This post is to summarize some knowledge points regarding Microsoft Azure learned from Internet.
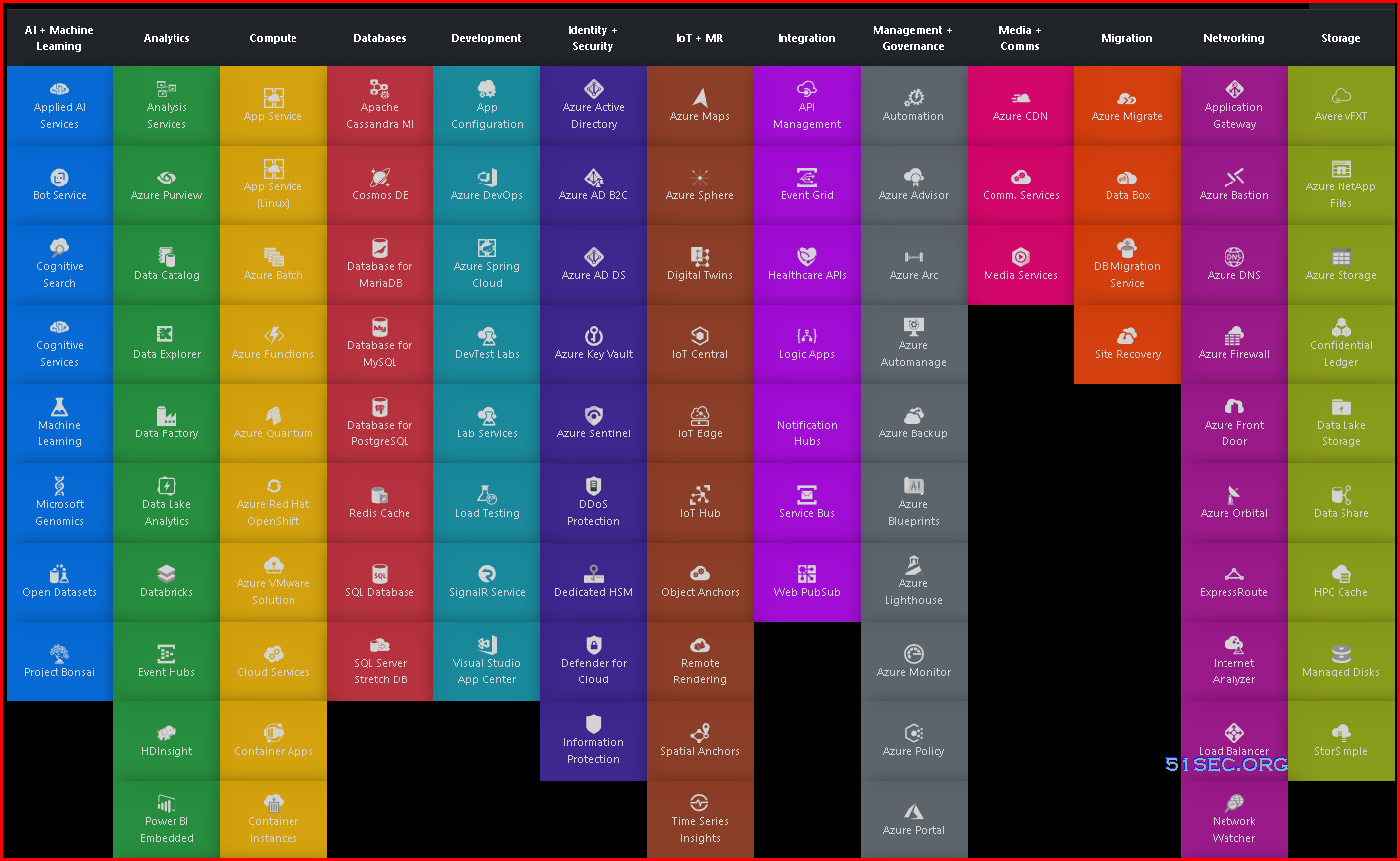
Azure Services
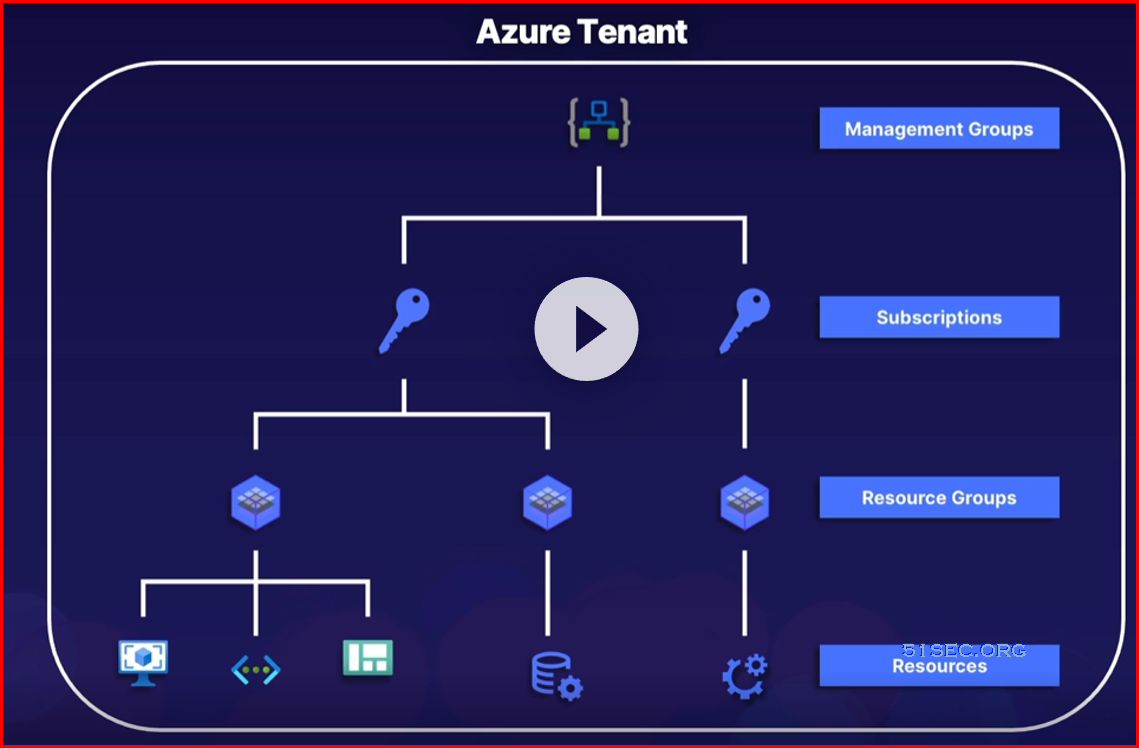
Azure Resources Hierarchy
- Tenant - Organization - AAD users
- Management Groups - Centralized management of subscriptions
- Subscriptions - Billing agreement
- Resource Groups - Group related resources together
- Resources - VMs, databases , etc
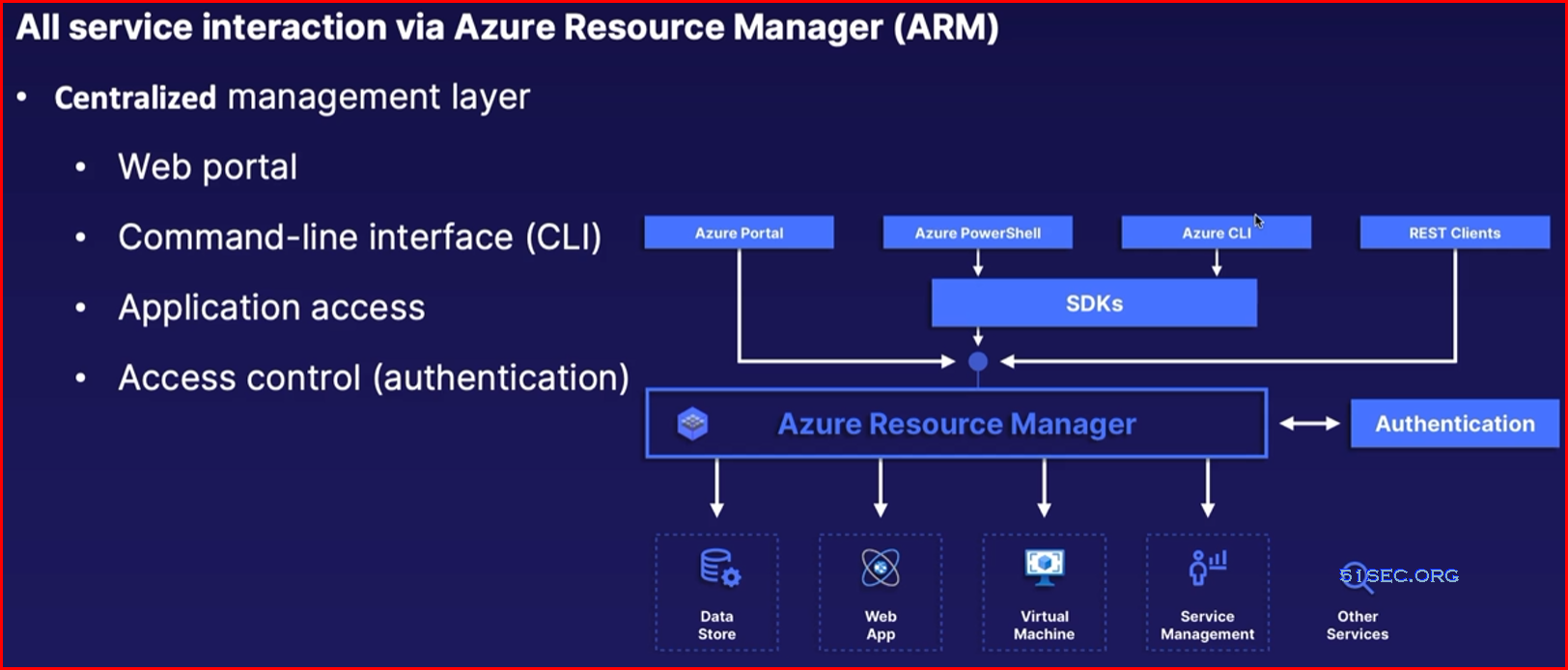
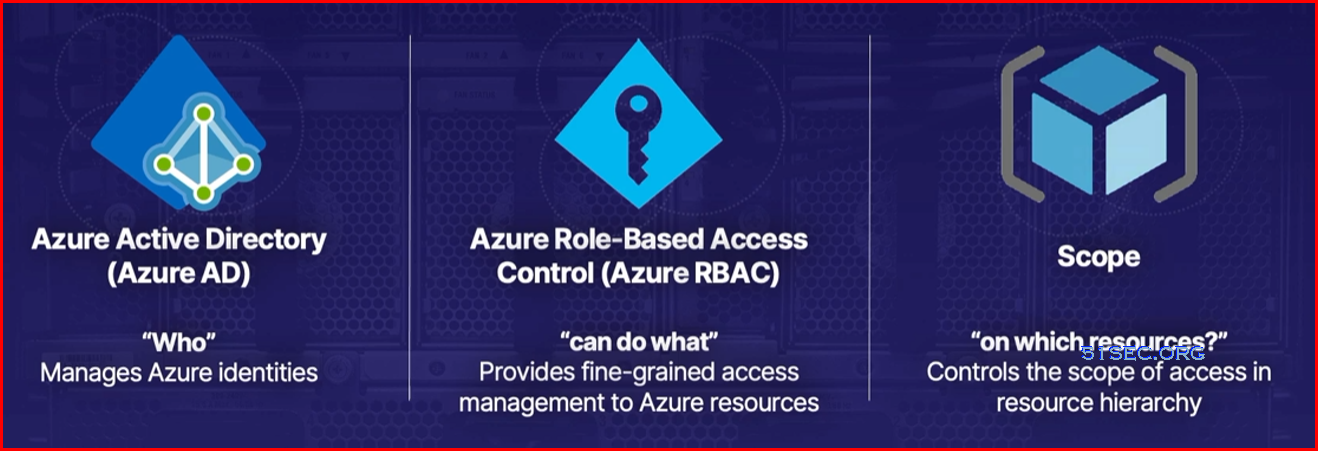
Identity and Access management
Components:
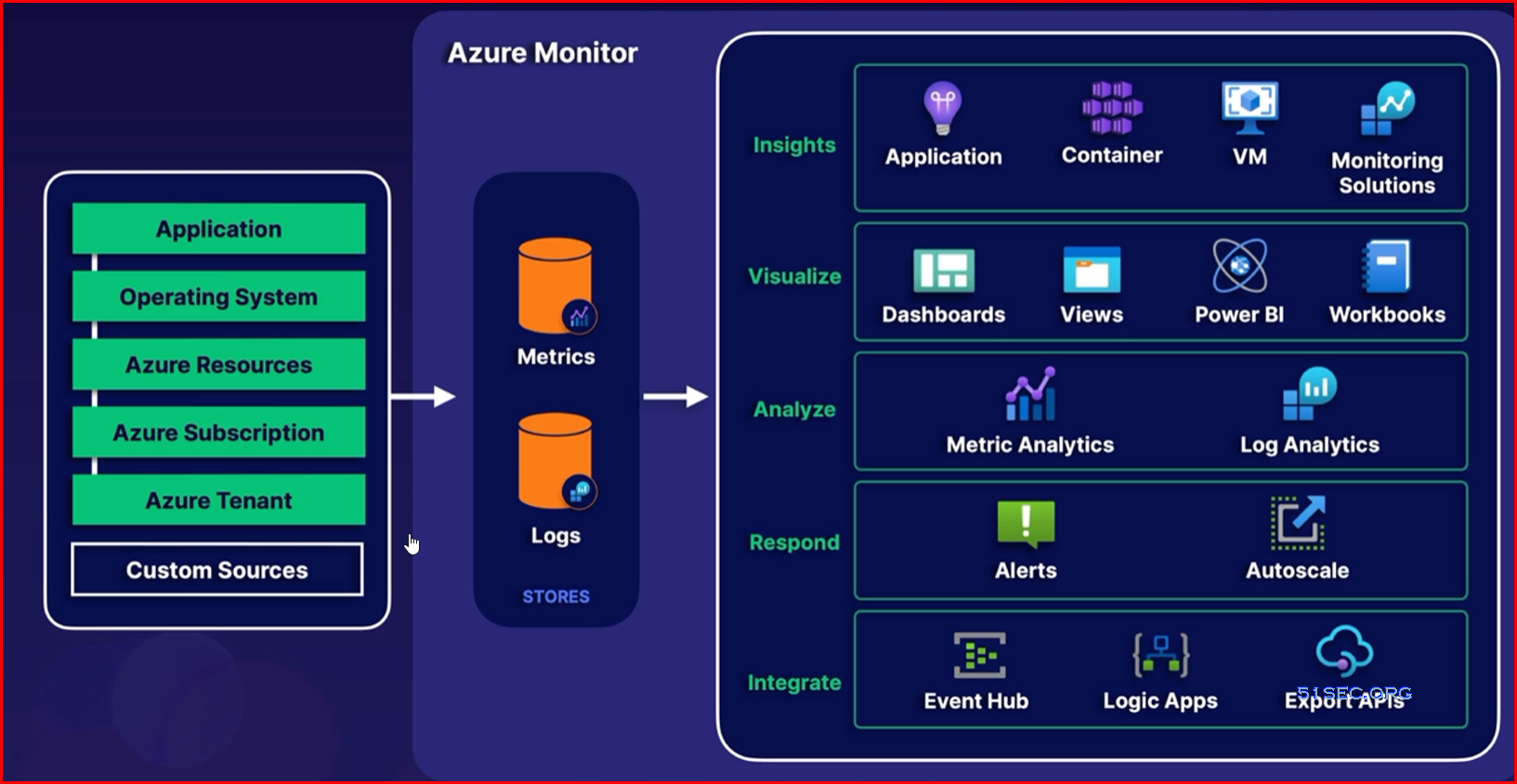
Monitoring Azure Environment
Logs
Metrics
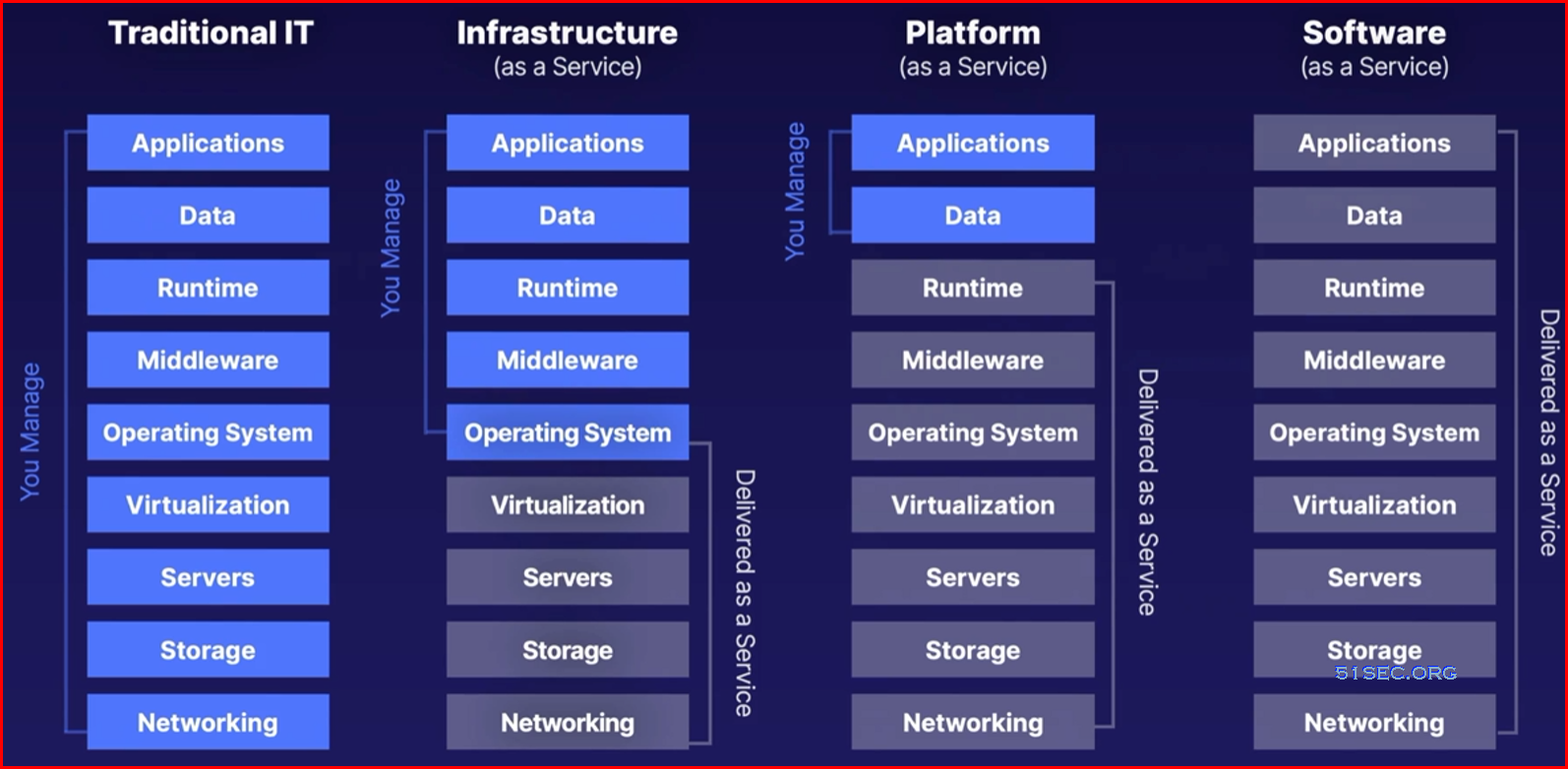
Core Services
- Virtual Machines (Compute)
- Flexibility
- Availability Set
- Scale Set
- Networking
- vNet - SDN
- Subnets
- Peering/VPN/Express Route
- Network Security Groups / Firewall
- Storage
- blob, Files, Disks, Queus, Tables.
- Database and Analytics
- Structured Data - Azure SQL, Cosmos DB, Managed Mysql/PostgreSQL, and others
- Analytics : BI - Azure Synapse - Azure Data Lake
- App service and Serverless Compute
- Web apps, Mobile apps, API apps, Cloud Services, service Fabric, Notification Hubs, Functions
Pricing Discount
Azure Pricing Calculator
- https://azure.microsoft.com/en-ca/pricing/calculator/
Azure Benefits and Incentives
- https://azure.microsoft.com/en-ca/pricing/offers/
- Azure Hybrid Benefits
- Azure Migration and Modernisation Programme
- FastTrack for Azure
- Azure dev/test pricing
- Free Azure Sentinel data ingestion
- Free support for commercial contracts
- Azure savings plan for compute
- Reservations
- Azure Spot Virtual Machines
- Azure dev/test pricing
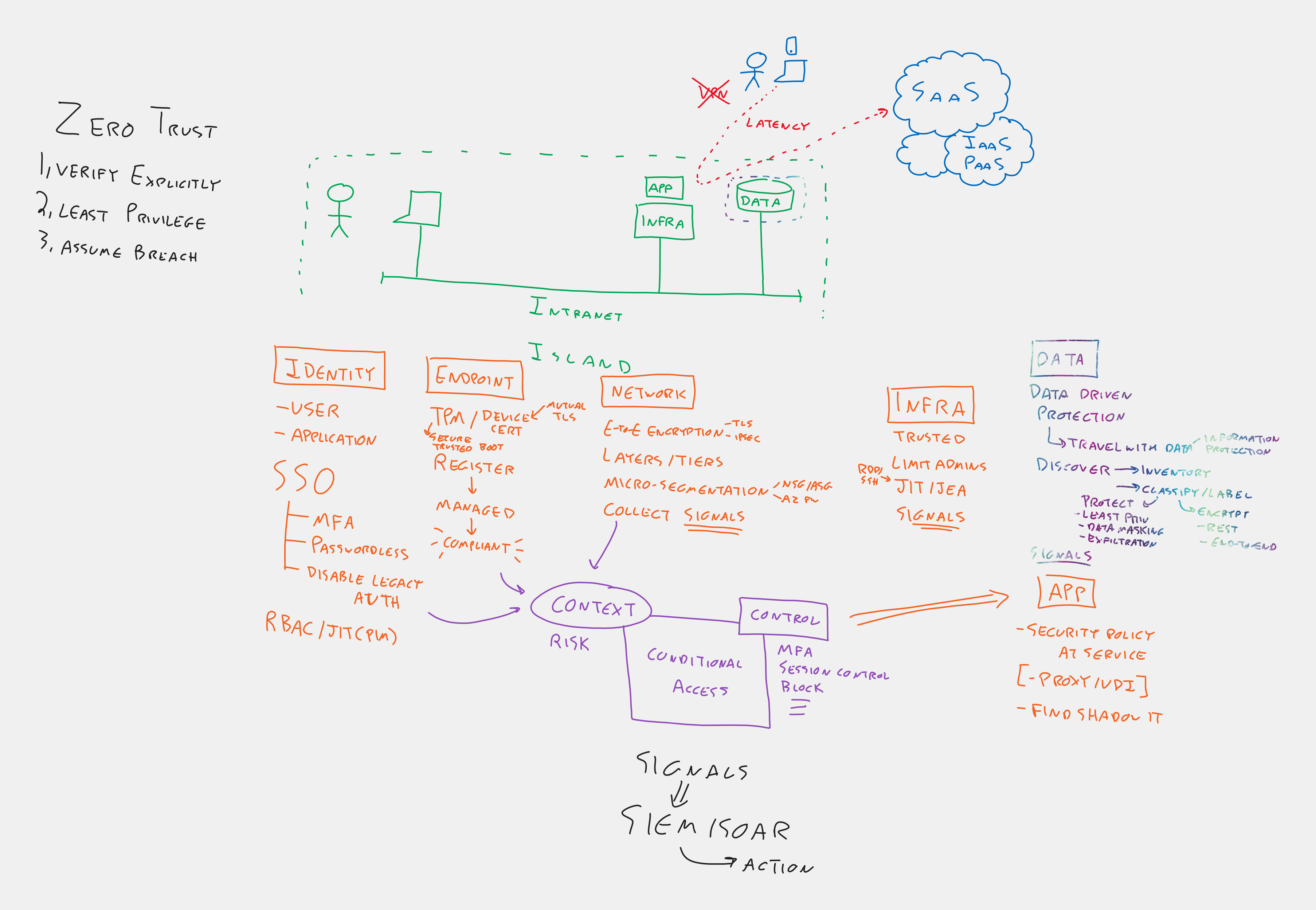
Microsoft Zero Trust (Assume-Breach)
- Verify explicitly
- Use least privilege access
- Assume breach
The key tenets of a modern defense-in-depth strategy include:
- Protect privileged access – use privileged access management solutions to monitor and secure access to privileged accounts (superuser accounts, local and domain administrator accounts, application administrative accounts, etc.) by both human and non-human identities (applications, scripts, bots, etc.).
- Lockdown critical endpoints – use advanced endpoint privilege management solutions to lock down privilege across all endpoints, prevent lateral movement, and defend against ransomware and other forms of malware.
- Enable adaptive multifactor authentication – use contextual information (location, time of day, IP address, device type, etc.) and business rules to determine which authentication factors to apply to a particular user in a particular situation.
- Secure developer tools – use secrets management solutions to secure, manage, rotate and monitor secrets and other credentials used by applications, automation scripts, and other non-human identities.
Zero Trust vs Defense in Depth
5 Steps to Create a Zero Trust Network
Note: MS Learn Zero Trust Guidance Center
RaMP initiatives for Zero Trust
To rapidly adopt Zero Trust in your organization, RaMP offers technical deployment guidance organized in these initiatives.
| Initiative | Steps |
|---|---|
| Top priority | Critical security modernization initiatives: |
User access and productivity | |
Data, compliance, and governance | |
| Modernize security operations |
|
| As needed | Additional initiatives based on Operational Technology (OT) or IoT usage, on-premises and cloud adoption, and security for in-house app development: |
| OT and Industrial IoT |
|
| Datacenter & DevOps Security |
|
Here is the overall architecture for Zero Trust.
The RaMP initiatives for Zero Trust address all of the elements of this architecture. As you step through the initiatives, we'll show which parts are being covered.
From John Savil's Zero Trust Video: https://www.youtube.com/watch?v=hhS8VdGnfOU&t=1018s








No comments:
Post a Comment