use Microsoft Defender for Cloud to strengthen the security posture of your data centers and your hybrid workloads in the cloud | portal.azure.com/#blade/Microsoft_Azure_Security |
| Microsoft Defender for Identity portal | Identify, detect, and investigate advanced threats, compromised identities, and malicious insider actions using Active Directory signals with Microsoft Defender for Identity | portal.atp.azure.com |
| Defender for Cloud Apps portal | Use Microsoft Defender for Cloud Apps to get rich visibility, control over data travel, and sophisticated analytics to identify and combat cyberthreats on cloud services | portal.cloudappsecurity.com |
| Microsoft Security Intelligence portal | Get security intelligence updates for Microsoft Defender for Endpoint, submit samples, and explore the threat encyclopedia | microsoft.com/wdsi |
Portals for other workloads
While these portals are not specifically for managing security, they support various workloads and tasks that can impact your security. Visit these portals to manage identities, permissions, device settings, and data handling policies.
| Portal name | Description | Link |
|---|---|---|
| Entra portal | Access and administer the Microsoft Entra family to protect your business with decentralized identity, identity protection, governance, and more, in a multi-cloud environment | entra.microsoft.com |
| Azure portal | View and manage all your Azure resources | portal.azure.com |
| Azure Active Directory portal | View and manage Azure Active Directory | aad.portal.azure.com |
| Microsoft Purview compliance portal | Manage data handling policies and ensure compliance with regulations | compliance.microsoft.com |
| Microsoft 365 admin center | Configure Microsoft 365 services; manage roles, licenses, and track updates to your Microsoft 365 services | admin.microsoft.com |
| Microsoft Intune admin center | Use Microsoft Intune to manage and secure devices. Can also combine Intune and Configuration Manager capabilities. | endpoint.microsoft.com |
| Microsoft Intune portal | Use Microsoft Intune to deploy device policies and monitor devices for compliance | endpoint.microsoft.com |
Plan and Pricing
- P1 - Support for Windows 10, Windows 11, iOS, Android OS, and macOS devices
- P2 - Support for Windows (client only) and non-Windows platforms (macOS, iOS, Android, and Linux)
- Vulnerability Management Addon for P2
- Business
- Microsoft Defender for Servers Plan 1 ($5) or Plan 2 ($15) (recommended for enterprise customers) as part of the Defender for Cloud offering. To learn more. see Overview of Microsoft Defender for Servers.
- Microsoft Defender for Endpoint for Servers (recommended for enterprise customers). To learn more, see Defender for Endpoint onboarding Windows Server.
- Microsoft Defender for Business servers (for small and medium-sized businesses who have Microsoft Defender for Business). To learn more, see How to get Microsoft Defender for Business servers.
Auto Onboarding using MDM - Intune
1. Defender - Settings - Endpoints - Configuration Management - Intune PermissionsUnlock Settings for Microsoft Defender Antivirus
After offboarded machine from MDE, your settings for Microsoft Defender Antivirus will be locked and greyed out for any changes.Or , you can use Windows PowerShell:
• Open PowerShell as an administrator. You can do this by typing
"PowerShell" in the search bar, right-clicking on Windows PowerShell,
and selecting "Run as administrator".
• Enter the following command and press Enter:
reg delete
"HKLM\SOFTWARE\Policies\Microsoft\Windows Defender" /f;
Set-MpPreference -UILockdown 0
References
- Patrick Mercier
- Clean up Domain Controller DNS Records with Powershell - Scripting Blog (microsoft.com)
- PowerShell Active Directory DNS - Using Windows PowerShell to remove Stale / Dead Domain Controller records
- https://aka.ms/mdi/sizingtool - GitHub - microsoft/Microsoft-Defender-for-Identity-Sizing-Tool
- Group Managed Service Accounts Overview | Microsoft Docs
- https://docs.microsoft.com/en-us/defender-for-identity/suspicious-activity-guide
- Microsoft Defender for Identity security alert guide
- This article provides a list of the security alerts issued by Microsoft Defender for Identity.
- https://github.com/microsoft/Azure-Advanced-Threat-Protection/tree/master/Auditing
- Azure-Advanced-Threat-Protection/Auditing at master · microsoft/Azure-Advanced-Threat-Protection
- Additional Resources to improve Customer Experience with Azure Advanced Threat Protection - Azure-Advanced-Threat-Protection/Auditing at master · microsoft/Azure-Advanced-Threat-Protection
- https://github.com/microsoft/DefendTheFlag/
GitHub - microsoft/DefendTheFlag: Get started fast with a built out lab, built from scratch via Azure Resource Manager (ARM) and Desired State Configuration (DSC), to test out Microsoft's security ...
- Get started fast with a built out lab, built from scratch via Azure Resource Manager (ARM) and Desired State Configuration (DSC), to test out Microsoft's security products. - GitHub - micro...
- https://docs.microsoft.com/en-us/defender-for-identity/playbook-setup-lab
- https://docs.microsoft.com/en-us/defender-for-identity/sensitive-accounts
- https://docs.microsoft.com/api/search/rss?search=%22This+article+is+updated+frequently+to+let+you+know+what%27s+new+in+the+latest+release+of+Azure+ATP%22&locale=en-us
- What's new in Microsoft Defender for Identity | Microsoft Docs
- PowerShell-Suite/Invoke-NetSessionEnum.ps1 at master · FuzzySecurity/PowerShell-Suite · GitHub















No comments:
Post a Comment