Install Agent
Download the agent installer
File will be saved to your downloads area, as defined by your local system.
Copy QualysCloudAgent.rpm to the host you want to monitor and run commands. Click here to troubleshoot.
Copy and paste this command for installation (sudo access required):
sudo rpm -ivh QualysCloudAgent.rpm
sudo /usr/local/qualys/cloud-agent/bin/qualys-cloud-agent.sh ActivationId=16beb165-1a29-4d238-80b9-5579d7810849 CustomerId=36ca3719-7f25-e45e-8243e-b1f1cc6b09e9 ServerUri=https://qagpublic.qg1.apps.qualys.ca/CloudAgent/
3. Verify Agents Installed Successful
Activate Agent
On Demand Scan
Uninstall Cloud Agent /Deactivate Agent to Recycle Licenses
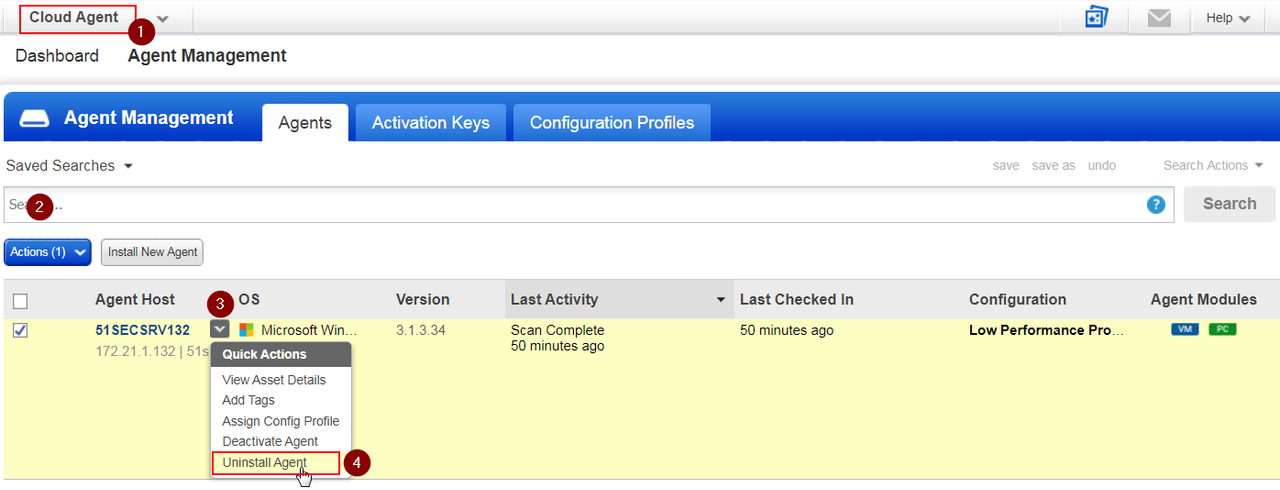
1. Uninstall Agent
2. Deactivate Agent
3. Manual Uninstall from host
Windows Agent
Use Uninstall.exe. Learn more
Linux/Unix Agent (RPM)
Use this command:
"sudo rpm -e qualys-cloud-agent"
Linux Agent (Debian)
Use this command:
"sudo dpkg --purge qualys-cloud-agent"
Report for Single Agent Using Tag
1. add tags2. New Template Based Scan Report
3. Select Technical Report as template
4. Add tag into asset tags for filtering
4. Run report immediately or scheduling it for later
Reports for Cloud Agent Findings:
https://success.qualys.com/support/s/article/000003222
- Log in to Qualys.
- Select Vulnerability Management from the drop-down list.
- Click Reports > Templates> New> Scan Template.
- On the Report Title tab, give a title to your template.
- Choose Host Targets. Please note that you'll need to run the report on asset tags to get AGENT tracked hosts that are not in VM license, or add IP tracked entries in VM modules (as required) to generate reports on IP/All asset group. Check reporting on agent hosts and cloud agent hosts in asset search report for details.
- On the Findings tab, select the Asset Group, IP, or tags then scroll down to select Agent Data.
- On the Display tab, select the following:
- Host Data
- Text Summary
- Vulnerability Details
- Results
- Appendix
- New
- Active
- Reopened
- Confirmed Vulnerabilities: Active
- Potential Vulnerabilities: Active
- Information Gathered: Active
11. Click Run.

















No comments:
Post a Comment